 Computer Tutorials
Computer Tutorials
 Browser
Browser
 QQ responds by reading browser history: the data is used to determine whether the login is malicious.
QQ responds by reading browser history: the data is used to determine whether the login is malicious.
QQ responds by reading browser history: the data is used to determine whether the login is malicious.
Xigua, the editor of php, introduced that QQ recently responded that the data read from the browser history is used to determine whether the login is malicious. It is understood that QQ will read browser history data when a user logs in, and determine whether the login is normal behavior by analyzing the websites the user has recently visited. This move is intended to increase account security and reduce the risk of malicious logins. However, this approach has also caused concerns and doubts among some users. Today, when privacy protection has become a hot issue, how to balance security and privacy has become an issue that requires serious consideration.

Tencent QQ responded to this question on its official Zhihu account, saying that recently we have received external feedback that PCQQ scanned and read the browser's history. Our QQ security team takes this very seriously and immediately launched an investigation. After investigation, we found that PCQQ does read browser history, but this is to determine the security risk of user login. These read data are only used for judgment in PCQQ's local client to identify whether there is a malicious login. It is worth emphasizing that all relevant data will not be uploaded to the cloud, will not be stored, and will not be used for any other purpose. We handle this issue very carefully to ensure user privacy and data security. At the same time, we also welcome further questions and feedback from users on this matter, and we will continue to pay attention and take appropriate measures to protect the rights and interests of users.
The specific situation is that this operation is a technical solution against malicious logins launched in history: because the system has identified that many fake QQ clients will maliciously access multiple websites as preliminary auxiliary work, so in PCQQ Access logic for detecting malicious and abnormal events is added to the client as an auxiliary means to identify malicious clients.
Tencent said that it deeply apologizes for this incident and is internally sorting out historical issues and strengthening user data access standards. At present, the technical logic for detecting malicious and abnormal requests has been replaced to solve the above security risk issues, and a new PCQQ version has been released. To reduce inconvenience, all affected historical versions of PCQQ will undergo hot updates and push upgrade packages starting today. At the same time, the above operations do not exist on mobile QQ and will not be affected.
The above is the detailed content of QQ responds by reading browser history: the data is used to determine whether the login is malicious.. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 What to do if the xlsx file cannot be opened on mobile phone
Apr 25, 2024 am 08:28 AM
What to do if the xlsx file cannot be opened on mobile phone
Apr 25, 2024 am 08:28 AM
Why can’t WPS and Excel documents be opened on Apple’s mobile phone? It shows that the file cannot be previewed. 1. The reason why WPS and Excel documents cannot be previewed on Apple’s mobile phone is because there are no applications that support these file formats installed on the mobile phone. The solution is to install an application that supports the document format. Application to convert documents to PDF format and send documents to computers or other devices for opening. 2. First check what the suffix of the file is. If it is an excel file but cannot be opened, it means that the file type is not registered in the computer's folder options. 3. First, open the QQ browser on your mobile phone; click the button in the middle below; click "File Download"; click "Document" to select the excel file you want to open. Summary Open QQ browsing
 How to open zip file on mobile phone
Apr 21, 2024 am 10:01 AM
How to open zip file on mobile phone
Apr 21, 2024 am 10:01 AM
How to open zip files on mobile phones 1. Open the file management and find the file in Zip format; click on the file to be opened and select decompression; select the location where the decompressed file will be stored; start decompressing the file; decompression is successful, and a file in Zip format will be decompressed as shown in the figure; You can now open and view it directly. 2. Find the software store on the mobile phone desktop. Open the software store and type compression in the search bar. After entering the compression, click on Almighty Compression and click Install. Open the downloaded Almighty Compression APP. Click the plus sign and select the compressed file you want to open on your phone to decompress it. 3. The method to open a zip file on a mobile phone is: first open "My Files" on the mobile phone and find the file in compressed zip format. Select a file in compressed zip format,
 What does dao mean in java
Apr 21, 2024 am 02:08 AM
What does dao mean in java
Apr 21, 2024 am 02:08 AM
DAO (Data Access Object) in Java is used to separate application code and persistence layer, its advantages include: Separation: Independent from application logic, making it easier to modify it. Encapsulation: Hide database access details and simplify interaction with the database. Scalability: Easily expandable to support new databases or persistence technologies. With DAOs, applications can call methods to perform database operations such as create, read, update, and delete entities without directly dealing with database details.
 How to remove the write protection of a USB flash drive? Several simple and effective methods can help you do it
May 02, 2024 am 09:04 AM
How to remove the write protection of a USB flash drive? Several simple and effective methods can help you do it
May 02, 2024 am 09:04 AM
U disk is one of the commonly used storage devices in our daily work and life, but sometimes we encounter situations where the U disk is write-protected and cannot write data. This article will introduce several simple and effective methods to help you quickly remove the write protection of the USB flash drive and restore the normal use of the USB flash drive. Tool materials: System version: Windows1020H2, macOS BigSur11.2.3 Brand model: SanDisk UltraFlair USB3.0 flash drive, Kingston DataTraveler100G3USB3.0 flash drive Software version: DiskGenius5.4.2.1239, ChipGenius4.19.1225 1. Check the physical write protection switch of the USB flash drive on some USB flash drives Designed with
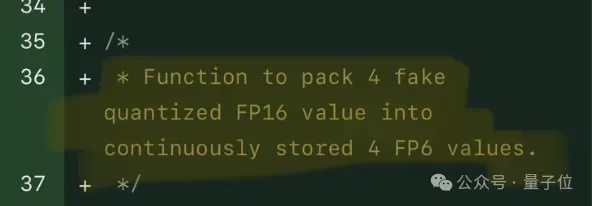 Single card running Llama 70B is faster than dual card, Microsoft forced FP6 into A100 | Open source
Apr 29, 2024 pm 04:55 PM
Single card running Llama 70B is faster than dual card, Microsoft forced FP6 into A100 | Open source
Apr 29, 2024 pm 04:55 PM
FP8 and lower floating point quantification precision are no longer the "patent" of H100! Lao Huang wanted everyone to use INT8/INT4, and the Microsoft DeepSpeed team started running FP6 on A100 without official support from NVIDIA. Test results show that the new method TC-FPx's FP6 quantization on A100 is close to or occasionally faster than INT4, and has higher accuracy than the latter. On top of this, there is also end-to-end large model support, which has been open sourced and integrated into deep learning inference frameworks such as DeepSpeed. This result also has an immediate effect on accelerating large models - under this framework, using a single card to run Llama, the throughput is 2.65 times higher than that of dual cards. one
 Usage of service layer in java
May 07, 2024 am 04:24 AM
Usage of service layer in java
May 07, 2024 am 04:24 AM
The Service layer in Java is responsible for business logic and business rules for executing applications, including processing business rules, data encapsulation, centralizing business logic and improving testability. In Java, the Service layer is usually designed as an independent module, interacts with the Controller and Repository layers, and is implemented through dependency injection, following steps such as creating an interface, injecting dependencies, and calling Service methods. Best practices include keeping it simple, using interfaces, avoiding direct manipulation of data, handling exceptions, and using dependency injection.
 What is the API interface for?
Apr 23, 2024 pm 01:51 PM
What is the API interface for?
Apr 23, 2024 pm 01:51 PM
An API interface is a specification for interaction between software components and is used to implement communication and data exchange between different applications or systems. The API interface acts as a "translator", converting the developer's instructions into computer language so that the applications can work together. Its advantages include convenient data sharing, simplified development, improved performance, enhanced security, improved productivity and interoperability.
 What does mysql database do?
Apr 22, 2024 pm 06:12 PM
What does mysql database do?
Apr 22, 2024 pm 06:12 PM
MySQL is a relational database management system that provides the following main functions: Data storage and management: Create and organize data, supporting various data types, primary keys, foreign keys, and indexes. Data query and retrieval: Use SQL language to query, filter and retrieve data, and optimize execution plans to improve efficiency. Data updates and modifications: Add, modify or delete data through INSERT, UPDATE, DELETE commands, supporting transactions to ensure consistency and rollback mechanisms to undo changes. Database management: Create and modify databases and tables, back up and restore data, and provide user management and permission control.



