In-depth analysis of the functions and benefits of mybatis first-level cache

Analysis of the functions and advantages of MyBatis first-level cache
Introduction:
During the development process, database access operations are inevitable. In order to improve performance and reduce the number of database accesses, MyBatis provides a first-level cache mechanism. This article will explore the functions and advantages of MyBatis first-level cache, and illustrate it with specific code examples.
1. The role of the first-level cache
The first-level cache of MyBatis refers to the caching mechanism in the same SqlSession. The first-level cache is enabled by default and can improve query performance. The specific functions are as follows:
- Reduce the number of database accesses: Using the first-level cache can avoid repeated queries to the database and improve system performance.
- Improving response speed: Since the first-level cache is located in the memory, data is read faster, which can reduce network transmission time, thereby shortening response time.
- Data consistency: In the same SqlSession, when multiple query operations operate on the same piece of data, MyBatis will automatically obtain data from the cache to ensure data consistency.
2. Advantages of first-level cache
MyBatis’s first-level cache has the following advantages:
- Simple and easy to use: first-level cache Usage is transparent to developers, no manual operations are required, and data access operations can be performed directly.
- Enabled by default: The first-level cache is enabled by default, that is, the execution results of SQL statements will be cached. In this way, you can directly obtain the benefits of caching without additional configuration.
- Restricted scope: The scope of the first-level cache is limited to the same SqlSession. When the SqlSession is submitted or closed, the cache will be invalidated to avoid data inconsistency.
3. Code examples
The following uses specific code examples to demonstrate the use of first-level cache.
- Create a UserMapper interface:
public interface UserMapper {
User getUserById(int id);
void updateUser(User user);
}- Enable first-level cache in the MyBatis configuration file:
<configuration>
<!-- 其他配置 -->
<settings>
<setting name="cacheEnabled" value="true" />
</settings>
<!-- 其他配置 -->
</configuration>- Writing code example:
public static void main(String[] args) {
try (SqlSessionFactory sessionFactory = new SqlSessionFactoryBuilder().build(Resources.getResourceAsStream("mybatis-config.xml"))) {
try (SqlSession sqlSession = sessionFactory.openSession()) {
// 创建 UserMapper 的代理对象
UserMapper userMapper = sqlSession.getMapper(UserMapper.class);
// 第一次查询,会从数据库中获取数据,并将数据缓存到一级缓存中
User user1 = userMapper.getUserById(1);
System.out.println(user1);
// 第二次查询,会从一级缓存中获取数据,不会访问数据库
User user2 = userMapper.getUserById(1);
System.out.println(user2);
// 更新用户信息
user1.setName("New Name");
userMapper.updateUser(user1);
// 清除一级缓存
sqlSession.clearCache();
// 第三次查询,会从数据库中获取数据,并将新的数据缓存到一级缓存中
User user3 = userMapper.getUserById(1);
System.out.println(user3);
}
}
}In the above example, the first query will get the data from the database and cache it into the first level cache. During the second query, the data is obtained directly from the first-level cache, avoiding the need to access the database again. After the user information is updated, the first-level cache is cleared, and the third query will re-obtain the latest data from the database and cache it in the first-level cache.
In summary, MyBatis's first-level cache has obvious advantages in improving database access performance and reducing network transmission delays. Developers only need simple configuration to enjoy the convenience brought by the first-level cache.
The above is the detailed content of In-depth analysis of the functions and benefits of mybatis first-level cache. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
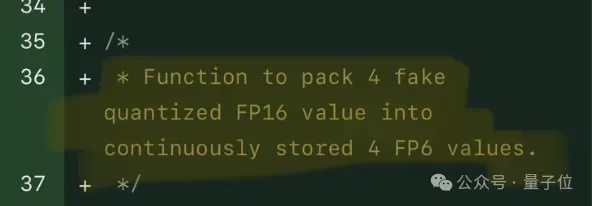 Single card running Llama 70B is faster than dual card, Microsoft forced FP6 into A100 | Open source
Apr 29, 2024 pm 04:55 PM
Single card running Llama 70B is faster than dual card, Microsoft forced FP6 into A100 | Open source
Apr 29, 2024 pm 04:55 PM
FP8 and lower floating point quantification precision are no longer the "patent" of H100! Lao Huang wanted everyone to use INT8/INT4, and the Microsoft DeepSpeed team started running FP6 on A100 without official support from NVIDIA. Test results show that the new method TC-FPx's FP6 quantization on A100 is close to or occasionally faster than INT4, and has higher accuracy than the latter. On top of this, there is also end-to-end large model support, which has been open sourced and integrated into deep learning inference frameworks such as DeepSpeed. This result also has an immediate effect on accelerating large models - under this framework, using a single card to run Llama, the throughput is 2.65 times higher than that of dual cards. one
 How to export the queried data in navicat
Apr 24, 2024 am 04:15 AM
How to export the queried data in navicat
Apr 24, 2024 am 04:15 AM
Export query results in Navicat: Execute query. Right-click the query results and select Export Data. Select the export format as needed: CSV: Field separator is comma. Excel: Includes table headers, using Excel format. SQL script: Contains SQL statements used to recreate query results. Select export options (such as encoding, line breaks). Select the export location and file name. Click "Export" to start the export.
 How to remove the write protection of a USB flash drive? Several simple and effective methods can help you do it
May 02, 2024 am 09:04 AM
How to remove the write protection of a USB flash drive? Several simple and effective methods can help you do it
May 02, 2024 am 09:04 AM
U disk is one of the commonly used storage devices in our daily work and life, but sometimes we encounter situations where the U disk is write-protected and cannot write data. This article will introduce several simple and effective methods to help you quickly remove the write protection of the USB flash drive and restore the normal use of the USB flash drive. Tool materials: System version: Windows1020H2, macOS BigSur11.2.3 Brand model: SanDisk UltraFlair USB3.0 flash drive, Kingston DataTraveler100G3USB3.0 flash drive Software version: DiskGenius5.4.2.1239, ChipGenius4.19.1225 1. Check the physical write protection switch of the USB flash drive on some USB flash drives Designed with
 What does schema mean in mysql
May 01, 2024 pm 08:33 PM
What does schema mean in mysql
May 01, 2024 pm 08:33 PM
Schema in MySQL is a logical structure used to organize and manage database objects (such as tables, views) to ensure data consistency, data access control and simplify database design. The functions of Schema include: 1. Data organization; 2. Data consistency; 3. Data access control; 4. Database design.
 What is the API interface for?
Apr 23, 2024 pm 01:51 PM
What is the API interface for?
Apr 23, 2024 pm 01:51 PM
An API interface is a specification for interaction between software components and is used to implement communication and data exchange between different applications or systems. The API interface acts as a "translator", converting the developer's instructions into computer language so that the applications can work together. Its advantages include convenient data sharing, simplified development, improved performance, enhanced security, improved productivity and interoperability.
 What does mysql database do?
Apr 22, 2024 pm 06:12 PM
What does mysql database do?
Apr 22, 2024 pm 06:12 PM
MySQL is a relational database management system that provides the following main functions: Data storage and management: Create and organize data, supporting various data types, primary keys, foreign keys, and indexes. Data query and retrieval: Use SQL language to query, filter and retrieve data, and optimize execution plans to improve efficiency. Data updates and modifications: Add, modify or delete data through INSERT, UPDATE, DELETE commands, supporting transactions to ensure consistency and rollback mechanisms to undo changes. Database management: Create and modify databases and tables, back up and restore data, and provide user management and permission control.
 Data Security in Artificial Intelligence: How to Unleash the Power of Artificial Intelligence
Apr 24, 2024 pm 06:20 PM
Data Security in Artificial Intelligence: How to Unleash the Power of Artificial Intelligence
Apr 24, 2024 pm 06:20 PM
In the digital age, data is often viewed as the battery that powers the innovation machine and drives business decisions. With the rise of modern solutions like artificial intelligence (AI) and machine learning (ML), organizations have access to vast amounts of data, enough to gain valuable insights and make informed decisions. However, this comes at the cost of subsequent data loss and confidentiality challenges. As organizations continue to grasp the potential of artificial intelligence, they must strike a balance between achieving business advancements while avoiding potential risks. This article focuses on the importance of data security in artificial intelligence and what security measures organizations can take to avoid risks while taking advantage of the viable solutions provided by artificial intelligence. In artificial intelligence, data security is crucial. Organizations need to ensure data used is legal
 How to upload running data to keep
May 04, 2024 pm 10:51 PM
How to upload running data to keep
May 04, 2024 pm 10:51 PM
Steps to upload running data to Keep: 1. Connect the device and authorize data access; 2. Turn on automatic synchronization; 3. Manually upload data (if the device does not support automatic synchronization).






