 System Tutorial
System Tutorial
 LINUX
LINUX
 A must-have for Linux! Use SHC encryption tool to protect shell script code security
A must-have for Linux! Use SHC encryption tool to protect shell script code security
A must-have for Linux! Use SHC encryption tool to protect shell script code security
It is very common to use scripts on Linux systems. However, due to the open nature of script code, sometimes scripts are maliciously modified, copied, and spread. To do this, we need a way to secure our script code. SHC is a very practical encryption tool that can help us encrypt shell scripts and protect the security of the code.
How to encrypt shell scripts in Linux environment? The shell script contains the password and you don't want someone else with execution permissions to view the shell script and get the password. You can install and use the shc tool. Ordinary users cannot read the encrypted shell script created by shc. SHC refers to: Shell Script Compiler (Shell Script Compiler).
environment
Centos8
Install shc
[root@localhost ~]# yum -y install shc
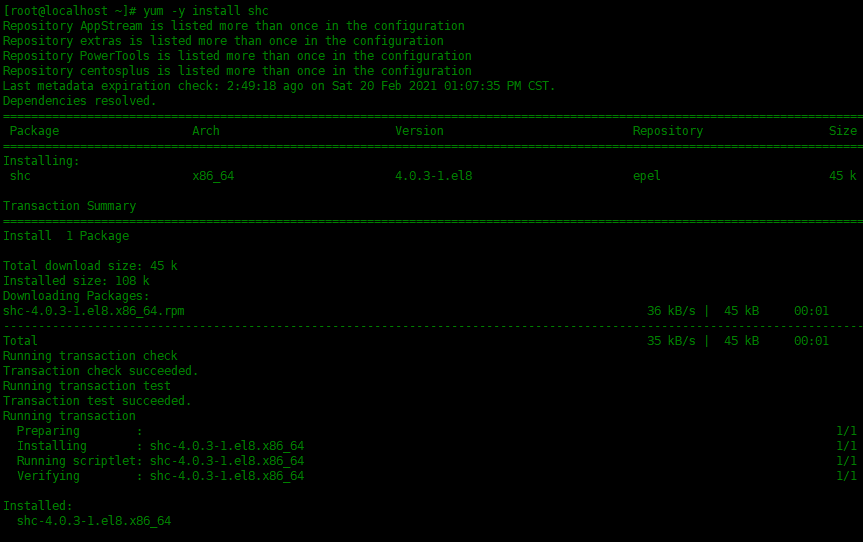
Create a shell script
Create a script file below:
[root@localhost ~]# vim welcome.sh #!/bin/sh echo "Welcome to linux world"
Use shc to encrypt the script file
As shown below, use shc to encrypt the welcome.sh script.
[root@localhost scripts]# shc -v -f welcome.sh shc shll=sh shc [-i]=-c shc [-x]=exec '%s' "$@" shc [-l]= shc opts= shc: cc welcome.sh.x.c -o welcome.sh.x shc: strip welcome.sh.x shc: chmod ug=rwx,o=rx welcome.sh.x
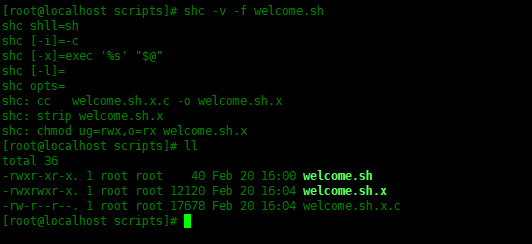
- welcome.sh is the original unencrypted shell script
- welcome.sh.x is an encrypted shell script in binary format
- welcome.sh.x.c is the C source code of the welcome.sh file. Compile this C source code to create the encrypted welcome.sh.x file above.
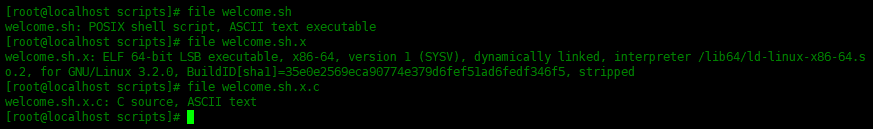
You can use the file command to view the file type:
[root@localhost scripts]# file welcome.sh welcome.sh: POSIX shell script, ASCII text executable [root@localhost scripts]# file welcome.sh.x welcome.sh.x: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86- 64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=35e0e2569eca90774e379d6fef51ad6fedf346f5, s tripped [root@localhost scripts]# file welcome.sh.x.c welcome.sh.x.c: C source, ASCII text [root@localhost scripts]#
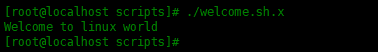
Execute the encrypted shell script
Now, let’s execute the encrypted Shell script and make sure it runs:
[root@localhost scripts]# ./welcome.sh.x Welcome to linux world
Specify the expiration time of the Shell script
With shc, you can also specify an expiration date. i.e. after this expiration date, when someone tries to execute the shell script, they will receive an error message. Create a new encrypted shell script using the shc -e option, specifying the expiration date. The expiration date is specified in dd/mm/yyyy format.
# 删除之前创建的.x , .x.c文件 [root@localhost scripts]# rm -rf welcome.sh.x* # 创建带有过期时间的加密脚本 [root@localhost scripts]# shc -e 01/02/2021 -v -f welcome.sh shc shll=sh shc [-i]=-c shc [-x]=exec '%s' "$@" shc [-l]= shc opts= shc: cc welcome.sh.x.c -o welcome.sh.x shc: strip welcome.sh.x shc: chmod ug=rwx,o=rx welcome.sh.x
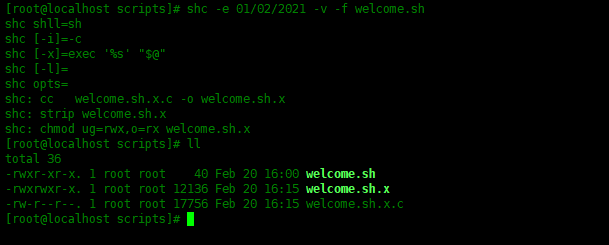
In this example, if someone tries to execute the welcome.sh.x script file, it will prompt that it has expired.
[root@localhost scripts]# ./welcome.sh.x ./welcome.sh.x: has expired! Please contact your provider jahidulhamid@yahoo.com
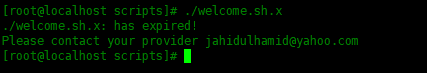
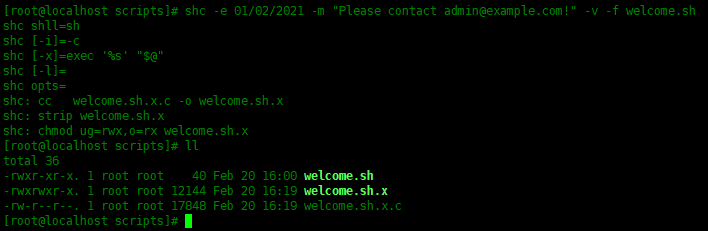
If you want to specify a custom expiration message, you need to add the -m option.
[root@localhost scripts]# shc -e 01/02/2021 -m "Please contact admin@example.com!" -v -f welcome.sh shc shll=sh shc [-i]=-c shc [-x]=exec '%s' "$@" shc [-l]= shc opts= shc: cc welcome.sh.x.c -o welcome.sh.x shc: strip welcome.sh.x shc: chmod ug=rwx,o=rx welcome.sh.x
Using the SHC tool can easily encrypt Shell scripts, effectively protecting the security of the scripts. This article explains how to use the SHC tool to encrypt shell scripts through examples, and also provides methods to solve some common problems. I hope this article can provide Shell script writers with an effective protection method to make script code more secure and reliable.
The above is the detailed content of A must-have for Linux! Use SHC encryption tool to protect shell script code security. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 How to start apache
Apr 13, 2025 pm 01:06 PM
How to start apache
Apr 13, 2025 pm 01:06 PM
The steps to start Apache are as follows: Install Apache (command: sudo apt-get install apache2 or download it from the official website) Start Apache (Linux: sudo systemctl start apache2; Windows: Right-click the "Apache2.4" service and select "Start") Check whether it has been started (Linux: sudo systemctl status apache2; Windows: Check the status of the "Apache2.4" service in the service manager) Enable boot automatically (optional, Linux: sudo systemctl
 What to do if the apache80 port is occupied
Apr 13, 2025 pm 01:24 PM
What to do if the apache80 port is occupied
Apr 13, 2025 pm 01:24 PM
When the Apache 80 port is occupied, the solution is as follows: find out the process that occupies the port and close it. Check the firewall settings to make sure Apache is not blocked. If the above method does not work, please reconfigure Apache to use a different port. Restart the Apache service.
 How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
In Debian systems, readdir system calls are used to read directory contents. If its performance is not good, try the following optimization strategy: Simplify the number of directory files: Split large directories into multiple small directories as much as possible, reducing the number of items processed per readdir call. Enable directory content caching: build a cache mechanism, update the cache regularly or when directory content changes, and reduce frequent calls to readdir. Memory caches (such as Memcached or Redis) or local caches (such as files or databases) can be considered. Adopt efficient data structure: If you implement directory traversal by yourself, select more efficient data structures (such as hash tables instead of linear search) to store and access directory information
 How to restart the apache server
Apr 13, 2025 pm 01:12 PM
How to restart the apache server
Apr 13, 2025 pm 01:12 PM
To restart the Apache server, follow these steps: Linux/macOS: Run sudo systemctl restart apache2. Windows: Run net stop Apache2.4 and then net start Apache2.4. Run netstat -a | findstr 80 to check the server status.
 How debian readdir integrates with other tools
Apr 13, 2025 am 09:42 AM
How debian readdir integrates with other tools
Apr 13, 2025 am 09:42 AM
The readdir function in the Debian system is a system call used to read directory contents and is often used in C programming. This article will explain how to integrate readdir with other tools to enhance its functionality. Method 1: Combining C language program and pipeline First, write a C program to call the readdir function and output the result: #include#include#include#includeintmain(intargc,char*argv[]){DIR*dir;structdirent*entry;if(argc!=2){
 How to learn Debian syslog
Apr 13, 2025 am 11:51 AM
How to learn Debian syslog
Apr 13, 2025 am 11:51 AM
This guide will guide you to learn how to use Syslog in Debian systems. Syslog is a key service in Linux systems for logging system and application log messages. It helps administrators monitor and analyze system activity to quickly identify and resolve problems. 1. Basic knowledge of Syslog The core functions of Syslog include: centrally collecting and managing log messages; supporting multiple log output formats and target locations (such as files or networks); providing real-time log viewing and filtering functions. 2. Install and configure Syslog (using Rsyslog) The Debian system uses Rsyslog by default. You can install it with the following command: sudoaptupdatesud
 How to solve the problem that apache cannot be started
Apr 13, 2025 pm 01:21 PM
How to solve the problem that apache cannot be started
Apr 13, 2025 pm 01:21 PM
Apache cannot start because the following reasons may be: Configuration file syntax error. Conflict with other application ports. Permissions issue. Out of memory. Process deadlock. Daemon failure. SELinux permissions issues. Firewall problem. Software conflict.
 Does the internet run on Linux?
Apr 14, 2025 am 12:03 AM
Does the internet run on Linux?
Apr 14, 2025 am 12:03 AM
The Internet does not rely on a single operating system, but Linux plays an important role in it. Linux is widely used in servers and network devices and is popular for its stability, security and scalability.



