1. The purpose of ssh mutual trust
1. When building a cluster, SSH mutual trust is required, which is conducive to convenient operation on another node.
2. When using scp remote copy operation, you need to enter the user name and password of the target server. At this time, you can do linuxmutual trust between serversssh Configure so that you can log in without a password when operating between multiple linux servers.
2. Principle of ssh mutual trust configuration
In short, the server stores the target host's certificate so that authentication is completed automatically without entering a password.
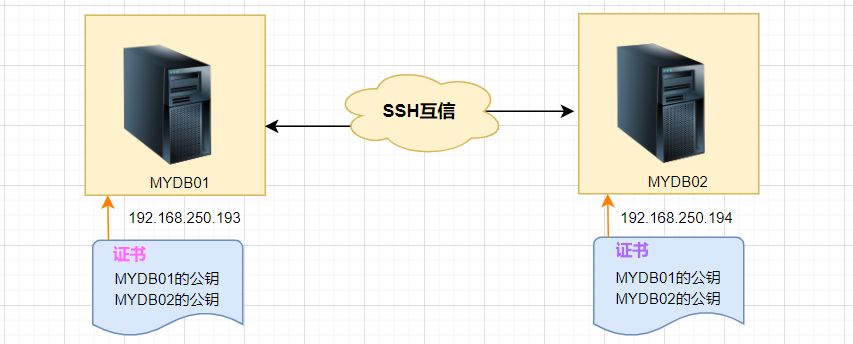
3. SSH mutual trust configuration steps
1. Each node generates its own public key and private key pair.
2. Send your public key file to the other party.
3. Verify whether the mutual trust configuration is successful.
4. Configure ssh mutual trust
Here are two LINUX hosts, MYDB01 and MYDB02, as examples:
4.1 Generate public key and private key pair
Generate on two hosts separately, press Enter directly when prompted to enter information:
#MYDB01Host:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 | [root@MYDB01 ~]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:lQex2+SbdmGGNBvU8vjaTKVCbfAmk8Eva+C6BPJ49G0 root@MYDB01
The key's randomart image is:
+---[RSA 2048]----+
|oo.. |
| == .|
|+ *@ |
| ..BB=B .|
|. o S..o=O+o |
| = o .. +=+. |
|. o o.E.+*.|
| . ... ...o|
|.. |
+----[SHA256]-----+
[root@MYDB01 ~]#
|
Copy after login
#MYDB02Host:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 | [root@MYDB02 ~]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Created directory '/root/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:8DGfMHFZDrEOOYhcpFGXI8tndQXTE4FampR6cTowAo4 root@MYDB02
The key's randomart image is:
+---[RSA 2048]----+
|o++ o.+=+=+o |
| + =oo=+*+=.o|
|E =.o+OB.X.. |
|oo+XB. |
| oS.+. |
| |
| |
| |
| |
+----[SHA256]-----+
[root@MYDB02 ~]#
|
Copy after login
In this way, the public key and secret key are created, and two files **id_rsa and id_rsa.pub** will be generated.
After generating the ssh key, the key will be stored in the **.ssh/directory** in the home directory by default.
The permissions of the private key and public key are **600 and 644** respectively.
.ssh directory permissions must be 700
Options:
-t rsa|dsaThe default is rsa format.
Then you can view the generated public key and private key files:
1 2 3 4 5 6 7 8 | [root@MYDB01 ~]# cd /root/.ssh
[root@MYDB01 .ssh]# pwd
/root/.ssh
[root@MYDB01 .ssh]# ll -sh
总用量 12K
4.0K -rw-------1 root root 1.7K 2月14 16:17 id_rsa
4.0K -rw-r--r--1 root root393 2月14 16:17 id_rsa.pub
[root@MYDB01 .ssh]#
|
Copy after login
4.2 Send your public key file to the other party
# Command format:
1 | ssh-copy-id [-i [identity_file]] [user@]machine
|
Copy after login
The function of this command is to transfer the contents of the id_rsa.pub file to the other party's .ssh directory, and generate a file named authorized_keys , and The **.ssh and .ssh/authorized_keys** permissions of the remote host user directory will be set.
# Perform the following operations on MYDB01:
1 2 3 4 5 6 7 8 9 10 11 12 | [root@MYDB01 .ssh]# ssh-copy-id 192.168.250.194
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.250.194's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '192.168.250.194'"
and check to make sure that only the key(s) you wanted were added.
[root@MYDB01 .ssh]#
|
Copy after login
View here on MYDB02 host:
1 2 3 4 5 6 7 8 9 | [root@MYDB02 ~]# cd /root/.ssh
[root@MYDB02 .ssh]# ll
总用量 12
-rw------- 1 root root393 2月14 16:41 authorized_keys
-rw------- 1 root root 1679 2月14 16:20 id_rsa
-rw-r--r-- 1 root root393 2月14 16:20 id_rsa.pub
[root@MYDB02 .ssh]# cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCtQ+pBp1T9fHAkrifEShaOAfBJFT+HdljR8mBxl7wZ1a91g3Zuzu35gJKsUjD+NqP9JcdyKapE309SHPvosvsJjLfccF4PaEZAgqHryu+S3cBn8zqA6fm62hsx/qI4I80PV0btcqfwphsD+5+vgkDJWAsUGQtqZdmMClAIy5gs0He0K2jpciKHvxWWClB3+dTJ0e9yIuIkV7lM+jqVIqYFJD0bRyy0zgNsY5/cLYFllM42TQDos93hVdqGXOHREpWo01KX2Jd8MKj4yNeiqgnj2mDtiNFWOUSkAbHpcKInuUOErJMqkV7MP0er5UKY/NemDzuORr2RxYqSTWaz/T7N root@MYDB01
[root@MYDB02 .ssh]#
|
Copy after login
The above operation is only one-sided trust. Host MYDB01 does not need to enter a password to log in to the host MYDB02. The reverse is not possible, so the following operations are required:
# Copy its key on host MYDB02 to host MYDB01:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | [root@MYDB02 .ssh]# ssh-copy-id 192.168.250.193
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
The authenticity of host '192.168.250.193 (192.168.250.193)' can't be established.
ECDSA key fingerprint is SHA256:vThEoRhUOECeD5jhE+m8TZA2+6OoElIoNOQ3XqtopZw.
ECDSA key fingerprint is MD5:97:40:b2:35:6e:07:5a:61:1f:73:f1:b2:6e:54:5b:7d.
Are you sure you want to continue connecting (yes/no)? y
Please type 'yes' or 'no': yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.250.193's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '192.168.250.193'"
and check to make sure that only the key(s) you wanted were added.
[root@MYDB02 .ssh]#
|
Copy after login
4.3 Verification of mutual trust
Log in via SSH on the MYDB01 host and MYDB02 host respectively to see if you need to enter a password:
Log in on MYDB01 host MYDB02Host:
1 2 3 | [root@MYDB01 .ssh]# ssh 192.168.250.194
Last login: Tue Jan 9 15:41:56 2023 from 192.168.250.193
[root@MYDB02 ~]#
|
Copy after login
Passwordless login successful.
Similarly, log in to MYDB01host on MYDB02host:
1 2 3 4 5 | [root@MYDB02 .ssh]# ssh 192.168.250.193
Last failed login: Tue Feb 14 16:48:54 CST 2023 from 192.168.250.194 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Tue Jan 9 15:41:34 2024 from 192.168.250.194
[root@MYDB01 ~]#
|
Copy after login
The above is the detailed content of Linux SSH login mutual trust configuration. For more information, please follow other related articles on the PHP Chinese website!






