 Web Front-end
Web Front-end
 HTML Tutorial
HTML Tutorial
 An in-depth analysis of the importance and impact of 4xx status codes in the HTTP protocol
An in-depth analysis of the importance and impact of 4xx status codes in the HTTP protocol
An in-depth analysis of the importance and impact of 4xx status codes in the HTTP protocol

In-depth understanding of the importance and impact of 4xx status codes in the HTTP protocol requires specific code examples
With the continuous development of the Internet, the HTTP protocol as an application layer protocol, play an important role. In HTTP communication, the server transmits the results of request processing to the client through status codes. Among these status codes, 4xx status codes usually represent client errors and are used to indicate that something went wrong with the request.
This article will focus on the importance and impact of 4xx status codes in the HTTP protocol, and provide some specific code examples to help understand.
First of all, the importance of 4xx status codes is that they can help developers quickly locate and solve request problems. When a client sends a request, the server indicates something went wrong with the request by returning the appropriate 4xx status code. These status codes can provide useful information to help developers analyze the cause of the error and take appropriate actions. For example, when the client accesses a resource that does not exist, the server will return a 404 status code, prompting "Not Found", which prompts the developer that the resource does not exist and may need to further check whether the URL path or resource is correct.
Secondly, 4xx status codes can also help improve user experience. By returning appropriate status codes, the client can handle the situation accordingly and provide more targeted error prompts. For example, when the client does not provide required request parameters, the server can return a 400 status code and include specific error information, such as "Missing required parameter" in the response body. In this way, the client can provide users with more friendly prompts based on the returned status code and error information, helping users quickly find and solve problems.
So, let’s look at some common 4xx status codes in specific HTTP protocols and provide some code examples.
- 400 - Bad Request: When the request sent by the client has a syntax error or cannot be understood by the server, the server will return a 400 status code. The following is a sample code that simulates a request that does not conform to the HTTP protocol:
1 2 3 4 5 |
|
- 404 - Not Found: When the resource requested by the client does not exist, the server will return 404 status code. Here is a sample code that simulates a request for a non-existent resource:
1 2 3 4 5 |
|
- 401 - Unauthorized: When the client requests a resource that requires authentication, but no valid authentication is provided When receiving information, the server will return a 401 status code. The following is a sample code that simulates a request that does not carry authentication information:
1 2 3 4 5 |
|
Through these specific code examples, we can better understand the 4xx status codes in the HTTP protocol. Not only do they help us quickly locate and resolve request issues, they also provide a better user experience.
In short, it is crucial for developers to have a deep understanding of the importance and impact of 4xx status codes in the HTTP protocol. By using appropriate status codes and error messages, we can better handle request issues and provide a more user-friendly experience. Through specific code examples, we can more intuitively feel the usage and impact of 4xx status codes.
The above is the detailed content of An in-depth analysis of the importance and impact of 4xx status codes in the HTTP protocol. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
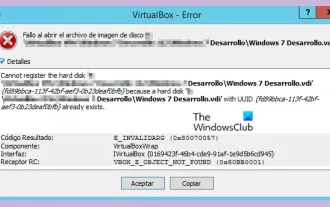 VBOX_E_OBJECT_NOT_FOUND(0x80bb0001)VirtualBox error
Mar 24, 2024 am 09:51 AM
VBOX_E_OBJECT_NOT_FOUND(0x80bb0001)VirtualBox error
Mar 24, 2024 am 09:51 AM
When trying to open a disk image in VirtualBox, you may encounter an error indicating that the hard drive cannot be registered. This usually happens when the VM disk image file you are trying to open has the same UUID as another virtual disk image file. In this case, VirtualBox displays error code VBOX_E_OBJECT_NOT_FOUND(0x80bb0001). If you encounter this error, don’t worry, there are some solutions you can try. First, you can try using VirtualBox's command line tools to change the UUID of the disk image file, which will avoid conflicts. You can run the command `VBoxManageinternal
 How effective is receiving phone calls using airplane mode?
Feb 20, 2024 am 10:07 AM
How effective is receiving phone calls using airplane mode?
Feb 20, 2024 am 10:07 AM
What happens when someone calls in airplane mode? Mobile phones have become one of the indispensable tools in people's lives. It is not only a communication tool, but also a collection of entertainment, learning, work and other functions. With the continuous upgrading and improvement of mobile phone functions, people are becoming more and more dependent on mobile phones. With the advent of airplane mode, people can use their phones more conveniently during flights. However, some people are worried about what impact other people's calls in airplane mode will have on the mobile phone or the user? This article will analyze and discuss from several aspects. first
 How to turn off the comment function on TikTok? What happens after turning off the comment function on TikTok?
Mar 23, 2024 pm 06:20 PM
How to turn off the comment function on TikTok? What happens after turning off the comment function on TikTok?
Mar 23, 2024 pm 06:20 PM
On the Douyin platform, users can not only share their life moments, but also interact with other users. Sometimes the comment function may cause some unpleasant experiences, such as online violence, malicious comments, etc. So, how to turn off the comment function of TikTok? 1. How to turn off the comment function of Douyin? 1. Log in to Douyin APP and enter your personal homepage. 2. Click "I" in the lower right corner to enter the settings menu. 3. In the settings menu, find "Privacy Settings". 4. Click "Privacy Settings" to enter the privacy settings interface. 5. In the privacy settings interface, find "Comment Settings". 6. Click "Comment Settings" to enter the comment setting interface. 7. In the comment settings interface, find the "Close Comments" option. 8. Click the "Close Comments" option to confirm closing comments.
 The impact of data scarcity on model training
Oct 08, 2023 pm 06:17 PM
The impact of data scarcity on model training
Oct 08, 2023 pm 06:17 PM
The impact of data scarcity on model training requires specific code examples. In the fields of machine learning and artificial intelligence, data is one of the core elements for training models. However, a problem we often face in reality is data scarcity. Data scarcity refers to the insufficient amount of training data or the lack of annotated data. In this case, it will have a certain impact on model training. The problem of data scarcity is mainly reflected in the following aspects: Overfitting: When the amount of training data is insufficient, the model is prone to overfitting. Overfitting refers to the model over-adapting to the training data.
 What problems will bad sectors on the hard drive cause?
Feb 18, 2024 am 10:07 AM
What problems will bad sectors on the hard drive cause?
Feb 18, 2024 am 10:07 AM
Bad sectors on a hard disk refer to a physical failure of the hard disk, that is, the storage unit on the hard disk cannot read or write data normally. The impact of bad sectors on the hard drive is very significant, and it may lead to data loss, system crash, and reduced hard drive performance. This article will introduce in detail the impact of hard drive bad sectors and related solutions. First, bad sectors on the hard drive may lead to data loss. When a sector in a hard disk has bad sectors, the data on that sector cannot be read, causing the file to become corrupted or inaccessible. This situation is especially serious if important files are stored in the sector where the bad sectors are located.
 Understand the importance and necessity of Linux backup
Mar 19, 2024 pm 06:18 PM
Understand the importance and necessity of Linux backup
Mar 19, 2024 pm 06:18 PM
Title: An in-depth discussion of the importance and necessity of Linux backup In today's information age, the importance and value of data have become increasingly prominent, and Linux, as an operating system widely used in servers and personal computers, has attracted much attention in terms of data security. . In the daily use of Linux systems, we will inevitably encounter problems such as data loss and system crashes. At this time, backup is particularly important. This article will delve into the importance and necessity of Linux backup, and combine it with specific code examples to illustrate the implementation of backup.
 What specific impact do mine cards have on the game?
Jan 03, 2024 am 09:05 AM
What specific impact do mine cards have on the game?
Jan 03, 2024 am 09:05 AM
Some users may consider buying mining cards for the sake of cheapness. After all, these cards are top-notch graphics cards. However, some gamers are worried about the impact of mining cards on playing games. Let’s take a look at the detailed introduction below. What are the effects of using a mining card to play games: 1. The stability of playing games with a mining card cannot be guaranteed, because the life of the mining card is very short and it is likely to become useless after just playing. 2. The mining card is basically a castrated version of the original version. Due to long-term wear and tear, the performance in all aspects may be weak. 3. In this way, users may not be able to display all the effects of the game when playing the game. 4. Moreover, the electronic components of the graphics card will age in advance, not to mention that playing games also consumes the graphics card, so it is drained to a greater extent, so the impact on the game is great. 5. In general, use mining cards to play games
 What impact does chassis leakage have on the computer?
Feb 22, 2024 pm 06:48 PM
What impact does chassis leakage have on the computer?
Feb 22, 2024 pm 06:48 PM
What impact does chassis leakage have on computers? With the continuous advancement of technology, computers have gradually become an indispensable tool in people's lives. Whether it is work, study or entertainment, they are inseparable from the use of computers. However, while we enjoy the convenience brought by computers, we also need to pay attention to its security. Case leakage is a potential problem that, if not dealt with in time, may have a serious impact on the computer and the user. First of all, chassis leakage will cause damage to computer hardware. The computer's motherboard, power supply, internal circuits and other components are all inside the chassis. Once the chassis





