Analyzing ROP attacks
ROP attack explanation
With the continuous development of information technology, network security issues have gradually attracted people's attention. Various new network attack methods emerge in endlessly, and one of the widely used attack methods is the ROP (Return Oriented Programming) attack. This article will explain in detail the ROP attack.
ROP attack (Return Oriented Programming Attack) is an attack method that uses the existing instruction sequence in the program to construct new functions. It uses small pieces of existing program code (called gadgets) to complete various malicious operations. Usually, attackers inject malicious code into the stack or other memory areas and then use these codes to control the execution flow of the program to achieve the purpose of the attack.
The core idea of the ROP attack is to use the control flow instructions in the program to redirect them to existing functions/code fragments. These code fragments can meet the attacker's needs due to their own characteristics. Based on the reuse of these code snippets, the attacker can achieve complete control of the program without writing a large amount of code himself.
The implementation process of ROP attack includes the following key steps:
- Find the exploitable gadget: The attacker needs to carefully analyze the executable code of the target program to find the exploitable gadget. sequence of instructions. These instruction sequences should have specific functions, such as rewriting the stack pointer, etc.
- Construct attack payload: The attacker constructs a series of gadget sequences and arranges them in a specific order to transfer the program.
- Rewrite the return address: The attacker finds the return address in the stack frame of the target program and modifies it to the starting address of the ROP chain. In this way, at the end of the function call, the program will jump to the gadget sequence carefully constructed by the attacker.
- Control program flow: By accurately selecting and constructing gadget sequences, attackers can control the execution flow of the program and achieve their own goals, such as obtaining system permissions, modifying sensitive data, etc.
ROP attacks have the following advantages:
- No need to exploit system vulnerabilities: Compared with traditional attack methods, ROP attacks do not need to rely on system software vulnerabilities. The attack is carried out by utilizing the instruction sequence that already exists in the program. This means that even if the operating system, applications, etc. have undergone security upgrades, ROP attacks are still feasible.
- Low-profile and concealed: Because ROP attacks do not cause abnormal termination or crash of the program, they are difficult to detect. Attackers can exploit existing code to achieve their goals without alerting the system.
However, ROP attacks also have some limitations and challenges:
- Requires high understanding of the program: ROP attacks require the attacker to have an in-depth understanding of the structure and mechanism of the target program understanding. The attacker needs to analyze the executable code of the program to find exploitable gadgets. This is very difficult for the average attacker.
- Depends on the executability of the program: ROP attacks rely on the existing instruction sequence in the program, so the target program needs to have certain executability. If the program does not have executable code blocks, the ROP attack cannot be carried out.
To sum up, ROP attack is an attack method that uses the existing code of the program to construct new functions. Although the attacker needs to have an in-depth understanding of the target program, since he does not need to exploit system vulnerabilities, his concealment is relatively high. Therefore, preventing ROP attacks requires strengthening the security design and code review of the program, and promptly repairing known vulnerabilities. Only in this way can we effectively prevent this new type of network attack.
The above is the detailed content of Analyzing ROP attacks. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to check traffic on Apple mobile phone
May 09, 2024 pm 06:00 PM
How to check traffic on Apple mobile phone
May 09, 2024 pm 06:00 PM
How to check data usage on Apple 1. The specific steps to check data usage on Apple mobile phone are as follows: Open the settings of the phone. Click the Cellular button. Scroll down on the cellular network page to see the specific data usage of each application. Click Apply to also set allowed networks. 2. Turn on the phone, find the settings option on the phone desktop, and click to enter. In the settings interface, find "Cellular Network" in the taskbar below and click to enter. In the cellular network interface, find the "Usage" option on the page and click to enter. 3. Another way is to check the traffic by yourself through the mobile phone, but the mobile phone can only see the total usage and will not display the remaining traffic: turn on the iPhone, find the "Settings" option and open it. Select "Bee"
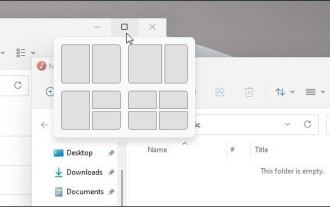 How to disable snapshot layout in Windows 11_ Tips for not using snapshot layout in win11
May 08, 2024 pm 06:46 PM
How to disable snapshot layout in Windows 11_ Tips for not using snapshot layout in win11
May 08, 2024 pm 06:46 PM
Win11 system announced the new [Snapshot Layout], which provides users with various window layout options through the [Maximize] button, so that users can choose from multiple layout templates to display two, three or four on the screen. open applications. This is an improvement over dragging multiple windows to the sides of the screen and then adjusting everything manually. [SnapGroups] will save the collection of apps the user is using and their layout, allowing the user to easily return to that setting when they have to stop and deal with other things. If someone is using a monitor that the user must unplug, when re-docking, the previously used snapshot layout will also be restored. To use snapshot layout, we can use the keyboard shortcut WindowsKey+Z to start
 How to sort the list page alphabetically in vscode How to sort the list page alphabetically in vscode
May 09, 2024 am 09:40 AM
How to sort the list page alphabetically in vscode How to sort the list page alphabetically in vscode
May 09, 2024 am 09:40 AM
1. First, after opening the vscode interface, click the settings icon button in the lower left corner of the page 2. Then, click the Settings option in the drop-down page column 3. Then, find the Explorer option in the jumped window 4. Finally, on the right side of the page Click the OpenEditorsnaming option, select the alphabetical button from the drop-down page and save the settings to complete the alphabetical sorting
 What is the value and use of icp coins?
May 09, 2024 am 10:47 AM
What is the value and use of icp coins?
May 09, 2024 am 10:47 AM
As the native token of the Internet Computer (IC) protocol, ICP Coin provides a unique set of values and uses, including storing value, network governance, data storage and computing, and incentivizing node operations. ICP Coin is considered a promising cryptocurrency, with its credibility and value growing with the adoption of the IC protocol. In addition, ICP coins play an important role in the governance of the IC protocol. Coin holders can participate in voting and proposal submission, affecting the development of the protocol.
 The difference between oracle database and mysql
May 10, 2024 am 01:54 AM
The difference between oracle database and mysql
May 10, 2024 am 01:54 AM
Oracle database and MySQL are both databases based on the relational model, but Oracle is superior in terms of compatibility, scalability, data types and security; while MySQL focuses on speed and flexibility and is more suitable for small to medium-sized data sets. . ① Oracle provides a wide range of data types, ② provides advanced security features, ③ is suitable for enterprise-level applications; ① MySQL supports NoSQL data types, ② has fewer security measures, and ③ is suitable for small to medium-sized applications.
 How to use merge in java
May 09, 2024 am 06:03 AM
How to use merge in java
May 09, 2024 am 06:03 AM
The merge() method in Java Collections merges two sorted ordered collections to generate a new sorted collection, maintaining the original order. Syntax: public static <T> List<T> merge(SortedMap<T, Double> a, SortedMap<T, Double> b). It accepts two sorted collections and returns a new collection containing all elements in sorted order. Note: The values of duplicate keys will be merged according to the merge function, and the original collection will not be modified.
 What are the advanced C++ performance optimization techniques?
May 08, 2024 pm 09:18 PM
What are the advanced C++ performance optimization techniques?
May 08, 2024 pm 09:18 PM
Performance optimization techniques in C++ include: Profiling to identify bottlenecks and improve array layout performance. Memory management uses smart pointers and memory pools to improve allocation and release efficiency. Concurrency leverages multi-threading and atomic operations to increase throughput of large applications. Data locality optimizes storage layout and access patterns and enhances data cache access speed. Code generation and compiler optimization applies compiler optimization techniques, such as inlining and loop unrolling, to generate optimized code for specific platforms and algorithms.
 What are the top ten virtual currency trading platforms? Ranking of the top ten virtual currency trading platforms in the world
Feb 20, 2025 pm 02:15 PM
What are the top ten virtual currency trading platforms? Ranking of the top ten virtual currency trading platforms in the world
Feb 20, 2025 pm 02:15 PM
With the popularity of cryptocurrencies, virtual currency trading platforms have emerged. The top ten virtual currency trading platforms in the world are ranked as follows according to transaction volume and market share: Binance, Coinbase, FTX, KuCoin, Crypto.com, Kraken, Huobi, Gate.io, Bitfinex, Gemini. These platforms offer a wide range of services, ranging from a wide range of cryptocurrency choices to derivatives trading, suitable for traders of varying levels.






