 Computer Tutorials
Computer Tutorials
 Computer Knowledge
Computer Knowledge
 Completely delete scanned harmful programs with one command
Completely delete scanned harmful programs with one command
Completely delete scanned harmful programs with one command

One command to completely delete the scanned harmful programs
Author: Tian Yi (formyz
)
An NFS
server is shared by multiple Web
projects
. These directories include PHP
programs, pictures, HTML
pages, documents and attachments uploaded by users, etc. Because some Web
frameworks are old and do not perform strict security checks on uploaded files, although this NFS
server is located in a protected internal network, a large number of malicious files are still uploaded by people with ulterior motives. The programmer was strongly requested to update the program (Discuz
), and the reply was that the update was too difficult to handle programmatically. From the system management level, the temporary measure is just to install the shadu
software, scan the shared directory, and then delete these harmful files (treating the symptoms but not the root cause).
Shared storage NFS
is deployed on Centos 7.9
, with a storage space of 44T
and a usage space of 4.5T
(as shown in the figure below). Due to relatively lax management, there is a large amount of spam information. Clean and archive.
Based on past experience and usage habits, we decided to deploy the open source, well-known security software Clavam
on Centos 7.9
, the host system where the NFS
service is located. Its official promotion is "
ClamAV
®
is an open-source antivirus engine for detecting trojans, viruses, malware & other malicious threats
”–ClamAV®
is an open-source anti-Virtual
engine for detecting special **loy***iMuma
, viruses, malware and other malicious threats. I don’t know when the logo at the bottom of the official website was replaced by the network equipment manufacturer CISCO
. Even so, Clamav
It is still open source and free and can be used without restrictions. On Centos 7.9
, there are at least 3
ways to deploy and install Clamav
: RPM
binary package, binary source code and Online package management tool "yum"
, as shown in the figure below.
The easiest and most convenient way to deploy and install Clamav under Centos 7.9
is "yum install
". Try executing "yum install clamav
" on the system command line and execute The process and output are as follows.
Unfortunately, Clamav
is not included in the software repository and cannot be installed correctly on the system. Try adding an "epel-release" additional software repository again, and execute the command "yum install epel-release
". Then continue to execute "yum list clamav
",
As can be seen from the output, the attached warehouse list already contains the software package "clamav
", as shown in the figure below.
Execute the command "yum install clamav
" for formal installation. In addition to the main software Clamav, there are several other dependent packages installed together, as shown in the figure below.
Compared with installing from source packages, there is no need to install the required dependencies one by one based on the error output during the installation process, which greatly improves efficiency.
The bingdu
library of Clamav that is installed and deployed for the first time is relatively old and lagging. The bingdu
signature library needs to be updated under the system command line to reduce the omission of scanning identification. The command to execute the bingdu
library update is "freshclam
" without any parameters or options. The execution process and output are shown in the figure below.
Bingdu
library is already the latest. Before officially executing the scan, in order to prevent the SSH remote terminal from being disconnected and causing the scan to be interrupted, it is strongly recommended to perform the scan on "screen
". If you execute the command "screen
" and it prompts that the command does not exist, use "yum install screen
" to install it. After correctly executing the command "screen
", the system immediately returns to the Shell
prompt. At this time, formally enter the following command to fully scan the suspected problematic shared directory and record the output to the log file "/var/ log/clamscan.log”
.
|
|
|
[root@nas wenku]# grep FOUND /var/log/clamscan.log /data/cu/attachment/forum/201305/29/22155372jcjxtt0vfx2uk2.zip: Win.Trojan.IRCBot-785 FOUND /data/cu/attachment/forum/201501/05/155857clzd9d10bwdpl3s0.zip: Unix.Trojan.Agent-37008 FOUND /data/cu/attachment/forum/201501/10/2110526a6afrfrzvas2h25.zip: Win.Tool.Chopper-9839749-0 FOUND /data/cu/attachment/forum/201501/10/210932qsy27wsnwazswagr.zip: Win.Tool.Chopper-9839749-0 FOUND /data/cu/attachment/forum/201405/18/082512hhjnzummmnuu4i8i.zip: Unix.Dropper.Mirai-7338045-0 FOUND /data/cu/attachment/forum/201205/11/084024426448y1bk6jmmb9.zip: Win.Trojan.SdBot-13589 FOUND /data/cu/attachment/forum/201206/05/092231faffjiak6z3gkzqv.zip: Win.Malware.Aa93a15d-6745814-0 FOUND /data/kong/blog/attach/attachment/201603/9/30229789_1457535724sulu.jpg: Win.Trojan.Generic-6584387-0 FOUND ………………. /data/wenku/App_Data/Documents/2012-03-10/7da3d2c7-6d16-44c2-aab1-e8a317716c15.txt: Dos.Trojan.Munga-4 FOUND /data/wenku/App_Data/Documents/2014-02-17/4ed74e66-54d1-46b5-8a41-4915ced095a5.ppt: Xls.Trojan.Agent-36856 FOUND /data/wenku/App_Data/Documents/2014-02-23/c5c1dfa6-9f04-4e53-b418-4d711ce5408d.ppt: Win.Exploit.Fnstenv_mov-1 FOUND /data/wenku/App_Data/Documents/2014-07-15/ae2dfca5-ddef-4c41-8812-bcc5543415e1.txt: Legacy.Trojan.Agent-34669 FOUND |
There are a total of 500
multiple records with the keyword "FOUND
", and the distribution path is irregular. These scattered malicious files cannot be processed by deleting the directory. If you manually delete one by one according to the absolute path, it is inefficient and error-prone; if there are thousands of malicious files distributed in this way, it is basically impossible to delete them one by one manually.
The command "clamscan
" itself has the option "--remove
" to directly delete the scanned malicious files, but this has not been confirmed by relevant personnel and may cause controversy. Therefore, these problematic malicious files need to be presented to relevant personnel for confirmation. Only after there are no objections can they be moved or deleted.
Start from the log file scanned by Clamav
, and use the tool to extract the full path of the malicious file. Use the following instructions.
|
[root@nas wenku]#grep FOUND /var/log/clamscan.log |awk -F[:] ‘{print $1}’ /data/wenku/App_Data/Documents/2016-04-11/8fe8d01e-e752-4e52-80df-f202374b2b6d.doc /data/wenku/App_Data/Documents/2016-04-11/03a14021-279f-45cd-83c5-b63076032c9e.doc /data/wenku/App_Data/Documents/2016-04-11/c45ddc01-ec3d-4a54-b674-8c2082d76ce3.doc /data/cu/attachment/forum/201305/29/22155372jcjxtt0vfx2uk2.zip /data/cu/attachment/forum/201501/05/155857clzd9d10bwdpl3s0.zip /data/cu/attachment/forum/201501/10/2110526a6afrfrzvas2h25.zip /data/cu/attachment/forum/201501/10/210932qsy27wsnwazswagr.zip /data/cu/attachment/forum/201405/18/082512hhjnzummmnuu4i8i.zip /data/cu/attachment/forum/201205/11/084024426448y1bk6jmmb9.zip /data/cu/attachment/forum/201206/05/092231faffjiak6z3gkzqv.zip ……………… |
Compared with the original log, the colon ":
" and all subsequent fields are removed. After this command, add a pipeline and pass parameters with "xargs
" to clean up all the scanned malicious files, no matter what path they are distributed to. The complete command is as follows.
|
grep FOUND /var/log/clamscan.log |awk -F[:] ‘{print $1}’| xargs rm -rf |
After execution, randomly find the full paths of several scanned malicious files. The files should not exist (
As shown in the figure below)
, which means the script is correct and is the result we expected.
The above is the detailed content of Completely delete scanned harmful programs with one command. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to make Google Maps the default map in iPhone
Apr 17, 2024 pm 07:34 PM
How to make Google Maps the default map in iPhone
Apr 17, 2024 pm 07:34 PM
The default map on the iPhone is Maps, Apple's proprietary geolocation provider. Although the map is getting better, it doesn't work well outside the United States. It has nothing to offer compared to Google Maps. In this article, we discuss the feasible steps to use Google Maps to become the default map on your iPhone. How to Make Google Maps the Default Map in iPhone Setting Google Maps as the default map app on your phone is easier than you think. Follow the steps below – Prerequisite steps – You must have Gmail installed on your phone. Step 1 – Open the AppStore. Step 2 – Search for “Gmail”. Step 3 – Click next to Gmail app
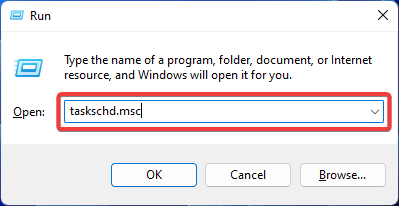 Fix: Operator denied request error in Windows Task Scheduler
Aug 01, 2023 pm 08:43 PM
Fix: Operator denied request error in Windows Task Scheduler
Aug 01, 2023 pm 08:43 PM
To automate tasks and manage multiple systems, mission planning software is a valuable tool in your arsenal, especially as a system administrator. Windows Task Scheduler does the job perfectly, but lately many people have reported operator rejected request errors. This problem exists in all iterations of the operating system, and even though it has been widely reported and covered, there is no effective solution. Keep reading to find out what might actually work for other people! What is the request in Task Scheduler 0x800710e0 that was denied by the operator or administrator? Task Scheduler allows automating various tasks and applications without user input. You can use it to schedule and organize specific applications, configure automatic notifications, help deliver messages, and more. it
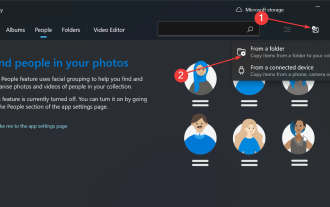 How to sort photos by face on Windows 10 and 11
Aug 08, 2023 pm 10:41 PM
How to sort photos by face on Windows 10 and 11
Aug 08, 2023 pm 10:41 PM
The operation of Windows is getting better and better with every version, with attractive features to improve the user experience. One feature users will want to explore on Windows 10 and 11 is the ability to sort photos by faces. This feature allows you to group photos of friends and family using facial recognition. Sounds fun, right? Read on to learn how to take advantage of this feature. Can I group photos by faces on Windows? Yes, you can use the Photos app to group pictures by faces on Windows 10 and 11. However, this feature is not available on the Photos app version. Additionally, you can link these photos to contacts using the People tab. Therefore, using this function you can
 Upload failed, file cannot be empty, inconsistent error
Feb 19, 2024 pm 01:21 PM
Upload failed, file cannot be empty, inconsistent error
Feb 19, 2024 pm 01:21 PM
Discorde is a popular file sharing platform, but users may encounter errors such as upload failure and file cannot be empty when uploading files. Although there is no clear explanation yet, these errors may appear randomly, preventing certain files from being uploaded, or even preventing the re-uploading of previously sent files. Fixed Upload Failed, File Cannot Be Empty Inconsistency Error It can be frustrating to get a File Cannot Be Empty error when an upload fails. Here are some suggested solutions that we hope will help. Available for iOS and Android users Verifying files Compressing files before sharing them Update/Reinstall Inconsistency 1] Available for iOS and Android users In iPhone and Android users, for file upload fails with error
 Clock app missing in iPhone: How to fix it
May 03, 2024 pm 09:19 PM
Clock app missing in iPhone: How to fix it
May 03, 2024 pm 09:19 PM
Is the clock app missing from your phone? The date and time will still appear on your iPhone's status bar. However, without the Clock app, you won’t be able to use world clock, stopwatch, alarm clock, and many other features. Therefore, fixing missing clock app should be at the top of your to-do list. These solutions can help you resolve this issue. Fix 1 – Place the Clock App If you mistakenly removed the Clock app from your home screen, you can put the Clock app back in its place. Step 1 – Unlock your iPhone and start swiping to the left until you reach the App Library page. Step 2 – Next, search for “clock” in the search box. Step 3 – When you see “Clock” below in the search results, press and hold it and
 How to write a simple countdown program in C++?
Nov 03, 2023 pm 01:39 PM
How to write a simple countdown program in C++?
Nov 03, 2023 pm 01:39 PM
C++ is a widely used programming language that is very convenient and practical in writing countdown programs. Countdown program is a common application that can provide us with very precise time calculation and countdown functions. This article will introduce how to use C++ to write a simple countdown program. The key to implementing a countdown program is to use a timer to calculate the passage of time. In C++, we can use the functions in the time.h header file to implement the timer function. The following is the code for a simple countdown program
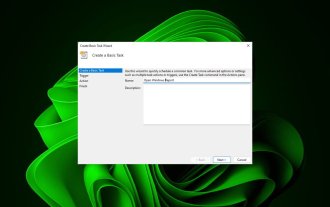 How to open a website using Task Scheduler
Oct 02, 2023 pm 11:13 PM
How to open a website using Task Scheduler
Oct 02, 2023 pm 11:13 PM
Do you frequently visit the same website at about the same time every day? This can lead to spending a lot of time with multiple browser tabs open and cluttering the browser while performing daily tasks. Well, how about opening it without having to launch the browser manually? It's very simple and doesn't require you to download any third-party apps, as shown below. How do I set up Task Scheduler to open a website? Press the key, type Task Scheduler in the search box, and then click Open. Windows On the right sidebar, click on the Create Basic Task option. In the Name field, enter the name of the website you want to open and click Next. Next, under Triggers, click Time Frequency and click Next. Select how long you want the event to repeat and click Next. Select enable
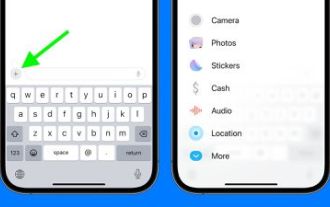 iOS 17: How to organize iMessage apps in Messages
Sep 18, 2023 pm 05:25 PM
iOS 17: How to organize iMessage apps in Messages
Sep 18, 2023 pm 05:25 PM
In iOS 17, Apple not only added several new messaging features, but also tweaked the design of the Messages app to give it a cleaner look. All iMessage apps and tools, such as the camera and photo options, can now be accessed by tapping the "+" button above the keyboard and to the left of the text input field. Clicking the "+" button brings up a menu column with a default order of options. Starting from the top, there's camera, photos, stickers, cash (if available), audio, and location. At the very bottom is a "More" button, which when tapped will reveal any other installed messaging apps (you can also swipe up to reveal this hidden list). How to reorganize your iMessage app You can do this below





