 Technology peripherals
Technology peripherals
 AI
AI
 Implementation of personalized recommendation system based on Transformer model
Implementation of personalized recommendation system based on Transformer model
Implementation of personalized recommendation system based on Transformer model

Personalized recommendation based on Transformer is a personalized recommendation method implemented using the Transformer model. Transformer is a neural network model based on the attention mechanism, which is widely used in natural language processing tasks, such as machine translation and text generation. In personalized recommendations, Transformer can learn the user's interests and preferences and recommend relevant content to the user based on this information. Through the attention mechanism, Transformer is able to capture the relationship between the user's interests and related content, thereby improving the accuracy and effectiveness of recommendations. By using the Transformer model, the personalized recommendation system can better understand the needs of users and provide users with more personalized and accurate recommendation services.
In personalized recommendations, you first need to establish an interaction matrix between users and items. This matrix records user behavior toward items, such as ratings, clicks, or purchases. Next, we need to convert this interaction information into vector form and input it into the Transformer model for training. In this way, the model can learn the relationship between users and items and generate personalized recommendation results. In this way, we can improve the accuracy and user satisfaction of the recommendation system.
The Transformer model in personalized recommendation usually includes an encoder and a decoder. The encoder is used to learn vector representations of users and items, and the decoder is used to predict the user's interest in other items. This architecture can effectively capture the complex relationships between users and items, thereby improving the accuracy and personalization of recommendations.
In the encoder, a multi-layer self-attention mechanism is first used to interact with the vector representations of users and items. The self-attention mechanism allows the model to learn more efficient vector representations by weighting them according to the importance of different positions in the input sequence. Next, the output of the attention mechanism is processed through a feedforward neural network to obtain the final vector representation. This method can help the model better capture the correlation information between users and items and improve the performance of the recommendation system.
In the decoder, we can use the user vector and item vector to predict the user's interest in other items. To calculate the similarity between users and items, we can use the dot product attention mechanism. By calculating the attention score, we can evaluate the correlation between the user and the item and use it as a basis for predicting the level of interest. Finally, we can rank items based on predicted interest and recommend them to users. This approach can improve the accuracy and personalization of recommendation systems.
To implement personalized recommendations based on Transformer, you need to pay attention to the following points:
1. Data preparation: collect interaction data between users and items, and build an interaction matrix. This matrix records the interaction between users and items, which can include information such as ratings, clicks, and purchases.
2. Feature representation: Convert users and items in the interaction matrix into vector representations. Embedding technology can be used to map users and items into a low-dimensional space and serve as input to the model.
3. Model construction: Build an encoder-decoder model based on Transformer. The encoder learns vector representations of users and items through a multi-layer self-attention mechanism, and the decoder uses user and item vectors to predict the user's interest in other items.
4. Model training: Use the interaction data between users and items as a training set to train the model by minimizing the gap between the predicted results and the real ratings. Optimization algorithms such as gradient descent can be used to update model parameters.
5. Recommendation generation: Based on the trained model, predict and rank items that the user has not interacted with, and recommend items with high interest to the user.
In practical applications, personalized recommendations based on Transformer have the following advantages:
- The model can fully consider the relationship between users and items The interactive relationship between them can capture richer semantic information.
- The Transformer model has good scalability and parallelism and can handle large-scale data sets and high concurrent requests.
- The model can automatically learn feature representations, reducing the need for manual feature engineering.
However, Transformer-based personalized recommendations also face some challenges:
- Data sparsity: In real scenarios, the interaction data between users and items is often sparse. Since users have only interacted with a small number of items, there are a large number of missing values in the data, which makes model learning and prediction difficult.
- Cold start problem: When new users or new items join the system, their interests and preferences cannot be accurately captured due to the lack of sufficient interaction data. This requires solving the cold start problem and providing recommendations for new users and new items through other methods (such as content-based recommendations, collaborative filtering, etc.).
- Diversity and long-tail problems: Personalized recommendations often face the problem of pursuing popular items, resulting in a lack of diversity in recommendation results and neglecting long-tail items. The Transformer model may be more likely to capture the correlation between popular items during the learning process, but the recommendation effect for long-tail items is poor.
- Interpretability and interpretability: As a black box model, the Transformer model’s prediction results are often difficult to explain. In some application scenarios, users want to understand why such recommendation results are obtained, and the model needs to have certain explanation capabilities.
- Real-time and efficiency: Transformer-based models usually have large network structures and parameter quantities, and require high computing resources. In real-time recommendation scenarios, personalized recommendation results need to be generated quickly, and the traditional Transformer model may have high computational complexity and latency.
The above is the detailed content of Implementation of personalized recommendation system based on Transformer model. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1382
1382
 52
52
 Explore the concepts, differences, advantages and disadvantages of RNN, LSTM and GRU
Jan 22, 2024 pm 07:51 PM
Explore the concepts, differences, advantages and disadvantages of RNN, LSTM and GRU
Jan 22, 2024 pm 07:51 PM
In time series data, there are dependencies between observations, so they are not independent of each other. However, traditional neural networks treat each observation as independent, which limits the model's ability to model time series data. To solve this problem, Recurrent Neural Network (RNN) was introduced, which introduced the concept of memory to capture the dynamic characteristics of time series data by establishing dependencies between data points in the network. Through recurrent connections, RNN can pass previous information into the current observation to better predict future values. This makes RNN a powerful tool for tasks involving time series data. But how does RNN achieve this kind of memory? RNN realizes memory through the feedback loop in the neural network. This is the difference between RNN and traditional neural network.
 Calculating floating point operands (FLOPS) for neural networks
Jan 22, 2024 pm 07:21 PM
Calculating floating point operands (FLOPS) for neural networks
Jan 22, 2024 pm 07:21 PM
FLOPS is one of the standards for computer performance evaluation, used to measure the number of floating point operations per second. In neural networks, FLOPS is often used to evaluate the computational complexity of the model and the utilization of computing resources. It is an important indicator used to measure the computing power and efficiency of a computer. A neural network is a complex model composed of multiple layers of neurons used for tasks such as data classification, regression, and clustering. Training and inference of neural networks requires a large number of matrix multiplications, convolutions and other calculation operations, so the computational complexity is very high. FLOPS (FloatingPointOperationsperSecond) can be used to measure the computational complexity of neural networks to evaluate the computational resource usage efficiency of the model. FLOP
 A case study of using bidirectional LSTM model for text classification
Jan 24, 2024 am 10:36 AM
A case study of using bidirectional LSTM model for text classification
Jan 24, 2024 am 10:36 AM
The bidirectional LSTM model is a neural network used for text classification. Below is a simple example demonstrating how to use bidirectional LSTM for text classification tasks. First, we need to import the required libraries and modules: importosimportnumpyasnpfromkeras.preprocessing.textimportTokenizerfromkeras.preprocessing.sequenceimportpad_sequencesfromkeras.modelsimportSequentialfromkeras.layersimportDense,Em
 Definition and structural analysis of fuzzy neural network
Jan 22, 2024 pm 09:09 PM
Definition and structural analysis of fuzzy neural network
Jan 22, 2024 pm 09:09 PM
Fuzzy neural network is a hybrid model that combines fuzzy logic and neural networks to solve fuzzy or uncertain problems that are difficult to handle with traditional neural networks. Its design is inspired by the fuzziness and uncertainty in human cognition, so it is widely used in control systems, pattern recognition, data mining and other fields. The basic architecture of fuzzy neural network consists of fuzzy subsystem and neural subsystem. The fuzzy subsystem uses fuzzy logic to process input data and convert it into fuzzy sets to express the fuzziness and uncertainty of the input data. The neural subsystem uses neural networks to process fuzzy sets for tasks such as classification, regression or clustering. The interaction between the fuzzy subsystem and the neural subsystem makes the fuzzy neural network have more powerful processing capabilities and can
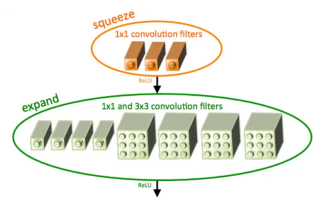 Introduction to SqueezeNet and its characteristics
Jan 22, 2024 pm 07:15 PM
Introduction to SqueezeNet and its characteristics
Jan 22, 2024 pm 07:15 PM
SqueezeNet is a small and precise algorithm that strikes a good balance between high accuracy and low complexity, making it ideal for mobile and embedded systems with limited resources. In 2016, researchers from DeepScale, University of California, Berkeley, and Stanford University proposed SqueezeNet, a compact and efficient convolutional neural network (CNN). In recent years, researchers have made several improvements to SqueezeNet, including SqueezeNetv1.1 and SqueezeNetv2.0. Improvements in both versions not only increase accuracy but also reduce computational costs. Accuracy of SqueezeNetv1.1 on ImageNet dataset
 Image denoising using convolutional neural networks
Jan 23, 2024 pm 11:48 PM
Image denoising using convolutional neural networks
Jan 23, 2024 pm 11:48 PM
Convolutional neural networks perform well in image denoising tasks. It utilizes the learned filters to filter the noise and thereby restore the original image. This article introduces in detail the image denoising method based on convolutional neural network. 1. Overview of Convolutional Neural Network Convolutional neural network is a deep learning algorithm that uses a combination of multiple convolutional layers, pooling layers and fully connected layers to learn and classify image features. In the convolutional layer, the local features of the image are extracted through convolution operations, thereby capturing the spatial correlation in the image. The pooling layer reduces the amount of calculation by reducing the feature dimension and retains the main features. The fully connected layer is responsible for mapping learned features and labels to implement image classification or other tasks. The design of this network structure makes convolutional neural networks useful in image processing and recognition.
 Steps to write a simple neural network using Rust
Jan 23, 2024 am 10:45 AM
Steps to write a simple neural network using Rust
Jan 23, 2024 am 10:45 AM
Rust is a systems-level programming language focused on safety, performance, and concurrency. It aims to provide a safe and reliable programming language suitable for scenarios such as operating systems, network applications, and embedded systems. Rust's security comes primarily from two aspects: the ownership system and the borrow checker. The ownership system enables the compiler to check code for memory errors at compile time, thus avoiding common memory safety issues. By forcing checking of variable ownership transfers at compile time, Rust ensures that memory resources are properly managed and released. The borrow checker analyzes the life cycle of the variable to ensure that the same variable will not be accessed by multiple threads at the same time, thereby avoiding common concurrency security issues. By combining these two mechanisms, Rust is able to provide
 Twin Neural Network: Principle and Application Analysis
Jan 24, 2024 pm 04:18 PM
Twin Neural Network: Principle and Application Analysis
Jan 24, 2024 pm 04:18 PM
Siamese Neural Network is a unique artificial neural network structure. It consists of two identical neural networks that share the same parameters and weights. At the same time, the two networks also share the same input data. This design was inspired by twins, as the two neural networks are structurally identical. The principle of Siamese neural network is to complete specific tasks, such as image matching, text matching and face recognition, by comparing the similarity or distance between two input data. During training, the network attempts to map similar data to adjacent regions and dissimilar data to distant regions. In this way, the network can learn how to classify or match different data to achieve corresponding



