 Technology peripherals
Technology peripherals
 It Industry
It Industry
 The European Commission launches a formal investigation into AliExpress to assess whether it violated the Digital Services Act
The European Commission launches a formal investigation into AliExpress to assess whether it violated the Digital Services Act
The European Commission launches a formal investigation into AliExpress to assess whether it violated the Digital Services Act
The European Commission announced today evening, Beijing time, that it has launched formal procedures to evaluate AliExpress, a subsidiary of Alibaba, to determine whether it has violated the Digital Services Act (DSA). This decision has attracted widespread attention and will further affect the development and regulation of the digital services industry.
Manage and mitigate risk
Content moderation and internal complaints handling mechanism
Advertising and recommendations Transparency of the system
Traceability of traders, reliability and integrity of information
Data access for researchers
Based on the preliminary investigation conducted to date, including analysis of the risk assessment report sent by AliExpress in August 2023, the information published in its transparency report and its formal request for information from the Commission. Reply, The Commission decided to initiate a formal investigation against AliExpress under the Digital Services Act.
This site learned from the announcement that according to the "Digital Services Act", Alibaba AliExpress was designated as a " "Super large online platform", previously announced that its monthly active users in the EU have reached 104.3 million . As such a platform, AliExpress must begin to fulfill a series of obligations stipulated in the Digital Services Act four months after being designated.
According to Alibaba’s fiscal 2024 third quarter financial report released last month, Alibaba International Digital Business Group’s revenue increased by 44% year-on-year, while AliExpress’s order volume increased by more than 60% year-on-year.
The above is the detailed content of The European Commission launches a formal investigation into AliExpress to assess whether it violated the Digital Services Act. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Alibaba Cloud announced that the 2024 Yunqi Conference will be held in Hangzhou from September 19th to 21st. Free application for free tickets
Aug 07, 2024 pm 07:12 PM
Alibaba Cloud announced that the 2024 Yunqi Conference will be held in Hangzhou from September 19th to 21st. Free application for free tickets
Aug 07, 2024 pm 07:12 PM
According to news from this website on August 5, Alibaba Cloud announced that the 2024 Yunqi Conference will be held in Yunqi Town, Hangzhou from September 19th to 21st. There will be a three-day main forum, 400 sub-forums and parallel topics, as well as nearly four Ten thousand square meters of exhibition area. Yunqi Conference is free and open to the public. From now on, the public can apply for free tickets through the official website of Yunqi Conference. An all-pass ticket of 5,000 yuan can be purchased. The ticket website is attached on this website: https://yunqi.aliyun.com/2024 /ticket-list According to reports, the Yunqi Conference originated in 2009 and was originally named the First China Website Development Forum. In 2011, it evolved into the Alibaba Cloud Developer Conference. In 2015, it was officially renamed the "Yunqi Conference" and has continued to successful move
 What does dao mean in java
Apr 21, 2024 am 02:08 AM
What does dao mean in java
Apr 21, 2024 am 02:08 AM
DAO (Data Access Object) in Java is used to separate application code and persistence layer, its advantages include: Separation: Independent from application logic, making it easier to modify it. Encapsulation: Hide database access details and simplify interaction with the database. Scalability: Easily expandable to support new databases or persistence technologies. With DAOs, applications can call methods to perform database operations such as create, read, update, and delete entities without directly dealing with database details.
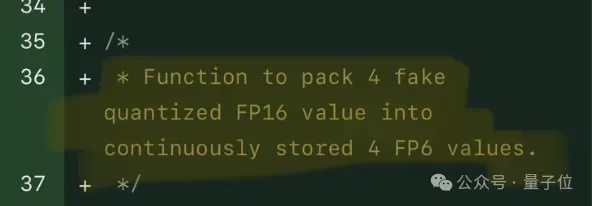 Single card running Llama 70B is faster than dual card, Microsoft forced FP6 into A100 | Open source
Apr 29, 2024 pm 04:55 PM
Single card running Llama 70B is faster than dual card, Microsoft forced FP6 into A100 | Open source
Apr 29, 2024 pm 04:55 PM
FP8 and lower floating point quantification precision are no longer the "patent" of H100! Lao Huang wanted everyone to use INT8/INT4, and the Microsoft DeepSpeed team started running FP6 on A100 without official support from NVIDIA. Test results show that the new method TC-FPx's FP6 quantization on A100 is close to or occasionally faster than INT4, and has higher accuracy than the latter. On top of this, there is also end-to-end large model support, which has been open sourced and integrated into deep learning inference frameworks such as DeepSpeed. This result also has an immediate effect on accelerating large models - under this framework, using a single card to run Llama, the throughput is 2.65 times higher than that of dual cards. one
 What does schema mean in mysql
May 01, 2024 pm 08:33 PM
What does schema mean in mysql
May 01, 2024 pm 08:33 PM
Schema in MySQL is a logical structure used to organize and manage database objects (such as tables, views) to ensure data consistency, data access control and simplify database design. The functions of Schema include: 1. Data organization; 2. Data consistency; 3. Data access control; 4. Database design.
 How to remove the write protection of a USB flash drive? Several simple and effective methods can help you do it
May 02, 2024 am 09:04 AM
How to remove the write protection of a USB flash drive? Several simple and effective methods can help you do it
May 02, 2024 am 09:04 AM
U disk is one of the commonly used storage devices in our daily work and life, but sometimes we encounter situations where the U disk is write-protected and cannot write data. This article will introduce several simple and effective methods to help you quickly remove the write protection of the USB flash drive and restore the normal use of the USB flash drive. Tool materials: System version: Windows1020H2, macOS BigSur11.2.3 Brand model: SanDisk UltraFlair USB3.0 flash drive, Kingston DataTraveler100G3USB3.0 flash drive Software version: DiskGenius5.4.2.1239, ChipGenius4.19.1225 1. Check the physical write protection switch of the USB flash drive on some USB flash drives Designed with
 What is the API interface for?
Apr 23, 2024 pm 01:51 PM
What is the API interface for?
Apr 23, 2024 pm 01:51 PM
An API interface is a specification for interaction between software components and is used to implement communication and data exchange between different applications or systems. The API interface acts as a "translator", converting the developer's instructions into computer language so that the applications can work together. Its advantages include convenient data sharing, simplified development, improved performance, enhanced security, improved productivity and interoperability.
 Redis cache implementation principle
Apr 19, 2024 pm 10:36 PM
Redis cache implementation principle
Apr 19, 2024 pm 10:36 PM
The Redis caching mechanism is implemented through key-value storage, memory storage, expiration policies, data structures, replication, and persistence. It follows the steps of obtaining data, cache hit, cache miss, writing to cache, and updating cache to provide fast data access and high-performance caching services.
 Data Security in Artificial Intelligence: How to Unleash the Power of Artificial Intelligence
Apr 24, 2024 pm 06:20 PM
Data Security in Artificial Intelligence: How to Unleash the Power of Artificial Intelligence
Apr 24, 2024 pm 06:20 PM
In the digital age, data is often viewed as the battery that powers the innovation machine and drives business decisions. With the rise of modern solutions like artificial intelligence (AI) and machine learning (ML), organizations have access to vast amounts of data, enough to gain valuable insights and make informed decisions. However, this comes at the cost of subsequent data loss and confidentiality challenges. As organizations continue to grasp the potential of artificial intelligence, they must strike a balance between achieving business advancements while avoiding potential risks. This article focuses on the importance of data security in artificial intelligence and what security measures organizations can take to avoid risks while taking advantage of the viable solutions provided by artificial intelligence. In artificial intelligence, data security is crucial. Organizations need to ensure data used is legal





