 System Tutorial
System Tutorial
 LINUX
LINUX
 chroot command on Linux: How to run and test applications in an isolated space
chroot command on Linux: How to run and test applications in an isolated space
chroot command on Linux: How to run and test applications in an isolated space
If you are a Linux enthusiast, you may often need to install or uninstall various applications or services on your system. But, did you know that every application or service depends on some shared object files provided by other software packages? If these object files are missing or damaged, your application or service may not work properly or even start. Therefore, knowing how to run and test applications or services in an isolated space is a very useful skill that can help you maintain and optimize your Linux system. This article will introduce a powerful command line tool called chroot, which allows you to create an independent environment on Linux and run and test applications or services in it.
What is chroot in Linux?
Let’s explore chroot in detail, understand its benefits, usage scenarios, how to set it up on a Linux system, and how to get out of (chroot) the environment if necessary.
chroot is change-root, arguably one of the simplest and oldest containerization software, which allows users to safely isolate applications and services. In computing terms, isolation is the confinement of a program into a restricted space, with predefined resources.
If you are familiar with Docker and how it works, you can think of chroot as a greatly simplified version of it. chroot provides an additional layer of isolation and security by changing the root directory of a program, limiting access and visibility.
Basically, you create a separate directory, copy all your program's dependencies into the new directory, and then run the chroot command. This allows programs to run normally while losing access to the underlying file system.
Setting up a program as a chroot environment is a good way to test its reliability in a safe space without changing the files of the actual system. In addition, in a chroot environment, you can reduce the security risks caused by compromised software packages, because in a chroot environment, compromised software packages will not be able to access and modify sensitive system files.
The program can only access and view files imported into the chroot directory, also known as "chroot jail". This prevents the program and its child processes from interfering with the operation of the underlying system.
What is a chroot jail?
A chroot jail is an isolated environment in which chroot programs run and execute. The term chroot jail originates from the concept that processes and their child processes within a chroot environment are unable to access or view the underlying file system and are restricted to the resources reserved for the chroot.
Now that you have a clear understanding of the concept of chroot, let’s get hands-on and learn how to create a chroot jail and execute programs within it.
How to create a chroot jail and execute programs in it
A chroot jail (chroot jail) is essentially a directory that contains all the resources, files, binaries and other dependencies required for the program to run properly.
However, unlike a regular Linux environment, the environment of a chroot jail is strictly restricted and the program cannot access external or additional files and system resources.
For example, to run a Bash shell in a chroot jail, you need to copy the Bash binary and all its dependencies into the chroot directory.
The following are the steps to create a chroot jail and generate a Bash shell:
1. To successfully run a program, you need to copy all its dependencies to the directory of the chroot jail. Let's use the which and ldd commands to find the location of the binary (Bash in this case) and all its dependencies:
┌──(linuxmi㉿linuxmi)-[~/www.linuxmi.com] └─$ which bash /usr/bin/bash ┌──(linuxmi㉿linuxmi)-[~/www.linuxmi.com] └─$ ldd /usr/bin/bash

2. Now that you know the location of the binaries and their dependencies, copy them to the directory you want to convert to a chroot jail. Use the mkdir command to create the necessary directories and the cp command to copy all files into the corresponding directories:
mkdir bin lib lib64 && cp -r /lib/ * ./lib && cp -r /lib64/* ./lib64/ && cp /bin/bash /bin/

3、最后,当程序和它的依赖项复制完成后,你可以使用 sudo 前缀以提升的权限运行 chroot 命令,在所选择的目录中生成 chroot 环境。默认情况下,它将生成一个Bash shell。下面是要输入的命令:
linuxmi@linuxmi:~$ sudo chroot www.linuxmi.com
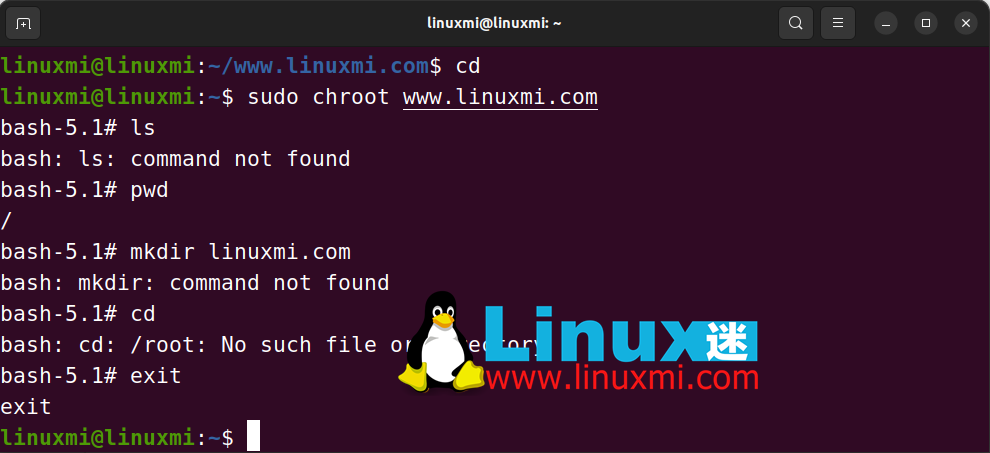
这就是生成chroot监狱并在其中运行程序的所有步骤。
如何逃离chroot监狱
虽然 chroot 监狱对于测试不稳定的软件很有用,但在处理 SSH 连接时也很有用,因为将连接的用户设置为 chroot 环境是保护 SSH 服务器的众多方法之一。
另一方面,如果你是一名渗透测试人员,并且已登录到目标的 SSH 服务器,发现它是一个 chroot 环境,可能会感到沮丧,感觉走投无路。
然而,有很多方法可以逃离错误配置的 chroot 狱,有些方法需要 C 编程技巧,而其他方法可以使用工具自动化。一些简单的 chroot 逃逸方法包括:
- 嵌套的 chroot 调用
- 带有保存的文件描述符的嵌套 chroot 调用
- 根目录挂载方法
- procfs 逃逸
- ptrace 逃逸
请注意,要使用这些方法之一进行 chroot 逃逸,你需要在系统中具有升级的特权。通过访问 chw00t 的 GitHub 存储库,你可以了解更多关于这些逃逸方法的信息,那是一个 chroot 逃逸自动化工具。
现在你应该对 Linux 中的 chroot 了如指掌了
通过本文的介绍,我们了解了chroot是什么、它是如何工作的以及如何实现它,我们还学习了如何创建chroot监狱并在其中执行应用程序或服务,以及如何逃离chroot监狱。chroot是一个简单而强大的工具,可以让你在安全和隔离的空间中运行和测试应用程序或服务。请记住,chroot并不是一个完美的安全解决方案,它有一些局限性和缺陷,因此你应该谨慎地使用它,并结合其他的沙盒或虚拟化技术来提高你的系统的安全性和稳定性。
The above is the detailed content of chroot command on Linux: How to run and test applications in an isolated space. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 How to open web.xml
Apr 03, 2025 am 06:51 AM
How to open web.xml
Apr 03, 2025 am 06:51 AM
To open a web.xml file, you can use the following methods: Use a text editor (such as Notepad or TextEdit) to edit commands using an integrated development environment (such as Eclipse or NetBeans) (Windows: notepad web.xml; Mac/Linux: open -a TextEdit web.xml)
 Four ways to implement multithreading in C language
Apr 03, 2025 pm 03:00 PM
Four ways to implement multithreading in C language
Apr 03, 2025 pm 03:00 PM
Multithreading in the language can greatly improve program efficiency. There are four main ways to implement multithreading in C language: Create independent processes: Create multiple independently running processes, each process has its own memory space. Pseudo-multithreading: Create multiple execution streams in a process that share the same memory space and execute alternately. Multi-threaded library: Use multi-threaded libraries such as pthreads to create and manage threads, providing rich thread operation functions. Coroutine: A lightweight multi-threaded implementation that divides tasks into small subtasks and executes them in turn.
 What is the Linux best used for?
Apr 03, 2025 am 12:11 AM
What is the Linux best used for?
Apr 03, 2025 am 12:11 AM
Linux is best used as server management, embedded systems and desktop environments. 1) In server management, Linux is used to host websites, databases, and applications, providing stability and reliability. 2) In embedded systems, Linux is widely used in smart home and automotive electronic systems because of its flexibility and stability. 3) In the desktop environment, Linux provides rich applications and efficient performance.
 How is Debian Hadoop compatibility
Apr 02, 2025 am 08:42 AM
How is Debian Hadoop compatibility
Apr 02, 2025 am 08:42 AM
DebianLinux is known for its stability and security and is widely used in server, development and desktop environments. While there is currently a lack of official instructions on direct compatibility with Debian and Hadoop, this article will guide you on how to deploy Hadoop on your Debian system. Debian system requirements: Before starting Hadoop configuration, please make sure that your Debian system meets the minimum operating requirements of Hadoop, which includes installing the necessary Java Runtime Environment (JRE) and Hadoop packages. Hadoop deployment steps: Download and unzip Hadoop: Download the Hadoop version you need from the official ApacheHadoop website and solve it
 Do I need to install an Oracle client when connecting to an Oracle database using Go?
Apr 02, 2025 pm 03:48 PM
Do I need to install an Oracle client when connecting to an Oracle database using Go?
Apr 02, 2025 pm 03:48 PM
Do I need to install an Oracle client when connecting to an Oracle database using Go? When developing in Go, connecting to Oracle databases is a common requirement...
 Is Debian Strings compatible with multiple browsers
Apr 02, 2025 am 08:30 AM
Is Debian Strings compatible with multiple browsers
Apr 02, 2025 am 08:30 AM
"DebianStrings" is not a standard term, and its specific meaning is still unclear. This article cannot directly comment on its browser compatibility. However, if "DebianStrings" refers to a web application running on a Debian system, its browser compatibility depends on the technical architecture of the application itself. Most modern web applications are committed to cross-browser compatibility. This relies on following web standards and using well-compatible front-end technologies (such as HTML, CSS, JavaScript) and back-end technologies (such as PHP, Python, Node.js, etc.). To ensure that the application is compatible with multiple browsers, developers often need to conduct cross-browser testing and use responsiveness
 libv are two
Apr 03, 2025 pm 08:03 PM
libv are two
Apr 03, 2025 pm 08:03 PM
I developed a project called Lua-Libuv and am happy to share my experience. The original intention of the project is to explore how to use Libuv (an asynchronous I/O library written in C) to build a simple HTTP server without having to learn the C language in depth. With the help of ChatGPT, I completed the basic code of HTTP.C. When dealing with persistent connections, I successfully implemented closing the connection and freeing resources at the right time. At first I tried to create a simple server that ended the main program by closing the connection, but I had some problems. I've tried sending blocks of data using streaming, and while it works, this blocks the main thread. In the end, I decided to give up on this approach because my goal was not to learn C language in depth. Finally, I
 Unable to log in to mysql as root
Apr 08, 2025 pm 04:54 PM
Unable to log in to mysql as root
Apr 08, 2025 pm 04:54 PM
The main reasons why you cannot log in to MySQL as root are permission problems, configuration file errors, password inconsistent, socket file problems, or firewall interception. The solution includes: check whether the bind-address parameter in the configuration file is configured correctly. Check whether the root user permissions have been modified or deleted and reset. Verify that the password is accurate, including case and special characters. Check socket file permission settings and paths. Check that the firewall blocks connections to the MySQL server.



