How to protect USB disk
php editor Apple will share with you some methods on U disk protection. In modern society, USB flash drives have become an indispensable storage tool in our lives. However, due to their easy loss and vulnerability to viruses, our important data sometimes faces the risk of leakage. Therefore, it is particularly important to know how to protect data on USB flash drives. This article will introduce you to some simple and effective USB flash drive protection methods to keep your data safe and reliable.
For example, the WannaCry Bitcoin ransomware virus that caused a global sensation in the past few years looks awesome, but in the end it only extorted thousands of dollars.
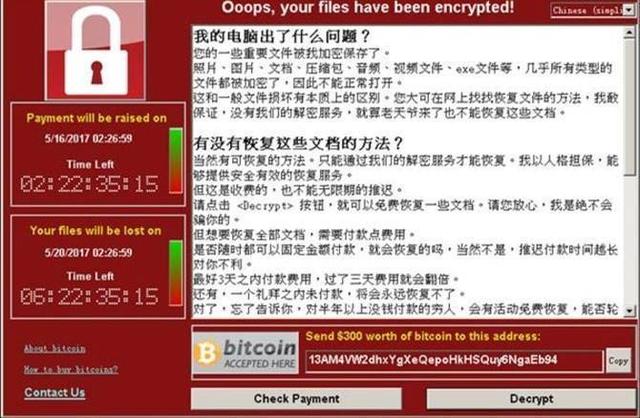
Developing a virus is indeed a costly task. Not only do you need to consider the risk of being caught or fined, but you also need to consider the development time, server and Translation and other costs. These costs cannot be measured in thousands of dollars, so developing viruses is indeed a thankless task.
But in China, there is a type of place where most of the viruses on the Chinese Internet are always hidden.
Those are the print shops in major cities, especially those inside and near schools, which can be called a picture book of the Chinese virus.

These viruses often sneak into your computer secretly, delete your files, and turn your files into garbled characters.
Xuebajun was often tricked when he was still a student. Fortunately, there were no mistakes when printing his graduation thesis.

Considering that it is also the graduation season recently, Xueba Jun will teach you a trick to make your U disk invulnerable to viruses. Use U disk You can also learn how to transfer files from disk to disk.
First we open the USB flash drive and create a new "text document" in it.
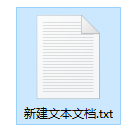
Then change the name of this text document to "Autorun.inf".
Note that the “.txt” suffix must also be changed, otherwise the file will not be valid.
As for whether to write something in the file, it doesn’t matter. The main thing is that there must be a file with this name.
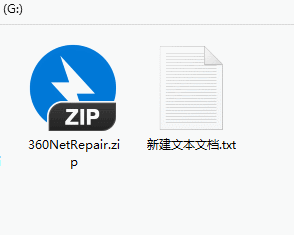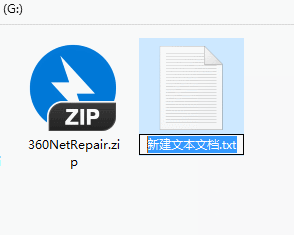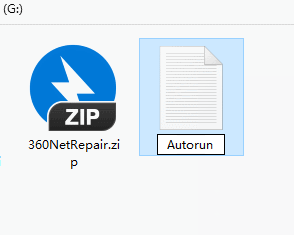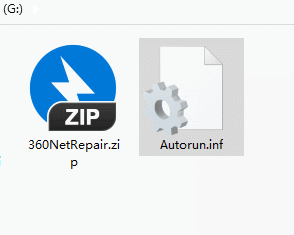
Then right-click the file and click "Properties".
Check both "Read-only" and "Hide" in the properties, and finally click "OK".
This way your USB flash drive can resist most common viruses.
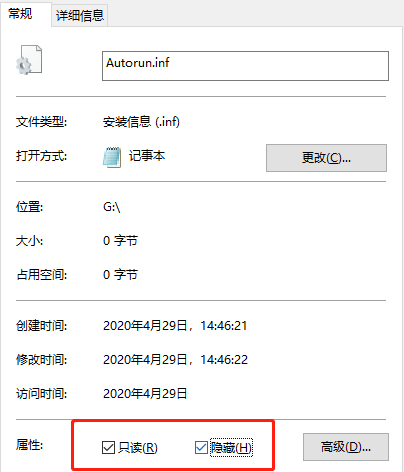
You may think that this setting is too simple?
It’s that simple. In fact, this operation takes advantage of the simple virus operation logic.

Most viruses quietly enter your USB drive and then hide themselves.
When you plug the USB drive into the next computer, it is run through a script called "Autorun.inf" and the destruction begins.
Now we have created this file in advance. Since the file management rules of Windows are that two files with the same name cannot exist in the same folder, so even if the virus writes the data to the U disk , it doesn't work either.

At this time, some students may ask, since there is already Autorun.inf and the house has been built for others, why do they want to break in and live in it? no?
It is possible. Everyone should have done this before.
When we make files, we often make many versions because of modified content. When you press Save As, if you click on the previous version of the file, you will be asked whether you want to overwrite it. , after overwriting, the old version file will disappear, leaving only the new version file.
The key lies in the "read-only" I just set in the properties. As the name suggests, files with "read-only" set can only is viewed and cannot be modified.
So even if the virus sees that the house has been built, it can only look at it and cannot live in it.
If you have any files that you don’t want others to modify, you can try changing its modification permissions with the "read-only" setting.

It’s actually that simple to avoid U disk poisoning. You don’t have to worry about any problems when you plug the U disk into other people’s computers in the future.
What? How to avoid computer virus?
Isn’t tinder fragrant? The computer hard drive is protected by tinder, what other tricks are needed?
The above is the detailed content of How to protect USB disk. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 What is Ouyi for? What is Ouyi
Apr 01, 2025 pm 03:18 PM
What is Ouyi for? What is Ouyi
Apr 01, 2025 pm 03:18 PM
OKX is a global digital asset trading platform. Its main functions include: 1. Buying and selling digital assets (spot trading), 2. Trading between digital assets, 3. Providing market conditions and data, 4. Providing diversified trading products (such as derivatives), 5. Providing asset value-added services, 6. Convenient asset management.
 How many times will the Dogecoin ETF price rise?
Mar 28, 2025 pm 03:42 PM
How many times will the Dogecoin ETF price rise?
Mar 28, 2025 pm 03:42 PM
The possible price increase of Dogecoin ETF after approval is 2 to 5 times, and the current price of $0.18 may rise to $0.6 to $1.2. 1) In the optimistic scenario, the increase can reach 3 times to 10 times, due to the bull market and the boost of Musk; 2) In the neutral scenario, the increase is 1.5 times to 3 times, due to moderate capital inflows; 3) In the pessimistic scenario, the increase is 0.5 times to 1.5 times, due to bear market and low liquidity.
 Will Dogecoin etf be approved?
Mar 28, 2025 pm 03:51 PM
Will Dogecoin etf be approved?
Mar 28, 2025 pm 03:51 PM
As of March 2025, the Dogecoin ETF has not yet had a clear approval schedule. 1. There is no formal application yet and the SEC has not received any relevant application. 2. Market demand and controversy are high, and regulators are conservative. 3. The potential timeline is a 1-2-year review period, which may be observed from 2025 to 2026, but there is high uncertainty.
 What are the Ethereum trading platforms?
Mar 26, 2025 pm 04:48 PM
What are the Ethereum trading platforms?
Mar 26, 2025 pm 04:48 PM
Want to play Ethereum? Choose the right trading platform first! There are centralized exchanges (CEXs) such as Binance, Ouyi, Coinbase, Kraken, and Gate.io. The advantages are fast speed and good liquidity, while the disadvantages are centralized risks. There are also decentralized exchanges (DEXs) such as Uniswap, SushiSwap, Balancer, and Curve. The advantages are security and transparency, while the disadvantages are slow speed and poor experience.
 How to calculate the transaction fee of gate.io trading platform?
Mar 31, 2025 pm 09:15 PM
How to calculate the transaction fee of gate.io trading platform?
Mar 31, 2025 pm 09:15 PM
The handling fees of the Gate.io trading platform vary according to factors such as transaction type, transaction pair, and user VIP level. The default fee rate for spot trading is 0.15% (VIP0 level, Maker and Taker), but the VIP level will be adjusted based on the user's 30-day trading volume and GT position. The higher the level, the lower the fee rate will be. It supports GT platform coin deduction, and you can enjoy a minimum discount of 55% off. The default rate for contract transactions is Maker 0.02%, Taker 0.05% (VIP0 level), which is also affected by VIP level, and different contract types and leverages
 The latest summary of Ethereum formal trading platform 2025
Mar 26, 2025 pm 04:45 PM
The latest summary of Ethereum formal trading platform 2025
Mar 26, 2025 pm 04:45 PM
In 2025, choosing a "formal" Ethereum trading platform means security, compliance and transparency. Licensed operations, financial security, transparent operations, AML/KYC, data protection and fair trading are key. Compliant exchanges such as Coinbase, Kraken, and Gemini are worth paying attention to. Binance and Ouyi have the opportunity to become formal platforms by strengthening compliance. DeFi is an option, but there are risks. Be sure to pay attention to security, compliance, expenses, spread risks, back up private keys, and conduct your own research.
 How to download kraken exchange
Mar 27, 2025 pm 04:21 PM
How to download kraken exchange
Mar 27, 2025 pm 04:21 PM
Want to experience a safe and reliable Kraken exchange? This tutorial details how to download the Kraken App (iOS & Android) and access the web version, and reminds everyone to pay attention to safety. Be sure to download it from the official channel, enable two-factor authentication, and protect account security.





