Dry stuff! Oracle decrypts 'zero loss' data protection
According to statistics, the data volume of most enterprises is expected to increase 50 times by 2020. Such a huge data set will lead to extremely high risks of data loss. Current solutions for protecting business data fail to meet the needs of mission-critical enterprise databases. These solutions have the potential to lose up to a day's worth of business data each time a restore is performed, place a heavy burden on production servers during backups, and fail to ensure database-level recoverability or scale to accommodate growing workloads. Database requirements. Basically, they replicate the database as a discrete set of files rather than a transactional system with specific integrity and performance requirements.
Oracle Zero Data Loss Recovery Appliance is a breakthrough data protection solution that directly meets these needs through tight integration with Oracle Database. The appliance eliminates the risk of data loss and significantly reduces the overhead of data protection on production servers. In addition, it scales to protect thousands of databases, ensures end-to-end data validation, and enables full lifecycle protection, including disk backup, tape backup, and remote replication.
Recently, Oracle held an online seminar titled "Oracle Decrypts 'Zero Loss' Data Protection", which provided an in-depth explanation of Oracle's upgrade path from capabilities to services and the excellent performance of Oracle's zero data loss recovery machine.
At this online seminar, Mr. Pan Yuqi, General Manager of Oracle China's System Business Technology Department, first delivered a speech titled "The Road to Internalizing the Cloud—Upgrading from Capabilities to Services."
Mr. Pan Yuqi first elaborated on the fact that Oracle has transformed into a cloud service provider for enterprise computing from three aspects.
1. Oracle provides comprehensive SaaS, PaaS, and IaaS services.
2. At Oracle, the research and development of SaaS, PaaS, and IaaS are integrated.
3. Oracle’s public cloud and private cloud use exactly the same technology.
In the process of realizing seamless migration of "public and private" clouds, comprehensive deployment will be carried out with the same standards, the same products, and unified management.
Mr. Pan Yuqi said that Oracle currently provides four major private cloud services: database as a service (Exadata), enterprise application as a service (PCA/Exalogic), big data and analysis as a service (Exadata/BDA), and data protection as a service (ZDLRA/ZFS). At this point, the traditional data center has been transformed into a private cloud.
Subsequently, Mr. Pan Yuqi cited several cases to illustrate that the existing disaster recovery system is often vulnerable to attacks or problems at the logical level and cannot cope with malicious attacks. Therefore, the disaster recovery system is often intolerant of disasters and urgently needs to change its inherent characteristics. With data protection thinking in mind, Oracle Zero Data Loss Recovery All-in-One came into being.
The second session of this online seminar is a tit-for-tat dialogue brought by Mr. Zhang Jingjing, Chief Technical Advisor of Oracle China System Business Technology Department, and Mr. Yang Zheng, Senior Technical Advisor of Oracle China System Business Technology Department: Data Protection-- -Reveal the black technology of ZDLRA.
The two of them first started with the name of Oracle's zero data loss recovery machine. ZDLRA, this seemingly strange name, stands for Zero Data Loss Recovery Appliance. As a data protection product, its name is so simple that you can tell at a glance that it is a data protection and recovery all-in-one machine, as well as its commitment to data, IT infrastructure and enterprise business.
ZDLRA is a data protection system specially designed to protect databases. The purpose of the design is to provide the highest level of protection for Oracle databases and ensure backup/recovery performance and efficiency. At the same time, it ensures that it can support all versions of Oracle databases and Various types of hardware, operating systems and business environments hosting databases. It is tightly integrated with Oracle's database to provide continuous data protection for the database, offloading almost all backup processing system resource overhead from the production server.
In order to achieve the design goal of zero data loss and significantly eliminate the recovery time (RTO) of the database, Oracle has introduced two new technologies for ZDLRA: Delta Push and Delta Storage Store).
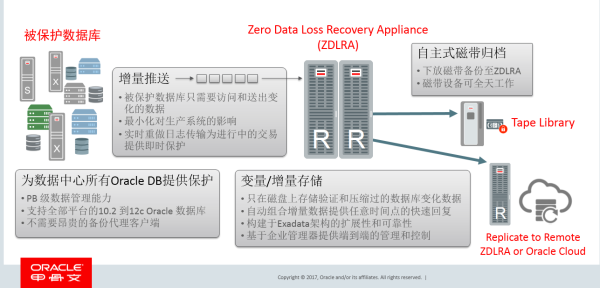
The base configuration consists of 2 compute servers and 3 storage servers, all connected via internal high-speed InfiniBand. It offers a highly available configuration, including 94 TB of available incoming backup capacity. Users can incrementally upgrade the base rack by adding more storage servers (up to 18 storage servers for a full rack). Adds 32 TB of usable capacity per storage server. Each full rack has a total usable capacity of 580 TB, with an effective virtual full backup capacity of 5.8 PB. The total database size that the Recovery Appliance can protect is equivalent to the available capacity for a typical recovery cycle of 10 days. If additional capacity is needed, another base rack can be connected via high-speed InfiniBand. The second rack contains its own two compute servers, increasing the connectivity and processing power of the configuration. As with the first rack, users can easily expand their storage capacity by gradually adding storage servers. Up to 18 fully configured racks can be connected to form a single appliance, providing over 10 PB of usable capacity, or over 100 PB of virtual full backup.
In addition to Delta Push and Delta Store, as well as powerful hardware configuration and hardware architecture system, ZDLRA also has two major technical backings. The first is MAA - Oracle Maximum Availability Architecture - based on Oracle high availability technology. Its goal is to achieve the optimal high availability architecture with the lowest cost and complexity. It ensures the high performance of the Oracle database. Availability (such as active clustering, replication, continuous Oracle data validation, Oracle-aware backup and recovery, non-downtime maintenance, etc.) is available for any platform or application and is tightly integrated with Oracle Engineered Systems. The second is the famous RMAN. As we all know, RMAN is the "core engine" used to back up and restore Oracle. It greatly saves the storage space and data transmission time required to back up and restore Oracle databases by using compression and other technologies - RMAN Using incremental backup technology, only the RMAN database blocks that have changed since the last backup are backed up.

A total of about 13,414 people participated in this online seminar. Everyone actively participated in asking questions and interacting. The attention on Oracle Zero Data Loss Recovery Appliance and Oracle business was extraordinary.
The above is the detailed content of Dry stuff! Oracle decrypts 'zero loss' data protection. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Difference between centos and ubuntu
Apr 14, 2025 pm 09:09 PM
Difference between centos and ubuntu
Apr 14, 2025 pm 09:09 PM
The key differences between CentOS and Ubuntu are: origin (CentOS originates from Red Hat, for enterprises; Ubuntu originates from Debian, for individuals), package management (CentOS uses yum, focusing on stability; Ubuntu uses apt, for high update frequency), support cycle (CentOS provides 10 years of support, Ubuntu provides 5 years of LTS support), community support (CentOS focuses on stability, Ubuntu provides a wide range of tutorials and documents), uses (CentOS is biased towards servers, Ubuntu is suitable for servers and desktops), other differences include installation simplicity (CentOS is thin)
 How to install centos
Apr 14, 2025 pm 09:03 PM
How to install centos
Apr 14, 2025 pm 09:03 PM
CentOS installation steps: Download the ISO image and burn bootable media; boot and select the installation source; select the language and keyboard layout; configure the network; partition the hard disk; set the system clock; create the root user; select the software package; start the installation; restart and boot from the hard disk after the installation is completed.
 Centos stops maintenance 2024
Apr 14, 2025 pm 08:39 PM
Centos stops maintenance 2024
Apr 14, 2025 pm 08:39 PM
CentOS will be shut down in 2024 because its upstream distribution, RHEL 8, has been shut down. This shutdown will affect the CentOS 8 system, preventing it from continuing to receive updates. Users should plan for migration, and recommended options include CentOS Stream, AlmaLinux, and Rocky Linux to keep the system safe and stable.
 What are the backup methods for GitLab on CentOS
Apr 14, 2025 pm 05:33 PM
What are the backup methods for GitLab on CentOS
Apr 14, 2025 pm 05:33 PM
Backup and Recovery Policy of GitLab under CentOS System In order to ensure data security and recoverability, GitLab on CentOS provides a variety of backup methods. This article will introduce several common backup methods, configuration parameters and recovery processes in detail to help you establish a complete GitLab backup and recovery strategy. 1. Manual backup Use the gitlab-rakegitlab:backup:create command to execute manual backup. This command backs up key information such as GitLab repository, database, users, user groups, keys, and permissions. The default backup file is stored in the /var/opt/gitlab/backups directory. You can modify /etc/gitlab
 Detailed explanation of docker principle
Apr 14, 2025 pm 11:57 PM
Detailed explanation of docker principle
Apr 14, 2025 pm 11:57 PM
Docker uses Linux kernel features to provide an efficient and isolated application running environment. Its working principle is as follows: 1. The mirror is used as a read-only template, which contains everything you need to run the application; 2. The Union File System (UnionFS) stacks multiple file systems, only storing the differences, saving space and speeding up; 3. The daemon manages the mirrors and containers, and the client uses them for interaction; 4. Namespaces and cgroups implement container isolation and resource limitations; 5. Multiple network modes support container interconnection. Only by understanding these core concepts can you better utilize Docker.
 How to use docker desktop
Apr 15, 2025 am 11:45 AM
How to use docker desktop
Apr 15, 2025 am 11:45 AM
How to use Docker Desktop? Docker Desktop is a tool for running Docker containers on local machines. The steps to use include: 1. Install Docker Desktop; 2. Start Docker Desktop; 3. Create Docker image (using Dockerfile); 4. Build Docker image (using docker build); 5. Run Docker container (using docker run).
 What to do after centos stops maintenance
Apr 14, 2025 pm 08:48 PM
What to do after centos stops maintenance
Apr 14, 2025 pm 08:48 PM
After CentOS is stopped, users can take the following measures to deal with it: Select a compatible distribution: such as AlmaLinux, Rocky Linux, and CentOS Stream. Migrate to commercial distributions: such as Red Hat Enterprise Linux, Oracle Linux. Upgrade to CentOS 9 Stream: Rolling distribution, providing the latest technology. Select other Linux distributions: such as Ubuntu, Debian. Evaluate other options such as containers, virtual machines, or cloud platforms.
 How to mount hard disk in centos
Apr 14, 2025 pm 08:15 PM
How to mount hard disk in centos
Apr 14, 2025 pm 08:15 PM
CentOS hard disk mount is divided into the following steps: determine the hard disk device name (/dev/sdX); create a mount point (it is recommended to use /mnt/newdisk); execute the mount command (mount /dev/sdX1 /mnt/newdisk); edit the /etc/fstab file to add a permanent mount configuration; use the umount command to uninstall the device to ensure that no process uses the device.




