Introduction to accurately detecting Linux kernel vulnerabilities
The usual mode of quoting open source software is to introduce the dynamic library or jar package of open source software. Therefore, the false alarm rate of vulnerabilities will be very low during vulnerability detection, but it is different for the Linux kernel. Since the Linux kernel function module is very It is rich and large, and will be tailored accordingly according to business needs during actual use. Therefore, how to achieve accurate vulnerability detection and reduce the false positive rate of vulnerability detection in this scenario is particularly prominent.
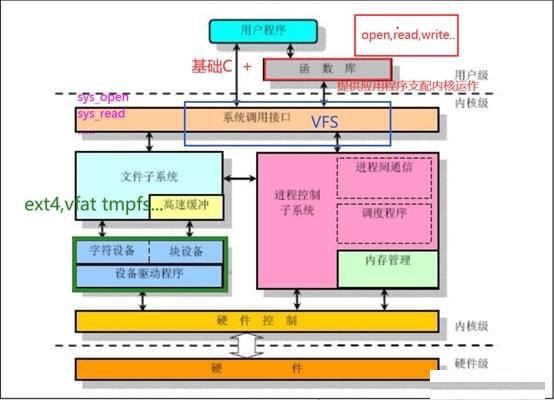
Linux kernel structure:
The Linux kernel is composed of seven parts, and each different part is composed of multiple kernel modules. The structural block diagram is as follows:
Linux cropping scene analysis:
By analyzing the Linux kernel source code, you can see that the implementation codes of different modules are stored in different directories. At the same time, you can use the information configured in config during compilation to control which modules are compiled into the final binary and which modules are trimmed. For example, taking the IPV6 module as an example, the configuration name that controls this module is CONFIG_IPV6. If the configuration item is set to y, it means that the function module has not been compiled into the final binary file, as shown below:
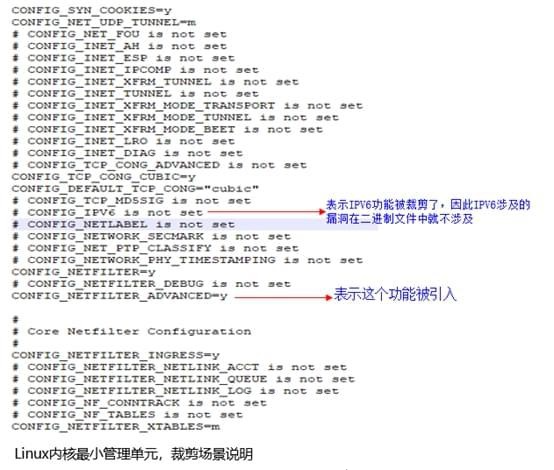
If the function module is cut, even if the vulnerability has not been patched, the vulnerabilities existing in the function module will not be affected in the binary. Therefore, vulnerabilities related to IPV6 will not be affected during vulnerability detection. It should be clearly marked in the report that it is not affected by this vulnerability, such as CVE-2013-0343 (the function ipv6_create_tempaddr in net/ipv6/addrconf.c in versions before Linux kernel 3.8 does not correctly handle the IPv6 temporary address generation problem. allows a remote attacker to cause a denial of service and then obtain sensitive information via ICMPv6 Router Advertisement (RA) messages.).
Analysis of the reasons why binary SCA tools in the industry cannot detect:
Why the usual binary SCA tools in the industry cannot achieve accurate detection? The reason is because the binary SCA tools in the industry associate a list of known vulnerabilities based on the name and version number of the detected open source software, and this through the tailoring function When applying the Linux kernel using the module method, the name and version number of the open source software will not change, so the tool cannot accurately detect it.
How the binary SCA tool implements this function:
To achieve accurate detection of known vulnerabilities in Linux kernel tailoring scenarios, binary SCA tools must implement updated fine-grained detection technology based on source code file granularity based on the original detection of open source software names and version numbers. , function granular detection capabilities, thereby achieving accurate detection of known vulnerabilities in tailoring scenarios, that is, you can know which codes are compiled into the final binary file and which codes are not included in the compilation. At the same time, the vulnerability library must also support fine-grained dimensions, that is, the vulnerability information must accurately locate the code fragments in which files and functions are introduced.
Taking CVE-2013-0343 as an example, by analyzing the vulnerability description information and the Linux kernel source code, we can obtain the positioning information related to the vulnerability and the following location codes:
"CVE-2013-0343": {
"net/ipv6/addrconf.c": [
“addrconf_add_ifaddr”,
“addrconf_dad_begin”,
“addrconf_dad_stop”,
“addrconf_dad_work”,
“addrconf_del_ifaddr”,
“addrconf_prefix_rcv”,
“addrconf_verify_rtnl”,
“addrconf_verify_work”,
“inet6_addr_add”,
“inet6_addr_del”,
“inet6_addr_modify”,
“inet6_rtm_deladdr”,
“inet6_rtm_newaddr”,
“inet6_set_iftoken”,
“inet6_set_link_af”,
“ipv6_create_tempaddr”,
“manage_tempaddrs”
]
}
Summarize
Based on the principle that if the source code that introduces the vulnerability does not participate in compiling the binary, then the compiled binary does not have the vulnerability; therefore, as long as the binary SCA tool can detect that the source code in the above location does not participate in compiling the final vmlinux binary file, then this vmlinux file is not affected by the CVE-2013-0343 vulnerability.
If binary SCA tools want to better assist security personnel in implementing security audits and reduce the false positive rate of vulnerability detection, they must develop to a more fine-grained detection dimension, not just at the level of open source software, but also on vulnerabilities. Library requirements also pose challenges for fine-grained accurate information.
The above is the detailed content of Introduction to accurately detecting Linux kernel vulnerabilities. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1392
1392
 52
52
 How to view the docker process
Apr 15, 2025 am 11:48 AM
How to view the docker process
Apr 15, 2025 am 11:48 AM
Docker process viewing method: 1. Docker CLI command: docker ps; 2. Systemd CLI command: systemctl status docker; 3. Docker Compose CLI command: docker-compose ps; 4. Process Explorer (Windows); 5. /proc directory (Linux).
 What computer configuration is required for vscode
Apr 15, 2025 pm 09:48 PM
What computer configuration is required for vscode
Apr 15, 2025 pm 09:48 PM
VS Code system requirements: Operating system: Windows 10 and above, macOS 10.12 and above, Linux distribution processor: minimum 1.6 GHz, recommended 2.0 GHz and above memory: minimum 512 MB, recommended 4 GB and above storage space: minimum 250 MB, recommended 1 GB and above other requirements: stable network connection, Xorg/Wayland (Linux)
 vscode cannot install extension
Apr 15, 2025 pm 07:18 PM
vscode cannot install extension
Apr 15, 2025 pm 07:18 PM
The reasons for the installation of VS Code extensions may be: network instability, insufficient permissions, system compatibility issues, VS Code version is too old, antivirus software or firewall interference. By checking network connections, permissions, log files, updating VS Code, disabling security software, and restarting VS Code or computers, you can gradually troubleshoot and resolve issues.
 Can vscode be used for mac
Apr 15, 2025 pm 07:36 PM
Can vscode be used for mac
Apr 15, 2025 pm 07:36 PM
VS Code is available on Mac. It has powerful extensions, Git integration, terminal and debugger, and also offers a wealth of setup options. However, for particularly large projects or highly professional development, VS Code may have performance or functional limitations.
 What is vscode What is vscode for?
Apr 15, 2025 pm 06:45 PM
What is vscode What is vscode for?
Apr 15, 2025 pm 06:45 PM
VS Code is the full name Visual Studio Code, which is a free and open source cross-platform code editor and development environment developed by Microsoft. It supports a wide range of programming languages and provides syntax highlighting, code automatic completion, code snippets and smart prompts to improve development efficiency. Through a rich extension ecosystem, users can add extensions to specific needs and languages, such as debuggers, code formatting tools, and Git integrations. VS Code also includes an intuitive debugger that helps quickly find and resolve bugs in your code.
 How to run java code in notepad
Apr 16, 2025 pm 07:39 PM
How to run java code in notepad
Apr 16, 2025 pm 07:39 PM
Although Notepad cannot run Java code directly, it can be achieved by using other tools: using the command line compiler (javac) to generate a bytecode file (filename.class). Use the Java interpreter (java) to interpret bytecode, execute the code, and output the result.
 What is the main purpose of Linux?
Apr 16, 2025 am 12:19 AM
What is the main purpose of Linux?
Apr 16, 2025 am 12:19 AM
The main uses of Linux include: 1. Server operating system, 2. Embedded system, 3. Desktop operating system, 4. Development and testing environment. Linux excels in these areas, providing stability, security and efficient development tools.
 How to use VSCode
Apr 15, 2025 pm 11:21 PM
How to use VSCode
Apr 15, 2025 pm 11:21 PM
Visual Studio Code (VSCode) is a cross-platform, open source and free code editor developed by Microsoft. It is known for its lightweight, scalability and support for a wide range of programming languages. To install VSCode, please visit the official website to download and run the installer. When using VSCode, you can create new projects, edit code, debug code, navigate projects, expand VSCode, and manage settings. VSCode is available for Windows, macOS, and Linux, supports multiple programming languages and provides various extensions through Marketplace. Its advantages include lightweight, scalability, extensive language support, rich features and version




