 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 In-depth understanding of the functions and principles of SELinux
In-depth understanding of the functions and principles of SELinux
In-depth understanding of the functions and principles of SELinux

SELinux is a Mandatory Access Control (MAC) security mechanism used to protect Linux operating systems and applications from malicious attacks and unauthorized access. This article will deeply explore the functions and principles of SELinux, and provide specific code examples to help readers better understand and apply this security tool.
1. The role of SELinux
SELinux is a security mechanism implemented at the kernel level. Its purpose is to strengthen the security of the Linux system and provide more fine-grained access control. Compared with traditional Linux access control (DAC), SELinux provides more detailed permission control, which can limit program access to system resources and interactions between processes.
With SELinux, users can define rules to restrict which processes can access which files, which network ports, and other access controls to system resources. This policy-based security mechanism can reduce the risk of malicious attacks on the system and improve the overall security of the system.
2. The principle of SELinux
In SELinux, each object (such as file, process, network port, etc.) has a unique label, which is called Security Context (Security Context) . The security context contains the security attribute information of the object, such as the object's access rights, users, roles, etc.
In addition, SELinux defines system resources and operations as a set of security policies, including rules for objects and operations that are allowed to be accessed. This method effectively upgrades permission management from the user level to the system level, enhancing system security.
3. SELinux code example
Next, we will use a specific code example to demonstrate how to define security policies and access rules in SELinux.
Example:
Suppose we have a script called test_script.sh and we want the script to only read / var/log/messages file and cannot be written to other files.
- First, create a SELinux policy module file
test_script.teand define access rules:
policy_module(test_script, 1.0);
require {
type unconfined_t;
type var_log_t;
type var_t;
class file { read open getattr };
}
allow unconfined_t var_log_t:file { read getattr };
dontaudit unconfined_t var_t:file { write create unlink };- Compile and load the policy module:
$ checkmodule -m -M -o test_script.mod test_script.te $ semodule_package -o test_script.pp -m test_script.mod $ semodule -i test_script.pp
- Set a security label for the
test_script.shscript:
$ chcon -t unconfined_t /path/to/test_script.sh
Through the above steps, we successfully set the security label for test_script. The sh script defines access rules, restricts its access rights to the /var/log/messages file, and improves system security.
Conclusion
Through the introduction and examples of this article, I believe readers will have a deeper understanding of the functions and principles of SELinux. As an important security mechanism, SELinux plays an important role in protecting Linux systems from malicious attacks and unauthorized access. I hope readers can further learn and apply SELinux and strengthen system security protection.
The above is the detailed content of In-depth understanding of the functions and principles of SELinux. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Complete guide to uninstalling Kali Linux software to solve system stability problems
Mar 23, 2024 am 10:50 AM
Complete guide to uninstalling Kali Linux software to solve system stability problems
Mar 23, 2024 am 10:50 AM
This study provides a comprehensive and in-depth analysis of software uninstallation problems that may arise during the penetration testing and security audit process of KaliLinux, and contributes solutions to ensure system stability and reliability. 1. Understand the installation method of the software. Before uninstalling the software from kalilinux, it is a crucial step to first determine its installation path. Then, the appropriate offloading solution is selected accordingly based on the selected path. Common installation methods include apt-get, dpkg, source code compilation and other forms. Each strategy has its own characteristics and corresponding offloading measures. 2. Use the apt-get command to uninstall software. In the KaliLinux system, the apt-get functional component is widely used to execute software packages efficiently and conveniently.
 A complete guide to installing the domestic operating system Kirin Linux, completed in 15 minutes
Mar 21, 2024 pm 02:36 PM
A complete guide to installing the domestic operating system Kirin Linux, completed in 15 minutes
Mar 21, 2024 pm 02:36 PM
Recently, the domestic operating system Kirin Linux has attracted much attention. As a senior computer engineer, I have a strong interest in technological innovation, so I have personally experienced the installation process of this system, and now I will share my experience with you. Before executing the installation procedure, I was fully prepared for the relevant steps. The first task is to download and copy the latest Kirin Linux operating system image to a USB flash drive; secondly, for 64-bit Linux, ensure that important data in personal devices have been backed up to deal with potential installation problems; finally, shut down the computer and insert the USB flash drive. After entering the installation interface and restarting the computer, press the F12 function key promptly, enter the system boot menu and select the USB priority boot option. With a beautiful and simple startup screen appearing in front of you
 Automount drives on Linux
Mar 20, 2024 am 11:30 AM
Automount drives on Linux
Mar 20, 2024 am 11:30 AM
If you are using a Linux operating system and want the system to automatically mount the drive on boot, you can do this by adding the device's unique identifier (UID) and mount point path to the fstab configuration file. fstab is a file system table file located in the /etc directory. It contains information about the file systems that need to be mounted when the system starts. By editing the fstab file, you can ensure that the required drives are loaded correctly every time the system starts, thus ensuring stable system operation. Automatically mounting drivers can be conveniently used in a variety of situations. For example, I plan to back up my system to an external storage device. To achieve automation, ensure that the device remains connected to the system, even at startup. Likewise, many applications will directly
 Analysis of the function and principle of nohup
Mar 25, 2024 pm 03:24 PM
Analysis of the function and principle of nohup
Mar 25, 2024 pm 03:24 PM
Analysis of the role and principle of nohup In Unix and Unix-like operating systems, nohup is a commonly used command that is used to run commands in the background. Even if the user exits the current session or closes the terminal window, the command can still continue to be executed. In this article, we will analyze the function and principle of the nohup command in detail. 1. The role of nohup: Running commands in the background: Through the nohup command, we can let long-running commands continue to execute in the background without being affected by the user exiting the terminal session. This needs to be run
 The best Linux version of 2024: perfect integration of technology and art, open and innovative attitude towards life
Apr 03, 2024 am 08:01 AM
The best Linux version of 2024: perfect integration of technology and art, open and innovative attitude towards life
Apr 03, 2024 am 08:01 AM
As a Linux enthusiast in 2024, my expectations for the best Linux distribution are exciting. Below, I will explain my personal views and analyze why the most attractive Linux distribution in 2024 has many unique advantages. 1. First introduction to the most beautiful Linux distribution. There is no doubt that the best Linux distribution in 2024 can be called the perfect fusion of technology and art. It has excellent performance in many aspects such as user interface, function planning and performance optimization, making it unique in the face of many competitors. This is not only an operating system, but also a symbol of a free, open and innovative attitude towards life. This optimal version incorporates a new design and interactive mode, which is bound to be refreshing. Whether it is layout structure, logo pattern or color matching,
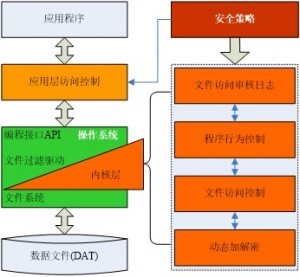 Linux kernel secure communication tool: in-depth analysis of xfrm configuration techniques
Apr 06, 2024 am 08:07 AM
Linux kernel secure communication tool: in-depth analysis of xfrm configuration techniques
Apr 06, 2024 am 08:07 AM
In the Linux operating system environment, xfrm is regarded as one of the crucial subsystems, providing comprehensive protection for the IPsec protocol, covering encryption, authentication, and security policies. By carefully setting the xfrm parameters, we can enhance the security of network data transmission and achieve the purpose of secure communication. Next, the article will have an in-depth discussion on how to configure xfrm in the Linux kernel, including the basic principles of xfrm and its configuration techniques, as well as common problems you may encounter and corresponding suggested solutions. 1.xfrm Overview XFRM, the "Transport Framework", is one of the components of the Linux kernel IPsec protocol. Its core task is to encrypt and identify Internet information through data packet conversion.
 What is PHP used for? Explore the role and functions of PHP
Mar 24, 2024 am 11:39 AM
What is PHP used for? Explore the role and functions of PHP
Mar 24, 2024 am 11:39 AM
PHP is a server-side scripting language widely used in web development. Its main function is to generate dynamic web content. When combined with HTML, it can create rich and colorful web pages. PHP is powerful. It can perform various database operations, file operations, form processing and other tasks, providing powerful interactivity and functionality for websites. In the following articles, we will further explore the role and functions of PHP, with detailed code examples. First, let’s take a look at a common use of PHP: dynamic web page generation: P
 Why do processes in Linux sleep?
Mar 20, 2024 pm 02:09 PM
Why do processes in Linux sleep?
Mar 20, 2024 pm 02:09 PM
Why do processes in Linux sleep? In the Linux operating system, a process can become dormant due to a number of different reasons and conditions. When a process is in a dormant state, it means that the process is temporarily suspended and cannot continue execution until certain conditions are met before it can be awakened to continue execution. Next, we will introduce in detail several common situations when a process enters hibernation in Linux, and illustrate them with specific code examples. Waiting for I/O to complete: When a process initiates an I/O operation (such as reading





