How to mount using mount command in Linux
Usage of the mount command mount in Linux
In the Linux system, the mount command is a very important command, used to mount the file system to the specified mount point. Mounting is the process of associating a file system with a directory in the operating system. Through mounting, we can access and operate files and directories in the file system.
The following will introduce the use of the mount command in detail and give specific code examples.
- Basic syntax
The basic syntax of the mount command is as follows:
mount [option] [-t file system type] device file name mount point
Options:
-a: Mount the existing file system in /etc/fstab.
-t: Specify the file system type.
-o: Specify mounting options. Use commas to separate multiple options.
- Specify the file system type
Use the -t option to specify the file system type to be mounted. Common file system types include ext2, ext3, ext4, xfs, ntfs, vfat, etc. The following is an example code for using the mount command to mount an ext4 file system:
mount -t ext4 /dev/sdb1 /mnt/mydisk
In the above command, mount the ext4 file system on the /dev/sdb1 device to the /mnt/mydisk directory.
- Specify mounting options
Use the -o option to specify mounting options. Multiple options are separated by commas. Common mount options include:
- ro: Read-only mount, mount the file system in read-only mode.
- rw: Read-write mount, mount the file system in a readable and writable manner.
- remount: Remount the mounted file system and can be used to modify the mount options.
- noexec: Disable execution of executable files on the file system.
- nodev: Disable the creation of device files on the file system.
- nosuid: Disable execution of setuid, setgid and sticky bits on the file system.
- sync: Write data synchronously and ensure that the writing is completed before returning.
- async: Write data asynchronously, without waiting when writing data.
The following is a sample code to use the mount command to mount an ext4 file system and specify the mount options:
mount -t ext4 -o rw,noexec /dev/sdb1 /mnt/mydisk
In the above command, the ext4 file on the /dev/sdb1 device The system is mounted to the /mnt/mydisk directory in a readable and writable manner, and execution of executable files on this file system is prohibited.
- Mount all file systems
Use the -a option of the mount command to mount all file systems in the /etc/fstab file. The following is a sample code for using the mount command to mount all file systems:
mount -a
In the above command, all file systems will be mounted based on the configuration information in the /etc/fstab file.
Summary:
The mount command is a very important command in the Linux system. It is used to mount the file system to the specified mount point. We can customize the mount behavior by specifying the file system type and mount options. Mastering the use of the mount command is very helpful for managing and operating file systems in Linux systems.
I hope this article can help readers better understand and use the mount command, and manage and operate the file system more efficiently in actual work.
The above is the detailed content of How to mount using mount command in Linux. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 How to run SUDO commands in Windows 11/10
Mar 09, 2024 am 09:50 AM
How to run SUDO commands in Windows 11/10
Mar 09, 2024 am 09:50 AM
The sudo command allows users to run commands in elevated privilege mode without switching to superuser mode. This article will introduce how to simulate functions similar to sudo commands in Windows systems. What is the Shudao Command? Sudo (short for "superuser do") is a command-line tool that allows users of Unix-based operating systems such as Linux and MacOS to execute commands with elevated privileges typically held by administrators. Running SUDO commands in Windows 11/10 However, with the launch of the latest Windows 11 Insider preview version, Windows users can now experience this feature. This new feature enables users to
 How to check the MAC address of the network card in Win11? How to use the command to obtain the MAC address of the network card in Win11
Feb 29, 2024 pm 04:34 PM
How to check the MAC address of the network card in Win11? How to use the command to obtain the MAC address of the network card in Win11
Feb 29, 2024 pm 04:34 PM
This article will introduce readers to how to use the command prompt (CommandPrompt) to find the physical address (MAC address) of the network adapter in Win11 system. A MAC address is a unique identifier for a network interface card (NIC), which plays an important role in network communications. Through the command prompt, users can easily obtain the MAC address information of all network adapters on the current computer, which is very helpful for network troubleshooting, configuring network settings and other tasks. Method 1: Use "Command Prompt" 1. Press the [Win+X] key combination, or [right-click] click the [Windows logo] on the taskbar, and in the menu item that opens, select [Run]; 2. Run the window , enter the [cmd] command, and then
 Super practical! Sar commands that will make you a Linux master
Mar 01, 2024 am 08:01 AM
Super practical! Sar commands that will make you a Linux master
Mar 01, 2024 am 08:01 AM
1. Overview The sar command displays system usage reports through data collected from system activities. These reports are made up of different sections, each containing the type of data and when the data was collected. The default mode of the sar command displays the CPU usage at different time increments for various resources accessing the CPU (such as users, systems, I/O schedulers, etc.). Additionally, it displays the percentage of idle CPU for a given time period. The average value for each data point is listed at the bottom of the report. sar reports collected data every 10 minutes by default, but you can use various options to filter and adjust these reports. Similar to the uptime command, the sar command can also help you monitor the CPU load. Through sar, you can understand the occurrence of excessive load
 Where is hyperv enhanced session mode? Tips for enabling or disabling Hyper-V enhanced session mode using commands in Win11
Feb 29, 2024 pm 05:52 PM
Where is hyperv enhanced session mode? Tips for enabling or disabling Hyper-V enhanced session mode using commands in Win11
Feb 29, 2024 pm 05:52 PM
In Win11 system, you can enable or disable Hyper-V enhanced session mode through commands. This article will introduce how to use commands to operate and help users better manage and control Hyper-V functions in the system. Hyper-V is a virtualization technology provided by Microsoft. It is built into Windows Server and Windows 10 and 11 (except Home Edition), allowing users to run virtual operating systems in Windows systems. Although virtual machines are isolated from the host operating system, they can still use the host's resources, such as sound cards and storage devices, through settings. One of the key settings is to enable Enhanced Session Mode. Enhanced session mode is Hyper
 What is the correct way to restart a service in Linux?
Mar 15, 2024 am 09:09 AM
What is the correct way to restart a service in Linux?
Mar 15, 2024 am 09:09 AM
What is the correct way to restart a service in Linux? When using a Linux system, we often encounter situations where we need to restart a certain service, but sometimes we may encounter some problems when restarting the service, such as the service not actually stopping or starting. Therefore, it is very important to master the correct way to restart services. In Linux, you can usually use the systemctl command to manage system services. The systemctl command is part of the systemd system manager
 Usage of WPSdatedif function
Feb 20, 2024 pm 10:27 PM
Usage of WPSdatedif function
Feb 20, 2024 pm 10:27 PM
WPS is a commonly used office software suite, and the WPS table function is widely used for data processing and calculations. In the WPS table, there is a very useful function, the DATEDIF function, which is used to calculate the time difference between two dates. The DATEDIF function is the abbreviation of the English word DateDifference. Its syntax is as follows: DATEDIF(start_date,end_date,unit) where start_date represents the starting date.
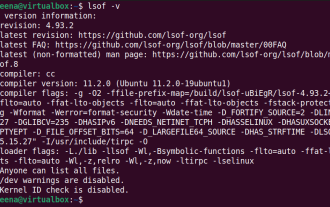 How to use LSOF to monitor ports in real time
Mar 20, 2024 pm 02:07 PM
How to use LSOF to monitor ports in real time
Mar 20, 2024 pm 02:07 PM
LSOF (ListOpenFiles) is a command line tool mainly used to monitor system resources similar to Linux/Unix operating systems. Through the LSOF command, users can get detailed information about the active files in the system and the processes that are accessing these files. LSOF can help users identify the processes currently occupying file resources, thereby better managing system resources and troubleshooting possible problems. LSOF is powerful and flexible, and can help system administrators quickly locate file-related problems, such as file leaks, unclosed file descriptors, etc. Via LSOF Command The LSOF command line tool allows system administrators and developers to: Determine which processes are currently using a specific file or port, in the event of a port conflict
 Detailed explanation of Linux ldconfig command
Mar 14, 2024 pm 12:18 PM
Detailed explanation of Linux ldconfig command
Mar 14, 2024 pm 12:18 PM
Detailed explanation of the Linuxldconfig command 1. Overview In the Linux system, ldconfig is a command used to configure shared libraries. It is used to update the links and cache of shared libraries and enable the system to load dynamically linked shared libraries correctly. The main function of ldconfig is to find dynamic link libraries and create symbolic links for program use. This article will delve into the usage and working principle of the ldconfig command, and use specific code examples to help readers better understand the functions of ldconfig




