 Database
Database
 Mysql Tutorial
Mysql Tutorial
 Oracle API security management and control: ensuring data transmission reliability
Oracle API security management and control: ensuring data transmission reliability
Oracle API security management and control: ensuring data transmission reliability

Title: Oracle API Security Management and Control: To ensure the reliability of data transmission, specific code examples are required
Data plays a vital role in today's information age , and data transmission security is an important issue that any organization must pay close attention to. Especially for companies using Oracle databases, ensuring API security and data transmission reliability is particularly critical. Through correct security management and control measures, potential data leakage, tampering or destruction can be effectively prevented and the confidentiality, integrity and availability of data can be ensured. This article will focus on the importance of Oracle API security management and control, and give specific code examples to help readers better understand and practice.
First of all, we need to understand the basic principles of Oracle API security management. In the Oracle database, API (Application Programming Interface) is an interface used to communicate with the database. Through the API, operations such as data query, insertion, update, and deletion can be implemented. Since APIs involve operating on sensitive data in databases, security controls must be strengthened to prevent malicious attacks or data leaks. When conducting API security management, the following aspects require our attention:
- Authentication (Authentication): Ensure that only authorized users or applications can access the API to prevent unauthorized persons from exceeding their rights. Access the database.
- Authorization: Differentiate different users or applications and assign corresponding operation permissions to ensure that data can only be accessed and operated by authorized users.
- Encryption: Encrypt the transmitted data to prevent the data from being stolen or tampered with during transmission.
- Monitoring: Monitor API usage and data access in real time, detect abnormal operations in a timely manner and respond accordingly.
Below, we will use specific code examples to show how to implement API security management and control in Oracle database.
First, let’s look at how to perform user authentication and authorization. In the Oracle database, we can complete authentication and authorization by creating users, roles and permissions. The following is a simple example:
1 2 3 4 5 6 7 8 9 10 11 |
|
With the above code, we create a user named my_user and create a role for it api_user, and assign the role to the user. At the same time, we also granted the api_user role the query, insert, update, and delete permissions on the my_table table. In this way, only users with the api_user role can operate on the my_table table.
Next, let’s look at how to encrypt data. In the Oracle database, we can use the DBMS_CRYPTO package to encrypt and decrypt data. The following is a simple example:
1 2 3 4 5 6 7 8 9 10 11 12 |
|
Through the above code, we use the DES3 algorithm to encrypt a piece of data and store the encrypted data in l_encrypted_data. In practical applications, we can write encrypted data into the database, or use encryption technology to ensure secure transmission of data when transmitting data over the network.
Finally, we need to implement the monitoring function of the API. In the Oracle database, we can track and monitor database operations by using the Audit function. The following is a simple example:
1 2 3 4 5 6 7 8 |
|
Through the above code, we audited the SELECT operation of the my_table table, and also audited the INSERT, UPDATE, and DELETE operations. In practical applications, we can view the audit records of database operations by querying the DBA_AUDIT_TRAIL table, and discover and respond to abnormal operations in a timely manner.
To sum up, by properly setting up authentication, authorization, encryption and monitoring measures, we can effectively manage and control the security of Oracle API and ensure the reliability of data transmission. Through specific code examples and technical means, we can better understand and practice API security management and control to ensure the safety and stability of database operations. We hope that the above content will be helpful to readers and draw attention to and in-depth study of API security management.
The above is the detailed content of Oracle API security management and control: ensuring data transmission reliability. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
 Why is Bittensor said to be the 'bitcoin' in the AI track?
Mar 04, 2025 pm 04:06 PM
Why is Bittensor said to be the 'bitcoin' in the AI track?
Mar 04, 2025 pm 04:06 PM
Original title: Bittensor=AIBitcoin? Original author: S4mmyEth, Decentralized AI Research Original translation: zhouzhou, BlockBeats Editor's note: This article discusses Bittensor, a decentralized AI platform, hoping to break the monopoly of centralized AI companies through blockchain technology and promote an open and collaborative AI ecosystem. Bittensor adopts a subnet model that allows the emergence of different AI solutions and inspires innovation through TAO tokens. Although the AI market is mature, Bittensor faces competitive risks and may be subject to other open source
 How to convert XML files to PDF on your phone?
Apr 02, 2025 pm 10:12 PM
How to convert XML files to PDF on your phone?
Apr 02, 2025 pm 10:12 PM
It is impossible to complete XML to PDF conversion directly on your phone with a single application. It is necessary to use cloud services, which can be achieved through two steps: 1. Convert XML to PDF in the cloud, 2. Access or download the converted PDF file on the mobile phone.
 Recommended XML formatting tool
Apr 02, 2025 pm 09:03 PM
Recommended XML formatting tool
Apr 02, 2025 pm 09:03 PM
XML formatting tools can type code according to rules to improve readability and understanding. When selecting a tool, pay attention to customization capabilities, handling of special circumstances, performance and ease of use. Commonly used tool types include online tools, IDE plug-ins, and command-line tools.
 Redstone/RED currency listing price forecast and detailed explanation of token economics
Mar 03, 2025 pm 10:42 PM
Redstone/RED currency listing price forecast and detailed explanation of token economics
Mar 03, 2025 pm 10:42 PM
This time, the Redstone token $RED will be launched on Binance Launchpool on Binance TGE! This is also the first time Binance has launched a pre-market trading limit mechanism! The first day limit is 200%, and the ban will be lifted after 3 days to avoid "the peak will be achieved when the market opens"! Launchpool mechanism introduces the BinanceLaunchpool participating in Redstone that needs to pledge designated tokens (BNB, USDC, FDUSD) activity period is 48 hours: 08:00 UTC on February 26, 2025 to 08:00 UTC on February 28, 2025 ending this pre-market daily limit rule: 18:00 on February 28, 2025
 How to do Oracle security settings on Debian
Apr 02, 2025 am 07:48 AM
How to do Oracle security settings on Debian
Apr 02, 2025 am 07:48 AM
To strengthen the security of Oracle database on the Debian system, it requires many aspects to start. The following steps provide a framework for secure configuration: 1. Oracle database installation and initial configuration system preparation: Ensure that the Debian system has been updated to the latest version, the network configuration is correct, and all required software packages are installed. It is recommended to refer to official documents or reliable third-party resources for installation. Users and Groups: Create a dedicated Oracle user group (such as oinstall, dba, backupdba) and set appropriate permissions for it. 2. Security restrictions set resource restrictions: Edit /etc/security/limits.d/30-oracle.conf
 How to access DeepSeekapi - DeepSeekapi access call tutorial
Mar 12, 2025 pm 12:24 PM
How to access DeepSeekapi - DeepSeekapi access call tutorial
Mar 12, 2025 pm 12:24 PM
Detailed explanation of DeepSeekAPI access and call: Quick Start Guide This article will guide you in detail how to access and call DeepSeekAPI, helping you easily use powerful AI models. Step 1: Get the API key to access the DeepSeek official website and click on the "Open Platform" in the upper right corner. You will get a certain number of free tokens (used to measure API usage). In the menu on the left, click "APIKeys" and then click "Create APIkey". Name your APIkey (for example, "test") and copy the generated key right away. Be sure to save this key properly, as it will only be displayed once
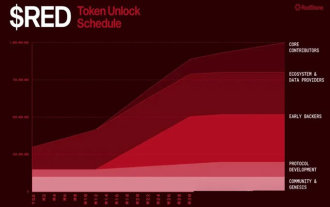 64th issue launchpool modular oracle: RED project analysis & reasonable currency price estimate
Mar 04, 2025 am 08:12 AM
64th issue launchpool modular oracle: RED project analysis & reasonable currency price estimate
Mar 04, 2025 am 08:12 AM
In-depth analysis of the 64th issue of Launchpool project RED: Modular oracle prospects and currency price predictions This article deeply analyzes the 64th issue of Launchpool project RED - a multi-chain oracle project across EVM and non-EVM chains, and makes reasonable estimates of the project fundamentals and currency price. The RED project was launched for only 2 days, with the total volume of Launchpool being 40,000,000RED (accounting for 4% of the maximum supply of tokens), and the initial circulation was 280,000,000RED (accounting for 28% of the total supply of tokens). Project Overview: RedStone is a modular blockchain oracle founded in 2020 and incubated by Arweave Chain with the team from Estonia. Currently supports 70 chains
 How to evaluate the destructive power of the website after discovering suspicious Trojan files?
Apr 01, 2025 am 08:39 AM
How to evaluate the destructive power of the website after discovering suspicious Trojan files?
Apr 01, 2025 am 08:39 AM
When a suspicious Trojan file is found on the website, how to evaluate its destructive power? Recently, a suspicious Trojan file was found while performing a security scan on the website. ...



