What are the more common data encryption algorithms?
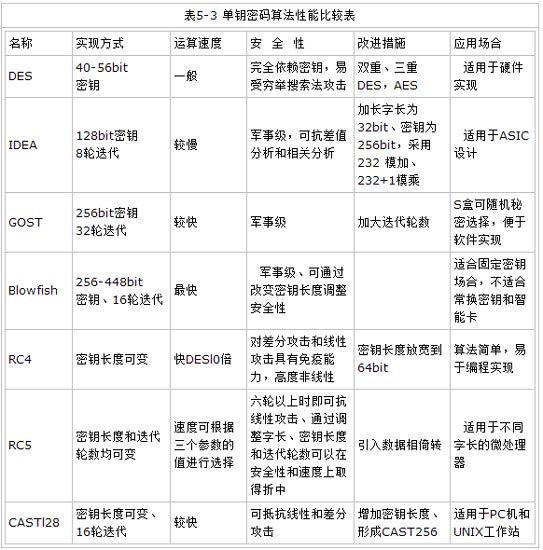
Comparison of several commonly used data encryption algorithms
Several symmetric encryption algorithms: AES, DES, 3DES
DES is a high-speed packet data encryption technology that divides data into small data blocks of fixed length and then encrypts each data block. 3DES is an encryption algorithm based on DES. By encrypting the same data block three times and using different keys, the strength of the ciphertext is improved. This encryption algorithm is suitable for scenarios where large amounts of data need to be encrypted because it is faster.
Compared with DES and 3DES algorithms, the AES algorithm has higher speed and resource efficiency, and also provides a higher level of security, so it is widely recognized as the next generation encryption standard.
Several asymmetric encryption algorithms: RSA, DSA, ECC
RSA and DSA have similar security and performance, while ECC has significant advantages in processing speed, bandwidth, storage space, etc.
Several linear hashing algorithms (signature algorithms): MD5, SHA1, HMAC
These algorithms only generate a string of irreversible ciphertext, which is used to verify whether the data has been modified during the transmission process. Since the same generation algorithm will only generate a unique ciphertext for the same plaintext, if the ciphertext generated by the same algorithm is different, it proves that the transmission data has been modified. Usually during data transmission, the use of MD5 and SHA1 algorithms requires both parties sending and receiving data to know the key generation algorithm before transmission. The difference is that the HMAC algorithm needs to generate a key. The sender uses this key to digest the data (generates ciphertext). The receiver then uses this key to digest the received data and determines the generated ciphertexts are the same. Therefore, the HMAC algorithm provides higher security and confidentiality.
For the selection of various encryption algorithms:
Due to the complexity of key management in symmetric encryption algorithms, key management directly determines security. Therefore, for small data volumes, consider using asymmetric encryption algorithms.
In the actual operation process, the usual method is to use an asymmetric encryption algorithm to manage the key of a symmetric algorithm, and use a symmetric encryption algorithm to encrypt data. This approach combines the advantages of two types of encryption algorithms, which can not only achieve faster encryption speed, but also facilitate and secure key management.
If the encryption algorithm is selected, how many bits of the key will be used? Generally speaking, the longer the key, the slower it runs. It should be selected according to the security level we actually need. Generally speaking, RSA recommends using 1024-bit numbers, ECC recommends using 160-bit numbers, and AES uses 128-bit numbers. That’s it.
Summarize what encryption algorithm technologies are available in PHP
1. MD5 encryption
string md5 ( string $str [, bool $raw_output = false ] )
2. Crype encryption
string crypt ( string $str [, string $salt ] )
crypt() Returns a hashed string based on the standard UNIX DES algorithm or another alternative algorithm available on the system.
3. Sha1 encryption
string sha1 ( string $str [, bool $raw_output = false ] )
4. URL encryption
string urlencode (string $str)
5. base64
string base64_encode ( string $data )
The above is the detailed content of What are the more common data encryption algorithms?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Discover How to Fix Drive Health Warning in Windows Settings
Mar 19, 2025 am 11:10 AM
Discover How to Fix Drive Health Warning in Windows Settings
Mar 19, 2025 am 11:10 AM
What does the drive health warning in Windows Settings mean and what should you do when you receive the disk warning? Read this php.cn tutorial to get step-by-step instructions to cope with this situation.
 How do I edit the Registry? (Warning: Use with caution!)
Mar 21, 2025 pm 07:46 PM
How do I edit the Registry? (Warning: Use with caution!)
Mar 21, 2025 pm 07:46 PM
Article discusses editing Windows Registry, precautions, backup methods, and potential issues from incorrect edits. Main issue: risks of system instability and data loss from improper changes.
 How do I manage services in Windows?
Mar 21, 2025 pm 07:52 PM
How do I manage services in Windows?
Mar 21, 2025 pm 07:52 PM
Article discusses managing Windows services for system health, including starting, stopping, restarting services, and best practices for stability.
 How do I change the default app for a file type?
Mar 21, 2025 pm 07:48 PM
How do I change the default app for a file type?
Mar 21, 2025 pm 07:48 PM
Article discusses changing default apps for file types on Windows, including reverting and bulk changes. Main issue: no built-in bulk change option.
 Windows Metadata and Internet Services Problem: How to Fix It?
Apr 02, 2025 pm 03:57 PM
Windows Metadata and Internet Services Problem: How to Fix It?
Apr 02, 2025 pm 03:57 PM
You may see the “A connection to the Windows Metadata and Internet Services (WMIS) could not be established.” error on Event Viewer. This post from php.cn introduces how to remove the Windows Metadata and Internet Services problem.
 How to Fix the Steam Cloud Error? Try These Methods
Apr 04, 2025 am 01:51 AM
How to Fix the Steam Cloud Error? Try These Methods
Apr 04, 2025 am 01:51 AM
The Steam Cloud error can be caused by many reasons. To play a game smoothly, you need to take some measures to remove this error before you launch the game. php.cn Software introduces some best ways as well as more useful information in this post.
 How do I use the Group Policy Editor (gpedit.msc)?
Mar 21, 2025 pm 07:48 PM
How do I use the Group Policy Editor (gpedit.msc)?
Mar 21, 2025 pm 07:48 PM
The article explains how to use the Group Policy Editor (gpedit.msc) in Windows for managing system settings, highlighting common configurations and troubleshooting methods. It notes that gpedit.msc is unavailable in Windows Home editions, suggesting
 How to Resolve the KB5035942 Update Issues – Crashing System
Apr 02, 2025 pm 04:16 PM
How to Resolve the KB5035942 Update Issues – Crashing System
Apr 02, 2025 pm 04:16 PM
KB5035942 update issues - crashing system commonly happens to users. Inflicted people hope to find a way out of the kind of trouble, such as crashing system, installation, or sound issues. Targeting these situations, this post published by php.cn wil




