 Computer Tutorials
Computer Tutorials
 Computer Knowledge
Computer Knowledge
 What should I do if there is a virus when inserting the USB disk?
What should I do if there is a virus when inserting the USB disk?
What should I do if there is a virus when inserting the USB disk?
php editor Zimo will introduce to you what we should do when a virus is found after inserting the USB flash drive. First, avoid opening any files in the USB drive to avoid further spread of the virus. Secondly, disconnect the USB flash drive from the computer promptly to prevent viruses from infecting other files. Next, we can use anti-virus software to fully scan the USB flash drive and remove viruses. During this process, you should ensure that the anti-virus software is the latest version and update the virus database in a timely manner. If the virus cannot be removed, you can try using a professional virus removal tool. Finally, in order to avoid similar situations from happening again, we should develop a good habit of using USB flash drives safely, do not insert other people's USB flash drives at will, conduct anti-virus checks on USB flash drives regularly, and back up important data regularly.
 Method 1: Repair through U disk properties
Method 1: Repair through U disk propertiesMany people will have this question: Can the U disk still be used if there is a virus in it? Yes, as long as we repair the U disk through the properties of the U disk, it can be used normally after checking for viruses. The specific operations are as follows:
Demo model: Dell optiplex 7050
System version: Windows 10
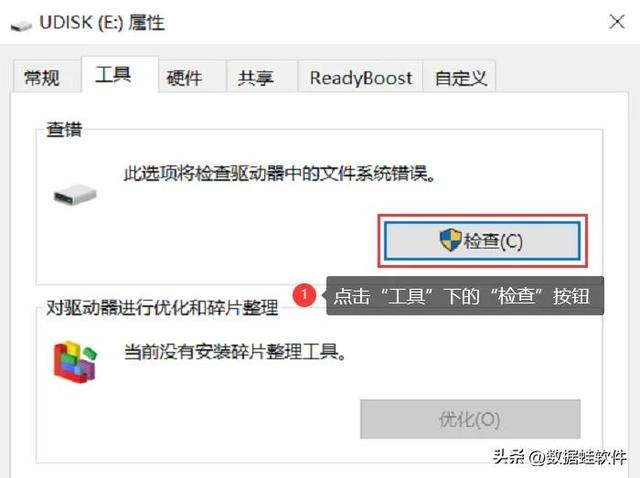
Step 1: After inserting the USB flash drive into the computer, open [This Computer] on the computer desktop. Find the U disk icon, right-click [Properties];
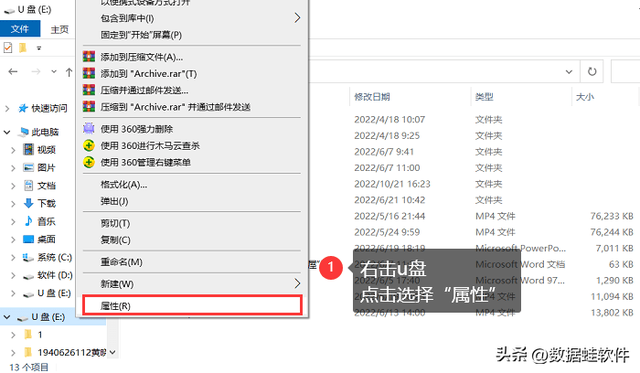
Step 2: In the open window, switch to the [Tools] interface and click [Check] . Then select [Scan and Repair Drive].
What should I do if I open the U disk and find that there is a virus in the U disk? We can also repair it by formatting the USB disk. The specific operation is as follows:
Demo model: Dell optiplex 7050
System version: Windows 10
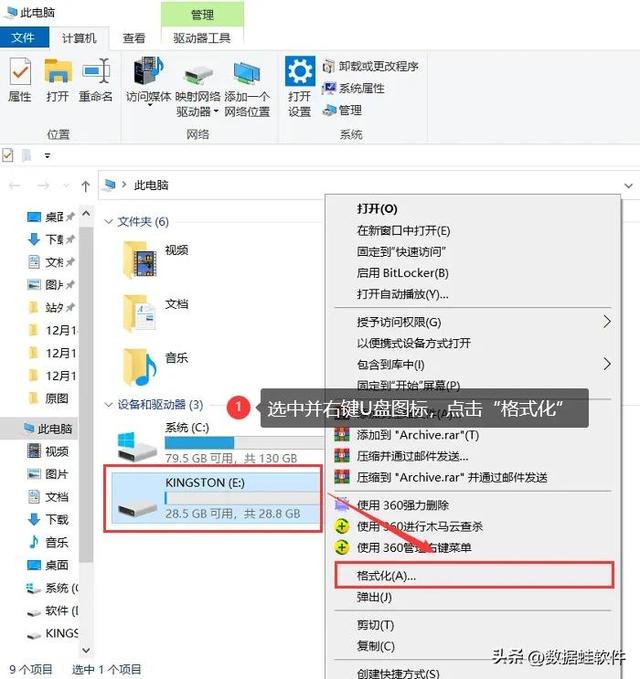
Step 1: Also open the [This Computer] icon, right-click the U disk, and click [Format] under the column;
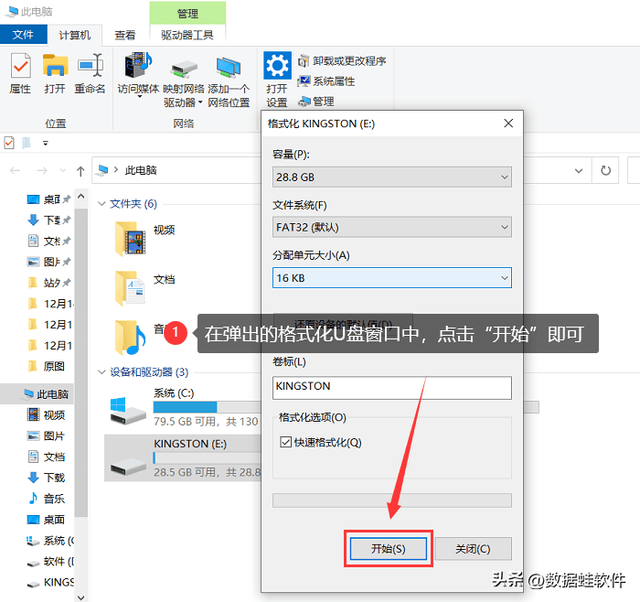
Step 2: In the pop-up U disk format window, select [Quick Format] and click [Start]. After the formatting is completed, the virus in the USB flash drive has also been cleaned.
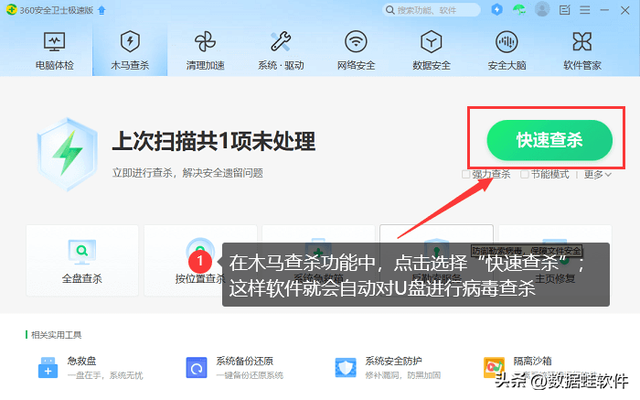
In addition to the above method of checking and killing viruses through U disk, U disk has viruses How to deal with it? We can also use third-party software-360 Security Guard to repair the USB flash drive. The specific operations are as follows:
Demo model: Dell optiplex 7050
System version: Windows 10
Software version: 360 Security Guard 13.0
Step 1: Open the software, find and click [Trojan Killer];
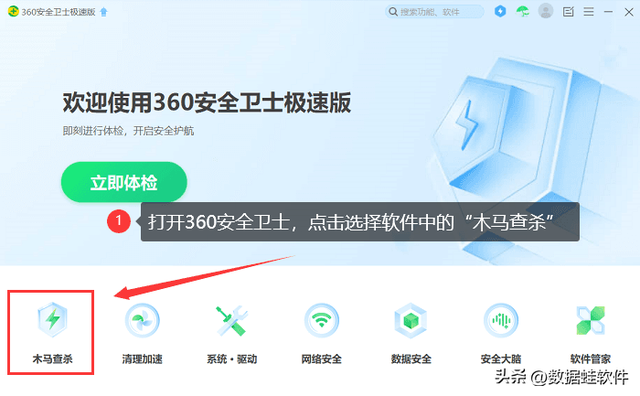
Step 2 : Then select [Quick Scan and Kill] to let the software scan and kill viruses on your computer.
#How to recover the data after the USB disk is formatted?
# There is a virus in the U disk. After we format it, all the data in it will be cleared. If you want to recover the important data inside, you can use software to recover it. Here we take [Data Frog Data Recovery Expert] as an example.
This software can not only recover data after formatting of U disk, but also recover data due to different situations such as system crash, partition problem, empty recycle bin, memory card data loss, hard disk data loss, etc. The specific operations are as follows:
Data recovery expert software download link: https://www.shujuwa.net/shujuhuifu/
Demo model :Dell optiplex 7050
System version: Windows 10
Software version: Datafrog Data Recovery Expert 3.1.6
Step 1: Open the software, Select the file type and file location you want to scan, and click [Scan];
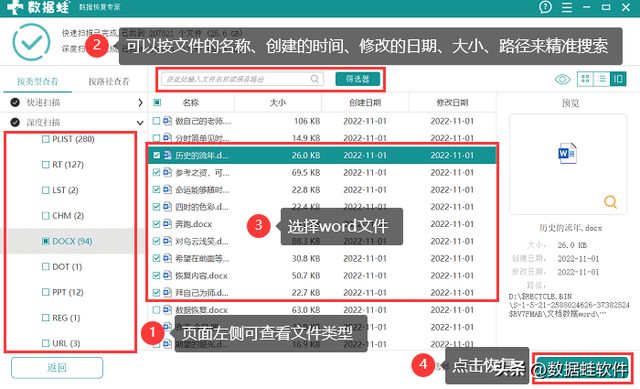
Step 2: The quick scan is over and you can select the file. If you haven't found all the files, use [Deep Scan] to help you find more data. At this time, you can click the file format on the left side of the page to view it, or you can enter the file name, time, date, etc. in [Filter] to accurately search. Select all the files to be recovered and click [Recover];
Step 3: Select the save location. If the save is successful, you can open it for viewing.
Note: File recovery is uncertain, and the specific recovery results are subject to the results of the software scan.
The operation of U disk virus is mainly through the Autorun.inf file, and then writing the corresponding code and implanting the virus program. If the user clicks on the virus by mistake, it will run automatically. What should I do if the USB disk has a virus? You can choose the above methods of repairing USB flash drives according to your actual situation.
Previous recommendations:
What should I do if my computer crashes? Super simple method
How to retrieve notebook data? Laptop data recovery, 6 tutorials
What should I do if files are accidentally deleted? Recover accidentally deleted data with these 4 methods
The above is the detailed content of What should I do if there is a virus when inserting the USB disk?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
 How to solve mysql cannot be started
Apr 08, 2025 pm 02:21 PM
How to solve mysql cannot be started
Apr 08, 2025 pm 02:21 PM
There are many reasons why MySQL startup fails, and it can be diagnosed by checking the error log. Common causes include port conflicts (check port occupancy and modify configuration), permission issues (check service running user permissions), configuration file errors (check parameter settings), data directory corruption (restore data or rebuild table space), InnoDB table space issues (check ibdata1 files), plug-in loading failure (check error log). When solving problems, you should analyze them based on the error log, find the root cause of the problem, and develop the habit of backing up data regularly to prevent and solve problems.
 Solutions to the errors reported by MySQL on a specific system version
Apr 08, 2025 am 11:54 AM
Solutions to the errors reported by MySQL on a specific system version
Apr 08, 2025 am 11:54 AM
The solution to MySQL installation error is: 1. Carefully check the system environment to ensure that the MySQL dependency library requirements are met. Different operating systems and version requirements are different; 2. Carefully read the error message and take corresponding measures according to prompts (such as missing library files or insufficient permissions), such as installing dependencies or using sudo commands; 3. If necessary, try to install the source code and carefully check the compilation log, but this requires a certain amount of Linux knowledge and experience. The key to ultimately solving the problem is to carefully check the system environment and error information, and refer to the official documents.
 How to use sql datetime
Apr 09, 2025 pm 06:09 PM
How to use sql datetime
Apr 09, 2025 pm 06:09 PM
The DATETIME data type is used to store high-precision date and time information, ranging from 0001-01-01 00:00:00 to 9999-12-31 23:59:59.99999999, and the syntax is DATETIME(precision), where precision specifies the accuracy after the decimal point (0-7), and the default is 3. It supports sorting, calculation, and time zone conversion functions, but needs to be aware of potential issues when converting precision, range and time zones.
 Can I retrieve the database password in Navicat?
Apr 08, 2025 pm 09:51 PM
Can I retrieve the database password in Navicat?
Apr 08, 2025 pm 09:51 PM
Navicat itself does not store the database password, and can only retrieve the encrypted password. Solution: 1. Check the password manager; 2. Check Navicat's "Remember Password" function; 3. Reset the database password; 4. Contact the database administrator.
 How to backup and restore database after mysql installation
Apr 08, 2025 am 11:45 AM
How to backup and restore database after mysql installation
Apr 08, 2025 am 11:45 AM
There is no absolutely optimal MySQL database backup and recovery solution, and it needs to be selected based on the amount of data, business importance, RTO and RPO. 1. Logical backup (mysqldump) is simple and easy to use, suitable for small databases, but slow and huge files; 2. Physical backup (xtrabackup) is fast, suitable for large databases, but is more complicated to use. The backup strategy needs to consider the backup frequency (RPO decision), backup method (data quantity and time requirement decision) and storage location (off-site storage is more secure), and regularly test the backup and recovery process to avoid backup file corruption, permission problems, insufficient storage space, network interruption and untested issues, and ensure data security.
 Does mysql need the internet
Apr 08, 2025 pm 02:18 PM
Does mysql need the internet
Apr 08, 2025 pm 02:18 PM
MySQL can run without network connections for basic data storage and management. However, network connection is required for interaction with other systems, remote access, or using advanced features such as replication and clustering. Additionally, security measures (such as firewalls), performance optimization (choose the right network connection), and data backup are critical to connecting to the Internet.
 How to view database password in Navicat for MariaDB?
Apr 08, 2025 pm 09:18 PM
How to view database password in Navicat for MariaDB?
Apr 08, 2025 pm 09:18 PM
Navicat for MariaDB cannot view the database password directly because the password is stored in encrypted form. To ensure the database security, there are three ways to reset your password: reset your password through Navicat and set a complex password. View the configuration file (not recommended, high risk). Use system command line tools (not recommended, you need to be proficient in command line tools).
 Does mysql need a server
Apr 08, 2025 pm 02:12 PM
Does mysql need a server
Apr 08, 2025 pm 02:12 PM
For production environments, a server is usually required to run MySQL, for reasons including performance, reliability, security, and scalability. Servers usually have more powerful hardware, redundant configurations and stricter security measures. For small, low-load applications, MySQL can be run on local machines, but resource consumption, security risks and maintenance costs need to be carefully considered. For greater reliability and security, MySQL should be deployed on cloud or other servers. Choosing the appropriate server configuration requires evaluation based on application load and data volume.



