Introduction and comparison of firefly algorithm and metaheuristic solving algorithm
The firefly algorithm is a meta-heuristic optimization algorithm inspired by the flickering behavior of fireflies and is designed to solve continuous optimization problems.
Principle of Firefly Algorithm
In the firefly algorithm, the objective function is related to the light intensity at the tail of the firefly. In terms of optimization, the attraction and movement of fireflies can inspire algorithms, which can be followed to obtain optimal solutions.
In the firefly algorithm, fireflies refer to randomly generated feasible solutions. They are assigned a light intensity proportional to their functional value based on their performance in the objective function. For minimization problems, the solution with the smallest function value will be assigned the highest light intensity. Once the light intensities of the solution are distributed, each firefly will follow the firefly with the higher light intensity. The brightest firefly will perform a local search by randomly moving around it.
The algorithm mimics how fireflies interact using flash lights. Assume that all fireflies are opposite-sex attracted, which means that any firefly can attract all other fireflies. The attractiveness of a firefly is directly proportional to its brightness, which depends on the objective function. Brighter fireflies attract other fireflies. Furthermore, according to the inverse square law, brightness gradually decreases with distance.
Firefly Algorithm and Metaheuristic Solving Algorithm
Fireflies communicate using flickering properties, and there are approximately 2,000 unique flash patterns. They produce brief, patterned flashes of light.
This flashing pattern of communication is used to attract mates and warn predators. The right partner will communicate by imitating the same pattern or responding in a specific pattern. Therefore, a firefly's flash causes a reaction in nearby fireflies.
Natural selection and survival of the fittest are the core ideas of early metaheuristic algorithms. Due to the complexity of algorithm modeling, the implementation of deterministic solution methods is challenging, thus promoting the development of metaheuristic solution algorithms.
Metaheuristic algorithms are approximate solutions to optimization problems that use the properties of randomness to iterate and improve the quality of the solution from a set of randomly generated feasible solutions.
Although metaheuristic algorithms cannot guarantee optimality, they can be tested to give reasonable and acceptable solutions.
Additionally, metaheuristic algorithms have the advantage of being immune to problem behavior, which makes them useful in many application scenarios.
The above is the detailed content of Introduction and comparison of firefly algorithm and metaheuristic solving algorithm. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
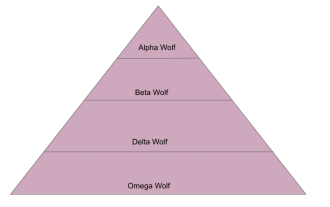 An in-depth analysis of the Gray Wolf Optimization Algorithm (GWO) and its strengths and weaknesses
Jan 19, 2024 pm 07:48 PM
An in-depth analysis of the Gray Wolf Optimization Algorithm (GWO) and its strengths and weaknesses
Jan 19, 2024 pm 07:48 PM
The Gray Wolf Optimization Algorithm (GWO) is a population-based metaheuristic algorithm that simulates the leadership hierarchy and hunting mechanism of gray wolves in nature. Gray Wolf Algorithm Inspiration 1. Gray wolves are considered to be apex predators and are at the top of the food chain. 2. Gray wolves like to live in groups (living in groups), with an average of 5-12 wolves in each pack. 3. Gray wolves have a very strict social dominance hierarchy, as shown below: Alpha wolf: Alpha wolf occupies a dominant position in the entire gray wolf group and has the right to command the entire gray wolf group. In the application of algorithms, Alpha Wolf is one of the best solutions, the optimal solution produced by the optimization algorithm. Beta wolf: Beta wolf reports to Alpha wolf regularly and helps Alpha wolf make the best decisions. In algorithm applications, Beta Wolf can
 Analyze the principles, models and composition of the Sparrow Search Algorithm (SSA)
Jan 19, 2024 pm 10:27 PM
Analyze the principles, models and composition of the Sparrow Search Algorithm (SSA)
Jan 19, 2024 pm 10:27 PM
The Sparrow Search Algorithm (SSA) is a meta-heuristic optimization algorithm based on the anti-predation and foraging behavior of sparrows. The foraging behavior of sparrows can be divided into two main types: producers and scavengers. Producers actively search for food, while scavengers compete for food from producers. Principle of Sparrow Search Algorithm (SSA) In Sparrow Search Algorithm (SSA), each sparrow pays close attention to the behavior of its neighbors. By employing different foraging strategies, individuals are able to efficiently use retained energy to pursue more food. Additionally, birds are more vulnerable to predators in their search space, so they need to find safer locations. Birds at the center of a colony can minimize their own range of danger by staying close to their neighbors. When a bird spots a predator, it makes an alarm call to
 Explore the basic principles and implementation process of nested sampling algorithms
Jan 22, 2024 pm 09:51 PM
Explore the basic principles and implementation process of nested sampling algorithms
Jan 22, 2024 pm 09:51 PM
The nested sampling algorithm is an efficient Bayesian statistical inference algorithm used to calculate the integral or summation under complex probability distributions. It works by decomposing the parameter space into multiple hypercubes of equal volume, and gradually and iteratively "pushing out" one of the smallest volume hypercubes, and then filling the hypercube with random samples to better estimate the integral value of the probability distribution. . Through continuous iteration, the nested sampling algorithm can obtain high-precision integral values and boundaries of parameter space, which can be applied to statistical problems such as model comparison, parameter estimation, and model selection. The core idea of this algorithm is to transform complex integration problems into a series of simple integration problems, and approach the real integral value by gradually reducing the volume of the parameter space. Each iteration step randomly samples from the parameter space
 What is the role of information gain in the id3 algorithm?
Jan 23, 2024 pm 11:27 PM
What is the role of information gain in the id3 algorithm?
Jan 23, 2024 pm 11:27 PM
The ID3 algorithm is one of the basic algorithms in decision tree learning. It selects the best split point by calculating the information gain of each feature to generate a decision tree. Information gain is an important concept in the ID3 algorithm, which is used to measure the contribution of features to the classification task. This article will introduce in detail the concept, calculation method and application of information gain in the ID3 algorithm. 1. The concept of information entropy Information entropy is a concept in information theory, which measures the uncertainty of random variables. For a discrete random variable number, and p(x_i) represents the probability that the random variable X takes the value x_i. letter
 Introduction to Wu-Manber algorithm and Python implementation instructions
Jan 23, 2024 pm 07:03 PM
Introduction to Wu-Manber algorithm and Python implementation instructions
Jan 23, 2024 pm 07:03 PM
The Wu-Manber algorithm is a string matching algorithm used to search strings efficiently. It is a hybrid algorithm that combines the advantages of Boyer-Moore and Knuth-Morris-Pratt algorithms to provide fast and accurate pattern matching. Wu-Manber algorithm step 1. Create a hash table that maps each possible substring of the pattern to the pattern position where that substring occurs. 2. This hash table is used to quickly identify potential starting locations of patterns in text. 3. Iterate through the text and compare each character to the corresponding character in the pattern. 4. If the characters match, you can move to the next character and continue the comparison. 5. If the characters do not match, you can use a hash table to determine the next potential character in the pattern.
 Numerical optimization principles and analysis of the Whale Optimization Algorithm (WOA)
Jan 19, 2024 pm 07:27 PM
Numerical optimization principles and analysis of the Whale Optimization Algorithm (WOA)
Jan 19, 2024 pm 07:27 PM
The Whale Optimization Algorithm (WOA) is a nature-inspired metaheuristic optimization algorithm that simulates the hunting behavior of humpback whales and is used for the optimization of numerical problems. The Whale Optimization Algorithm (WOA) starts with a set of random solutions and optimizes based on a randomly selected search agent or the best solution so far through position updates of the search agent in each iteration. Whale Optimization Algorithm Inspiration The Whale Optimization Algorithm is inspired by the hunting behavior of humpback whales. Humpback whales prefer food found near the surface, such as krill and schools of fish. Therefore, humpback whales gather food together to form a bubble network by blowing bubbles in a bottom-up spiral when hunting. In an "upward spiral" maneuver, the humpback whale dives about 12m, then begins to form a spiral bubble around its prey and swims upward
 Scale Invariant Features (SIFT) algorithm
Jan 22, 2024 pm 05:09 PM
Scale Invariant Features (SIFT) algorithm
Jan 22, 2024 pm 05:09 PM
The Scale Invariant Feature Transform (SIFT) algorithm is a feature extraction algorithm used in the fields of image processing and computer vision. This algorithm was proposed in 1999 to improve object recognition and matching performance in computer vision systems. The SIFT algorithm is robust and accurate and is widely used in image recognition, three-dimensional reconstruction, target detection, video tracking and other fields. It achieves scale invariance by detecting key points in multiple scale spaces and extracting local feature descriptors around the key points. The main steps of the SIFT algorithm include scale space construction, key point detection, key point positioning, direction assignment and feature descriptor generation. Through these steps, the SIFT algorithm can extract robust and unique features, thereby achieving efficient image processing.
 Explore the concepts of Bayesian methods and Bayesian networks in depth
Jan 24, 2024 pm 01:06 PM
Explore the concepts of Bayesian methods and Bayesian networks in depth
Jan 24, 2024 pm 01:06 PM
The concept of Bayesian method Bayesian method is a statistical inference theorem mainly used in the field of machine learning. It performs tasks such as parameter estimation, model selection, model averaging and prediction by combining prior knowledge with observation data. Bayesian methods are unique in their ability to flexibly handle uncertainty and improve the learning process by continuously updating prior knowledge. This method is particularly effective when dealing with small sample problems and complex models, and can provide more accurate and robust inference results. Bayesian methods are based on Bayes' theorem, which states that the probability of a hypothesis given some evidence is equal to the probability of the evidence multiplied by the prior probability. This can be written as: P(H|E)=P(E|H)P(H) where P(H|E) is the posterior probability of hypothesis H given evidence E, P(





