 System Tutorial
System Tutorial
 LINUX
LINUX
 Linux file permission settings: symbolic representation VS numerical representation, which one do you prefer?
Linux file permission settings: symbolic representation VS numerical representation, which one do you prefer?
Linux file permission settings: symbolic representation VS numerical representation, which one do you prefer?
File permission settings are quite critical, directly affecting the rights to access, modify, and execute files. Here I would like to introduce two different setting methods as well as my personal experience and opinionsLinux Setting permissions on files, I hope I can give you some suggestions for your reference.
Allow us to first review the basics of Linux file permissions warmly. Every file has three basic permissions: read (r), write (w) and execute (x). These permissions can be assigned appropriately to the owner, group and remaining users.
Please allow me to give you a brief introduction to symbolic representation. When using this method, we need to remember: "r" means read-only, "w" means writable, and "x" means it has execute permission. In addition, we can also grant additional permissions through plus sign(), or cancel corresponding permissions through minus sign(-). As for the user type, "u" represents the owner's Linux system, "g" represents the group to which it belongs, and "o" represents other users.

Another method is to use numerical representation. When using this method, you need to remember that "r" is 4, "w" is 2, and "x" is 1. Just add up the various permission values to get the required number. Among them, the first digit represents the permissions of the owner, the second digit represents the permissions of the group to which it belongs, and the last digit represents the permissions of other users!
Next, let’s take a look at the similarities and differences between these two permission setting methods. The symbolic representation is relatively simple and clear, easy to understand and remember; while the numerical representation is more rigorous, only one number can summarize all permissions, and at the same time, the required permissions can be calculated.
Solinux sets permissions for files, which expression method do you think is more appropriate? If you prefer to be direct and easy to remember and only need to implement a few basic permission settings, symbolic representation may be a good choice for you; and when you are good at calculating and using numbers, or often need to perform complex permission settings, numerical representation Law may be more suitable.
Please take a look at this example to demonstrate how to use two methods to set permissions. Suppose there is a "myfile" file, and you want to give the owner read, write, and execute permissions, the group you belong to read and execute permissions, and exclude other users from any rights. Use symbols to represent rules, and just run the following commands to achieve the corresponding functions:

```
chmod u rwx,g rx,o-rwx myfile
If you choose to use numeric notation, you can run the following command:
chmod 754 myfile
There are some common issues that need to be paid attention to. For example, how to let the owner and the group share the same permissions? How to quickly adjust the permissions of multiple files in batches? When you set file permissions, you can make good use of wildcards to help you modify the permissions of multiple files more easily. For example, with the powerful function of `chmod u rwx *.txt`, you can give the owner full read, write and execute permissions for all your txt files!
Next, let’s talk about security issues. Properly setting file permissions can help prevent unauthorized use and malicious behavior. Be sure to grant only necessary permissions, and regularly check and correct file permission settings.
After comparing the respective advantages and suitable usage environments of the two representation methods, we found that you can freely choose symbolic or numerical representation according to your personal preferences and actual needs. Please note that no matter which expression form you choose, be sure to set file permissions correctly to ensure the security of your system!
The above is the detailed content of Linux file permission settings: symbolic representation VS numerical representation, which one do you prefer?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1389
1389
 52
52
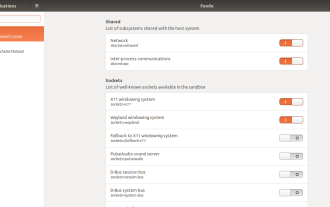 How To Easily Configure Flatpak Apps Permissions With Flatseal
Mar 22, 2025 am 09:21 AM
How To Easily Configure Flatpak Apps Permissions With Flatseal
Mar 22, 2025 am 09:21 AM
Flatpak application permission management tool: Flatseal User Guide Flatpak is a tool designed to simplify Linux software distribution and use. It safely encapsulates applications in a virtual sandbox, allowing users to run applications without root permissions without affecting system security. Because Flatpak applications are located in this sandbox environment, they must request permissions to access other parts of the operating system, hardware devices (such as Bluetooth, network, etc.) and sockets (such as pulseaudio, ssh-auth, cups, etc.). This guide will guide you on how to easily configure Flatpak with Flatseal on Linux
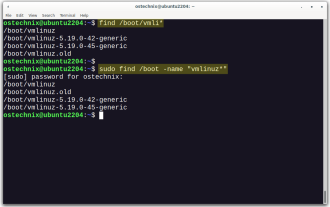 How To List Or Check All Installed Linux Kernels From Commandline
Mar 23, 2025 am 10:43 AM
How To List Or Check All Installed Linux Kernels From Commandline
Mar 23, 2025 am 10:43 AM
Linux Kernel is the core component of a GNU/Linux operating system. Developed by Linus Torvalds in 1991, it is a free, open-source, monolithic, modular, and multitasking Unix-like kernel. In Linux, it is possible to install multiple kernels on a sing
 How To Type Indian Rupee Symbol In Ubuntu Linux
Mar 22, 2025 am 10:39 AM
How To Type Indian Rupee Symbol In Ubuntu Linux
Mar 22, 2025 am 10:39 AM
This brief guide explains how to type Indian Rupee symbol in Linux operating systems. The other day, I wanted to type "Indian Rupee Symbol (₹)" in a word document. My keyboard has a rupee symbol on it, but I don't know how to type it. After
 What is the Linux best used for?
Apr 03, 2025 am 12:11 AM
What is the Linux best used for?
Apr 03, 2025 am 12:11 AM
Linux is best used as server management, embedded systems and desktop environments. 1) In server management, Linux is used to host websites, databases, and applications, providing stability and reliability. 2) In embedded systems, Linux is widely used in smart home and automotive electronic systems because of its flexibility and stability. 3) In the desktop environment, Linux provides rich applications and efficient performance.
 How To Enable Bucklespring Keyboard Sound In Linux
Mar 22, 2025 am 09:07 AM
How To Enable Bucklespring Keyboard Sound In Linux
Mar 22, 2025 am 09:07 AM
Experience the satisfying click of a vintage IBM Model M keyboard, even without owning one! This tutorial shows you how to enable the authentic sound of a bucklespring keyboard on your Linux system using the Bucklespring utility. Table of Contents -
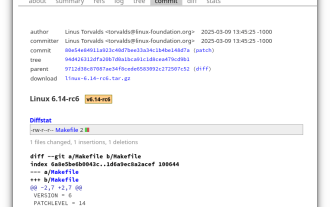 Linux Kernel 6.14 RC6 Released
Mar 24, 2025 am 10:21 AM
Linux Kernel 6.14 RC6 Released
Mar 24, 2025 am 10:21 AM
Linus Torvalds has released Linux Kernel 6.14 Release Candidate 6 (RC6), reporting no significant issues and keeping the release on track. The most notable change in this update addresses an AMD microcode signing issue, while the rest of the updates
 LocalSend - The Open-Source Airdrop Alternative For Secure File Sharing
Mar 24, 2025 am 09:20 AM
LocalSend - The Open-Source Airdrop Alternative For Secure File Sharing
Mar 24, 2025 am 09:20 AM
If you're familiar with AirDrop, you know it's a popular feature developed by Apple Inc. that enables seamless file transfer between supported Macintosh computers and iOS devices using Wi-Fi and Bluetooth. However, if you're using Linux and missing o
 What are the 5 basic components of Linux?
Apr 06, 2025 am 12:05 AM
What are the 5 basic components of Linux?
Apr 06, 2025 am 12:05 AM
The five basic components of Linux are: 1. The kernel, managing hardware resources; 2. The system library, providing functions and services; 3. Shell, the interface for users to interact with the system; 4. The file system, storing and organizing data; 5. Applications, using system resources to implement functions.



