A simple article explaining what a hash algorithm is! What is a hash algorithm?
In understanding Bitcoin investment and blockchain technology, hash algorithms can be said to appear frequently. The currency circle jokes that rap has hip-hop, and algorithms have hash. As for the word "algorithm", it is currently used vaguely by domestic users. Sometimes it refers to the consensus mechanism, and sometimes it refers to the specific Hash algorithm. As a blockchain algorithm, the Hash algorithm has always been obscure to the general public. So, what is Hash algorithm? Hash algorithm? Next, the editor of the currency circle will give you a simple explanation of what a hash algorithm is? I hope that investors can understand the hash algorithm after reading this article.
What is a hash algorithm?
Hash is transliterated from "Hash", also known as "Hash". It is essentially a way for a computer program to take an input of any length and then run it through a hashing algorithm to create a small digital "fingerprint". For example, the combination of numbers and letters produces a "hash value". In mathematical terms, this hash function maps data of any length onto a domain of limited length. In general, hash functions are used to compress messages or data, generate data digests, and ultimately make the data size smaller and have a fixed format.
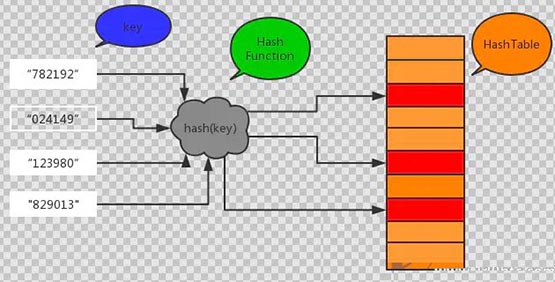
Characteristics of hash algorithm
1. Easy compression: For any size of input x, the length of the Hash value is very small. In practical applications, The length of the Hash value generated by function H is fixed.
2. Easy to calculate: For any given message, it is relatively easy to calculate its Hash value.
“3. One-wayness refers to finding a process that makes its reverse computation difficult for a specific hash value. In other words, it is a task to reversely deduce the original input from the hash output. A challenging task. One-wayness is one of the foundations for ensuring the security of hash functions. For a given hash function H and its hash value H(M), it is computationally infeasible to infer M. ”
4. Collision resistance: The ideal Hash function is collision-free, but it is difficult to achieve this in the design of actual algorithms.
There are two types of collision resistance: one is weak collision resistance, which means that it is computationally impossible to find another message such that its hash value is the same as the given message; the other is strong collision resistance property, that is, it is computationally infeasible to find two different messages with the same hash value.
High sensitivity is viewed from the perspective of bits, which means that a change in one bit will cause half of the bits to change. This means that any slight change in the message M will cause the hash value H(M) to change, and even if the input is only slightly different, the hashed output will be completely different. This feature ensures that the hash function can respond sensitively to subtle changes in the input data, so that any modifications are accurately reflected in the hash value.
Use of hash algorithm:
Hash algorithm can check whether the information is the same. This advantage can save the time of repeated file transmission.
To give a very common example in life, we will use some software to transfer file data to others in life and work. If someone sends a file to one person, and then another person sends the same file If it is given to another person, then the social software will compare the hash values of the two transmissions when it transmits the file for the second time. If it is found that they are the same, the software will not upload the file to the server again.
In addition, the hash algorithm can also verify whether the owner of the information is authentic.
For example, if we register an account on a website, if the website saves the password, no matter how safe the website is, there will be a risk of being stolen. But if you use the hash value of the password instead of saving the password, there is no such risk, because the hash value encryption process is not irreversible.
The above is the detailed content of A simple article explaining what a hash algorithm is! What is a hash algorithm?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1381
1381
 52
52
 What is Ouyi for? What is Ouyi
Apr 01, 2025 pm 03:18 PM
What is Ouyi for? What is Ouyi
Apr 01, 2025 pm 03:18 PM
OKX is a global digital asset trading platform. Its main functions include: 1. Buying and selling digital assets (spot trading), 2. Trading between digital assets, 3. Providing market conditions and data, 4. Providing diversified trading products (such as derivatives), 5. Providing asset value-added services, 6. Convenient asset management.
 How to roll positions in digital currency? What are the digital currency rolling platforms?
Mar 31, 2025 pm 07:36 PM
How to roll positions in digital currency? What are the digital currency rolling platforms?
Mar 31, 2025 pm 07:36 PM
Digital currency rolling positions is an investment strategy that uses lending to amplify trading leverage to increase returns. This article explains the digital currency rolling process in detail, including key steps such as selecting trading platforms that support rolling (such as Binance, OKEx, gate.io, Huobi, Bybit, etc.), opening a leverage account, setting a leverage multiple, borrowing funds for trading, and real-time monitoring of the market and adjusting positions or adding margin to avoid liquidation. However, rolling position trading is extremely risky, and investors need to operate with caution and formulate complete risk management strategies. To learn more about digital currency rolling tips, please continue reading.
 How to calculate the transaction fee of gate.io trading platform?
Mar 31, 2025 pm 09:15 PM
How to calculate the transaction fee of gate.io trading platform?
Mar 31, 2025 pm 09:15 PM
The handling fees of the Gate.io trading platform vary according to factors such as transaction type, transaction pair, and user VIP level. The default fee rate for spot trading is 0.15% (VIP0 level, Maker and Taker), but the VIP level will be adjusted based on the user's 30-day trading volume and GT position. The higher the level, the lower the fee rate will be. It supports GT platform coin deduction, and you can enjoy a minimum discount of 55% off. The default rate for contract transactions is Maker 0.02%, Taker 0.05% (VIP0 level), which is also affected by VIP level, and different contract types and leverages
 Tutorial on how to register, use and cancel Ouyi okex account
Mar 31, 2025 pm 04:21 PM
Tutorial on how to register, use and cancel Ouyi okex account
Mar 31, 2025 pm 04:21 PM
This article introduces in detail the registration, use and cancellation procedures of Ouyi OKEx account. To register, you need to download the APP, enter your mobile phone number or email address to register, and complete real-name authentication. The usage covers the operation steps such as login, recharge and withdrawal, transaction and security settings. To cancel an account, you need to contact Ouyi OKEx customer service, provide necessary information and wait for processing, and finally obtain the account cancellation confirmation. Through this article, users can easily master the complete life cycle management of Ouyi OKEx account and conduct digital asset transactions safely and conveniently.
 Binance binance computer version entrance Binance binance computer version PC official website login entrance
Mar 31, 2025 pm 04:36 PM
Binance binance computer version entrance Binance binance computer version PC official website login entrance
Mar 31, 2025 pm 04:36 PM
This article provides a complete guide to login and registration on Binance PC version. First, we explained in detail the steps for logging in Binance PC version: search for "Binance Official Website" in the browser, click the login button, enter the email and password (enable 2FA to enter the verification code) to log in. Secondly, the article explains the registration process: click the "Register" button, fill in the email address, set a strong password, and verify the email address to complete the registration. Finally, the article also emphasizes account security, reminding users to pay attention to the official domain name, network environment, and regularly updating passwords to ensure account security and better use of various functions provided by Binance PC version, such as viewing market conditions, conducting transactions and managing assets.
 What are the recommended websites for virtual currency app software?
Mar 31, 2025 pm 09:06 PM
What are the recommended websites for virtual currency app software?
Mar 31, 2025 pm 09:06 PM
This article recommends ten well-known virtual currency-related APP recommendation websites, including Binance Academy, OKX Learn, CoinGecko, CryptoSlate, CoinDesk, Investopedia, CoinMarketCap, Huobi University, Coinbase Learn and CryptoCompare. These websites not only provide information such as virtual currency market data, price trend analysis, etc., but also provide rich learning resources, including basic blockchain knowledge, trading strategies, and tutorials and reviews of various trading platform APPs, helping users better understand and make use of them
 Currency Trading Network Official Website Collection 2025
Mar 31, 2025 pm 03:57 PM
Currency Trading Network Official Website Collection 2025
Mar 31, 2025 pm 03:57 PM
It ranks among the top in the world, supports all categories of transactions such as spot, contracts, and Web3 wallets. It has high security and low handling fees. A comprehensive trading platform with a long history, known for its compliance and high liquidity, supports multilingual services. The industry leader covers currency trading, leverage, options, etc., with strong liquidity and supports BNB deduction fees.
 On which platform is web3 transaction?
Mar 31, 2025 pm 07:54 PM
On which platform is web3 transaction?
Mar 31, 2025 pm 07:54 PM
This article lists the top ten well-known Web3 trading platforms, including Binance, OKX, Gate.io, Kraken, Bybit, Coinbase, KuCoin, Bitget, Gemini and Bitstamp. The article compares the characteristics of each platform in detail, such as the number of currencies, trading types (spot, futures, options, NFT, etc.), handling fees, security, compliance, user groups, etc., aiming to help investors choose the most suitable trading platform. Whether it is high-frequency traders, contract trading enthusiasts, or investors who focus on compliance and security, they can find reference information from it.



