Understand the architecture of Oracle12.2: file system and multi-tenancy
- RVWR: Recovery Writer Process. When the database sets up a flashback area, the process regularly writes the flashback data in the memory, specifically the flashback buffer in the shared pool, to flashback. logs.
- Result cache –> RCBG:result cache is used to store the results of the original data operation during the execution of the SQL statement or plsql function. When the database performs the same operation on the same object again Operations can directly obtain results, avoiding waste of computing resources.
- ASH buffer–>MMNL: ASH buffer is used to store statistical information of active sessions, including SQL execution status, application connection status, waiting events, etc. When the ASH buffer is full, the MMNL process is responsible for writing the data in the buffer to disk.
- In memory undo (IMU): Open an area in the shared pool to store temporary undo. If multiple pieces of data are modified in a transaction, the undo data block in the buffer Cache will not be modified, but It is to add IMU nodes for recording. Mainly to reduce the Redo generated by undo.
- Private Redo log buffers: Mainly used to manage the temporary Redo generated by the IMU, store the Redo information of the transaction in the shared pool, and reduce the consumption of Redo log buffer.
- Flash Cache: The full name is Database smart flash Cache, which is an optimization technology for flash memory developed from 11.2. It aims to store some data by using flash memory instead of traditional slow disk devices. To achieve the purpose of reducing the overall delay of the database, improving the IOPS of the database, and improving the performance of the database.
Flash Cache works as follows:
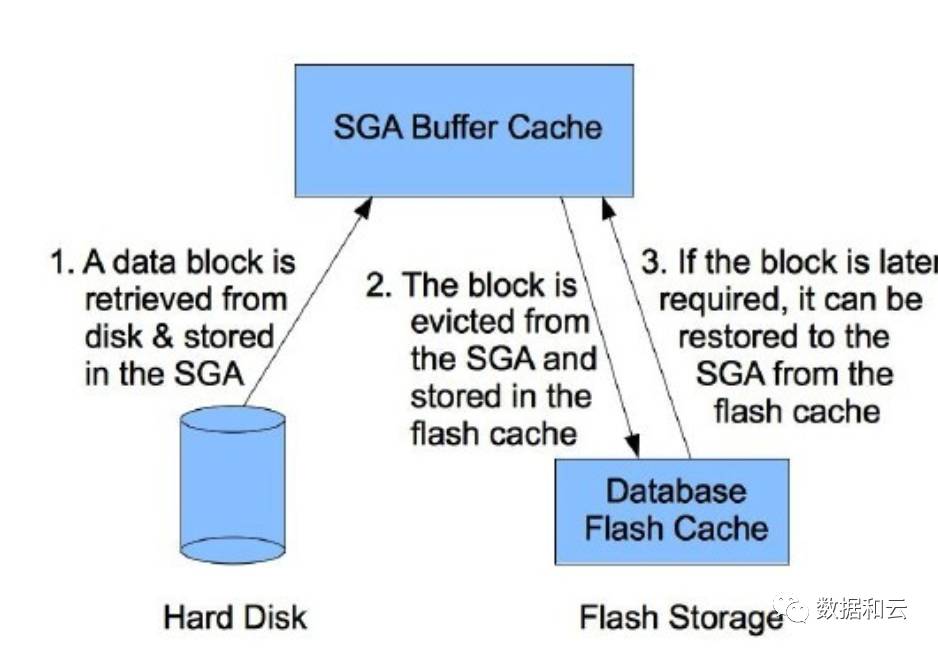
The content stored in Flash Cache is controlled in two ways:
1. Flash Cache’s intelligent selection algorithm: determine by evaluating the frequency of access of data blocks and index blocks.
2. Modify the cell_flash_cache attribute of the database object.
Flash Cache storage content basic standards
Mainly small IO operations, as well as data blocks, index blocks, file headers, control files, etc. will be cached;
For RMAN backup IO operations, data pump IO operations, ASM mirroring operations, table space formatting, etc. will not be cached;
The cache priority of IO operations for full table scans is relatively low.
When data is stored in the flash Cache, it is mainly to improve the query speed. In other words, it is equivalent to adding a part of the buffer Cache area in addition to the memory, but the performance is better and the speed is better. Then, just like the buffer Cache, when the data in the flash Cache is full or written to a certain extent, the data needs to be written to the disk to leave space for new operation data.
Writing data in the cache to disk is called flushing. You can configure the Starting and stopping cache flushing levels value, which represents the percentage of the entire cache size occupied. When the data in the cache that has not been written to the disk reaches the starting flushing value, the controller starts flushing (written from the cache to the disk). When the amount of unwritten disk data in the cache is lower than the stop flush value, the flushing process stops.
If the start flushing level is set higher, more unwritten data can be cached in the memory. This helps improve the performance of write operations, but at the expense of data protection. If you want to get data protection, you can use lower start and stop values. Testing shows that the performance is better when using close start and stop flushing levels. If the stop level value is much lower than the start value, disk congestion will occur during flushing
Smart Flash LoggingFor a long time, the IO bottleneck of Redo log has been a major problem that has plagued the OLTP system, because the write delay of Redo directly drags down the response speed of the entire system and even the entire cluster.
In the traditional database architecture, some DBAs will separately allocate small block storage with low read and write latency to Redo. Starting from 11204, Oracle has proposed a new solution to specifically provide Redo in the flash memory area. Create an area to store temporary redo.
Place column storage in Flash Cache to improve write IO for frequently operated column storage objects
- Change Tracking File:Detect block changes in incremental backup and record them to the file. The recording unit is block.
- wallet: Oracle Wallet is a container used to store keys. To put it simply, it is a password box. Through this password box, you can use it without entering a password in situations that originally required entering a password, thereby protecting sensitive information such as account passwords, improving security, and making it more convenient to use.
Application Container is a new component proposed in 12.2. It divides the database system under the same application into a sub-container to achieve relative business isolation and data security while ensuring the same management of multi-tenants.
PDB has its own undo table spaceStarting from 12.2, each PDB has its own undo tablespace. This eliminates contention between multiple PDBs. If you want to perform flashback or timestamp-based recovery, you only need to search in your own undo data to improve efficiency.
Flexible creation method of PDB1. Create from PDB$seed (or application root): by copying files
2. The existing PDB is created through hot clone
Note: In 12.1, when creating a new PDB based on a PDB, the original library needs to be opened in read only mode.
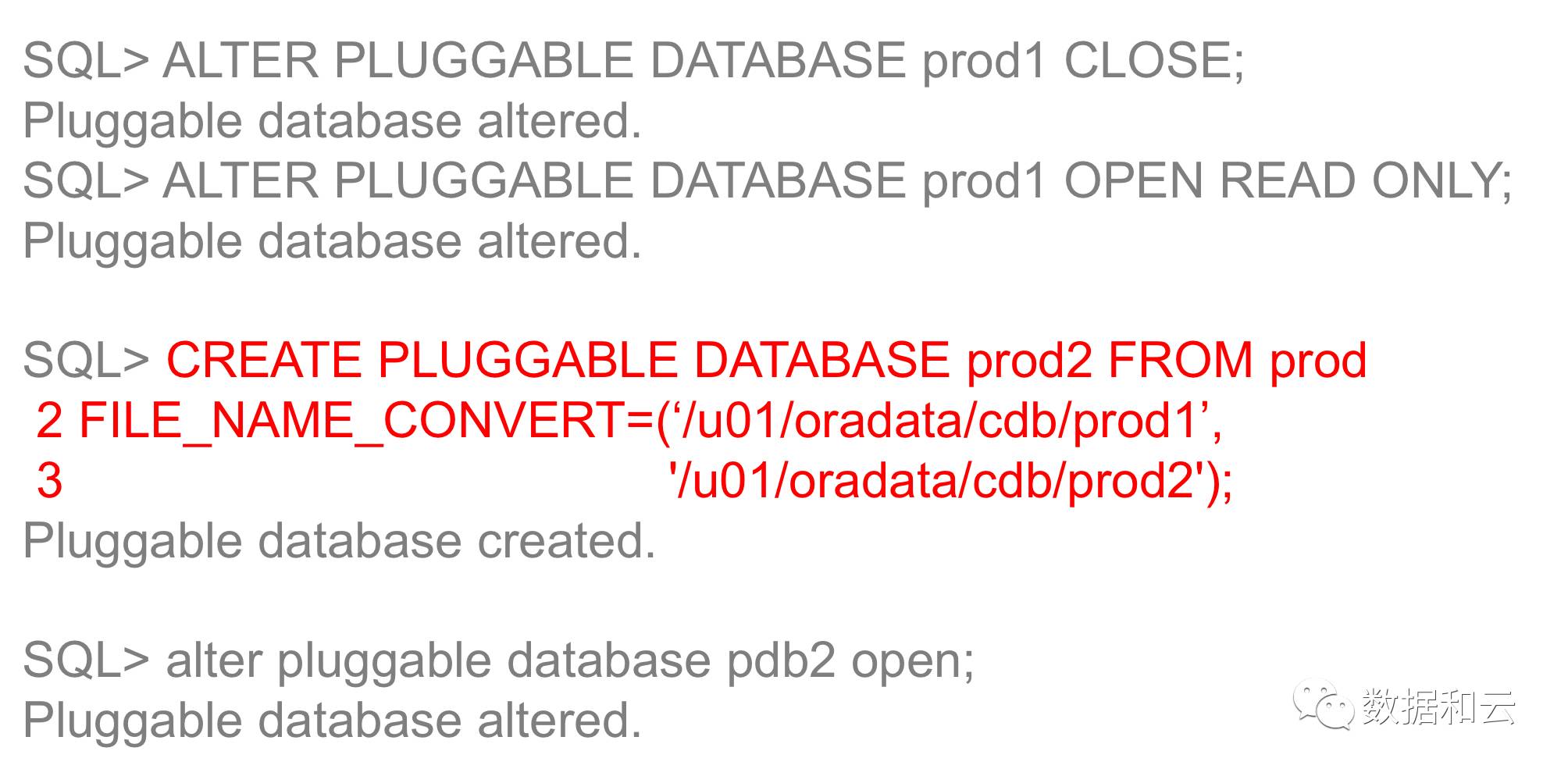
In 12.2, the original library can continue to perform DML operations without being affected.
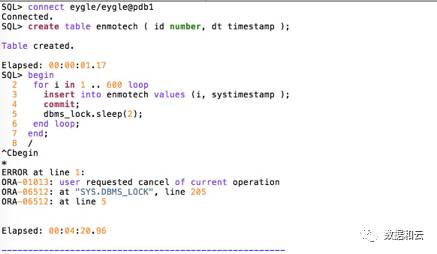
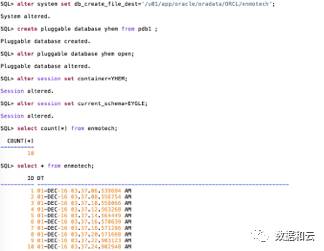
After the cloning is completed, the data will continue to be refreshed to the new database.
3. Migration from PDBs in other CDBs: Relocate
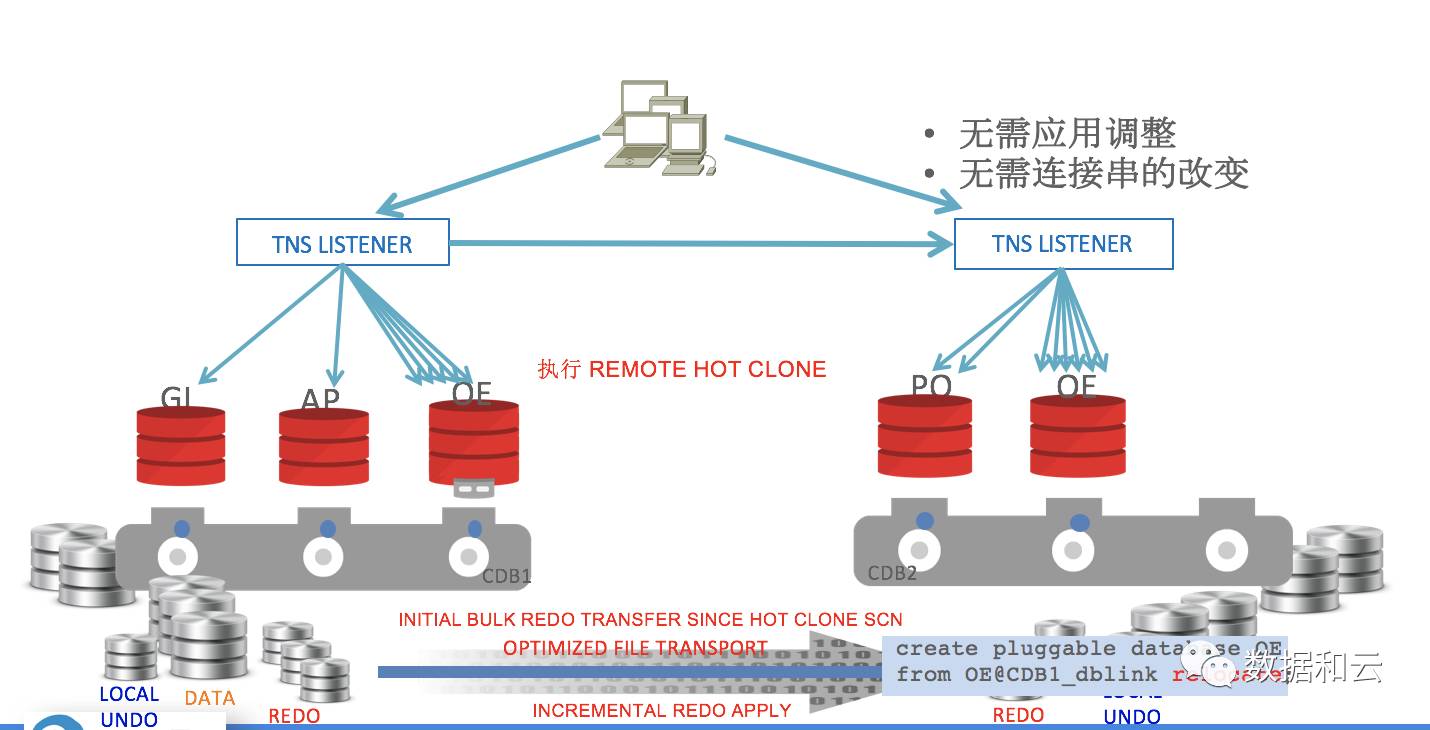
The front-end executes a command such as create pluggable database from relocate, and the background will automatically execute remote hot clone and perform remote file copy and synchronization.
4. Generate a new PDB through shadow copy of ASM disk files.
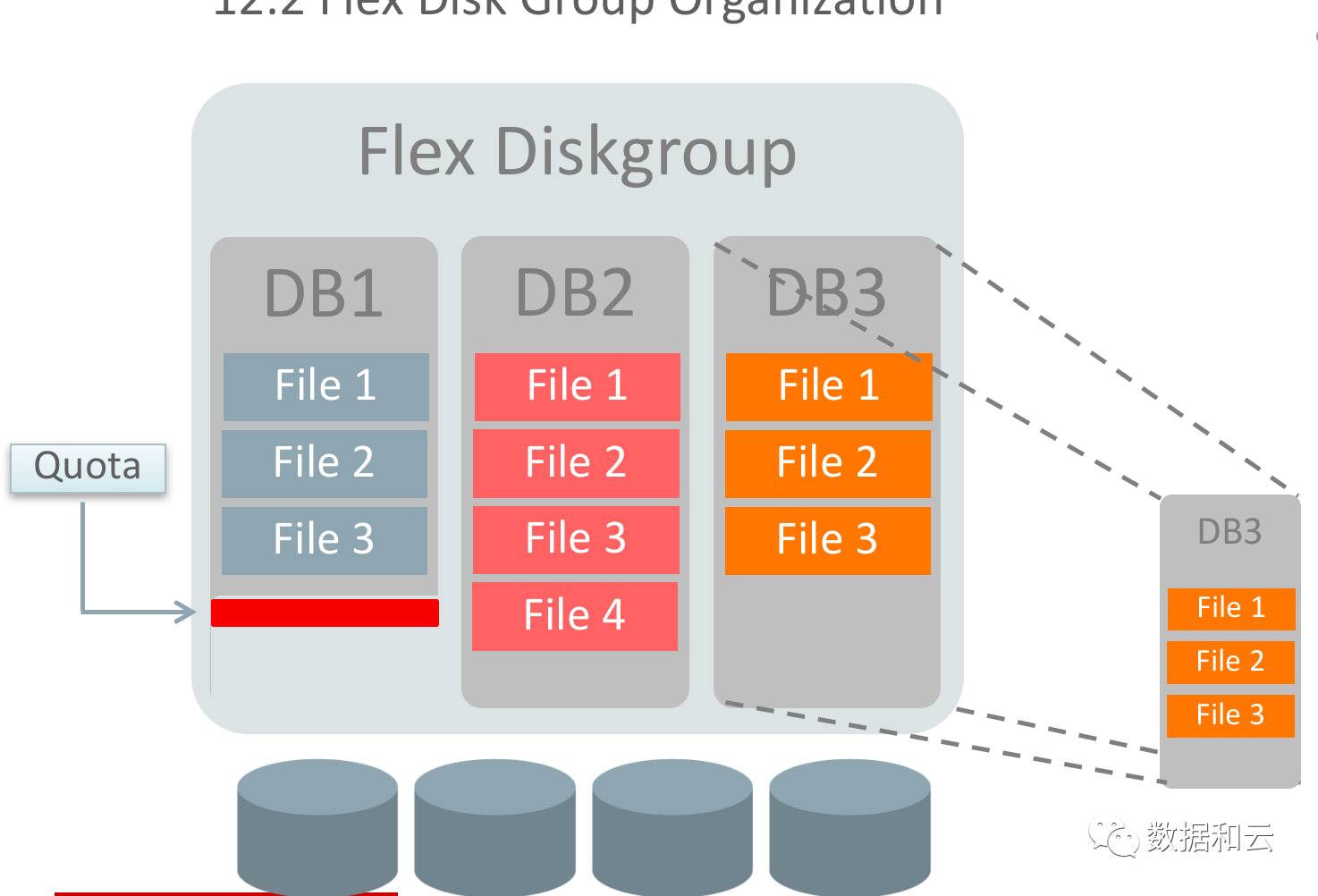
PDB memory resource management
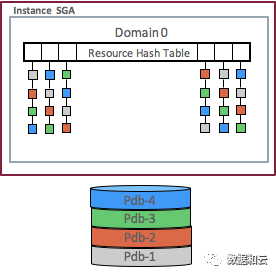
In a multi-tenant environment, multiple PDBs share memory resources. When a PDB needs to address buffer cache, it needs to search from the entire shared resources, which is very inconvenient. In 12.2, Oracle implemented PDB-based domain division for some resources.
The hash list of memory resources in 12.1 is as follows:
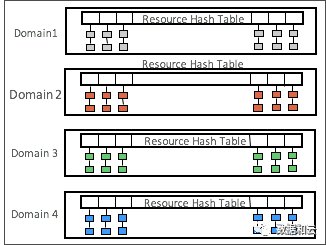
This is what happens in 12.2:
More new features of PDB
1. Character set: In 12.2, if the CDB character set is a superset, that is, AL32UTF8, then PDBs with different character sets are supported. At the same time, through Proxy PDB, PDBs with different character sets can be queried. Proxy will identify and make the character sets of both parties compatible without garbled characters.
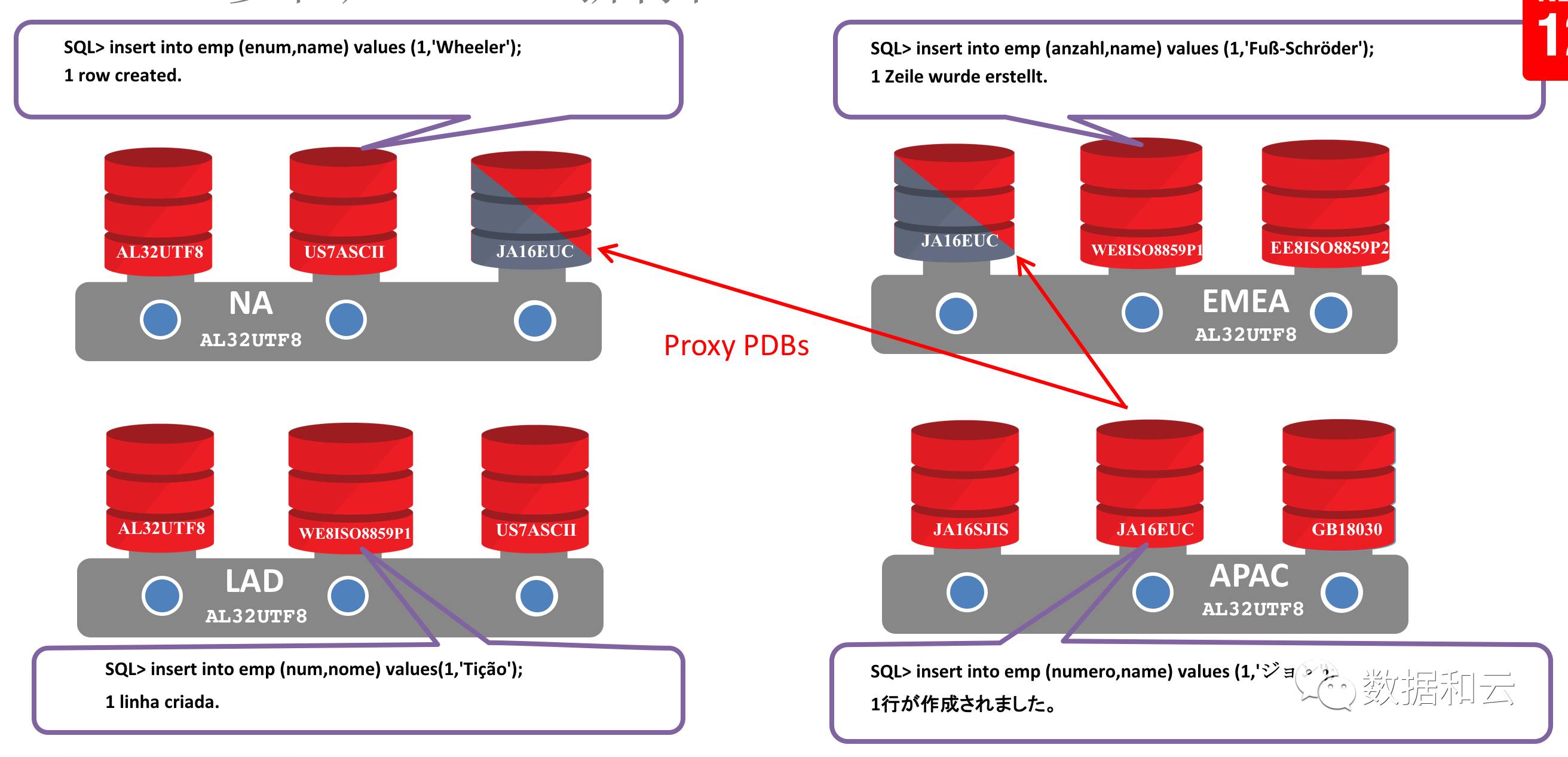
Multi-tenant technology has been widely used by users, and Yunhe Enmo, as a leader in the data service industry, has helped users realize the cloud transformation of systems in the Internet era through the combination of zData solutions and Oracle multi-tenant.
For more detailed explanations of new features of multi-tenancy, please refer to
YH9:Oracle Multitenant Knowledge Base
Multi-tenant technology has been widely used by users. As a leader in the data service industry, Yunhe Enmo has helped users realize the cloud transformation of systems in the Internet era through the combination of zData solutions and Oracle multi-tenant.
Article from WeChat public account: Data and Cloud
The above is the detailed content of Understand the architecture of Oracle12.2: file system and multi-tenancy. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 How to start nginx in Linux
Apr 14, 2025 pm 12:51 PM
How to start nginx in Linux
Apr 14, 2025 pm 12:51 PM
Steps to start Nginx in Linux: Check whether Nginx is installed. Use systemctl start nginx to start the Nginx service. Use systemctl enable nginx to enable automatic startup of Nginx at system startup. Use systemctl status nginx to verify that the startup is successful. Visit http://localhost in a web browser to view the default welcome page.
 How to check whether nginx is started
Apr 14, 2025 pm 01:03 PM
How to check whether nginx is started
Apr 14, 2025 pm 01:03 PM
How to confirm whether Nginx is started: 1. Use the command line: systemctl status nginx (Linux/Unix), netstat -ano | findstr 80 (Windows); 2. Check whether port 80 is open; 3. Check the Nginx startup message in the system log; 4. Use third-party tools, such as Nagios, Zabbix, and Icinga.
 How to start nginx server
Apr 14, 2025 pm 12:27 PM
How to start nginx server
Apr 14, 2025 pm 12:27 PM
Starting an Nginx server requires different steps according to different operating systems: Linux/Unix system: Install the Nginx package (for example, using apt-get or yum). Use systemctl to start an Nginx service (for example, sudo systemctl start nginx). Windows system: Download and install Windows binary files. Start Nginx using the nginx.exe executable (for example, nginx.exe -c conf\nginx.conf). No matter which operating system you use, you can access the server IP
 How to solve nginx304 error
Apr 14, 2025 pm 12:45 PM
How to solve nginx304 error
Apr 14, 2025 pm 12:45 PM
Answer to the question: 304 Not Modified error indicates that the browser has cached the latest resource version of the client request. Solution: 1. Clear the browser cache; 2. Disable the browser cache; 3. Configure Nginx to allow client cache; 4. Check file permissions; 5. Check file hash; 6. Disable CDN or reverse proxy cache; 7. Restart Nginx.
 How to check whether nginx is started?
Apr 14, 2025 pm 12:48 PM
How to check whether nginx is started?
Apr 14, 2025 pm 12:48 PM
In Linux, use the following command to check whether Nginx is started: systemctl status nginx judges based on the command output: If "Active: active (running)" is displayed, Nginx is started. If "Active: inactive (dead)" is displayed, Nginx is stopped.
 How to solve nginx403 error
Apr 14, 2025 pm 12:54 PM
How to solve nginx403 error
Apr 14, 2025 pm 12:54 PM
The server does not have permission to access the requested resource, resulting in a nginx 403 error. Solutions include: Check file permissions. Check the .htaccess configuration. Check nginx configuration. Configure SELinux permissions. Check the firewall rules. Troubleshoot other causes such as browser problems, server failures, or other possible errors.
 How to clean nginx error log
Apr 14, 2025 pm 12:21 PM
How to clean nginx error log
Apr 14, 2025 pm 12:21 PM
The error log is located in /var/log/nginx (Linux) or /usr/local/var/log/nginx (macOS). Use the command line to clean up the steps: 1. Back up the original log; 2. Create an empty file as a new log; 3. Restart the Nginx service. Automatic cleaning can also be used with third-party tools such as logrotate or configured.
 Difference between centos and ubuntu
Apr 14, 2025 pm 09:09 PM
Difference between centos and ubuntu
Apr 14, 2025 pm 09:09 PM
The key differences between CentOS and Ubuntu are: origin (CentOS originates from Red Hat, for enterprises; Ubuntu originates from Debian, for individuals), package management (CentOS uses yum, focusing on stability; Ubuntu uses apt, for high update frequency), support cycle (CentOS provides 10 years of support, Ubuntu provides 5 years of LTS support), community support (CentOS focuses on stability, Ubuntu provides a wide range of tutorials and documents), uses (CentOS is biased towards servers, Ubuntu is suitable for servers and desktops), other differences include installation simplicity (CentOS is thin)




