Structure and parameter analysis of log4j configuration file
Structure and parameter analysis of log4j configuration file
[Introduction]
In software development, logs are a very important tool that can help developers Record key information and error information during the operation for troubleshooting and analysis when necessary. Log4j is a commonly used Java logging framework. It provides powerful logging functions to facilitate log management and debugging for developers. This article will introduce the structure and parameter analysis of the log4j configuration file, and provide specific code examples.
[Structure of log4j configuration file]
The log4j configuration file adopts .properties or .xml file format and is used to define the behavior of log4j. The following is the structure of a typical log4j configuration file:
- Root Logger
log4j.rootLogger=[level], [appender1], [appender2]...
rootLogger is the root Logger of log4j, and all log output will pass through here. [level] indicates the log level of the root Logger. Commonly used ones include DEBUG, INFO, WARN, ERROR, and FATAL. [appender1] and [appender2] represent additional Appenders, and there can be multiple.
- Logger
log4j.logger.[package]=[level], [appender1], [appender2]...
Logger is log4j A logger used to control logging for a specific package or class. [package] represents the name of the package or class, [level] represents the log level of the Logger, which can be set to inheritance or disabled. [appender1] and [appender2] represent additional Appenders, and there can be multiple.
- Appender
log4j.appender.[name]=[class]
Appender is the log output target of log4j, used to determine the log output Destination and means. [name] represents the name of the Appender, and [class] represents the implementation class of the Appender.
- Layout
log4j.appender.[name].layout=[class]
Layout is the log layout of log4j, used to control log output format. [name] represents the name of the Appender, and [class] represents the implementation class of Layout.
[Parameter analysis and sample code]
The following are commonly used log4j configuration file parameters and their parsing instructions, and provide specific code examples:
- Log level
log4j.rootLogger=DEBUG
means setting the log level of the root Logger to DEBUG, which means that all log information will be output.
- Output to console
log4j.appender.console=org.apache.log4j.ConsoleAppender
Indicates using ConsoleAppender as the output target, that is, log Information is output to the console.
- Output to file
log4j.appender.file=org.apache.log4j.FileAppender
log4j.appender.file.File=log.log
log4j.appender.file.ImmediateFlush=true
means using FileAppender as the output target and outputting log information to the file log.log. ImmediateFlush is set to true to write information to the file immediately.
- Output to log file and perform date cutting
log4j.appender.daily=org.apache.log4j.DailyRollingFileAppender
log4j.appender.daily.File= log.log
log4j.appender.daily.DatePattern='.'yyyy-MM-dd
means using DailyRollingFileAppender as the output target and outputting the log information to the log.log file. DatePattern is set to '.'yyyy-MM-dd means that a new log file will be generated every day, with date as the suffix.
- Output to different files according to the log level
log4j.appender.debug=org.apache.log4j.RollingFileAppender
log4j.appender.debug.File=debug .log
log4j.appender.debug.Threshold=DEBUG
log4j.appender.error=org.apache.log4j.RollingFileAppender
log4j.appender.error.File=error.log
log4j.appender.error.Threshold=ERROR
means that the log information will be output to the debug.log and error.log files respectively according to the log level. Setting Threshold to DEBUG and ERROR respectively means that only log information of the corresponding level and above will be output.
[Summary]
This article introduces the structure and parameter analysis of the log4j configuration file, and provides specific code examples. As a mature and stable logging framework, log4j provides developers with powerful logging and management functions. Properly configuring the log level and output target of log4j can help developers quickly locate problems and debug, and improve development efficiency.
The above is the detailed content of Structure and parameter analysis of log4j configuration file. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
 In-depth understanding of log4j configuration: implementing log rotation and backup strategies
Feb 18, 2024 pm 02:05 PM
In-depth understanding of log4j configuration: implementing log rotation and backup strategies
Feb 18, 2024 pm 02:05 PM
Detailed explanation of log4j configuration: How to configure log rotation and backup policies, specific code examples are required Introduction: For an enterprise-level application, logs are very important. It not only helps developers track and fix bugs, but also monitors system health in real time. Log4j is one of the most commonly used logging frameworks in Java. It provides a wealth of configuration options. This article will introduce in detail the configuration method of log4j's log rotation and backup strategy, and give specific code examples. 1. Log rotation configuration The log rotation strategy is
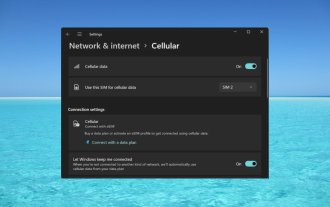 How to enable or disable eSIM on Windows 11
Sep 20, 2023 pm 05:17 PM
How to enable or disable eSIM on Windows 11
Sep 20, 2023 pm 05:17 PM
If you bought your laptop from a mobile operator, you most likely had the option to activate an eSIM and use your cellular network to connect your computer to the Internet. With eSIM, you don't need to insert another physical SIM card into your laptop because it's already built-in. It is very useful when your device cannot connect to the network. How to check if my Windows 11 device is eSIM compatible? Click the Start button and go to Network & Internet > Cellular > Settings. If you don't see the "Cellular" option, your device doesn't have eSIM capabilities and you should check another option, such as using your mobile device to connect your laptop to a hotspot. In order to activate and
 Super complete! Common ways to write configuration files in Python
Apr 11, 2023 pm 10:22 PM
Super complete! Common ways to write configuration files in Python
Apr 11, 2023 pm 10:22 PM
Why should we write the fixed file of the configuration file? We can directly write it as a .py file, such as settings.py or config.py. The advantage of this is that we can directly import parts of it through import in the same project; but if we need to use it in other When sharing configuration files on non-Python platforms, writing a single .py is not a good choice. At this time we should choose a common configuration file type to store these fixed parts. Currently, the commonly used and popular configuration file format types mainly include ini, json, toml, yaml, xml, etc. We can access these types of configuration files through standard libraries or third-party libraries.
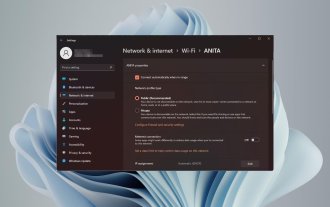 How to change network type to private or public in Windows 11
Aug 24, 2023 pm 12:37 PM
How to change network type to private or public in Windows 11
Aug 24, 2023 pm 12:37 PM
Setting up a wireless network is common, but choosing or changing the network type can be confusing, especially if you don't know the consequences. If you're looking for advice on how to change the network type from public to private or vice versa in Windows 11, read on for some helpful information. What are the different network profiles in Windows 11? Windows 11 comes with a number of network profiles, which are essentially sets of settings that can be used to configure various network connections. This is useful if you have multiple connections at home or office so you don't have to set it all up every time you connect to a new network. Private and public network profiles are two common types in Windows 11, but generally
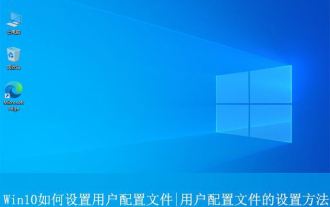 Where is the win10 user profile? How to set the user profile in Win10
Jun 25, 2024 pm 05:55 PM
Where is the win10 user profile? How to set the user profile in Win10
Jun 25, 2024 pm 05:55 PM
Recently, many Win10 system users want to change the user profile, but they don’t know how to do it. This article will show you how to set the user profile in Win10 system! How to set up user profile in Win10 1. First, press the "Win+I" keys to open the settings interface, and click to enter the "System" settings. 2. Then, in the opened interface, click "About" on the left, then find and click "Advanced System Settings". 3. Then, in the pop-up window, switch to the "" option bar and click "User Configuration" below.
 Install Helm on Ubuntu
Mar 20, 2024 pm 06:41 PM
Install Helm on Ubuntu
Mar 20, 2024 pm 06:41 PM
Helm is an important component of Kubernetes that simplifies the deployment of Kubernetes applications by bundling configuration files into a package called HelmChart. This approach makes updating a single configuration file more convenient than modifying multiple files. With Helm, users can easily deploy Kubernetes applications, simplifying the entire deployment process and improving efficiency. In this guide, I'll cover different ways to implement Helm on Ubuntu. Please note: The commands in the following guide apply to Ubuntu 22.04 as well as all Ubuntu versions and Debian-based distributions. These commands are tested and should work correctly on your system. in U
 Super complete! Common ways to write configuration files in Python
Apr 13, 2023 am 08:31 AM
Super complete! Common ways to write configuration files in Python
Apr 13, 2023 am 08:31 AM
Why write configuration files? During the development process, we often use some fixed parameters or constants. For these more fixed and commonly used parts, they are often written into a fixed file to avoid repetition in different module codes and keep the core code clean. We can directly write this fixed file into a .py file, such as settings.py or config.py. The advantage of this is that we can directly import parts of it through import in the same project; but if we need to do it on other non-Python platforms When configuring file sharing, writing a single .py is not a good choice. At this time we should choose a common configuration file type
 Log4j vulnerability repair guide: Thoroughly understand and quickly resolve log4j vulnerabilities
Feb 19, 2024 am 08:20 AM
Log4j vulnerability repair guide: Thoroughly understand and quickly resolve log4j vulnerabilities
Feb 19, 2024 am 08:20 AM
Log4j vulnerability repair tutorial: Comprehensive understanding and rapid resolution of log4j vulnerabilities, specific code examples are required Introduction: Recently, serious vulnerabilities in Apachelog4j have attracted widespread attention and discussion. This vulnerability allows an attacker to remotely execute arbitrary code via a maliciously constructed log4j configuration file, thereby compromising the security of the server. This article will comprehensively introduce the background, causes and repair methods of the log4j vulnerability, and provide specific code examples to help developers fix the vulnerability in a timely manner. 1. Vulnerability background Apa




