 System Tutorial
System Tutorial
 LINUX
LINUX
 Briefly describe the process of sending and receiving network data packets in Linux system
Briefly describe the process of sending and receiving network data packets in Linux system
Briefly describe the process of sending and receiving network data packets in Linux system
Linux server receives network data packets, what processing needs to be done, and how does it pass the data to the application process step by step? When an application process sends a data packet, how does Linux send the data packet out? Today we will talk about this topic.
Before it is ready to receive network data packets, Linux needs to do a lot of preparation work, such as: initialization of the network subsystem, registration of the protocol stack, initialization of the network card driver, starting the network card, etc. Only after these are ready, Only then can you actually start receiving network packets.
Network Protocol Stack
Before introducing Linux to send and receive network data packets, let us first understand the Linux network protocol stack.
The International Organization for Standardization has formulated the Open System Interconnection Reference Model, which is the OSI network model. The model mainly has 7 layers, namely application layer, presentation layer, session layer, transport layer, Network layer, data link layer and physical layer.
Because the OSI model is too complex, it is only a conceptual and theoretical model with too many layers, which increases the complexity of network work, so it has not been applied on a large scale.
The most common one we use is the TCP/IP network model. The Linux system implements the network protocol stack according to this network model.
The TCP/IP network model has 4 layers, namely application layer, transport layer, network layer and network interface layer. The functions of each layer are as follows:
1, Application layer Corresponds to the upper layer of the OSI reference model, providing users with various services required, such as: FTP, Telnet, DNS, SMTP, etc.
2, Transport layer Corresponds to the transport layer of the OSI reference model, which provides end-to-end communication functions for application layer entities, ensuring the sequential transmission of data packets and the integrity of data. This layer defines two main protocols: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
3, Network layer Corresponds to the network layer of the OSI reference model and mainly solves host-to-host communication problems. It contains protocols designed for the logical transmission of data packets throughout the network. It focuses on reassigning an IP address to the host to complete the addressing of the host. It is also responsible for routing data packets in various networks. There are three main protocols in this layer: Internet Protocol (IP), Internet Group Management Protocol (IGMP), and Internet Control Message Protocol (ICMP).
4, Network interface layer Corresponds to the physical layer and data link layer in the OSI reference model. It is responsible for monitoring the exchange of data between the host and the network. In fact, TCP/IP itself does not define the protocol of this layer. Instead, each network participating in the interconnection uses its own physical layer and data link layer protocols, and then connects to the network access layer of TCP/IP. Address Resolution Protocol (ARP) works at this layer, the data link layer of the OSI reference model. 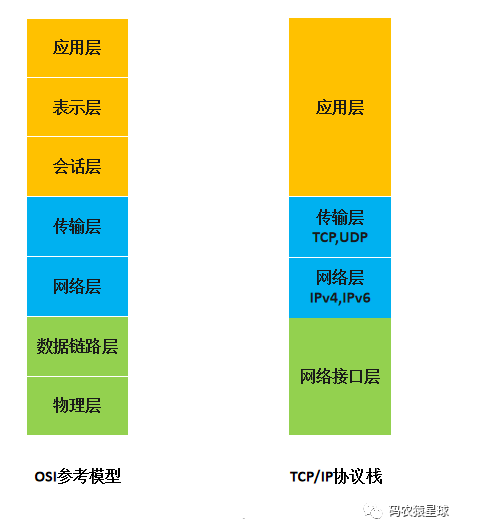
Receive network data packet
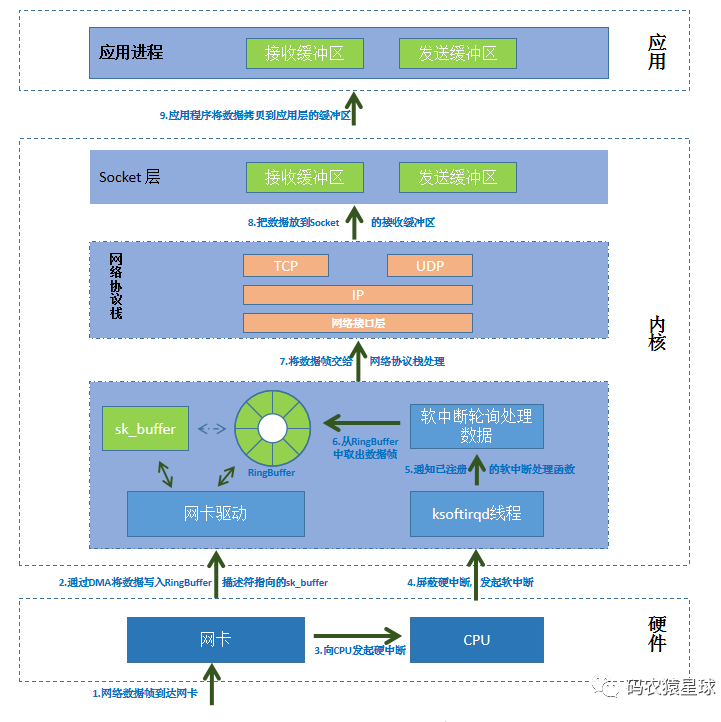
After the network data packet reaches the network card, it is stored in the receiving queue of the network card in FIFO order. The network card writes the network packet to the specified memory address (Ring Buffer) through DMA technology.
Ring Buffer is created and initialized when the network card driver starts, and stores the descriptor of the sk_buff buffer (physical address and size, etc.).
“
When the network packet arrives, get the pointed sk_buff descriptor from the Ring Buffer and write the data to the address through DMA. After the data in sk_buff is handed over to the upper protocol stack for processing, the description in the Ring Buffer is updated to the newly allocated sk_buff.
”
Then the network card initiates a hardware interrupt to the CPU. When the CPU receives the hardware interrupt request, it finds the registered interrupt processing function according to the interrupt registry.
The hardware interrupt handling function will do the following things:
1. Shield the interruption of the network card
“
The purpose is to prevent the CPU from being frequently interrupted and unable to handle other tasks. Masking interrupts tells the network card that it already knows that there is data in the memory. Next time it receives a data packet, it can just write to the memory directly without notifying the CPU.
”
2. Initiate a soft interrupt and restore the interrupt just blocked
“
After the ksoftirqd thread in the kernel receives the soft interrupt, it will call the corresponding soft interrupt processing function to poll and process the data, that is: obtain a data frame from the Ring Buffer, represented by sk_buff, and hand it over as a network packet The network protocol stack is processed layer by layer from bottom to top.
”
The network protocol stack processes network packets as follows:
1. Network interface layer
“
First, the network interface layer checks the legality and correctness of the message. If it is illegal or the message verification is incorrect, discard it. Otherwise, find out the type of upper layer protocol (IPv4 or IPv6) and remove the frame header and frame tail. , and then handed over to the upper layer, the network layer, for processing.
”
2. Network layer
“
The network layer takes out the IP header and determines the next direction of the network packet, whether it is forwarded or handed over to the upper layer. After confirming that the network packet is to be sent to the local machine, the type of the upper layer protocol (such as TCP or UDP) is taken out, the IP header is removed, and then handed over to the transport layer for processing.
”
3. Transport layer
“
After the transport layer takes out the TCP header or UDP header, it finds the corresponding Socket based on the four-tuple [source IP, source port, destination IP, destination port], and copies the data to the Socket's receive buffer.
”
4. Application layer
“
Finally, the application layer program calls the Socket interface to copy the data in the kernel's Socket receiving buffer to the application layer buffer.
”
At this point, the receiving process of a network packet is over.
Send network packet
After we understand the receiving process of network packets, it is easy to understand the sending process of network packets. The sending direction of network packets is exactly opposite to the receiving direction.
First, the application calls the Socket interface to send network packets. This is a system call that will fall from user mode into the socket layer of kernel mode.
The socket layer will apply for a kernel-mode sk_buff memory, copy the data to be sent by the user to the sk_buff memory, and add it to the Socket sending buffer to wait for processing by the network protocol stack.
Since network data packets are raw data when transmitted from the application to the kernel, the protocol stack must add communication conventions to the raw data to ensure that the data can be correctly recognized when it reaches the server. The network protocol stack takes out the data packet from the Socket sending buffer, and then processes it layer by layer from top to bottom according to the layers of the TCP/IP stack (transport layer, network layer, network interface layer). Each layer converts the protocol header Information is continuously inserted into data packets.
The protocol stack's processing flow for sending data packets is as follows:
1. Transport layer
“
At the transport layer, the TCP header will be added to the server and a new copy of sk_buff will be copied. This is because sk_buff will be released when it reaches the network card and the transmission is completed, and the TCP protocol supports retransmission. To ensure Network packets are transmitted reliably. This sk_buff cannot be deleted before receiving the ACK from the other party.
”
2. Network layer
“
At the network layer, it mainly does the following work: selecting routes (confirming the IP of the next hop), filling in IP headers, netfilter filtering, and fragmenting data packets that exceed the MTU size. After processing these tasks, it will be handed over to the network interface layer for processing.
”
3. Network interface layer
“
The network interface layer will perform physical address addressing to find the MAC address of the next hop, fill in the frame header and frame trailer, and put it in the sending queue. Then trigger a soft interrupt to tell the network card driver: There are new network packets in the queue that need to be sent. When the driver receives the notification, it will read the network frame from the send packet queue through DMA, and write the data into the FIFO send queue of the network card through DMA.
”
4. Network card equipment
“
The network card device takes out the data packet from the FIFO transmission queue and sends it to the network; when the transmission is completed, the network card device will trigger a hard interrupt to release memory, mainly to release sk_buff memory and clean up RingBuffer memory. Finally, when the ACK response of this TCP message is received, the transport layer will release the original sk_buff.
”
At this point, the process of sending a network packet is over.
The above is the detailed content of Briefly describe the process of sending and receiving network data packets in Linux system. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 How to use docker desktop
Apr 15, 2025 am 11:45 AM
How to use docker desktop
Apr 15, 2025 am 11:45 AM
How to use Docker Desktop? Docker Desktop is a tool for running Docker containers on local machines. The steps to use include: 1. Install Docker Desktop; 2. Start Docker Desktop; 3. Create Docker image (using Dockerfile); 4. Build Docker image (using docker build); 5. Run Docker container (using docker run).
 How to view the docker process
Apr 15, 2025 am 11:48 AM
How to view the docker process
Apr 15, 2025 am 11:48 AM
Docker process viewing method: 1. Docker CLI command: docker ps; 2. Systemd CLI command: systemctl status docker; 3. Docker Compose CLI command: docker-compose ps; 4. Process Explorer (Windows); 5. /proc directory (Linux).
 What to do if the docker image fails
Apr 15, 2025 am 11:21 AM
What to do if the docker image fails
Apr 15, 2025 am 11:21 AM
Troubleshooting steps for failed Docker image build: Check Dockerfile syntax and dependency version. Check if the build context contains the required source code and dependencies. View the build log for error details. Use the --target option to build a hierarchical phase to identify failure points. Make sure to use the latest version of Docker engine. Build the image with --t [image-name]:debug mode to debug the problem. Check disk space and make sure it is sufficient. Disable SELinux to prevent interference with the build process. Ask community platforms for help, provide Dockerfiles and build log descriptions for more specific suggestions.
 What computer configuration is required for vscode
Apr 15, 2025 pm 09:48 PM
What computer configuration is required for vscode
Apr 15, 2025 pm 09:48 PM
VS Code system requirements: Operating system: Windows 10 and above, macOS 10.12 and above, Linux distribution processor: minimum 1.6 GHz, recommended 2.0 GHz and above memory: minimum 512 MB, recommended 4 GB and above storage space: minimum 250 MB, recommended 1 GB and above other requirements: stable network connection, Xorg/Wayland (Linux)
 vscode cannot install extension
Apr 15, 2025 pm 07:18 PM
vscode cannot install extension
Apr 15, 2025 pm 07:18 PM
The reasons for the installation of VS Code extensions may be: network instability, insufficient permissions, system compatibility issues, VS Code version is too old, antivirus software or firewall interference. By checking network connections, permissions, log files, updating VS Code, disabling security software, and restarting VS Code or computers, you can gradually troubleshoot and resolve issues.
 Can vscode be used for mac
Apr 15, 2025 pm 07:36 PM
Can vscode be used for mac
Apr 15, 2025 pm 07:36 PM
VS Code is available on Mac. It has powerful extensions, Git integration, terminal and debugger, and also offers a wealth of setup options. However, for particularly large projects or highly professional development, VS Code may have performance or functional limitations.
 What is vscode What is vscode for?
Apr 15, 2025 pm 06:45 PM
What is vscode What is vscode for?
Apr 15, 2025 pm 06:45 PM
VS Code is the full name Visual Studio Code, which is a free and open source cross-platform code editor and development environment developed by Microsoft. It supports a wide range of programming languages and provides syntax highlighting, code automatic completion, code snippets and smart prompts to improve development efficiency. Through a rich extension ecosystem, users can add extensions to specific needs and languages, such as debuggers, code formatting tools, and Git integrations. VS Code also includes an intuitive debugger that helps quickly find and resolve bugs in your code.
 How to back up vscode settings and extensions
Apr 15, 2025 pm 05:18 PM
How to back up vscode settings and extensions
Apr 15, 2025 pm 05:18 PM
How to back up VS Code configurations and extensions? Manually backup the settings file: Copy the key JSON files (settings.json, keybindings.json, extensions.json) to a safe location. Take advantage of VS Code synchronization: enable synchronization with your GitHub account to automatically back up all relevant settings and extensions. Use third-party tools: Back up configurations with reliable tools and provide richer features such as version control and incremental backups.



