高性能MySql进化论(三):ID(标示符)的选择_MySQL
bitsCN.com
高性能MySql进化论(三):ID(标示符)的选择
在设计数据库表结构的时候,通常情况下每张表结构都有一个字段作为ID,因为 ID会被用来做查询,JOIN,FK等操作,所以ID设计的好坏对性能的影响很大。
在为ID选择合适的类型的时候不仅需要考虑这种类型在数据库中存储所占用的空间,还需要考虑该类型在计算或者是值比较时的特性,例如BIT类型存储的时候是二进制的形式,而在数字计算的上下文时,会被转换成对应的十进制形式。
对ID进行JOIN操作或者是被用来作为其他表的FK时,涉及的字段类型要保持完全的一致,即使类型都是整数,Unsigned/Signed这样的微小细节也要保持一致,否则在性能方面可能会有意想不到的性能问题,这种问题往往又是难以被发现的。如果使用的Storage Engine 是InnoDB,则可以有效的防止关联字段类型不匹配的问题,如果类型不匹配则会抛出 异常“ERROR 1005 (HY000): Can’t createtable”(VARCHAR(10)和VARCHAR(20)会被认为类型是完全相同的)。
创建ID时,要遵守“尽量最小类型原则”(在满足以后需求变化的情况下,要选择占用存储空间最小的类型),例如 有一张存储全国省份的表,对于这张种需求而言,TINYINT比INT更适合作为ID的类型,虽然选用TINYINT只是节省了3个BYTE, 但是在进行JOIN操作或者是作为FK时,性能可能会有很大的提升。
实际的应用开发中,ID的类型往往是多样的,例如INT,VARCHAR是比较常用的两种类型,但是有些情况下也可以使用ENUM作为ID的类型,下面的内容分别对这几种类型进行描述
整数类型
因为整数类型是一种简单的类型,对比于字符串它的处理更简单速度更快,而且它还支持AUTO_INCREMENT特性,所以一般情况下它是作为ID的首选类型
字符串
因为MySQL处理字符串要比整数消耗更多的存储/内存空间,而且速度也相对较慢,所以应该尽量避免使用字符串作为ID的类型。
在无法避免字符串作为ID的类型时,往往会采用“随机值”的策略来生成ID的值,常用的方法包括UUID,MD5, SHA1.在这种情况下需要额外注意,因为随机生成的ID值可能会带来以下三个问题:
(1) 在执行INSERT语句时意味着索引值会被任意写到索引表的不同位置,这种对于磁盘的随机访问行为,将会导致插入操作的变慢,
(2) 在执行SELECT操作时,因为逻辑相关的索引也被会被任意写到索引表的不同位置,也会导致查询的变慢。
(3) 对于数据库提供的CACHE机制而言,这种随机值的策略产生的影响也是比较大的。因为CACHE往往是基于“热区”的原理来实现的,比如说索引表中有100个索引,你执行了多次的查询的结果都是索引表中的20-30这部分的索引,那么 MySQL Serve为了提高查询效率会把20-30这部分索引的值放到CACHE中,如果你又有一些查询的结果是在30-40 之间的,那么Server会对CACHE进行更新。如果是基于随机的索引,意味着“热区”的区间将会很大,这将导致CACHE的命中率受到影响,而且也会导致CACHE的不断刷新。
如果存储UUID 值,则应该移除“-”符号;或者更好的做法是,用UNHEX() 函数转换UUID 值为16 字节的数字,并且存储在一个BINARY(16) 列中。检索时可以通过HEX()函数来格式化为十六进制格式。
枚举
对于ID来说,EMUM 和SET 类型通常是一个糟糕的选择,尽管对某些只包含固定状态或者类型的静态“定义表”来说可能是没有问题的。ENUM 和SET 列适合存储固定信息,例如有序的状态、产品类型、人的性别。没有特殊需求,应该放弃这个选择
bitsCN.com

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
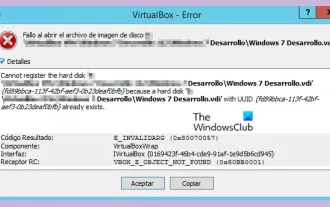 VBOX_E_OBJECT_NOT_FOUND(0x80bb0001)VirtualBox error
Mar 24, 2024 am 09:51 AM
VBOX_E_OBJECT_NOT_FOUND(0x80bb0001)VirtualBox error
Mar 24, 2024 am 09:51 AM
When trying to open a disk image in VirtualBox, you may encounter an error indicating that the hard drive cannot be registered. This usually happens when the VM disk image file you are trying to open has the same UUID as another virtual disk image file. In this case, VirtualBox displays error code VBOX_E_OBJECT_NOT_FOUND(0x80bb0001). If you encounter this error, don’t worry, there are some solutions you can try. First, you can try using VirtualBox's command line tools to change the UUID of the disk image file, which will avoid conflicts. You can run the command `VBoxManageinternal
 How effective is receiving phone calls using airplane mode?
Feb 20, 2024 am 10:07 AM
How effective is receiving phone calls using airplane mode?
Feb 20, 2024 am 10:07 AM
What happens when someone calls in airplane mode? Mobile phones have become one of the indispensable tools in people's lives. It is not only a communication tool, but also a collection of entertainment, learning, work and other functions. With the continuous upgrading and improvement of mobile phone functions, people are becoming more and more dependent on mobile phones. With the advent of airplane mode, people can use their phones more conveniently during flights. However, some people are worried about what impact other people's calls in airplane mode will have on the mobile phone or the user? This article will analyze and discuss from several aspects. first
 How to turn off the comment function on TikTok? What happens after turning off the comment function on TikTok?
Mar 23, 2024 pm 06:20 PM
How to turn off the comment function on TikTok? What happens after turning off the comment function on TikTok?
Mar 23, 2024 pm 06:20 PM
On the Douyin platform, users can not only share their life moments, but also interact with other users. Sometimes the comment function may cause some unpleasant experiences, such as online violence, malicious comments, etc. So, how to turn off the comment function of TikTok? 1. How to turn off the comment function of Douyin? 1. Log in to Douyin APP and enter your personal homepage. 2. Click "I" in the lower right corner to enter the settings menu. 3. In the settings menu, find "Privacy Settings". 4. Click "Privacy Settings" to enter the privacy settings interface. 5. In the privacy settings interface, find "Comment Settings". 6. Click "Comment Settings" to enter the comment setting interface. 7. In the comment settings interface, find the "Close Comments" option. 8. Click the "Close Comments" option to confirm closing comments.
 File Inclusion Vulnerabilities in Java and Their Impact
Aug 08, 2023 am 10:30 AM
File Inclusion Vulnerabilities in Java and Their Impact
Aug 08, 2023 am 10:30 AM
Java is a commonly used programming language used to develop various applications. However, just like other programming languages, Java has security vulnerabilities and risks. One of the common vulnerabilities is the file inclusion vulnerability (FileInclusionVulnerability). This article will explore the principle, impact and how to prevent this vulnerability. File inclusion vulnerabilities refer to the dynamic introduction or inclusion of other files in the program, but the introduced files are not fully verified and protected, thus
 The impact of data scarcity on model training
Oct 08, 2023 pm 06:17 PM
The impact of data scarcity on model training
Oct 08, 2023 pm 06:17 PM
The impact of data scarcity on model training requires specific code examples. In the fields of machine learning and artificial intelligence, data is one of the core elements for training models. However, a problem we often face in reality is data scarcity. Data scarcity refers to the insufficient amount of training data or the lack of annotated data. In this case, it will have a certain impact on model training. The problem of data scarcity is mainly reflected in the following aspects: Overfitting: When the amount of training data is insufficient, the model is prone to overfitting. Overfitting refers to the model over-adapting to the training data.
 What problems will bad sectors on the hard drive cause?
Feb 18, 2024 am 10:07 AM
What problems will bad sectors on the hard drive cause?
Feb 18, 2024 am 10:07 AM
Bad sectors on a hard disk refer to a physical failure of the hard disk, that is, the storage unit on the hard disk cannot read or write data normally. The impact of bad sectors on the hard drive is very significant, and it may lead to data loss, system crash, and reduced hard drive performance. This article will introduce in detail the impact of hard drive bad sectors and related solutions. First, bad sectors on the hard drive may lead to data loss. When a sector in a hard disk has bad sectors, the data on that sector cannot be read, causing the file to become corrupted or inaccessible. This situation is especially serious if important files are stored in the sector where the bad sectors are located.
 What specific impact do mine cards have on the game?
Jan 03, 2024 am 09:05 AM
What specific impact do mine cards have on the game?
Jan 03, 2024 am 09:05 AM
Some users may consider buying mining cards for the sake of cheapness. After all, these cards are top-notch graphics cards. However, some gamers are worried about the impact of mining cards on playing games. Let’s take a look at the detailed introduction below. What are the effects of using a mining card to play games: 1. The stability of playing games with a mining card cannot be guaranteed, because the life of the mining card is very short and it is likely to become useless after just playing. 2. The mining card is basically a castrated version of the original version. Due to long-term wear and tear, the performance in all aspects may be weak. 3. In this way, users may not be able to display all the effects of the game when playing the game. 4. Moreover, the electronic components of the graphics card will age in advance, not to mention that playing games also consumes the graphics card, so it is drained to a greater extent, so the impact on the game is great. 5. In general, use mining cards to play games
 What impact does chassis leakage have on the computer?
Feb 22, 2024 pm 06:48 PM
What impact does chassis leakage have on the computer?
Feb 22, 2024 pm 06:48 PM
What impact does chassis leakage have on computers? With the continuous advancement of technology, computers have gradually become an indispensable tool in people's lives. Whether it is work, study or entertainment, they are inseparable from the use of computers. However, while we enjoy the convenience brought by computers, we also need to pay attention to its security. Case leakage is a potential problem that, if not dealt with in time, may have a serious impact on the computer and the user. First of all, chassis leakage will cause damage to computer hardware. The computer's motherboard, power supply, internal circuits and other components are all inside the chassis. Once the chassis




