 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 Understand the classification and characteristics of Linux systems
Understand the classification and characteristics of Linux systems
Understand the classification and characteristics of Linux systems

Classification and characteristics of Linux system
In the field of computer science, Linux operating system is widely used in various devices and scenarios. Its open source nature makes it popular. This article will introduce the classification and characteristics of Linux systems, and explain them with specific code examples.
1. Classification of Linux systems
Linux systems can be divided into many different classifications according to their uses and functions, mainly including the following:
- Server version of Linux: Used to build network servers, website services and other scenarios, such as Ubuntu Server, CentOS, etc. It is characterized by stability, efficiency and powerful network functions.
- Desktop version of Linux: Desktop operating system suitable for individual users, such as Ubuntu, Fedora, etc. Desktop Linux usually has a good user interface and rich application support.
- Embedded Linux: Used in embedded devices, such as smart homes, smartphones, etc., and can be customized according to needs. For example, the Android operating system is built on the Linux kernel.
- Real-time Linux: A Linux system with real-time performance, suitable for scenarios with high real-time requirements, such as industrial control, aerospace, etc. RTLinux is a real-time Linux system.
2. Characteristics of Linux system
Linux system has many outstanding characteristics, which make it widely used and developed in various fields, mainly including the following points:
- Open source and free: The Linux system follows the GNU General Public License and is open source and free. Anyone can view, modify and distribute the source code.
- Multi-user and multi-tasking: The Linux system supports multiple users to log in at the same time and can perform multiple tasks at the same time to improve system resource utilization.
- Stable and reliable: Linux system is considered to be a very stable and reliable operating system that can maintain good operation even under high load.
- Strong security: The Linux system has a high degree of security, is less threatened by viruses and malware, and has a complete rights management mechanism.
- Highly customizable: The source code of the Linux system kernel can be tailored and customized as needed, so various customized Linux distributions can be implemented on different devices.
3. Specific code examples
The following are some specific code examples, showing some features of the Linux system:
# View Linux system version information uname -a # Check system resource usage top # Install package management tools apt-get install <package_name> #Write a simple shell script echo "Hello, Linux!" # Set file permissions chmod 755 <file_name>
Through the above code examples, we can experience the flexibility and powerful functions of the Linux system, which is one of the reasons for its popularity.
Conclusion
As an open source operating system, Linux system has shown strong charm in different fields. By understanding its classification and characteristics, and demonstrating it through specific code examples, we hope that readers will have a deeper understanding of the power of the Linux system and thus better utilize it to meet various needs and challenges.
The above is the detailed content of Understand the classification and characteristics of Linux systems. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 Using Task Manager in Linux
Aug 15, 2024 am 07:30 AM
Using Task Manager in Linux
Aug 15, 2024 am 07:30 AM
There are many questions that Linux beginners often ask, "Does Linux have a Task Manager?", "How to open the Task Manager on Linux?" Users from Windows know that the Task Manager is very useful. You can open the Task Manager by pressing Ctrl+Alt+Del in Windows. This task manager shows you all the running processes and the memory they consume, and you can select and kill a process from the task manager program. When you first use Linux, you will also look for something that is equivalent to a task manager in Linux. A Linux expert prefers to use the command line to find processes, memory consumption, etc., but you don't have to
 7 ways to help you check the registration date of Linux users
Aug 24, 2024 am 07:31 AM
7 ways to help you check the registration date of Linux users
Aug 24, 2024 am 07:31 AM
Did you know, how to check the creation date of an account on a Linux system? If you know, what can you do? Did you succeed? If yes, how to do it? Basically Linux systems don't track this information, so what are the alternative ways to get this information? You may ask why am I checking this? Yes, there are situations where you may need to review this information and it will be helpful to you at that time. You can use the following 7 methods to verify. Use /var/log/secure Use aureport tool Use .bash_logout Use chage command Use useradd command Use passwd command Use last command Method 1: Use /var/l
 Centos 7 installation and configuration NTP network time synchronization server
Aug 05, 2024 pm 10:35 PM
Centos 7 installation and configuration NTP network time synchronization server
Aug 05, 2024 pm 10:35 PM
Experimental environment: OS: LinuxCentos7.4x86_641. View the current server time zone & list the time zone and set the time zone (if it is already the correct time zone, please skip it): #timedatectl#timedatectllist-timezones#timedatectlset-timezoneAsia/Shanghai2. Understanding of time zone concepts: GMT, UTC, CST, DSTUTC: The entire earth is divided into twenty-four time zones. Each time zone has its own local time. In international radio communication situations, for the sake of unification, a unified time is used, called Universal Coordinated Time (UTC). :UniversalTim
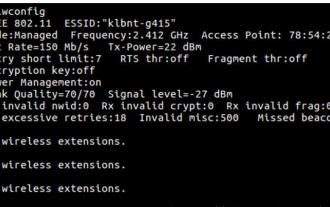 How to connect two Ubuntu hosts to the Internet using one network cable
Aug 07, 2024 pm 01:39 PM
How to connect two Ubuntu hosts to the Internet using one network cable
Aug 07, 2024 pm 01:39 PM
How to use one network cable to connect two ubuntu hosts to the Internet 1. Prepare host A: ubuntu16.04 and host B: ubuntu16.042. Host A has two network cards, one is connected to the external network and the other is connected to host B. Use the iwconfig command to view all network cards on the host. As shown above, the network cards on the author's A host (laptop) are: wlp2s0: This is a wireless network card. enp1s0: Wired network card, the network card connected to host B. The rest has nothing to do with us, no need to care. 3. Configure the static IP of A. Edit the file #vim/etc/network/interfaces to configure a static IP address for interface enp1s0, as shown below (where #==========
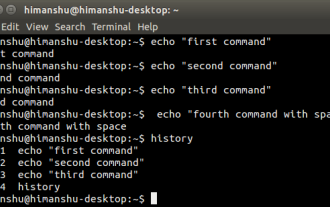 How to hide your Linux command line history
Aug 17, 2024 am 07:34 AM
How to hide your Linux command line history
Aug 17, 2024 am 07:34 AM
If you are a Linux command line user, sometimes you may not want certain commands to be recorded in your command line history. There could be many reasons, for example, you hold a certain position in a company and you have certain privileges that you don't want others to abuse. Or maybe there are some particularly important commands that you don't want to execute by mistake while browsing the history list. However, is there a way to control which commands go into the history list and which don't? Or in other words, can we enable incognito mode like a browser in a Linux terminal? The answer is yes, and depending on the specific goals you want, there are many ways to achieve it. In this article, we’ll discuss some proven methods. Note: All commands appearing in this article have been tested under Ubuntu. different
 Detailed explanation: Shell script variable judgment parameter command
Sep 02, 2024 pm 03:25 PM
Detailed explanation: Shell script variable judgment parameter command
Sep 02, 2024 pm 03:25 PM
The system variable $n is the parameter passed to the script or function. n is a number indicating the number of parameters. For example, the first parameter is $1, and the second parameter is $2$? The exit status of the previous command, or the return value of the function. Returns 0 on success, 1 on failure $#Number of parameters passed to the script or function $* All these parameters are enclosed in double quotes. If a script receives two parameters, $* is equal to $1$2$0The name of the command being executed. For shell scripts, this is the path to the activated command. When $@ is enclosed in double quotes (""), it is slightly different from $*. If a script receives two parameters, $@ is equivalent to $1$2$$the process number of the current shell. For a shell script, this is the process I when it is executing
 Zabbix 3.4 Source code compilation installation
Sep 04, 2024 am 07:32 AM
Zabbix 3.4 Source code compilation installation
Sep 04, 2024 am 07:32 AM
1. Installation environment (Hyper-V virtual machine): $hostnamectlStatichostname:localhost.localdomainIconname:computer-vmChassis:vmMachineID:renwoles1d8743989a40cb81db696400BootID:renwoles272f4aa59935dcdd0d456501Virtualization:microsoftOperatingSystem:CentOS Linux7(Core)CPEOSName:cpe:
 How to install and configure ArangoDB
Aug 07, 2024 pm 06:19 PM
How to install and configure ArangoDB
Aug 07, 2024 pm 06:19 PM
ArangoDB is an open source distributed native multi-model database. It is a NoSQL database with three data models: graph, document and key/value. ArangoDB uses SQL-like query language (AQL) to build high-performance applications. ArangoDB installation ArangoDB supports installation on Windows, Linux, Docker, Mac and other systems. Installation of ArangoDB under Windows You can download the compressed package version or the executable file version under Windows. I prefer to use the compressed package version. After downloading, just select a directory and decompress it directly. untie



