"Hidden Files" Ace Security Clearance Strategy
"Hidden Files" Ace Security is a puzzle adventure game that is loved by players. Players need to play a top security guard, unlock various puzzles, and complete tasks. In the game, players need to use clever operations and strategies to use the intelligence of the ace security guard to solve various problems. In this article, Banana, the editor of PHP, has carefully prepared the "Hidden Files" Ace Security Clearance Guide for you to help you successfully pass the game and experience the fun of the game!

"Secret Files" Ace Security Clearance Strategy
Level: Ace Security
Game mission: Find out the abnormalities and do the following Select
Steps to pass
1. To enter the game, first click on the frog doll on the computer screen, and then find the damage on the door, the doll clothes, the green footprints on the ground, and the dog head on the wall. Mark and control these five dangerous places with knives;

#2. Then we click on the peephole to find the brand new umbrella, the bloody rusty knife, and the slip-on jacket pocket. Find the three dangerous places on the phone, and then choose not to open the door;

3. Then see another person and find three abnormal points on her body, namely the back Hidden knife, face in a good mood, filial piety cloth on the waist, and then choose not to open the door;

#4. Then find the abnormal points on the next person, which are the doll clothes , vertical pupil, green marker on hand, green footprints on the ground;

5. Then swipe right to see the woman in yellow, click on the woman in yellow, and then choose not to open the door You can pass the level.

The above is the detailed content of "Hidden Files" Ace Security Clearance Strategy. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 How to correct the yellowing of the computer screen
Apr 30, 2024 am 08:58 AM
How to correct the yellowing of the computer screen
Apr 30, 2024 am 08:58 AM
How to adjust the computer screen when it turns yellow? 1. Move the slider in the window to adjust the screen color, and the problem is solved. The method may be caused by a problem with the monitor data cable or poor contact. You can check whether the interface is loose and then replace the connection cable with a new one. 2. Click the Windows icon in the lower left corner of the computer, and then click Settings. In the settings interface, click System. Select Display, click Advanced display settings, and that's it. First open the control panel. 3. Move the slider in the window to adjust the gamma value. Finally, move the slider in the window to adjust the screen color and the problem is solved. Why does the computer screen turn yellow? It is relatively rare that the computer screen turns yellow due to a malfunction of the graphics card itself. It is recommended to have it checked for maintenance. Monitor display mode problem some display
 A simple way to set up automatic line wrapping with Beyond Compare
Apr 22, 2024 pm 01:04 PM
A simple way to set up automatic line wrapping with Beyond Compare
Apr 22, 2024 pm 01:04 PM
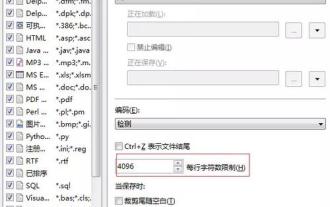
In fact, BeyondCompare does not support automatic line wrapping. In the new version BeyondCompare4, you can limit the characters of each line of the file to achieve the purpose of automatic line wrapping for easy modification. You can follow the steps below: Click: Tools (T) in the menu bar, then select: File Format (F) in the pop-up list; find 'Characters per line' in the [Convert] tab on the right side of the pop-up box For the word "limit", modify the previous value (the default is 4096) and save it. Generally, it can be set to 80 to 90 or more. Of course, in BeyondCompare, you can also consider other ways to slightly improve it. The solution is as follows: Solution 1: Temporarily switch to the upper and lower layout. Select under the [View] menu
 How many centimeters is an 8-inch tablet?
Apr 22, 2024 pm 04:25 PM
How many centimeters is an 8-inch tablet?
Apr 22, 2024 pm 04:25 PM
How big is an eight-inch tablet? 1. The size of an 8-inch tablet is 32 cm; the size of a 9-inch tablet is 286 cm; the size of a 7-inch tablet is 2638 cm; and the size of a 10-inch tablet is 24 cm. 2. The aspect ratio of a 2-inch tablet computer is 16:9, so the screen length and width are 32 cm and 11 cm respectively. The so-called 8-inch tablet computer refers to the size of the screen, not the size of the overall machine. The 8-inch screen size refers to the diagonal length of the screen. 1 inch is equal to 54 centimeters, so 8 inches is equal to 32 centimeters. 3. The eight-inch tablet is 128 cm long and 80 cm wide. An eight-inch tablet refers to a tablet with a screen diagonal length of 8 inches. Based on the common screen aspect ratio of 16:10, it can be calculated that its length is approximately 128 cm.
 How to disable automatic backup in Windows 10
Apr 18, 2024 pm 07:49 PM
How to disable automatic backup in Windows 10
Apr 18, 2024 pm 07:49 PM
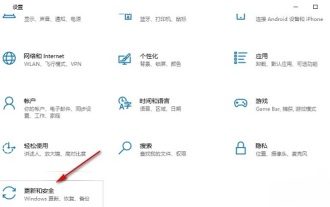
Some Windows 10 users have found that the system's built-in automatic backup function is activated during use. Although this function helps ensure data security, some users may not feel the need to continue enabling it due to storage space considerations or other reasons. This function. Therefore, if you want to turn off the automatic backup function in Windows 10 system, the correct operation steps are particularly important. Next, this article will introduce in detail how to turn off the automatic backup function of the Win10 system for the reference implementation of users who have this need. Close method 1. Use the "win+i" shortcut key to quickly open the "Settings" page. After entering the new page, you need to click the "Update and Security" option. 2. In the new interface that opens, click in the left column
 How to hide or turn off the taskbar volume icon in Windows 10
Apr 15, 2024 pm 05:19 PM
How to hide or turn off the taskbar volume icon in Windows 10
Apr 15, 2024 pm 05:19 PM
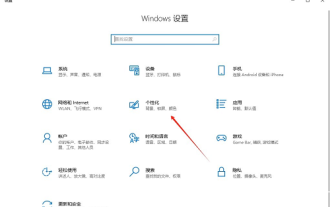
In the Windows 10 operating system, the taskbar usually displays an intuitive volume icon under default settings, allowing users to adjust the system volume at any time. Some friends hope to turn off or hide this volume control icon due to personal preference or interface simplicity. The following is a detailed operation plan for everyone, let’s take a look. Close method 1. Use the "win+i" shortcut key to open the "Settings" interface. After entering the "Settings" interface, you need to click the "Personalization" option. 2. In the new interface that opens, you need to click the "Taskbar" option in the left column. 3. Then click "Select which icons appear on the taskbar" in the "Notification Area" on the right. 4. Then find the "Volume", and finally click the switch button on the right.
 Laptop external monitor cannot go full screen
Apr 19, 2024 pm 04:16 PM
Laptop external monitor cannot go full screen
Apr 19, 2024 pm 04:16 PM
What to do if the laptop screen is not full screen? Steps: 1. Turn on the computer, right-click on the desktop and click the "Display Settings" option. Adjust the resolution so that the monitor fills the entire screen. If you don't want to change the current resolution, click "Advanced display settings". In the interface, find and click the "Display Adapter Properties for Monitor 1" option. If the computer monitor cannot display in full screen, it may be because the screen resolution setting is incorrect, or the monitor OSD setting is wrong. You can correct the settings to restore full screen display. The specific operation method is as follows: Set the screen resolution correctly (taking WIN7 as an example): right-click a blank space on the desktop and select "Screen Resolution". Adjust the resolution so that the monitor fills the entire screen. If you don't want to change the current resolution, click "Advanced display settings". In the interface, find and click "
 How to improve computer startup speed by modifying Windows 10 registry
Apr 19, 2024 am 08:01 AM
How to improve computer startup speed by modifying Windows 10 registry
Apr 19, 2024 am 08:01 AM
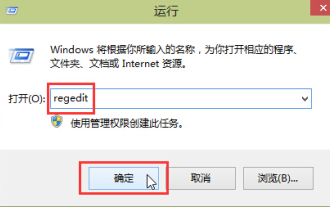
In the process of using the Windows 10 operating system, many users find that it takes a long time to start up their computers, which affects the user experience. In order to optimize the boot speed, some people have suggested that the purpose can be achieved by modifying the system registry. In response to this demand, this article will provide an in-depth analysis of how to effectively improve computer startup speed by properly adjusting Windows 10 registry settings. Let’s take a look below. Operation method 1. Use the "win+R" shortcut key to start running, enter "regedit", and click "OK" to open. 2. After entering the Registry Editor, click "HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurren" in the left column
 How to transfer files from WeChat on mobile phone to computer
Apr 19, 2024 am 08:30 AM
How to transfer files from WeChat on mobile phone to computer
Apr 19, 2024 am 08:30 AM
How to transfer files from WeChat to computer Question 4: How to transfer files from WeChat on mobile phone to computer Method 1: Use WeChat File Transfer Assistant to log in to WeChat web version. (Website: wx.qq) Users can log in to the WeChat web version by scanning the QR code on the webpage with their mobile phone. Then long press the document and click Multi-select, as shown in the figure below. 03 Then click on the three dots at the bottom right of the screen, as shown in the picture below. 04Then click to download the selected content, as shown in the figure below. Open the browser and open the WeChat web version. Click on the official WeChat web version. Use your mobile phone WeChat to scan the QR code to log in. Use WeChat on your mobile phone to scan and scan the code. Click to log in on your mobile phone and agree to log in to the web version of WeChat. After logging in to the web version of WeChat, the file transfer assistant appears. Use WeChat on your mobile phone to find File Transfer Assistant.




