 System Tutorial
System Tutorial
 LINUX
LINUX
 Detailed explanation of Ubuntu server SSH security hardening strategy development process and reminders
Detailed explanation of Ubuntu server SSH security hardening strategy development process and reminders
Detailed explanation of Ubuntu server SSH security hardening strategy development process and reminders
php editor Banana specially introduced the process of formulating the Ubuntu server SSH security hardening strategy in detail, and provided some reminders. In an era where network security is becoming increasingly important, protecting the security of your servers is crucial. SSH is a commonly used remote login protocol, but it also faces some security risks. By understanding the process of formulating security hardening strategies and following precautions, we can help us improve the security of our servers and avoid being attacked by hackers. In this article, we will start with the preparation work, introduce the process of formulating the SSH security hardening strategy step by step, and remind everyone of the things you need to pay attention to.

Before formulating an SSH security hardening strategy, you first need to understand the working principle of SSH. SSH uses encryption and authentication technology to achieve secure remote access. Understand the working principle of SSH. , helpful for subsequent strategy formulation and configuration.
Different servers have different security requirements. Therefore, before formulating an SSH security hardening strategy, it is necessary to analyze the security requirements of the server, whether it is necessary to restrict remote access IPs, whether it is necessary to use key authentication, etc.
According to the security requirements of the server, formulate specific SSH security policies, restrict remote access IP range, disable root user login, enable two-step verification, etc.
Configure the SSH server accordingly according to the established security policy, which can be achieved by editing the SSH configuration file (/etc/ssh/sshd_config) and modifying parameters such as PermitRootLogin, PasswordAuthentication, etc.
After completing the configuration of the SSH server, testing and verification are required. You can log in to the server remotely to check whether it takes effect according to the policy and whether there are security vulnerabilities.
Regularly update the system and SSH software to repair known security vulnerabilities in a timely manner and improve the security of the server.
When logging in through SSH, using a complex password can effectively prevent brute force cracking. The password should contain uppercase and lowercase letters, numbers, and special characters, and be no less than 8 characters in length.
Disabling unnecessary SSH services can reduce the risk of the server being exposed to the external network. Only opening necessary ports and services can effectively reduce the attack surface.
Enabling login auditing can record information related to each SSH login, including login time, logged in user, etc. When a security event occurs, it can be traced and analyzed through the audit log.
Regularly back up important data to quickly restore data in the event of a security incident. Backup data should be stored in a safe and reliable place to avoid data leakage.
In SSH security hardening, disabling root user login is a very important strategy. By disabling root user login, you can prevent attackers from directly using root privileges to perform malicious operations. In order to facilitate management, you can create an ordinary The user is given sudo permissions to manage the server, which not only improves the security of the server but also facilitates management. Security is an ongoing task that requires constant monitoring and updates.
The above is the detailed content of Detailed explanation of Ubuntu server SSH security hardening strategy development process and reminders. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
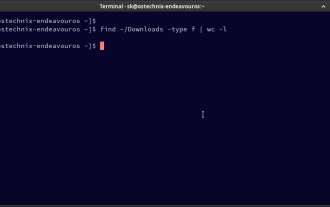 How To Count Files And Directories In Linux: A Beginner's Guide
Mar 19, 2025 am 10:48 AM
How To Count Files And Directories In Linux: A Beginner's Guide
Mar 19, 2025 am 10:48 AM
Efficiently Counting Files and Folders in Linux: A Comprehensive Guide Knowing how to quickly count files and directories in Linux is crucial for system administrators and anyone managing large datasets. This guide demonstrates using simple command-l
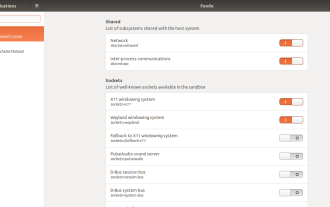 How To Easily Configure Flatpak Apps Permissions With Flatseal
Mar 22, 2025 am 09:21 AM
How To Easily Configure Flatpak Apps Permissions With Flatseal
Mar 22, 2025 am 09:21 AM
Flatpak application permission management tool: Flatseal User Guide Flatpak is a tool designed to simplify Linux software distribution and use. It safely encapsulates applications in a virtual sandbox, allowing users to run applications without root permissions without affecting system security. Because Flatpak applications are located in this sandbox environment, they must request permissions to access other parts of the operating system, hardware devices (such as Bluetooth, network, etc.) and sockets (such as pulseaudio, ssh-auth, cups, etc.). This guide will guide you on how to easily configure Flatpak with Flatseal on Linux
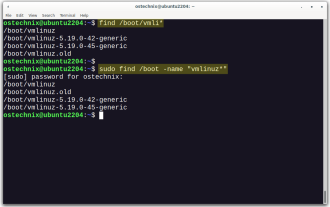 How To List Or Check All Installed Linux Kernels From Commandline
Mar 23, 2025 am 10:43 AM
How To List Or Check All Installed Linux Kernels From Commandline
Mar 23, 2025 am 10:43 AM
Linux Kernel is the core component of a GNU/Linux operating system. Developed by Linus Torvalds in 1991, it is a free, open-source, monolithic, modular, and multitasking Unix-like kernel. In Linux, it is possible to install multiple kernels on a sing
 How To Type Indian Rupee Symbol In Ubuntu Linux
Mar 22, 2025 am 10:39 AM
How To Type Indian Rupee Symbol In Ubuntu Linux
Mar 22, 2025 am 10:39 AM
This brief guide explains how to type Indian Rupee symbol in Linux operating systems. The other day, I wanted to type "Indian Rupee Symbol (₹)" in a word document. My keyboard has a rupee symbol on it, but I don't know how to type it. After
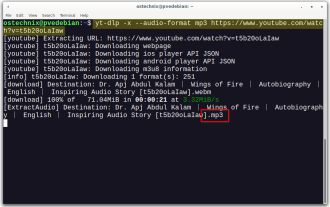 Yt-dlp Commands: The Complete Tutorial For Beginners (2025)
Mar 21, 2025 am 11:00 AM
Yt-dlp Commands: The Complete Tutorial For Beginners (2025)
Mar 21, 2025 am 11:00 AM
Have you ever wanted to save your favorite videos from the internet? Whether it's a funny cat video or a tutorial you want to watch later, Yt-dlp is here to help! In this comprehensive yt-dlp tutorial, we will explain what yt-dlp is, how to install i
 What is the Linux best used for?
Apr 03, 2025 am 12:11 AM
What is the Linux best used for?
Apr 03, 2025 am 12:11 AM
Linux is best used as server management, embedded systems and desktop environments. 1) In server management, Linux is used to host websites, databases, and applications, providing stability and reliability. 2) In embedded systems, Linux is widely used in smart home and automotive electronic systems because of its flexibility and stability. 3) In the desktop environment, Linux provides rich applications and efficient performance.
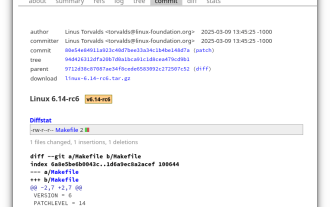 Linux Kernel 6.14 RC6 Released
Mar 24, 2025 am 10:21 AM
Linux Kernel 6.14 RC6 Released
Mar 24, 2025 am 10:21 AM
Linus Torvalds has released Linux Kernel 6.14 Release Candidate 6 (RC6), reporting no significant issues and keeping the release on track. The most notable change in this update addresses an AMD microcode signing issue, while the rest of the updates
 LocalSend - The Open-Source Airdrop Alternative For Secure File Sharing
Mar 24, 2025 am 09:20 AM
LocalSend - The Open-Source Airdrop Alternative For Secure File Sharing
Mar 24, 2025 am 09:20 AM
If you're familiar with AirDrop, you know it's a popular feature developed by Apple Inc. that enables seamless file transfer between supported Macintosh computers and iOS devices using Wi-Fi and Bluetooth. However, if you're using Linux and missing o



