How to change network location in win7
php editor Xiaoxin brings you the method of changing the network location in Win7. When using Win7 system, we often encounter situations where we need to change the network location, such as switching from a public network to a home network. Changing network locations can help us better manage network connections and shared resources. Below, we will introduce two simple and easy methods to help you quickly change the network location of Win7. Whether you are a novice or a user with certain computer skills, you can easily master these techniques to make network configuration more convenient and flexible.
Note: In fact, the division of NAT types can easily lead to confusion. Many NAT devices will actually use a mix of translation methods instead of just one. Therefore, the definition of a NAT type can only be used to describe a working method, not a device. For example, many NAT devices use symmetric NAT to handle internally initiated connections and also support static port mapping. The latter can be regarded as a variant of full-cone NAT. In addition, in some cases, a public network address and port of the NAT device may be mapped to multiple internal servers at the same time to achieve load balancing. For example, a site that provides WEB servers may have hundreds or even thousands of servers providing HTTP services, but to the outside world, they only appear as one or a few IP addresses.
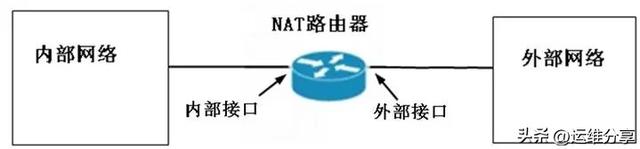
NAT network structure only shows the NAT deployed on the router
NAT working principle: the network is divided into two parts: private network and public network, and the NAT gateway is set from the private network to the public network At the routing exit location, bidirectional traffic must pass through the NAT gateway; network access can only be initiated from the private network side first, and the public network cannot actively access the private network host; the NAT gateway completes two address conversions or translations in the two access directions. , the source information is replaced in the outbound direction, and the destination information is replaced in the inbound direction; the existence of the NAT gateway is transparent to both communicating parties; in order to realize the bidirectional translation function, the NAT gateway needs to maintain an association table to save the session information.Judging from the above characteristics, NAT is mainly used to hide and convert internal network information. However, if you want to achieve communication between hidden devices under NAT (peer-to-peer network transmission), you must perform NAT penetration. In addition, it should be pointed out that although the NAT gateway can achieve a certain degree of transparency, it cannot completely hide the communicating parties because users can carry IP and port information in the data packet instead of only in the IP header. used in.
5. Problems caused by NAT: Peer-to-peer network transmission needs to penetrate NAT: In the definition of IP protocol, in theory, each site with an IP address has considerable ability to obtain services and provide services at the protocol level. There is no difference between different IP addresses. However, the working principle of NAT destroys this feature. If you want to achieve true peer-to-peer network transmission, you need to penetrate NAT. This is the focus of this article. The application layer needs to maintain UDP session connections: Since NAT resources are limited, the converted resources (i.e. ip/port combination) will be recycled according to certain rules, and UDP communication is connectionless, so the application layer protocol based on UDP cannot be used without data transmission. But when you need to maintain the connection, you need to send packets to keep the session from expiring, which is the usual heartbeat and the like. Complications of IP-based access restriction policies 2. Technical points and principles 1. Terminology: 1. Internal Tuple: refers to the tuple composed of the private address and port number of the internal host, that is, the source address of the packet sent by the internal host, A tuple composed of ports; 2. External Tuple: refers to a tuple consisting of external address and port obtained after the internal Tuple undergoes NAT source address/port conversion, that is, the external host receives the NAT converted tuple message, it sees the source address (usually the address of the NAT device) and source port of the message; 3. Target Tuple: refers to the tuple composed of the address and port of the external host, that is, the address of the internal host. A tuple consisting of the destination address and port of the sent message. 4. Hole punch: Penetrate NAT2. NAT type 1). Basic NATconverts the private IP address of the intranet host into the public network IP address one-to-one, without converting TCP/UDP ports. For static NAT and dynamic NAT.
2).NAPTNAPT will not only change the IP address of the IP datagram passing through this NAT device, but also change the TCP/UDP port of the IP datagram.
Full Cone NAT: All requests from the same internal Tuple X are translated by NAT to the same external Tuple Y, regardless of whether these requests belong to the same application or multiple applications. In addition, when the X-Y conversion relationship is established, any external host can use the address and port in Y as the target address and port at any time to send UDP messages to the internal host. , so although this method is simple enough, it is not so safe.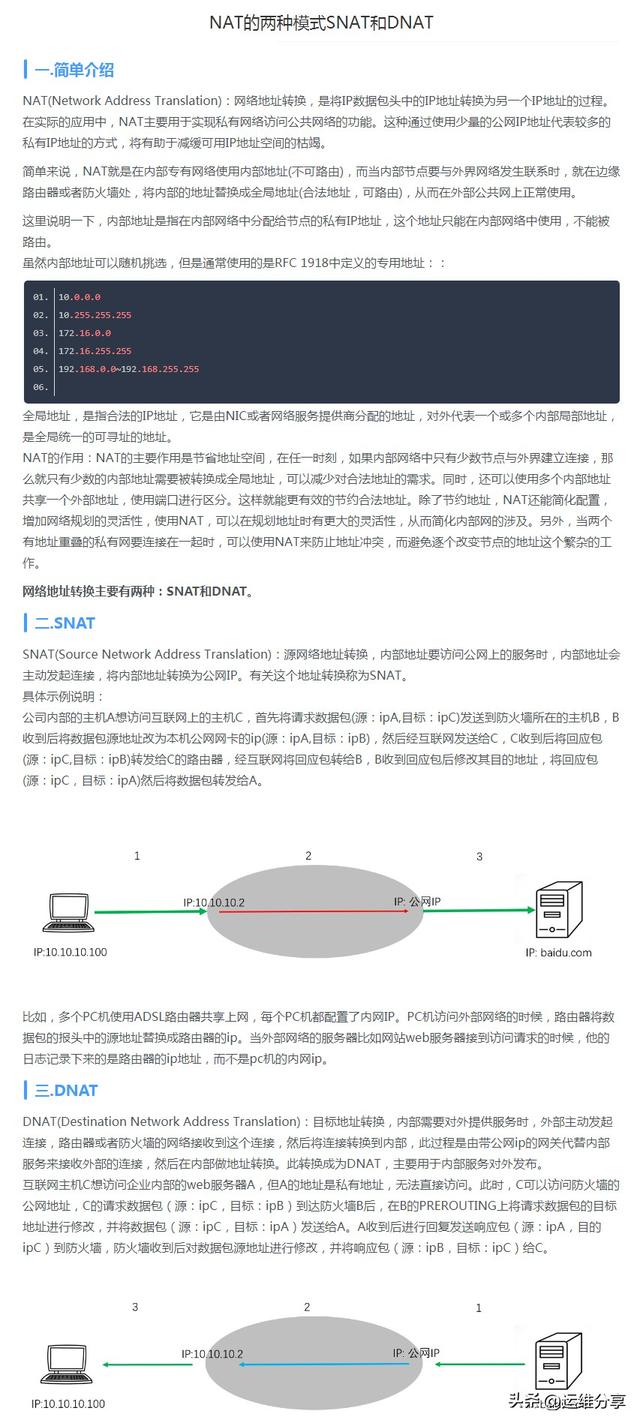
The above is the detailed content of How to change network location in win7. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1389
1389
 52
52
 How to install WinNTSetup into Win11 system_How to install WinNTSetup into Win11 system
May 08, 2024 am 11:19 AM
How to install WinNTSetup into Win11 system_How to install WinNTSetup into Win11 system
May 08, 2024 am 11:19 AM
First download the latest Win11 system ISO image, and then in Win10 system, you can directly right-click on the downloaded ISO image file and select [Load]; if it is under WinPE, WinXP, or Win7 system, you need to use the virtual optical drive tool to load the ISO Image; or you can directly decompress the ISO image file without using a virtual optical drive. Then run WinNTSetup. The software interface is as shown in the figure: First locate the location of the install.wim file. You can find the install.wim file in the sources directory of the Win11 ISO image loaded or decompressed by the virtual optical drive. Then set the location of the boot disk and installation disk. Generally, you are going to put W
 When I turn on the computer, it always stops at the motherboard logo screen. Nothing happens when I press anything, and I can't enter the bios?
Apr 23, 2024 am 09:13 AM
When I turn on the computer, it always stops at the motherboard logo screen. Nothing happens when I press anything, and I can't enter the bios?
Apr 23, 2024 am 09:13 AM
When I turn on the computer, it always stops at the motherboard logo screen. Nothing happens when I press anything, and I can't enter the bios? This is usually because the BIOS battery voltage is too low, and the system time has returned to the BIOS preset time, such as 2000.1.1, 00:00. You can use it after pressing F1 to enter the bios and set the time. Do not turn off the AC power after shutting down at night. Generally, the system time will not be lost when you turn on the computer the next day, and you can still enter the system normally. If the AC power is cut off, the battery voltage cannot sustain the power consumption of the bios, and the computer will be in the same state again the next day when it is turned on. Replacing the bios battery is the ultimate solution. Win11 is stuck on the motherboard logo interface when booting? 1. It is a problem with bios settings. We only need to find the corresponding setting items.
 What should I do if the Win7 taskbar does not display the icon? How to solve the problem of the computer taskbar icon disappearing
Jun 09, 2024 pm 01:49 PM
What should I do if the Win7 taskbar does not display the icon? How to solve the problem of the computer taskbar icon disappearing
Jun 09, 2024 pm 01:49 PM
Recently, many users using Win7 system have found that the icons in the taskbar suddenly disappeared, which makes the operation very inconvenient and they do not know how to solve the problem. This article will introduce to you how to solve the problem of disappearing taskbar icons in Win7 system. Bar! Cause Analysis When encountering such a situation, there are generally two situations: one is that the taskbar on the computer does not really disappear, but is just hidden, and the other is that the taskbar does disappear. Method 1: 1. There is a situation that you need to confirm first, that is, when the mouse is placed at the bottom of the screen, the taskbar will be displayed. You can directly click the mouse on the taskbar and select "Properties". 2. In the dialog box that opens, click & on the "Hide taskbar" option.
 How to clear all desktop background images in Win7? Tips for deleting personalized background images in Win7
Jun 02, 2024 am 09:01 AM
How to clear all desktop background images in Win7? Tips for deleting personalized background images in Win7
Jun 02, 2024 am 09:01 AM
In Win7 system, many users want to delete personalized desktop background images, but do not know how to delete them. This article will show you how to delete personalized background images in Win7 system. 1. First, open the control panel interface of the Win7 system and click to enter the "Appearance and Personalization" settings; 2. Then, in the opened interface, click the "Change Desktop Background" setting; 3. Then, click below "Desktop background" option; 4. Then, select Select all, and then click Clear all. Of course, you can also use it under "Customize", right-click the theme you want to delete, and then click &q on the shortcut menu
 How to connect to mobile phone hotspot network in win7 system
Apr 13, 2024 pm 11:48 PM
How to connect to mobile phone hotspot network in win7 system
Apr 13, 2024 pm 11:48 PM
To connect Windows 7 to a Cellular Hotspot, follow these steps: Open the Wireless Network Connections panel and find the Cellular Hotspot network. Right-click on the hotspot network and select Connect. Verify connection.
 Where is the network discovery in Win7? Tips for enabling the network discovery function in Win7
Jun 04, 2024 am 09:02 AM
Where is the network discovery in Win7? Tips for enabling the network discovery function in Win7
Jun 04, 2024 am 09:02 AM
Many computer users know that network discovery is a network setting. This setting will affect whether the computer can find other computers and devices on the network and whether it can find the computer when other computers on the network are found. So how to enable network discovery in win7? The following computer System Home U Disk Installation will introduce you to the tutorial on how to enable network discovery in win7 system. 1. First, click the "Start Menu" icon on the desktop taskbar and choose to open the "Control Panel" interface. 2. Then, in the interface that opens, set "View by" to "Category", and then choose to enter "Network and Internet"
 Win7 network adapter is missing, how to restore it (methods and steps to solve the problem of Win7 network adapter disappearing)
Apr 23, 2024 pm 06:19 PM
Win7 network adapter is missing, how to restore it (methods and steps to solve the problem of Win7 network adapter disappearing)
Apr 23, 2024 pm 06:19 PM
But sometimes users may encounter the problem that the network adapter suddenly disappears. Win7 operating system is a widely used operating system, which brings great troubles to network connection and use. To help users quickly solve network connection problems, this article will introduce the methods and steps on how to restore the Win7 network adapter. 1. Check the network adapter in the device manager 2. Uninstall and reinstall the network adapter driver. Select, right-click the network adapter and "Uninstall Device" and then restart the computer and install the driver automatically, or go to the official website to download the latest driver and install it manually. . 3. Check whether the device is disabled. Search for "Network Connections" in the start menu, open it, right-click the wireless connection or Ethernet connection, and select "Enable" to ensure that the device has not been disabled.
 How to connect a bluetooth mouse in win7 system
Apr 13, 2024 pm 11:45 PM
How to connect a bluetooth mouse in win7 system
Apr 13, 2024 pm 11:45 PM
How to connect a Bluetooth mouse to a Windows 7 system: Make sure Bluetooth is turned on and the mouse is charged; click "Start" → "Devices and Printers"; click "Add Device"; find the Bluetooth mouse and enter the pairing code (if any); Click Next to complete the connection; move the mouse to verify the connection.




