 Technology peripherals
Technology peripherals
 It Industry
It Industry
 ICBC's U.S. subsidiary was attacked by ransomware, causing some system outages
ICBC's U.S. subsidiary was attacked by ransomware, causing some system outages
ICBC's U.S. subsidiary was attacked by ransomware, causing some system outages
ICBC Financial Services Co., Ltd. (hereinafter referred to as "ICBC Financial"), a wholly-owned subsidiary of Industrial and Commercial Bank of China, recently issued an announcement on its official website, stating that they were attacked by ransomware in the United States, causing some system interruptions. This incident occurred on November 8th, Eastern Time (November 9th, Beijing time)
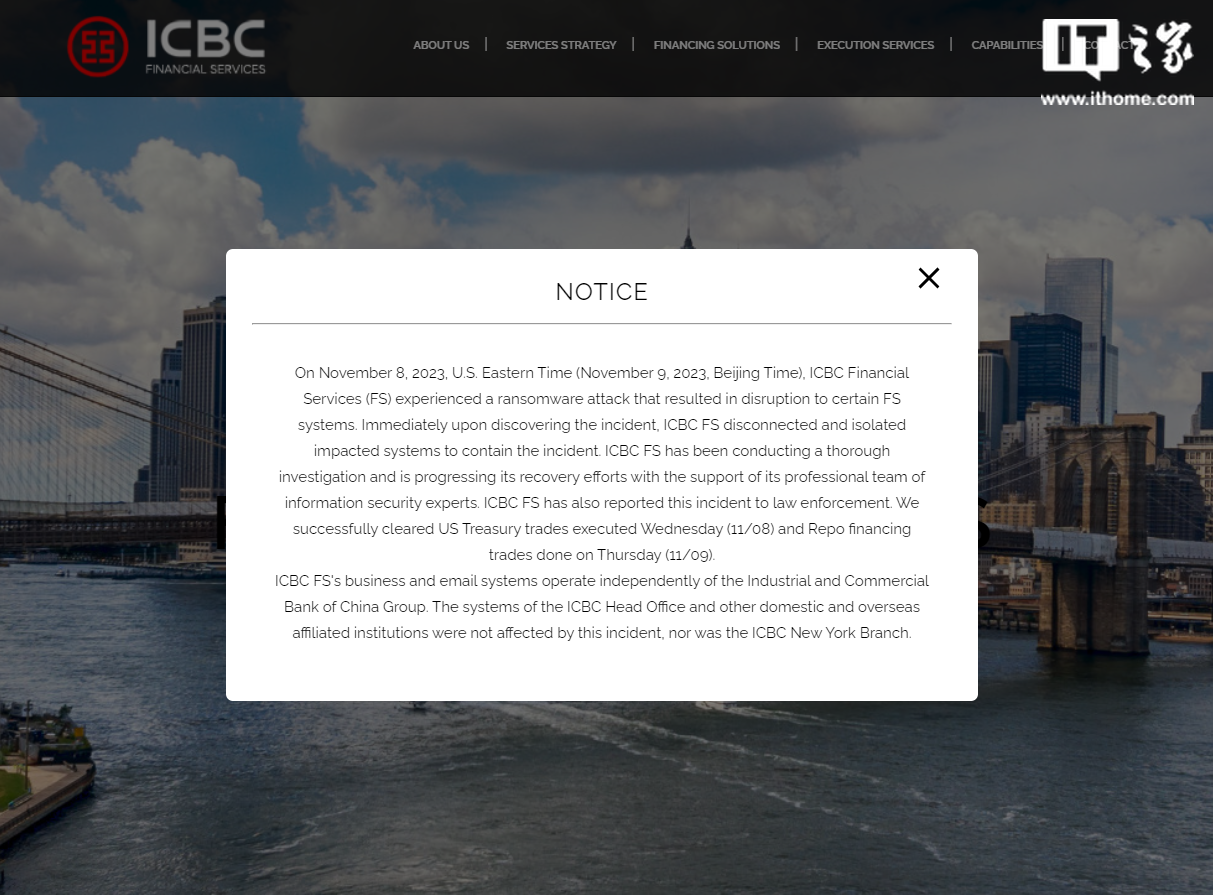
The official website of ICBC Financial issued an announcement saying that it was discovered that After the attack, the company immediately cut off and isolated the affected systems to avoid further spread of the attack. At present, the company has launched a thorough investigation and is supported by a team of information security experts and is working to restore the system. The company will also report the matter to law enforcement
This website noted that the statement also stated that despite the attack, the company successfully completed the settlement of U.S. Treasury securities transactions on November 8 and the return on November 9. purchase transaction. At the same time, the statement also showed that the company's business and email systems are independent from the ICBC Group's operations. The head office and other domestic and overseas branches of ICBC, including ICBC New York Branch, are not affected by this incident
ICBC Financial, a wholly-owned subsidiary of ICBC, is headquartered in New York, USA and is committed to serving major global institutions. Institutional clients in the market provide global clearing, financing and other services
Advertising statement: External links in this article (including but not limited to hyperlinks, QR codes, passwords, etc.) are intended to provide more information and save screening Time is for reference only. Please note that all articles on this site contain this statement
The above is the detailed content of ICBC's U.S. subsidiary was attacked by ransomware, causing some system outages. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1385
1385
 52
52
 Canada plans to ban hacking tool Flipper Zero as car theft problem surges
Jul 17, 2024 am 03:06 AM
Canada plans to ban hacking tool Flipper Zero as car theft problem surges
Jul 17, 2024 am 03:06 AM
This website reported on February 12 that the Canadian government plans to ban the sale of hacking tool FlipperZero and similar devices because they are labeled as tools that thieves can use to steal cars. FlipperZero is a portable programmable test tool that helps test and debug various hardware and digital devices through multiple protocols, including RFID, radio, NFC, infrared and Bluetooth, and has won the favor of many geeks and hackers. Since the release of the product, users have demonstrated FlipperZero's capabilities on social media, including using replay attacks to unlock cars, open garage doors, activate doorbells and clone various digital keys. ▲FlipperZero copies the McLaren keychain and unlocks the car Canadian Industry Minister Franço
 Hacker releases jailbreak tool compatible with iOS 15 and iOS 16
May 29, 2023 pm 04:34 PM
Hacker releases jailbreak tool compatible with iOS 15 and iOS 16
May 29, 2023 pm 04:34 PM
Apple has been working hard to improve the security of its operating system and devices, which has been proven considering how difficult it is for hackers to create jailbreak tools for iOS 15. But those who are keen on tinkering with iOS can now celebrate, as the palera1n team has released a jailbreak tool that is not only compatible with iOS15, but also iOS16. For those unfamiliar, the jailbreaking process removes software restrictions on an iOS device so that users can access and modify system files, allowing for various modifications such as tweaks, themes, and sideloading of apps outside of the App Store. Of course, Apple has always opposed the process of jailbreaking its devices. iOS15 and iOS16 jailbreak paler
 Hackers use AI face-changing technology to apply for jobs. Artificial intelligence security issues cannot be ignored
Apr 08, 2023 pm 02:51 PM
Hackers use AI face-changing technology to apply for jobs. Artificial intelligence security issues cannot be ignored
Apr 08, 2023 pm 02:51 PM
After the epidemic in the United States, many companies adopted the "Work From Home" (WFH) model. The FBI's Crime Complaint Center stated that they have recently received complaints from many corporate employers that during the recruitment process, job applicants have stolen the identities of others and used Deepfake technology to participate in remote interviews. These positions involve information technology, computer programming, databases and software-related fields. Some job seekers try to use the background and expertise of others to get jobs and use Deepfake technology to forge videos. They found that when conducting online interviews with job seekers, the job seekers' movements or opening and closing of their lips were not consistent with their speaking sounds. For example, when sneezing or coughing sounds were heard, the drawings
 European Interpol dismantles Ragnar Locker ransomware group, Capcom was attacked
Oct 23, 2023 pm 03:37 PM
European Interpol dismantles Ragnar Locker ransomware group, Capcom was attacked
Oct 23, 2023 pm 03:37 PM
According to news from this website on October 23, Europol issued a document announcing that law enforcement and judicial authorities from 11 countries this week carried out a major crackdown on one of the most dangerous ransomware campaigns in recent years - the RagnarLocker ransomware organization. It is understood that the group has launched multiple attacks on critical infrastructure around the world, including a cyberattack against Capcom in 2020. From October 16th to 20th, criminal police conducted search operations in the Czech Republic, Spain and Latvia. The "main leader" of the malicious ransomware was arrested in Paris, France, on October 16, and his home in the Czech Republic was also raided. In the following days, five suspects were questioned in Spain and Latvia. At the end of the action week, suspected Lagnar Group development
 Is it time to start worrying about AI hackers?
Apr 11, 2023 pm 02:52 PM
Is it time to start worrying about AI hackers?
Apr 11, 2023 pm 02:52 PM
AI attacks will first determine the target, then obtain feedback and continuously optimize and improve. If one day AI can develop completely novel solutions or even begin to optimize solutions, its lethality will be huge. System ambiguity is the current barrier against AI hackers. For games like Go, the rules, goals, and feedback are all simple and certain. There are no external things to disrupt the situation. Losing or winning is the feedback. GPT-3 AI can write coherent articles because the world it lives in is only text. Because of this, many current hacker reward activities are conducted in simulated environments, all artificial, all constrained, and all rules are prepared for AI. The fuzziness of the system is the key. We can input all global tax laws into AI, because there are
 Akira ransomware: FBI and Europol sound alert over $42 million in losses
Apr 22, 2024 am 11:00 AM
Akira ransomware: FBI and Europol sound alert over $42 million in losses
Apr 22, 2024 am 11:00 AM
Akira extracts millions of dollars from 250 companies as ransomware crisis deepens. An emerging ransomware group called Akira has attracted the attention of well-known organizations around the world. The group is estimated to be only one year old. Due to its extensive network intrusion activities, it has successfully invaded more than 250 organizations around the world and collected nearly 42 million yuan. USD ransom. An investigation led by the FBI revealed that Akira has been actively targeting businesses and critical infrastructure in North America, Europe and Australia since March 2023. Akira ransomware, which initially only targeted Windows systems, became more threatening after the FBI discovered its Linux version.
 The Matrix is coming! Burying 10,000 micron electrodes to eavesdrop on the brain, Musk's brain machine will be implanted in the human body
May 14, 2023 am 10:55 AM
The Matrix is coming! Burying 10,000 micron electrodes to eavesdrop on the brain, Musk's brain machine will be implanted in the human body
May 14, 2023 am 10:55 AM
There is a complex network in your head - 86 billion switches! It weighs 2 and a half pounds and consumes only 20W of power, which is equivalent to the energy consumption of a light bulb. However, it has created infinite miracles in bioelectronics! Is the brain an electronic organ? The core of brain research is the application of sensor technology. Whether we are familiar with scalp electrodes, magnetic resonance imaging, or newly pioneered methods such as implanted chips, we are all trying to explore this mysterious organ. Recently, the Belgian nanodigital research institute Imec pioneered the Neuropixels detector, which is a new probe to observe the living brain at the neuron level. The first-generation Neuropixels detector alone has been delivered to about 650 laboratories around the world. Meanwhile, Ime
 Who is a cyber hacker?
Sep 07, 2023 pm 05:42 PM
Who is a cyber hacker?
Sep 07, 2023 pm 05:42 PM
Cyber hackers refer to individuals or organizations with advanced computer technology and programming capabilities who invade computer systems, networks or devices through illegal means to gain unauthorized access, steal sensitive information, damage systems or conduct other malicious activities. Cyber hackers are divided into different types including ethical hackers, black hat hackers, gray hat hackers, state-level hackers and non-state hackers. Detailed introduction: 1. Ethical hackers, also known as white hat hackers or security consultants, are a type of legal hackers employed by organizations to test and evaluate computer systems and networks in an authorized manner.



