Detailed explanation of Linux signal set operation functions
Let’s first review what a pending signal set is. When a signal is generated and reaches its destination, this process is called signal delivery. The intermediate state from signal generation to delivery is called the pending state of the signal. The reason for the pending state may be that the signal is blocked, that is, the corresponding bit in the signal mask word (or blocked signal set) is set to 1. Both the blocking signal set and the pending signal set are maintained by the kernel. The whole process is shown in the figure below:
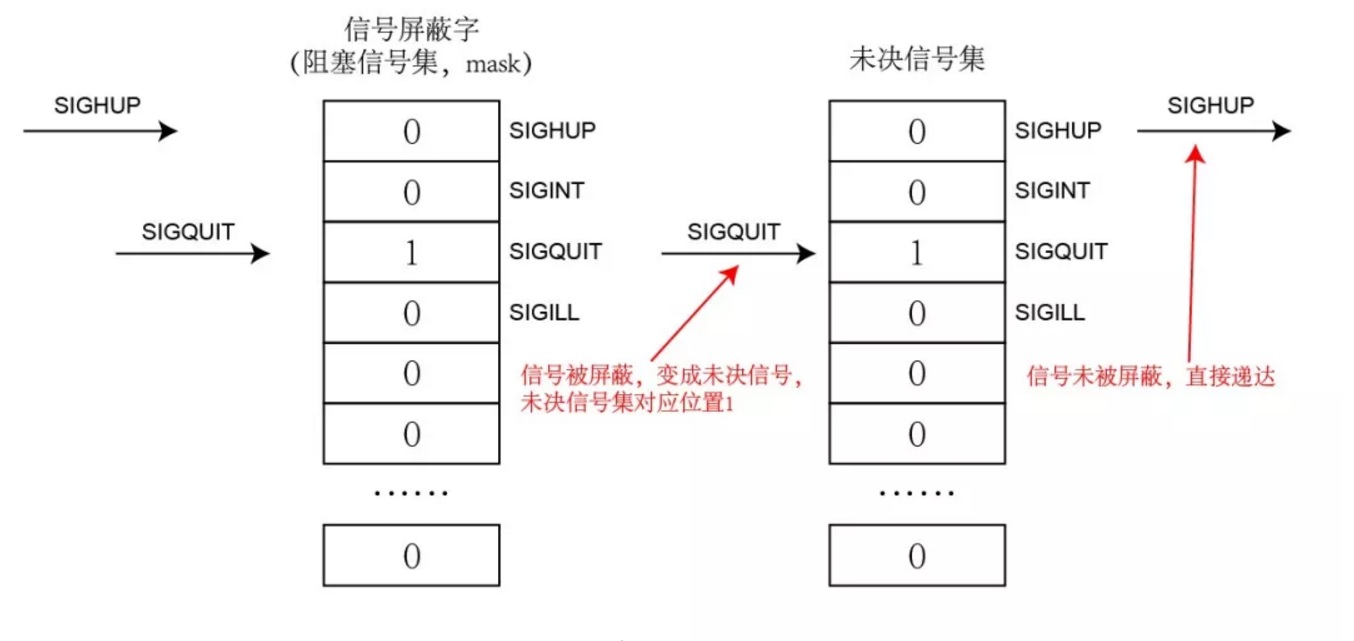
Sometimes we need to block a certain signal, so we need to modify the blocking signal set. So, how do we modify the blocking signal set? One method provided by the system is that we first create a set that is the same as the blocking signal set, and then use it to modify the blocking signal set.
The system provides a series of signal set setting functions. These functions are as follows:
sigset_t set; 信号集数据类型,本质是typedef unsigned long sigset_t; int sigemptyset(sigset_t *set); 将某个信号集清0 int sigfillset(sigset_t *set); 将某个信号集置1 int sigaddset(sigset_t *set, int signum); 将某个信号加入信号集 int sigdelset(sigset_t *set, int signum); 将某个信号清出信号集 以上几个函数返回值均是:成功:0;失败:-1 int sigismember(const sigset_t *set, int signum); 判断某个信号是否在信号集中 返回值:在集合:1;不在:0;出错:-1
After using the above functions to create the signal set, how to change the blocking signal set? The system provides another function: sigprocmask function. The sigprocmask function can be used to block signals or unblock signals. Its essence is to use the signal set we created to change the blocking signal set.
Function prototype:
int sigprocmask(int how, const sigset_t *set, sigset_t *oldset);
return value:
Success: 0; Failure: -1, set errno
Parameter explanation:
set: The incoming parameter is a bitmap. Which bit in the set is 1 indicates which signal is blocked by the current process.
oldset: Outgoing parameters, save the old signal mask set. This is somewhat similar to setitimer.
how parameter value:
Assume that the current signal mask word is mask
1.SIG_BLOCK: When how is set to this value, set indicates the signal that needs to be blocked. Equivalent to mask = mask | set
2.SIG_UNBLOCK: When how is set to this, set indicates the signal that needs to be unblocked. Equivalent to mask = mask & ~set
3.SIG_SETMASK: When how is set to this, set represents the new mask set used to replace the original mask. Equivalent to mask = set. If calling sigprocmask unblocks several current signals, at least one of the signals will be delivered before sigprocmask returns.
How do we read the set of pending signals? The system provides the sigpending function.
Function prototype:
int sigpending(sigset_t *set);
Parameter Description:
set outgoing parameters.
return value:
Return value: Success: 0; Failure: -1, set errno
Example: Print the pending status of all regular signals to the screen.
#include
#include
#include
void printPending(sigset_t *set)
{
int i = 0;
for (i = 0; i if (sigismember(set, i) == 1)
printf("1");
else
printf("0");
}
printf("\n");
}
int main()
{
sigset_t set, oldset, pendset;
sigemptyset(&set);
sigaddset(&set, SIGQUIT); // ctrl + \ 将产生SIGQUIT信号
sigprocmask(SIG_BLOCK, &set, &oldset);
while (1) {
sigpending(&pendset);
printPending(&pendset); // 写一个函数打印未决信号集
sleep(1);
}
}
The above is the detailed content of Detailed explanation of Linux signal set operation functions. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 Unable to log in to mysql as root
Apr 08, 2025 pm 04:54 PM
Unable to log in to mysql as root
Apr 08, 2025 pm 04:54 PM
The main reasons why you cannot log in to MySQL as root are permission problems, configuration file errors, password inconsistent, socket file problems, or firewall interception. The solution includes: check whether the bind-address parameter in the configuration file is configured correctly. Check whether the root user permissions have been modified or deleted and reset. Verify that the password is accurate, including case and special characters. Check socket file permission settings and paths. Check that the firewall blocks connections to the MySQL server.
 Solutions to the errors reported by MySQL on a specific system version
Apr 08, 2025 am 11:54 AM
Solutions to the errors reported by MySQL on a specific system version
Apr 08, 2025 am 11:54 AM
The solution to MySQL installation error is: 1. Carefully check the system environment to ensure that the MySQL dependency library requirements are met. Different operating systems and version requirements are different; 2. Carefully read the error message and take corresponding measures according to prompts (such as missing library files or insufficient permissions), such as installing dependencies or using sudo commands; 3. If necessary, try to install the source code and carefully check the compilation log, but this requires a certain amount of Linux knowledge and experience. The key to ultimately solving the problem is to carefully check the system environment and error information, and refer to the official documents.
 How to solve mysql cannot be started
Apr 08, 2025 pm 02:21 PM
How to solve mysql cannot be started
Apr 08, 2025 pm 02:21 PM
There are many reasons why MySQL startup fails, and it can be diagnosed by checking the error log. Common causes include port conflicts (check port occupancy and modify configuration), permission issues (check service running user permissions), configuration file errors (check parameter settings), data directory corruption (restore data or rebuild table space), InnoDB table space issues (check ibdata1 files), plug-in loading failure (check error log). When solving problems, you should analyze them based on the error log, find the root cause of the problem, and develop the habit of backing up data regularly to prevent and solve problems.
 Can mysql run on android
Apr 08, 2025 pm 05:03 PM
Can mysql run on android
Apr 08, 2025 pm 05:03 PM
MySQL cannot run directly on Android, but it can be implemented indirectly by using the following methods: using the lightweight database SQLite, which is built on the Android system, does not require a separate server, and has a small resource usage, which is very suitable for mobile device applications. Remotely connect to the MySQL server and connect to the MySQL database on the remote server through the network for data reading and writing, but there are disadvantages such as strong network dependencies, security issues and server costs.
 Unable to access mysql from terminal
Apr 08, 2025 pm 04:57 PM
Unable to access mysql from terminal
Apr 08, 2025 pm 04:57 PM
Unable to access MySQL from the terminal may be due to: MySQL service not running; connection command error; insufficient permissions; firewall blocks connection; MySQL configuration file error.
 What is the most use of Linux?
Apr 09, 2025 am 12:02 AM
What is the most use of Linux?
Apr 09, 2025 am 12:02 AM
Linux is widely used in servers, embedded systems and desktop environments. 1) In the server field, Linux has become an ideal choice for hosting websites, databases and applications due to its stability and security. 2) In embedded systems, Linux is popular for its high customization and efficiency. 3) In the desktop environment, Linux provides a variety of desktop environments to meet the needs of different users.
 Monitor MySQL and MariaDB Droplets with Prometheus MySQL Exporter
Apr 08, 2025 pm 02:42 PM
Monitor MySQL and MariaDB Droplets with Prometheus MySQL Exporter
Apr 08, 2025 pm 02:42 PM
Effective monitoring of MySQL and MariaDB databases is critical to maintaining optimal performance, identifying potential bottlenecks, and ensuring overall system reliability. Prometheus MySQL Exporter is a powerful tool that provides detailed insights into database metrics that are critical for proactive management and troubleshooting.
 How to solve the problem of missing dependencies when installing MySQL
Apr 08, 2025 pm 12:00 PM
How to solve the problem of missing dependencies when installing MySQL
Apr 08, 2025 pm 12:00 PM
MySQL installation failure is usually caused by the lack of dependencies. Solution: 1. Use system package manager (such as Linux apt, yum or dnf, Windows VisualC Redistributable) to install the missing dependency libraries, such as sudoaptinstalllibmysqlclient-dev; 2. Carefully check the error information and solve complex dependencies one by one; 3. Ensure that the package manager source is configured correctly and can access the network; 4. For Windows, download and install the necessary runtime libraries. Developing the habit of reading official documents and making good use of search engines can effectively solve problems.




