 Technology peripherals
Technology peripherals
 AI
AI
 Comparative analysis of the effects of face detection and blur algorithms
Comparative analysis of the effects of face detection and blur algorithms
Comparative analysis of the effects of face detection and blur algorithms

Face detection and fuzzy algorithms are important research directions in the field of computer vision and are widely used in face recognition, image processing, security monitoring and other fields. The goal of face detection algorithms is to accurately detect face areas from images or videos, while blurring algorithms protect privacy by blurring specific areas in images or videos. This article aims to compare and analyze these two algorithms so that readers can fully understand their characteristics and applications. The face detection algorithm mainly determines whether there is a face by analyzing the color, texture, edge and other features in the image, and can distinguish the face from other objects. Commonly used face detection algorithms include Viola-Jones algorithm, Haar feature detection, convolutional neural network based on deep learning, etc. These algorithms can quickly and accurately locate face areas in complex image environments, providing a basis for subsequent face recognition and
1. Face detection algorithm
1. Definition and Principle
Face detection algorithm is a technology used to detect the location of faces in images or videos. Currently commonly used methods are based on features, statistics and deep learning. Feature-based methods achieve face detection by extracting features from images. The statistics-based method establishes a statistical model and uses probability distribution to determine whether it is a human face. Methods based on deep learning use deep neural networks to achieve accurate face detection by training models. Through these algorithms, we can quickly and efficiently find the location of a face in an image or video.
2. Application fields
Face detection algorithms are used in the fields of face recognition, expression analysis, face tracking, human-computer interaction, etc. widely used. It can be used in face recognition access control systems, social media applications, video surveillance systems and other scenarios.
3. Comparative analysis
(1) Accuracy: The accuracy of the face detection algorithm is one of the important indicators to evaluate its performance . Deep learning-based methods often achieve higher accuracy because deep neural networks can learn richer feature representations. Statistics-based methods and feature-based methods may have certain accuracy limitations in complex scenarios.
(2) Efficiency: The efficiency of the face detection algorithm involves the running speed and resource consumption of the algorithm. Feature-based methods usually have faster speed and lower computational resource requirements, making them suitable for real-time applications. However, methods based on deep learning may require higher computing resources and time costs due to their more complex network structures.
(3) Robustness: The robustness of the face detection algorithm refers to its ability to adapt to interference factors such as lighting changes, posture changes, and occlusion. Methods based on deep learning usually have good robustness and can cope with complex scene changes. However, statistical-based methods and feature-based methods may not perform well when facing complex environments.
(4) Privacy protection: The protection of personal privacy needs to be considered in the application of face detection algorithms. Some algorithms may obtain specific feature information of the face after detecting the face, which may lead to the risk of privacy leakage. Therefore, privacy protection is an aspect that needs to be paid attention to in face detection algorithms.
2. Fuzzy algorithm
1. Definition and principle
Fuzzy algorithm is a Technology that blurs specific areas in an image or video to protect private information. Common blur algorithms include Gaussian blur, mosaic blur and motion blur.
2. Application fields
Fuzzy algorithm is mainly used in the field of privacy protection, such as sensitive information such as faces and license plates in surveillance videos Obfuscated to protect personal privacy.
3. Comparative analysis
(1) Accuracy: Compared with the face detection algorithm, the accuracy requirements of the fuzzy algorithm are relatively low Low. The blur algorithm mainly focuses on blurring sensitive areas without accurately locating and identifying faces.
(2) Efficiency: Fuzzy algorithms usually have high computational efficiency and can perform real-time blur processing in real-time scenarios. Compared with deep learning-based face detection algorithms, fuzzy algorithms have lower computational resource requirements.
(3) Robustness: The fuzzy algorithm is more robust to factors such as lighting changes and posture changes. It can blur sensitive areas to a certain extent to protect privacy. .
(4) Privacy protection: As a means of privacy protection, fuzzy algorithm can effectively blur sensitive information and reduce the risk of privacy leakage. However, obfuscation algorithms may not be able to completely eliminate sensitive information, so in some scenarios with high security requirements, other privacy protection measures may need to be combined.
in conclusion
Face detection algorithms and fuzzy algorithms have different characteristics in terms of accuracy, efficiency, robustness and privacy protection. Face detection algorithms have high accuracy and robustness in areas such as face recognition, but may require higher computing resources. Fuzzy algorithm is mainly used for privacy protection and has high efficiency and robustness. According to the needs of specific application scenarios, you can choose an appropriate algorithm or combine the two algorithms to achieve better results.
The above is the detailed content of Comparative analysis of the effects of face detection and blur algorithms. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1392
1392
 52
52
 Bytedance Cutting launches SVIP super membership: 499 yuan for continuous annual subscription, providing a variety of AI functions
Jun 28, 2024 am 03:51 AM
Bytedance Cutting launches SVIP super membership: 499 yuan for continuous annual subscription, providing a variety of AI functions
Jun 28, 2024 am 03:51 AM
This site reported on June 27 that Jianying is a video editing software developed by FaceMeng Technology, a subsidiary of ByteDance. It relies on the Douyin platform and basically produces short video content for users of the platform. It is compatible with iOS, Android, and Windows. , MacOS and other operating systems. Jianying officially announced the upgrade of its membership system and launched a new SVIP, which includes a variety of AI black technologies, such as intelligent translation, intelligent highlighting, intelligent packaging, digital human synthesis, etc. In terms of price, the monthly fee for clipping SVIP is 79 yuan, the annual fee is 599 yuan (note on this site: equivalent to 49.9 yuan per month), the continuous monthly subscription is 59 yuan per month, and the continuous annual subscription is 499 yuan per year (equivalent to 41.6 yuan per month) . In addition, the cut official also stated that in order to improve the user experience, those who have subscribed to the original VIP
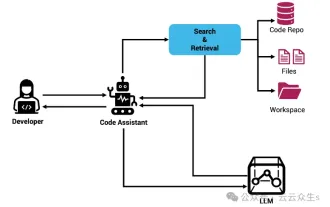 Context-augmented AI coding assistant using Rag and Sem-Rag
Jun 10, 2024 am 11:08 AM
Context-augmented AI coding assistant using Rag and Sem-Rag
Jun 10, 2024 am 11:08 AM
Improve developer productivity, efficiency, and accuracy by incorporating retrieval-enhanced generation and semantic memory into AI coding assistants. Translated from EnhancingAICodingAssistantswithContextUsingRAGandSEM-RAG, author JanakiramMSV. While basic AI programming assistants are naturally helpful, they often fail to provide the most relevant and correct code suggestions because they rely on a general understanding of the software language and the most common patterns of writing software. The code generated by these coding assistants is suitable for solving the problems they are responsible for solving, but often does not conform to the coding standards, conventions and styles of the individual teams. This often results in suggestions that need to be modified or refined in order for the code to be accepted into the application
 Can fine-tuning really allow LLM to learn new things: introducing new knowledge may make the model produce more hallucinations
Jun 11, 2024 pm 03:57 PM
Can fine-tuning really allow LLM to learn new things: introducing new knowledge may make the model produce more hallucinations
Jun 11, 2024 pm 03:57 PM
Large Language Models (LLMs) are trained on huge text databases, where they acquire large amounts of real-world knowledge. This knowledge is embedded into their parameters and can then be used when needed. The knowledge of these models is "reified" at the end of training. At the end of pre-training, the model actually stops learning. Align or fine-tune the model to learn how to leverage this knowledge and respond more naturally to user questions. But sometimes model knowledge is not enough, and although the model can access external content through RAG, it is considered beneficial to adapt the model to new domains through fine-tuning. This fine-tuning is performed using input from human annotators or other LLM creations, where the model encounters additional real-world knowledge and integrates it
 Seven Cool GenAI & LLM Technical Interview Questions
Jun 07, 2024 am 10:06 AM
Seven Cool GenAI & LLM Technical Interview Questions
Jun 07, 2024 am 10:06 AM
To learn more about AIGC, please visit: 51CTOAI.x Community https://www.51cto.com/aigc/Translator|Jingyan Reviewer|Chonglou is different from the traditional question bank that can be seen everywhere on the Internet. These questions It requires thinking outside the box. Large Language Models (LLMs) are increasingly important in the fields of data science, generative artificial intelligence (GenAI), and artificial intelligence. These complex algorithms enhance human skills and drive efficiency and innovation in many industries, becoming the key for companies to remain competitive. LLM has a wide range of applications. It can be used in fields such as natural language processing, text generation, speech recognition and recommendation systems. By learning from large amounts of data, LLM is able to generate text
 Five schools of machine learning you don't know about
Jun 05, 2024 pm 08:51 PM
Five schools of machine learning you don't know about
Jun 05, 2024 pm 08:51 PM
Machine learning is an important branch of artificial intelligence that gives computers the ability to learn from data and improve their capabilities without being explicitly programmed. Machine learning has a wide range of applications in various fields, from image recognition and natural language processing to recommendation systems and fraud detection, and it is changing the way we live. There are many different methods and theories in the field of machine learning, among which the five most influential methods are called the "Five Schools of Machine Learning". The five major schools are the symbolic school, the connectionist school, the evolutionary school, the Bayesian school and the analogy school. 1. Symbolism, also known as symbolism, emphasizes the use of symbols for logical reasoning and expression of knowledge. This school of thought believes that learning is a process of reverse deduction, through existing
 To provide a new scientific and complex question answering benchmark and evaluation system for large models, UNSW, Argonne, University of Chicago and other institutions jointly launched the SciQAG framework
Jul 25, 2024 am 06:42 AM
To provide a new scientific and complex question answering benchmark and evaluation system for large models, UNSW, Argonne, University of Chicago and other institutions jointly launched the SciQAG framework
Jul 25, 2024 am 06:42 AM
Editor |ScienceAI Question Answering (QA) data set plays a vital role in promoting natural language processing (NLP) research. High-quality QA data sets can not only be used to fine-tune models, but also effectively evaluate the capabilities of large language models (LLM), especially the ability to understand and reason about scientific knowledge. Although there are currently many scientific QA data sets covering medicine, chemistry, biology and other fields, these data sets still have some shortcomings. First, the data form is relatively simple, most of which are multiple-choice questions. They are easy to evaluate, but limit the model's answer selection range and cannot fully test the model's ability to answer scientific questions. In contrast, open-ended Q&A
 SOTA performance, Xiamen multi-modal protein-ligand affinity prediction AI method, combines molecular surface information for the first time
Jul 17, 2024 pm 06:37 PM
SOTA performance, Xiamen multi-modal protein-ligand affinity prediction AI method, combines molecular surface information for the first time
Jul 17, 2024 pm 06:37 PM
Editor | KX In the field of drug research and development, accurately and effectively predicting the binding affinity of proteins and ligands is crucial for drug screening and optimization. However, current studies do not take into account the important role of molecular surface information in protein-ligand interactions. Based on this, researchers from Xiamen University proposed a novel multi-modal feature extraction (MFE) framework, which for the first time combines information on protein surface, 3D structure and sequence, and uses a cross-attention mechanism to compare different modalities. feature alignment. Experimental results demonstrate that this method achieves state-of-the-art performance in predicting protein-ligand binding affinities. Furthermore, ablation studies demonstrate the effectiveness and necessity of protein surface information and multimodal feature alignment within this framework. Related research begins with "S
 SK Hynix will display new AI-related products on August 6: 12-layer HBM3E, 321-high NAND, etc.
Aug 01, 2024 pm 09:40 PM
SK Hynix will display new AI-related products on August 6: 12-layer HBM3E, 321-high NAND, etc.
Aug 01, 2024 pm 09:40 PM
According to news from this site on August 1, SK Hynix released a blog post today (August 1), announcing that it will attend the Global Semiconductor Memory Summit FMS2024 to be held in Santa Clara, California, USA from August 6 to 8, showcasing many new technologies. generation product. Introduction to the Future Memory and Storage Summit (FutureMemoryandStorage), formerly the Flash Memory Summit (FlashMemorySummit) mainly for NAND suppliers, in the context of increasing attention to artificial intelligence technology, this year was renamed the Future Memory and Storage Summit (FutureMemoryandStorage) to invite DRAM and storage vendors and many more players. New product SK hynix launched last year



