 Computer Tutorials
Computer Tutorials
 Computer Knowledge
Computer Knowledge
 How to check whether the file system in Linux is successfully mounted?
How to check whether the file system in Linux is successfully mounted?
How to check whether the file system in Linux is successfully mounted?

To check whether the file system in Linux is successfully mounted, you can use the following methods:
Use the df command: Use the df command to view the file system information that has been mounted in the current system. Execute the following command:
df -h
This command will display detailed information about all file systems that have been mounted in the current system, including mount points, file system types, total capacity, used space, and free space.
Use the mount command: Use the mount command to view all mounted file system information in the current system. Execute the following command:
mount
This will list all mounted file systems, including mount points, file system types, devices and other information.
Check the /etc/fstab file: The /etc/fstab
file contains file system information that needs to be mounted when the system starts. You can check this file to confirm that the file system mount is configured correctly. Execute the following command:
cat /etc/fstab
This will display the contents of the /etc/fstab file and check whether it contains the correct mount information.
Check the mount point: Directly enter the mount point directory to see if the files and directories in it can be accessed normally to determine whether the mount is successful. For example, if you want to check the mounting status of the /mnt
directory, you can execute the following command:
ls /mnt
If the files and directories in the /mnt directory can be listed, the mounting is successful.
Using the above method, you can check the mounting status of the file system in the Linux system to ensure that the file system has been successfully mounted to the specified mount point.
The above is the detailed content of How to check whether the file system in Linux is successfully mounted?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
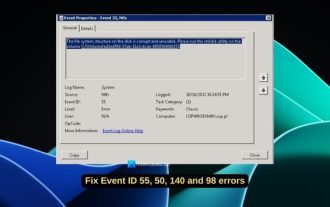 Fix event ID 55, 50, 98, 140 disk error in event viewer
Mar 19, 2024 am 09:43 AM
Fix event ID 55, 50, 98, 140 disk error in event viewer
Mar 19, 2024 am 09:43 AM
If you find event ID 55, 50, 140 or 98 in the Event Viewer of Windows 11/10, or encounter an error that the disk file system structure is damaged and cannot be used, please follow the guide below to resolve the issue. What does Event 55, File system structure on disk corrupted and unusable mean? At session 55, the file system structure on the Ntfs disk is corrupted and unusable. Please run the chkMSK utility on the volume. When NTFS is unable to write data to the transaction log, an error with event ID 55 is triggered, which will cause NTFS to fail to complete the operation unable to write the transaction data. This error usually occurs when the file system is corrupted, possibly due to the presence of bad sectors on the disk or the file system's inadequacy of the disk subsystem.
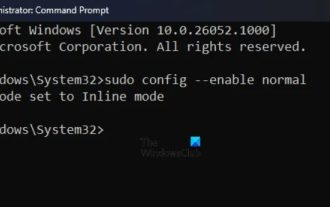 How to run SUDO commands in Windows 11/10
Mar 09, 2024 am 09:50 AM
How to run SUDO commands in Windows 11/10
Mar 09, 2024 am 09:50 AM
The sudo command allows users to run commands in elevated privilege mode without switching to superuser mode. This article will introduce how to simulate functions similar to sudo commands in Windows systems. What is the Shudao Command? Sudo (short for "superuser do") is a command-line tool that allows users of Unix-based operating systems such as Linux and MacOS to execute commands with elevated privileges typically held by administrators. Running SUDO commands in Windows 11/10 However, with the launch of the latest Windows 11 Insider preview version, Windows users can now experience this feature. This new feature enables users to
 How to check the MAC address of the network card in Win11? How to use the command to obtain the MAC address of the network card in Win11
Feb 29, 2024 pm 04:34 PM
How to check the MAC address of the network card in Win11? How to use the command to obtain the MAC address of the network card in Win11
Feb 29, 2024 pm 04:34 PM
This article will introduce readers to how to use the command prompt (CommandPrompt) to find the physical address (MAC address) of the network adapter in Win11 system. A MAC address is a unique identifier for a network interface card (NIC), which plays an important role in network communications. Through the command prompt, users can easily obtain the MAC address information of all network adapters on the current computer, which is very helpful for network troubleshooting, configuring network settings and other tasks. Method 1: Use "Command Prompt" 1. Press the [Win+X] key combination, or [right-click] click the [Windows logo] on the taskbar, and in the menu item that opens, select [Run]; 2. Run the window , enter the [cmd] command, and then
 Where is hyperv enhanced session mode? Tips for enabling or disabling Hyper-V enhanced session mode using commands in Win11
Feb 29, 2024 pm 05:52 PM
Where is hyperv enhanced session mode? Tips for enabling or disabling Hyper-V enhanced session mode using commands in Win11
Feb 29, 2024 pm 05:52 PM
In Win11 system, you can enable or disable Hyper-V enhanced session mode through commands. This article will introduce how to use commands to operate and help users better manage and control Hyper-V functions in the system. Hyper-V is a virtualization technology provided by Microsoft. It is built into Windows Server and Windows 10 and 11 (except Home Edition), allowing users to run virtual operating systems in Windows systems. Although virtual machines are isolated from the host operating system, they can still use the host's resources, such as sound cards and storage devices, through settings. One of the key settings is to enable Enhanced Session Mode. Enhanced session mode is Hyper
 Super practical! Sar commands that will make you a Linux master
Mar 01, 2024 am 08:01 AM
Super practical! Sar commands that will make you a Linux master
Mar 01, 2024 am 08:01 AM
1. Overview The sar command displays system usage reports through data collected from system activities. These reports are made up of different sections, each containing the type of data and when the data was collected. The default mode of the sar command displays the CPU usage at different time increments for various resources accessing the CPU (such as users, systems, I/O schedulers, etc.). Additionally, it displays the percentage of idle CPU for a given time period. The average value for each data point is listed at the bottom of the report. sar reports collected data every 10 minutes by default, but you can use various options to filter and adjust these reports. Similar to the uptime command, the sar command can also help you monitor the CPU load. Through sar, you can understand the occurrence of excessive load
 What is the correct way to restart a service in Linux?
Mar 15, 2024 am 09:09 AM
What is the correct way to restart a service in Linux?
Mar 15, 2024 am 09:09 AM
What is the correct way to restart a service in Linux? When using a Linux system, we often encounter situations where we need to restart a certain service, but sometimes we may encounter some problems when restarting the service, such as the service not actually stopping or starting. Therefore, it is very important to master the correct way to restart services. In Linux, you can usually use the systemctl command to manage system services. The systemctl command is part of the systemd system manager
 How to use LSOF to monitor ports in real time
Mar 20, 2024 pm 02:07 PM
How to use LSOF to monitor ports in real time
Mar 20, 2024 pm 02:07 PM
LSOF (ListOpenFiles) is a command line tool mainly used to monitor system resources similar to Linux/Unix operating systems. Through the LSOF command, users can get detailed information about the active files in the system and the processes that are accessing these files. LSOF can help users identify the processes currently occupying file resources, thereby better managing system resources and troubleshooting possible problems. LSOF is powerful and flexible, and can help system administrators quickly locate file-related problems, such as file leaks, unclosed file descriptors, etc. Via LSOF Command The LSOF command line tool allows system administrators and developers to: Determine which processes are currently using a specific file or port, in the event of a port conflict
 fstab(File System Table)
Feb 19, 2024 pm 06:30 PM
fstab(File System Table)
Feb 19, 2024 pm 06:30 PM
fstab (FileSystemTable) is a configuration file in the Linux system, used to define the rules for mounting file systems when the system starts. The fstab file is located in the /etc directory and can be created manually or modified by an editor. Each line specifies a file system to be mounted. Each line has six fields, and their meanings are as follows: The file system device file or UUID can be used to specify the device of the file system to be mounted. The UUID is a unique identifier. The UUID of the device can be obtained through the blkid command. 2. Mount point: Specify the directory to which the file system is to be mounted, which can be an absolute path (such as /mnt/data) or a relative path (such as ../data). 3. File system class





