 System Tutorial
System Tutorial
 LINUX
LINUX
 The most commonly used Linux commands: can solve more than 95% of problems
The most commonly used Linux commands: can solve more than 95% of problems
The most commonly used Linux commands: can solve more than 95% of problems
-
Operating System Overview
-
Linux operating system installation
-
Linux File System
-
Linux command operations
-
Linux Permission Management
-
- Users and User Groups
- User operation command
- Permission operation
-
Linux process management
-
Linux Other commonly used commands
-
Linux system software installation
-
- Commonly used software installation
- Common commands for software installation
Operating System Overview
Operating System Operating System, referred to as OS, is a piece of software in layman’s terms, but it is different from general software. The operating system is a computer program that manages and controls computer hardware and software resources. It is the most basic program that runs directly on "bare metal". System software, any other software must be supported by the operating system to run.
Linux operating system installation
For information on Linux installation, read this article - Linux installation tutorial
“
- https://blog.csdn.net/huaijiu123/article/details/82083452
”
Linux File System
-
/var: Contains files, spool files, log files, locked files, temporary files, page format files, etc. that are changed during normal operations. -
/home: Contains user files: parameter setting files, personalized files, documents, data, EMALL, cached data, etc. Each time a user is added, the system will create a new and new file in the home directory based on its user name. A folder with the same name as other users to save their user configuration. -
/proc: Contains phantom files. They do not actually exist on the disk and do not occupy any space (use ls-l to display their size). When viewing these files, they are actually Access information stored in memory that is used to access the system. -
/bin: Contains executable files (binary) required when the system starts. These files can be used by ordinary users. -
/etc: The configuration file directory of the operating system (firewall, startup items) -
/root: is the home directory of the system administrator (also called super user or root user). -
/dev: is the device directory. Devices under Linux are treated as files. In this way, the hardware is abstracted, convenient for reading and writing, network sharing, and needs to be temporarily loaded into the file system. Under normal circumstances, the device will have A separate subdirectory. The contents of these devices will appear in a separate subdirectory.
Linux command operation
-
View current directory command: **
pwd** -
Open folder command: **
cd** -
-
Open the specified folder:
cd [directory name] -
Open the root directory of the current user:
cd ~ -
Return to the upper directory:
cd … -
Return to the directory:
cd - -
Open the root directory:
cd /
-
Open the specified folder:
-
Browse the file list command in the directory: **
ls** -
-
View the file list in the current directory in column format:
ls -l -
View all files in the current directory (including hidden files):
ls -a -
View all files in the current directory in list format:
ls -la
-
View the file list in the current directory in column format:
-
Create file directory command: **
mkdir** -
-
Create a new file directory:
mkdir Folder name -
Create a new multi-level directory recursively:
mkdir -p folder name -
For example, to create a new test directory in the user directory, the command is written as follows:
mkdir -p test/test1/test2/test3How to recursively create a multi-level directory
-
Create a new file directory:
-
Delete file directory command: **
rmkdir** -
-
Delete the specified directory:
rmkdir directory name -
Recursively delete the specified directory and intermediate directories:
rmdir -p directory nameThere is no typo here, there is no letter k
-
Delete the specified directory:
-
Delete file or directory command: **
rm** -
-
Commonly used commands:
rm -rf [directory or file]rm -ri [directory or file] -
Forcefully delete a file or directory:
rm -rf directory or file -
Ask to confirm deletion before deletion:
rm -ri directory or file
-
Commonly used commands:
“
Because the consequences of forced deletion are not very good, it is generally not recommended to use
rm -rfto delete filesIf the r parameter is not followed by the rm command, the directory cannot be deleted, only the files can be deleted
”
-
Copy file or directory command: **
cp** -
-
Recursively copy all files and folders in directory 1 to directory 2:
cp -r [directory 1][directory 2] -
When performing a copy operation, ask the user before overwriting the original directory:
cp -ri [directory 1][directory 2]
-
Recursively copy all files and folders in directory 1 to directory 2:
-
Commands to move files and modify file names: **
mv** -
-
Change the name of folder 1 to folder 2:
mv file 1 file 2(rename the file) -
Move the files in directory 1 to directory 2:
mv directory 2 directory 2(Move the files in directory 1 to directory 2)
-
Change the name of folder 1 to folder 2:
-
Create file command: **
touch** -
- touch file name
-
View and edit file commands: **
vi** -
- The vi command is a powerful file editing command for UNIX operating systems or UNIX-like operating systems. When the user enters the vi file name, he can enter vi mode to view and edit the file content. If the file already exists, the file will be opened directly. , if the file does not exist, the system will open a new, empty file.
The three modes of vi are as follows:
- Command mode
When the user uses the vi command to open a file, it enters the command mode, and the user can enter commands to perform various functions.
- Input mode
If the user wants to modify the file, he can use the following commands to enter the input mode. After the user enters the input mode, he can modify the file at will. Except for the Esc key, any characters entered by the user will be treated as The content is written into the file, and the user can perform related operations on the file by inputting Esc.
- Last line pattern
If the user completes the editing command, he can press esc ":" to enter the last line mode. The user can continue to search the file content, or enter ":wq!" to save the file and exit, or enter " :q!" Force quit file editing.
-
View and edit file commands: **
cat** -
-
Display the contents of a small file:
cat file name -
Create and open a new file:
cat > File Name
-
Display the contents of a small file:
-
View the content at the beginning of the file Command: **
head** -
-
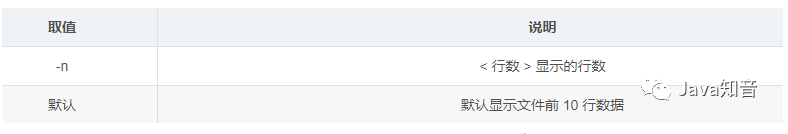
head [parameter] [file name]
-
For example, use the head command to display the n lines of data starting from a file: head -n file name
-
View the end of file content command: **
tail** -
-
Dynamically load the contents of a file (often used to view log files):
tail -f file name -
Display the data of the last few lines of the file:
tail -n line number file name
-
Dynamically load the contents of a file (often used to view log files):
“
Linux Permission Management
”
Users and User Groups
User refers to a collection of a series of permissions in an operating system. Operators can perform certain permitted operations in the system through user names and passwords. Different users can have different permissions. Each user in the Linux operating system has a unique identification UID. When using a command to create a user, if the user's UID is not specified, the system will automatically assign it a UID.
A user group is a collection of users with the same characteristics. In the Linux system, each user belongs to at least one user group. Each user group in the Linux operating system has a unique identifier GID. When using the command to create a user group, if the GID of the user group is not specified, the system will automatically assign it a GID. When using -u to specify a user ID, the user ID should be greater than 500 to avoid conflicts. Because after the Linux operating system is installed, some users will be created by default, so ID numbers within 500 may be occupied.
Linux permission mechanism has the following characteristics:
- The system has a user with the highest authority, whose name is root. The root user belongs to the root user group.
- By default, only root authority can add and delete users in the system.
- After adding a user, if no user group is specified for the user, the system will add a user group with the same name to the user and the user belongs to this group.
- There is no need to log in to switch from root to ordinary user, and login is required to switch from ordinary user to root.
- Root can grant and revoke read, write, and execute permissions for a certain file to the user.
User operation command
-
Switch user command: **
su** -
-
su [username]orsu -[username] -
Both
su[username]andsu -[username]can switch users. The former is similar to temporarily switching users. When using this command to switch to a new user, the user configuration will still be used. Original user configuration, such as environment variables, system variables, etc. When the latter switches users, the environment variables and system settings are all switched to the user configuration of the new user.
-
-
View the current logged in user command: **
whoami** -
View the group command to which the current user belongs: **
groups** -
View current user UID and GID command: **
id** -
Add new user command: **
useradd**
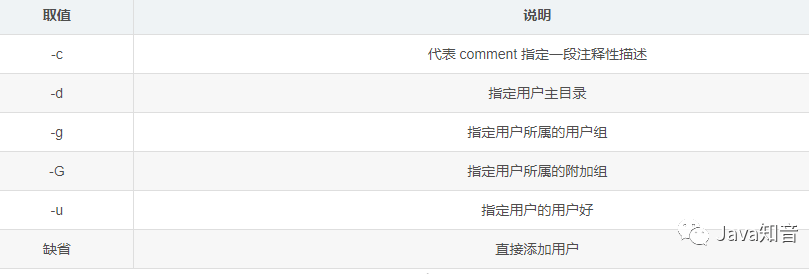
Add a user in the Linux operating system: useradd username
Add a user in the Linux operating system and specify the user UID: useradd -u Specified UID user name
-
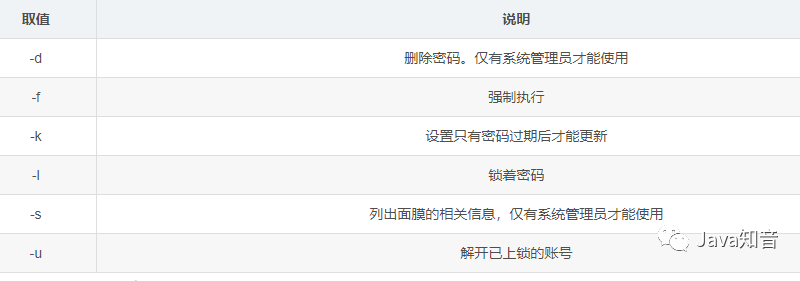
Modify user password command: **
passwd**For example: Modify the password of the current user named sang:passwd sang
After adding a user, the user can log in only if a password is set for him
-
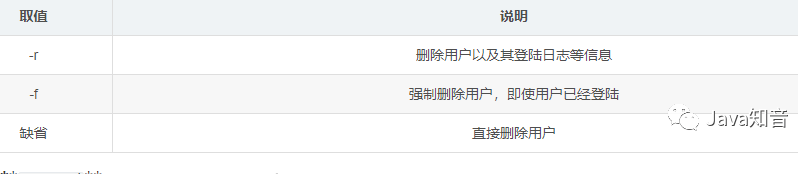
Delete user command: **
userdel** -
-
Delete user:
userdel username -
Delete the user and delete his login information at the same time:
userdel -r username
-
Delete user:
-
Modify user information command: **
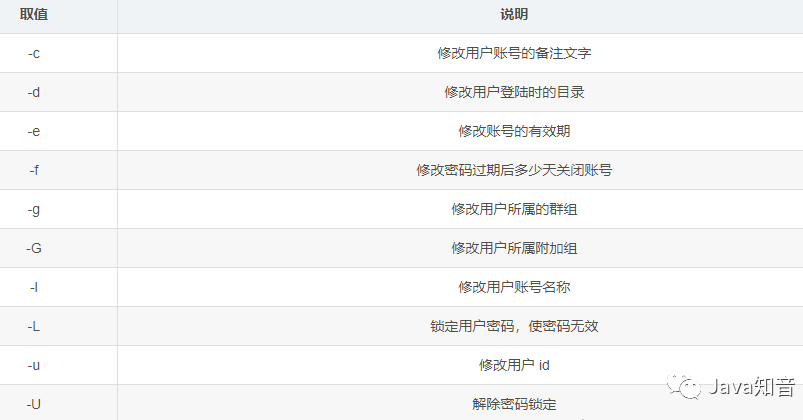
usermod** -
-
Syntax:
usermod [options] [parameters] [username] -
Modify user login name:
usermod -l new username old username -
Modify the group to which the user belongs:
usermod -g new group name user name
-
Syntax:
-
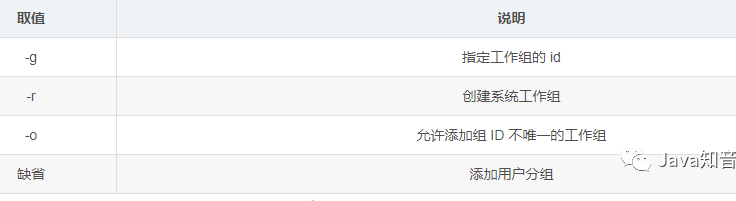
Add user group command: **
groupadd** -
-
Syntax:
groupadd [options] [group name] -
Modify user login name:
groupadd group name -
Modify the group to which the user belongs:
groupadd -g group GID group name
-
Syntax:
Permission operation
The Linux operating system defines three permissions for files: read, write, and execute. Different users or user groups can have different permissions. The system uses "r", "w", and "x" to represent file reading respectively. , write, and execute permissions. Use the ls -l command to view the user's operation permissions on the current directory or file.
List:
drwxr -xr -x. 2 root root 4096 Sep 23 2011 bin
means the following meanings from left to right:
-
d:代表 bin 数目目录而不是文件 -
rwx:代表拥有者具有读、写、执行的权限 -
r -x:代表同组用户具有读、执行的权限,但是没有写权限 -
r -x:代表其他组用户具有读、执行权限,没有写权限
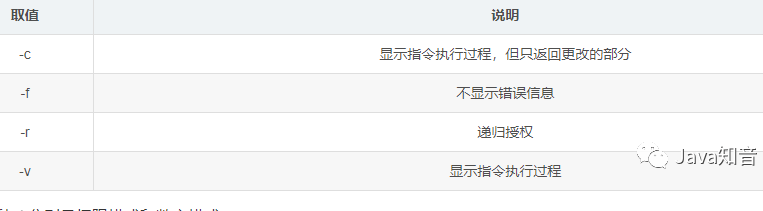
常用的变更权限命令为:chmod
语法:chmod [选项] [参数]
chmod 的参数可以分为两种,分别是权限模式和数字模式。
权限模式:
权限模式使用 u、g、o 分别代表拥有者、同组用户、其他组用户,使用 + 和一代表赋予和收回权限,使用 r、w、x 代表读、写、执行权限。
例如:将文件01的执行权限给当前用户,写权限赋给用户所在的用户组和其他用户。
chmod -r U+X,G+W F01
例如:将文件 f01 的读、写、执行的权限赋给当前用户,将读、写权限赋给用户所在的用户组和其他用户。
chmod -r u=rwx,g=rw,o=rw f01
数字模式:
为了简化授权步骤,用户也可以采用数字模式进行授权,使用二进制的形式代表 r、w、x 三种权限,如 101 (5) =r -x,111 (7) =rwx,100 (3) =r- -
例如:将文件 f01 的读、写、执行的权限赋给当前用户,将读和执行权限赋给用户组、将写和执行权限赋给其他用户。
chmod 753 -r f01
例如:将文件 f01 的读、写、执行权限赋给所有用户。
chmod 777 -r f01
Linux 进程管理
在 Linux 的应用中,我们需要对进程进行管理,如查看某个进程是否启动、以及在必要的时刻,杀掉某个线程。
- 查看进程命令:ps
ps 命令是 Linux 操作系统中查看进程的命令,通过 ps 命令我们可以查看 Linux 操作系统中正在运行的过程,并可以获得进程的 PID(进程的唯一标识),通过 PID 可以对进程进行相应的管理。
ps -ef | grep [进程关键字]
根据进程关键词查看进程命令显示如下,显示的进程列表中第一列表示开启进程的用户,第二列表示进程唯一标识 PID,第三列表示父进程 PPID,第四列表示 CPU 占用资源比列,最后一列表示进程所执行程序的具体位置。
[shang@localhost ~]$ ps -ef|grep sshd root 1829 1 0 May24 ? 00:00:00 /usr/sbin/sshd shang 24166 24100 0 20:17 pts/2 00:00:00 grep sshd [shang@localhost ~]$
- 杀掉进程命令:kill
当系统中有进程进入死循环,或者需要被关闭时,我们可以使用 kill 命令对其关闭。
kill -9 [PID] PID 为 Linux 操作系统中进程的标识
Linux Other commonly used commands
- Clear screen command: clear
- Query command detailed parameter command: man
- Mount command: mnt
- Remote connection service SSH related commands:
-
Start SSH service command:
service sshd start -
Restart SSH service command:
service sshd restart -
Shut down the SSH service command:
service sshd stop
Linux is a remote server in most cases. Developers connect to Linux through remote tools and start the JAR of a certain project. Once the window is closed, the JAR stops running. Therefore, the JAR is generally started through the following command. :nohup java -jar jar-0.0.1-SNAPSHOT.jar &
There is nohup here, which means that the service will not hang when the current window is closed and will continue to run in the background
Linux system software installation
Commonly used software installation
There are three commonly used software installation methods under Linux.
- tar installation: If the developer provides tar, tar.gz, tar.bz format packages (the tar format is packaged and uncompressed, and the package ending in gz is packaged and compressed according to gzip Software package, tar.bz is a software package packaged and compressed in binary mode), which can be installed using tar package. The tar installation method is essentially to decompress the software package provided by the software developer, and then complete the software installation through corresponding configuration.
- rpm installation: The rpm installation method is a software package manager launched by the redhat Linux series. It is similar to the exe installation program under Windows and can be installed directly using the rpm command.
- yum installation: yum installation is still essentially an rpm package installation. The difference from the rpm installation method is that the user can specify the software package to be installed through the yum parameter, and the system will automatically download the corresponding rpm from the Internet. software package. There is no need for users to care about the download address of the software package and the dependencies of the software package.
Common commands for software installation
-
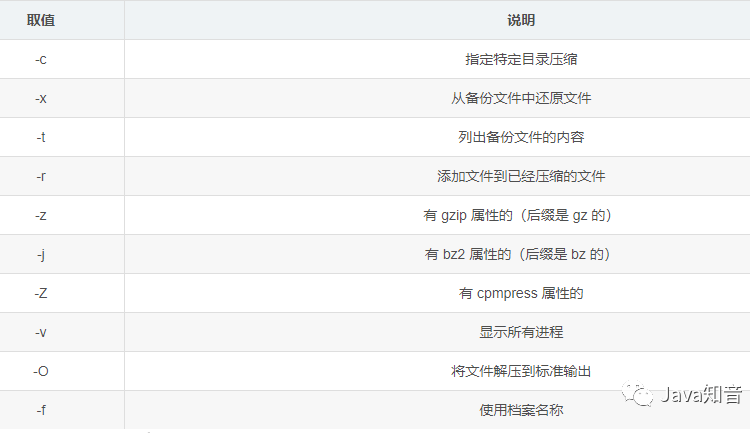
Decompression command:
tar -
Syntax:
tar [options] [compressed package] -
Unzip the gzip package:
tar -zxvf [package name] -
Unzip the bz package:
tar -jxvf [package name] -
Unzip the ordinary package:
tar -xvf [package name]
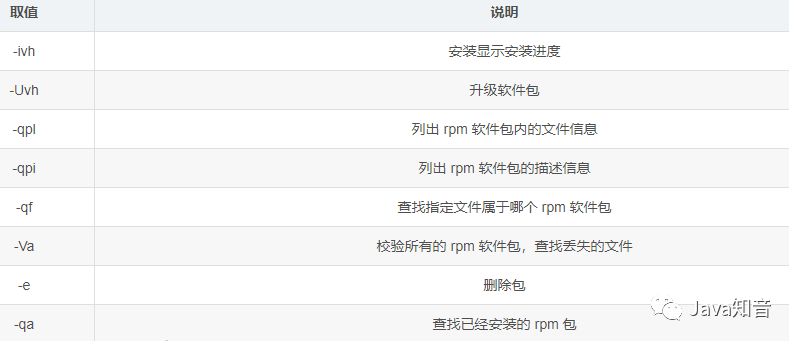
Installation and uninstallation command: rpm
-
Syntax:
rpm [options] [package] -
Check whether a certain software package has been installed:
rpm -qa|grep [package keyword] -
Uninstall an installed software package:
rpm -e Full name of software package -
Install the package and check the progress:
rpm -ivh package path
The above is the detailed content of The most commonly used Linux commands: can solve more than 95% of problems. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 Difference between centos and ubuntu
Apr 14, 2025 pm 09:09 PM
Difference between centos and ubuntu
Apr 14, 2025 pm 09:09 PM
The key differences between CentOS and Ubuntu are: origin (CentOS originates from Red Hat, for enterprises; Ubuntu originates from Debian, for individuals), package management (CentOS uses yum, focusing on stability; Ubuntu uses apt, for high update frequency), support cycle (CentOS provides 10 years of support, Ubuntu provides 5 years of LTS support), community support (CentOS focuses on stability, Ubuntu provides a wide range of tutorials and documents), uses (CentOS is biased towards servers, Ubuntu is suitable for servers and desktops), other differences include installation simplicity (CentOS is thin)
 How to use docker desktop
Apr 15, 2025 am 11:45 AM
How to use docker desktop
Apr 15, 2025 am 11:45 AM
How to use Docker Desktop? Docker Desktop is a tool for running Docker containers on local machines. The steps to use include: 1. Install Docker Desktop; 2. Start Docker Desktop; 3. Create Docker image (using Dockerfile); 4. Build Docker image (using docker build); 5. Run Docker container (using docker run).
 How to install centos
Apr 14, 2025 pm 09:03 PM
How to install centos
Apr 14, 2025 pm 09:03 PM
CentOS installation steps: Download the ISO image and burn bootable media; boot and select the installation source; select the language and keyboard layout; configure the network; partition the hard disk; set the system clock; create the root user; select the software package; start the installation; restart and boot from the hard disk after the installation is completed.
 Centos options after stopping maintenance
Apr 14, 2025 pm 08:51 PM
Centos options after stopping maintenance
Apr 14, 2025 pm 08:51 PM
CentOS has been discontinued, alternatives include: 1. Rocky Linux (best compatibility); 2. AlmaLinux (compatible with CentOS); 3. Ubuntu Server (configuration required); 4. Red Hat Enterprise Linux (commercial version, paid license); 5. Oracle Linux (compatible with CentOS and RHEL). When migrating, considerations are: compatibility, availability, support, cost, and community support.
 How to view the docker process
Apr 15, 2025 am 11:48 AM
How to view the docker process
Apr 15, 2025 am 11:48 AM
Docker process viewing method: 1. Docker CLI command: docker ps; 2. Systemd CLI command: systemctl status docker; 3. Docker Compose CLI command: docker-compose ps; 4. Process Explorer (Windows); 5. /proc directory (Linux).
 Detailed explanation of docker principle
Apr 14, 2025 pm 11:57 PM
Detailed explanation of docker principle
Apr 14, 2025 pm 11:57 PM
Docker uses Linux kernel features to provide an efficient and isolated application running environment. Its working principle is as follows: 1. The mirror is used as a read-only template, which contains everything you need to run the application; 2. The Union File System (UnionFS) stacks multiple file systems, only storing the differences, saving space and speeding up; 3. The daemon manages the mirrors and containers, and the client uses them for interaction; 4. Namespaces and cgroups implement container isolation and resource limitations; 5. Multiple network modes support container interconnection. Only by understanding these core concepts can you better utilize Docker.
 What to do if the docker image fails
Apr 15, 2025 am 11:21 AM
What to do if the docker image fails
Apr 15, 2025 am 11:21 AM
Troubleshooting steps for failed Docker image build: Check Dockerfile syntax and dependency version. Check if the build context contains the required source code and dependencies. View the build log for error details. Use the --target option to build a hierarchical phase to identify failure points. Make sure to use the latest version of Docker engine. Build the image with --t [image-name]:debug mode to debug the problem. Check disk space and make sure it is sufficient. Disable SELinux to prevent interference with the build process. Ask community platforms for help, provide Dockerfiles and build log descriptions for more specific suggestions.
 What computer configuration is required for vscode
Apr 15, 2025 pm 09:48 PM
What computer configuration is required for vscode
Apr 15, 2025 pm 09:48 PM
VS Code system requirements: Operating system: Windows 10 and above, macOS 10.12 and above, Linux distribution processor: minimum 1.6 GHz, recommended 2.0 GHz and above memory: minimum 512 MB, recommended 4 GB and above storage space: minimum 250 MB, recommended 1 GB and above other requirements: stable network connection, Xorg/Wayland (Linux)



