
A quick guide to using Terminal to recover deleted files with still running processes on your Linux system.
Deleted files can be recovered in many cases, such as when the file has an active process operating on it and is currently in use by a single or multiple users. In a Linux system, each currently running process is given an ID, called a process identifier (PID), and stored in the /proc directory. This is exactly what we need to recover deleted files in a process that is still running (with PID).
Calculate MD5 hash of original fileBefore deleting, we will calculate the MD5 of the file. This way we can compare the original MD5 hash with the MD5 hash of the recovered file. This process will ensure that the integrity of the compressed file we recover is the same and that it has not been corrupted.
md5sum opengapps.zip >> md5-opengapps.txt
To display the contents of the text file.
cat md5-opengapps.txt 86489b68b40d144f0e00a0ea8407f7c0 opengapps.zip
After checking the MD5 hash of the compressed file. We keep the compressed file open (LCTT Annotation: Here we use file-roller, a graphical interface decompression program to keep the compressed file open, which is built into the GNOME environment; in the desktop environment, use desktop tools to open a compressed package It can also play the same role. Also, the example in this article is not very appropriate. If the open configuration file of a service process is deleted, then this recovery is very meaningful) and delete it. After that, we will start the recovery process of the files with the following steps:
rm opengapps.zip
As we mentioned earlier, the running process is in the /proc directory. We can search for the required process in this directory using the following command:
Since we already know that the file name includes the .zip extension, we can search using the .zip extension. It will limit the output results and show the required processes.
ps -axu | grep .zip m 13119 0.8 1.0 121788 30788 ? Sl 06:17 0:00 file-roller /home/m/Downloads/Compressed/opengapps.zip m 13164 0.0 0.0 5108 832 pts/20 S+ 06:18 0:00 grep --color=auto .zip
We will then go to the directory containing PID 13119 and open the fd subdirectory.
cd /proc/13119/fd
fd (file descriptor) directory contains multiple files, including the files we need to recover. This file is linked to the original file as a hard link.
All files in the fd directory are numerically linked to "filename". Therefore, to determine which of these files is linked to the original file, we will list the /fd directory with the verbose listing option.
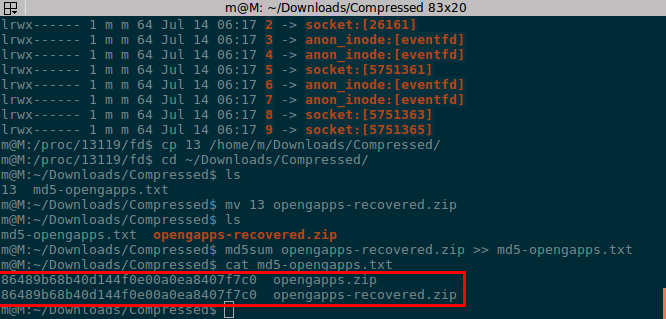
ls -l total 0 lr-x------ 1 m m 64 Jul 14 06:17 0 -> /dev/null lrwx------ 1 m m 64 Jul 14 06:17 1 -> socket:[26161] lrwx------ 1 m m 64 Jul 14 06:17 10 -> anon_inode:[eventfd] lr-x------ 1 m m 64 Jul 14 06:17 11 -> anon_inode:inotify lrwx------ 1 m m 64 Jul 14 06:17 12 -> socket:[5752671] lr-x------ 1 m m 64 Jul 14 06:17 13 -> /home/m/Downloads/Compressed/opengapps.zip (deleted) lrwx------ 1 m m 64 Jul 14 06:17 2 -> socket:[26161] lrwx------ 1 m m 64 Jul 14 06:17 3 -> anon_inode:[eventfd] lrwx------ 1 m m 64 Jul 14 06:17 4 -> anon_inode:[eventfd] lrwx------ 1 m m 64 Jul 14 06:17 5 -> socket:[5751361] lrwx------ 1 m m 64 Jul 14 06:17 6 -> anon_inode:[eventfd] lrwx------ 1 m m 64 Jul 14 06:17 7 -> anon_inode:[eventfd] lrwx------ 1 m m 64 Jul 14 06:17 8 -> socket:[5751363] lrwx------ 1 m m 64 Jul 14 06:17 9 -> socket:[5751365]
As you can see in the terminal output, the original file "opengapps.zip" has been deleted, but it is still linked to a filename 13 with process PID 13119. However, we can still recover it by copying the linked files to a safe place.
cp 13 /home/m/Downloads/Compressed
After the file is copied. We will go back to the directory containing the recovered files and rename it using the following command.
mv 13 opengapps-recovered.zip
Since we have restored the file. Let's check the integrity of the file, just to make sure the file isn't corrupted and is the same as the original. Earlier we saved the MD5 hash of the original file.
md5sum opengapps-recovered.zip >> md5-opengapps.txt
This command will check the MD5 hash of the file and append the MD5 hash of the newly recovered file in the file to easily compare the two MD5 hashes.
The contents of a text file can be displayed to compare the MD5 hash values of the original and recovered files.
cat md5-opengapps.txt 86489b68b40d144f0e00a0ea8407f7c0 opengapps.zip 86489b68b40d144f0e00a0ea8407f7c0 opengapps-recovered.zip
The MD5 hash of the recovered file is the same. So, we successfully recovered our previously deleted files with consistent file integrity and working fine.
Note: In some cases, some files cannot be seen with the ps -axu command. So, try to check the running program and recover files from it.
Suppose we have a video with an .avi extension being played using Totem media player. All you need to do is check the PID of Totem and follow the same instructions mentioned in this example.
To find the PID of a running program, use the following command, followed by the name of the program.
pidof 程序名
The above is the detailed content of Say goodbye to the worry of accidentally deleting files in Linux, mom no longer has to worry. For more information, please follow other related articles on the PHP Chinese website!




