Can I upgrade win7 to win10 under pe?
php editor Yuzai brings you the answer to "upgrading win7 to win10 under pe". In the process of upgrading from Win7 to Win10, using the PE system can provide a convenient and safe way. The PE system can help you perform data backup and system repair during the upgrade process to avoid data loss and unexpected situations. However, it should be noted that compatibility issues may occur during the upgrade process. It is recommended to perform a system backup before upgrading and ensure the compatibility of hardware devices and software applications. After upgrading, you can enjoy better performance and more functions brought by Win10.
Even though it stopped supporting as early as 2020, many friends still use it.
Indeed, after all, the win7 system is really famous for its stability and speed, plus it takes up less memory/CPU and other advantages.
You said, how could it not make people excited?
Of course, some friends think that Microsoft has stopped supporting it, and the Win7 system should be unusable long ago.
But this is not the case. After all, the Windows system exists more as a tool.

Microsoft has stopped system maintenance and updates, but if we want to use it, let alone the Win7 system, even the XP system.
As long as you want, you can install and use it normally, but it cannot enjoy the update service provided by Microsoft.
So, will there be any functional restrictions on Win7 system?

Actually, if you think about it from another angle, you won’t have this problem.
For us, the Windows system serves more as an open platform, allowing us to use other software programs and the like.
Therefore, it is not difficult for you to see that there are some masters on the Internet who will renovate a new version of Windows system by themselves.

And these versions of Windows systems can be used normally by everyone.
Sorry, the topic is a bit off topic, let’s go back to the win7 system.
In a word, just because the Win7 system stops serving, it does not mean that it cannot be used. As long as the program you want to use is compatible, then there is no problem at all.
Although, in 2019, Microsoft said it would stop services.
But in fact, the group targeted by this service suspension refers to us ordinary people.
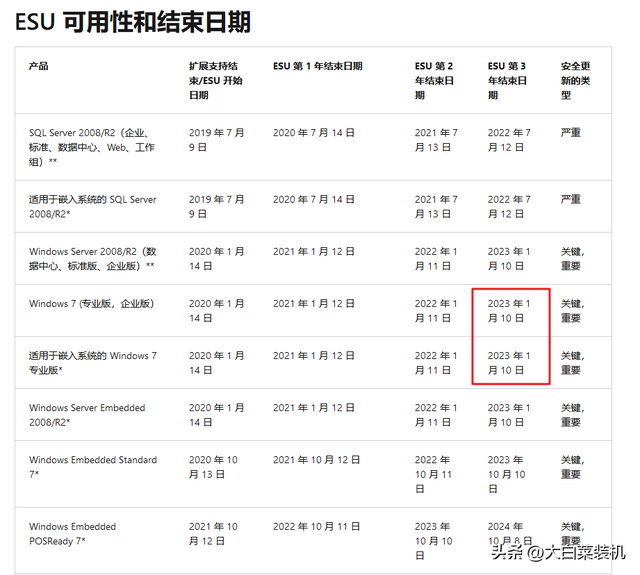
Major enterprise users can still subscribe to security patches through Microsoft’s ESU service, which is a paid method.

Interestingly, according to the data statistics company Statcounter, as of In November 2022, Win7 still holds a market share of 10.25%.
So, from this perspective, the win7 system has always been very active.

However, this time, the win7 system has really completely withdrawn from the stage of history!
Today, Microsoft officially stated that on Tuesday (January 10), the Windows 7 operating system will end ESU (paid extended support).
To put it simply, even if you have money, you can’t get win7 security patches.
Of course, this news is the same as the previous one, and it doesn’t seem to have a great impact on us.
After all, many users in China who use win7 system are ordinary people, and they don’t know or have never thought about spending money to purchase support services.
But, at the same time, you need to know that win7 in this state is more vulnerable to attacks.
In fact, it is now a general trend for win7 system users to upgrade to Win10.
After all, the win10 system has long since been riddled with bugs and has gradually become stable now.
In this era, although it is not as barbaric as it was in 2000, there are all kinds of viruses everywhere that make people feel tired.

But, friends, what is happening now is the craze of various rogue plug-ins.
So, if it is not really necessary to win7 system, the editor highly recommends upgrading to win10 system.
If it is due to configuration reasons, there is also a streamlined version for win10 system.

Currently, the latest version is Windows 10 Enterprise Edition LTSC 2021, and the service end time is January 12, 2027
Friends in need can make a USB boot disk , then download the system image to install it
The above is the detailed content of Can I upgrade win7 to win10 under pe?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 How to use sql datetime
Apr 09, 2025 pm 06:09 PM
How to use sql datetime
Apr 09, 2025 pm 06:09 PM
The DATETIME data type is used to store high-precision date and time information, ranging from 0001-01-01 00:00:00 to 9999-12-31 23:59:59.99999999, and the syntax is DATETIME(precision), where precision specifies the accuracy after the decimal point (0-7), and the default is 3. It supports sorting, calculation, and time zone conversion functions, but needs to be aware of potential issues when converting precision, range and time zones.
 Can I retrieve the database password in Navicat?
Apr 08, 2025 pm 09:51 PM
Can I retrieve the database password in Navicat?
Apr 08, 2025 pm 09:51 PM
Navicat itself does not store the database password, and can only retrieve the encrypted password. Solution: 1. Check the password manager; 2. Check Navicat's "Remember Password" function; 3. Reset the database password; 4. Contact the database administrator.
 How to view database password in Navicat for MariaDB?
Apr 08, 2025 pm 09:18 PM
How to view database password in Navicat for MariaDB?
Apr 08, 2025 pm 09:18 PM
Navicat for MariaDB cannot view the database password directly because the password is stored in encrypted form. To ensure the database security, there are three ways to reset your password: reset your password through Navicat and set a complex password. View the configuration file (not recommended, high risk). Use system command line tools (not recommended, you need to be proficient in command line tools).
 How to delete rows that meet certain criteria in SQL
Apr 09, 2025 pm 12:24 PM
How to delete rows that meet certain criteria in SQL
Apr 09, 2025 pm 12:24 PM
Use the DELETE statement to delete data from the database and specify the deletion criteria through the WHERE clause. Example syntax: DELETE FROM table_name WHERE condition; Note: Back up data before performing a DELETE operation, verify statements in the test environment, use the LIMIT clause to limit the number of deleted rows, carefully check the WHERE clause to avoid misdeletion, and use indexes to optimize the deletion efficiency of large tables.
 How to recover data after SQL deletes rows
Apr 09, 2025 pm 12:21 PM
How to recover data after SQL deletes rows
Apr 09, 2025 pm 12:21 PM
Recovering deleted rows directly from the database is usually impossible unless there is a backup or transaction rollback mechanism. Key point: Transaction rollback: Execute ROLLBACK before the transaction is committed to recover data. Backup: Regular backup of the database can be used to quickly restore data. Database snapshot: You can create a read-only copy of the database and restore the data after the data is deleted accidentally. Use DELETE statement with caution: Check the conditions carefully to avoid accidentally deleting data. Use the WHERE clause: explicitly specify the data to be deleted. Use the test environment: Test before performing a DELETE operation.
 How to add columns in PostgreSQL?
Apr 09, 2025 pm 12:36 PM
How to add columns in PostgreSQL?
Apr 09, 2025 pm 12:36 PM
PostgreSQL The method to add columns is to use the ALTER TABLE command and consider the following details: Data type: Select the type that is suitable for the new column to store data, such as INT or VARCHAR. Default: Specify the default value of the new column through the DEFAULT keyword, avoiding the value of NULL. Constraints: Add NOT NULL, UNIQUE, or CHECK constraints as needed. Concurrent operations: Use transactions or other concurrency control mechanisms to handle lock conflicts when adding columns.
 Navicat's method to view PostgreSQL database password
Apr 08, 2025 pm 09:57 PM
Navicat's method to view PostgreSQL database password
Apr 08, 2025 pm 09:57 PM
It is impossible to view PostgreSQL passwords directly from Navicat, because Navicat stores passwords encrypted for security reasons. To confirm the password, try to connect to the database; to modify the password, please use the graphical interface of psql or Navicat; for other purposes, you need to configure connection parameters in the code to avoid hard-coded passwords. To enhance security, it is recommended to use strong passwords, periodic modifications and enable multi-factor authentication.
 How to clean all data with redis
Apr 10, 2025 pm 05:06 PM
How to clean all data with redis
Apr 10, 2025 pm 05:06 PM
How to clean all Redis data: Redis 2.8 and later: The FLUSHALL command deletes all key-value pairs. Redis 2.6 and earlier: Use the DEL command to delete keys one by one or use the Redis client to delete methods. Alternative: Restart the Redis service (use with caution), or use the Redis client (such as flushall() or flushdb()).




