Methods to solve localstorage security vulnerabilities

Security vulnerabilities in localstorage and how to solve them
With the development of the Internet, more and more applications and websites are beginning to use the Web Storage API, of which localstorage is the most A commonly used one. Localstorage provides a mechanism to store data on the client side, persisting data across page sessions regardless of session end or page refresh. However, just because of the convenience and wide application of localstorage, it also has some security vulnerabilities, which may cause users' sensitive information to be leaked or used maliciously.
First of all, the data in localstorage is stored in the browser in clear text, which means that anyone with access to the browser can directly view and modify the stored data. Therefore, for sensitive information such as passwords, credit card information, etc., it is best not to store it directly in localstorage, but to encrypt it before storing it.
Secondly, another reason why localstorage has security risks is that all scripts under the same domain name can access and modify localstorage data. This means that if a malicious script is present in a website, it can obtain and tamper with data stored in localstorage by other legitimate scripts. In order to avoid this situation from happening, we can take the following measures:
- Store sensitive information in sessionstorage: sessionstorage is only valid in the current session. After the page is closed, the session ends and the data will follow. destroy. Storing sensitive information in sessionstorage avoids the risk of data leakage over time.
- Encrypt data: Even if the data is stored in localstorage, the data can be encrypted first to ensure that it cannot be decrypted even if it is obtained by a malicious script. Algorithms such as AES can be used to encrypt data, combined with key management strategies to ensure the security of keys.
- Restrict scripts that access localstorage: You can use CSP (Content Security Policy) to restrict the browser from loading resources under the specified domain name to avoid the injection of malicious scripts.
The sample code is as follows:
Encryption function:
function encryptData(data, key) {
// 使用AES算法对数据进行加密处理
// ...
return encryptedData;
}Decryption function:
function decryptData(encryptedData, key) {
// 使用AES算法对数据进行解密处理
// ...
return decryptedData;
}Storage sensitive information:
var sensitiveData = {
username: 'example',
password: 'example123'
};
var encryptedData = encryptData(JSON.stringify(sensitiveData), 'encryption-key');
localStorage.setItem('encryptedSensitiveData', encryptedData);Obtain and decrypt sensitive information:
var encryptedData = localStorage.getItem('encryptedSensitiveData');
var decryptedData = decryptData(encryptedData, 'encryption-key');
var sensitiveData = JSON.parse(decryptedData);
console.log(sensitiveData.username);Through the above encryption and decryption function, sensitive information is stored in localstorage in encrypted form. Even if someone obtains the data in localstorage, the sensitive information cannot be directly decoded. At the same time, limiting the access scope of localstorage and strengthening the security of domain name resource loading can further improve the security of localstorage.
In summary, although localstorage provides us with a convenient client-side storage mechanism, it also has some security vulnerabilities. In order to protect users' sensitive information, we need to take measures such as avoiding direct storage of sensitive information, encrypting data, and restricting access to localstorage scripts. Only by comprehensively considering these factors can the security of localstorage and the confidentiality of user information be ensured.
The above is the detailed content of Methods to solve localstorage security vulnerabilities. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Solution to the problem that Win11 system cannot install Chinese language pack
Mar 09, 2024 am 09:48 AM
Solution to the problem that Win11 system cannot install Chinese language pack
Mar 09, 2024 am 09:48 AM
Solution to the problem that Win11 system cannot install Chinese language pack With the launch of Windows 11 system, many users began to upgrade their operating system to experience new functions and interfaces. However, some users found that they were unable to install the Chinese language pack after upgrading, which troubled their experience. In this article, we will discuss the reasons why Win11 system cannot install the Chinese language pack and provide some solutions to help users solve this problem. Cause Analysis First, let us analyze the inability of Win11 system to
 Five tips to teach you how to solve the problem of Black Shark phone not turning on!
Mar 24, 2024 pm 12:27 PM
Five tips to teach you how to solve the problem of Black Shark phone not turning on!
Mar 24, 2024 pm 12:27 PM
As smartphone technology continues to develop, mobile phones play an increasingly important role in our daily lives. As a flagship phone focusing on gaming performance, the Black Shark phone is highly favored by players. However, sometimes we also face the situation that the Black Shark phone cannot be turned on. At this time, we need to take some measures to solve this problem. Next, let us share five tips to teach you how to solve the problem of Black Shark phone not turning on: Step 1: Check the battery power. First, make sure your Black Shark phone has enough power. It may be because the phone battery is exhausted
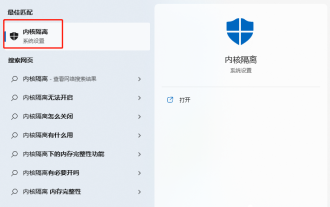 The driver cannot be loaded on this device. How to solve it? (Personally tested and valid)
Mar 14, 2024 pm 09:00 PM
The driver cannot be loaded on this device. How to solve it? (Personally tested and valid)
Mar 14, 2024 pm 09:00 PM
Everyone knows that if the computer cannot load the driver, the device may not work properly or interact with the computer correctly. So how do we solve the problem when a prompt box pops up on the computer that the driver cannot be loaded on this device? The editor below will teach you two ways to easily solve the problem. Unable to load the driver on this device Solution 1. Search for "Kernel Isolation" in the Start menu. 2. Turn off Memory Integrity, and it will prompt "Memory Integrity has been turned off. Your device may be vulnerable." Click behind to ignore it, and it will not affect the use. 3. The problem can be solved after restarting the machine.
 Ten limitations of artificial intelligence
Apr 26, 2024 pm 05:52 PM
Ten limitations of artificial intelligence
Apr 26, 2024 pm 05:52 PM
In the field of technological innovation, artificial intelligence (AI) is one of the most transformative and promising developments of our time. Artificial intelligence has revolutionized many industries, from healthcare and finance to transportation and entertainment, with its ability to analyze large amounts of data, learn from patterns, and make intelligent decisions. However, despite its remarkable progress, AI also faces significant limitations and challenges that prevent it from reaching its full potential. In this article, we will delve into the top ten limitations of artificial intelligence, revealing the limitations faced by developers, researchers, and practitioners in this field. By understanding these challenges, it is possible to navigate the complexities of AI development, reduce risks, and pave the way for responsible and ethical advancement of AI technology. Limited data availability: The development of artificial intelligence depends on data
 How to solve the problem of automatically saving pictures when publishing on Xiaohongshu? Where is the automatically saved image when posting?
Mar 22, 2024 am 08:06 AM
How to solve the problem of automatically saving pictures when publishing on Xiaohongshu? Where is the automatically saved image when posting?
Mar 22, 2024 am 08:06 AM
With the continuous development of social media, Xiaohongshu has become a platform for more and more young people to share their lives and discover beautiful things. Many users are troubled by auto-save issues when posting images. So, how to solve this problem? 1. How to solve the problem of automatically saving pictures when publishing on Xiaohongshu? 1. Clear the cache First, we can try to clear the cache data of Xiaohongshu. The steps are as follows: (1) Open Xiaohongshu and click the "My" button in the lower right corner; (2) On the personal center page, find "Settings" and click it; (3) Scroll down and find the "Clear Cache" option. Click OK. After clearing the cache, re-enter Xiaohongshu and try to post pictures to see if the automatic saving problem is solved. 2. Update the Xiaohongshu version to ensure that your Xiaohongshu
 How to solve Chinese garbled characters in Linux
Feb 21, 2024 am 10:48 AM
How to solve Chinese garbled characters in Linux
Feb 21, 2024 am 10:48 AM
The Linux Chinese garbled problem is a common problem when using Chinese character sets and encodings. Garbled characters may be caused by incorrect file encoding settings, system locale not being installed or set, and terminal display configuration errors, etc. This article will introduce several common workarounds and provide specific code examples. 1. Check the file encoding setting. Use the file command to view the file encoding. Use the file command in the terminal to view the encoding of the file: file-ifilename. If there is "charset" in the output
 Share the method to solve the problem that PyCharm cannot be opened
Feb 22, 2024 am 09:03 AM
Share the method to solve the problem that PyCharm cannot be opened
Feb 22, 2024 am 09:03 AM
Title: How to solve the problem that PyCharm cannot be opened. PyCharm is a powerful Python integrated development environment, but sometimes we may encounter the problem that PyCharm cannot be opened. In this article, we'll share some common workarounds and provide specific code examples. Hope this helps those who encounter this problem. Method 1: Clear the cache Sometimes PyCharm’s cache files may cause the program to fail to open normally. We can try clearing the cache to solve this problem. Tool
 How to solve the problem of default gateway automatically disappearing
Feb 24, 2024 pm 04:18 PM
How to solve the problem of default gateway automatically disappearing
Feb 24, 2024 pm 04:18 PM
How to solve the problem that the default gateway disappears automatically. In modern society, the Internet has become an indispensable part of people's lives. Whether for work or entertainment, we all need stable network connections to complete various tasks. The default gateway is one of the key elements connecting the local network to the external Internet. However, sometimes we may encounter the problem that the default gateway disappears automatically, resulting in the inability to access the Internet. So, how should we solve this problem when the default gateway disappears? First, we should clarify the concept of default gateway. The default gateway is a network route




