Characteristics and advantages of enumeration types in Golang

Golang is a very popular programming language. It is designed to be simple and efficient, and is known for its concurrency performance. In Golang, although enumeration types are not directly supported like other languages, constants and iota can be used to achieve similar functions. This article will introduce the characteristics and advantages of enumeration types in Golang and provide specific code examples.
1. Characteristics of enumeration types in Golang
In Golang, although there is no such type as enumeration (enum), constants (const) and iota can be used to simulate enumerations. Function. iota is an incrementing counter in the constant group. It will increment by 1 every time a constant declaration is encountered. This allows us to easily define a set of related constants and automatically assign values to them through iota.
2. Advantages of enumeration types in Golang
1. Clarity: Using constants and iota to define enumeration types can make the code clear and understandable without Additional definitions and declarations are required like other languages.
2. Flexibility: When defining an enumeration type, you can add, delete, or adjust the order of constants at any time without worrying about affecting other parts of the code.
3. Safety: Using enumeration types can reduce the possibility of making mistakes, because type checking will be performed at compile time to avoid some potential errors.
3. Code Example
The following is a simple example showing how to use constants and iota to define enumeration types in Golang:
package main
import "fmt"
const (
Monday = iota
Tuesday
Wednesday
Thursday
Friday
Saturday
Sunday
)
func main() {
fmt.Println("Monday:", Monday)
fmt.Println("Tuesday:", Tuesday)
fmt.Println("Wednesday:", Wednesday)
fmt.Println("Thursday:", Thursday)
fmt.Println("Friday:", Friday)
fmt.Println("Saturday:", Saturday)
fmt.Println("Sunday:", Sunday)
}In this example, we define an enumeration type representing the week, and assign an increasing value starting from 0 to each constant through iota. In the main function, we print out the value of each constant, and you can see that they correspond to 0 to 6, representing Monday to Sunday respectively.
Conclusion
Through the above introduction and examples, we have learned how to use constants and iota to simulate the functions of enumeration types in Golang, and demonstrated the characteristics and advantages of enumeration types. This approach is not only concise and clear, but also improves the flexibility and security of the code, allowing us to better manage and use enumerated types. I hope this article is helpful to you, thank you for reading!
The above is the detailed content of Characteristics and advantages of enumeration types in Golang. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to remove comment restrictions on video accounts? What is the word limit for comments on a video account?
Mar 22, 2024 pm 02:11 PM
How to remove comment restrictions on video accounts? What is the word limit for comments on a video account?
Mar 22, 2024 pm 02:11 PM
With the popularity of video accounts on social media, more and more people are beginning to use video accounts to share their daily lives, insights and stories. However, some users may experience comments being restricted, which can leave them confused and dissatisfied. 1. How to remove comment restrictions on video accounts? To lift the restriction on commenting on a video account, you must first ensure that the account has been properly registered and real-name authentication has been completed. Video accounts have requirements for comments. Only accounts that have completed real-name authentication can lift comment restrictions. If there are any abnormalities in the account, these issues need to be resolved before comment restrictions can be lifted. 2. Comply with the community standards of the video account. Video accounts have certain standards for comment content. If the comment involves illegal content, you will be restricted from speaking. To lift comment restrictions, you need to abide by the community of the video account
 What is an MD5 hash value?
Feb 18, 2024 pm 08:50 PM
What is an MD5 hash value?
Feb 18, 2024 pm 08:50 PM
What is the MD5 value? In computer science, MD5 (MessageDigestAlgorithm5) is a commonly used hash function used to digest or encrypt messages. It produces a fixed-length 128-bit binary number, usually represented in 32-bit hexadecimal. The MD5 algorithm was designed by Ronald Rivest in 1991. Although the MD5 algorithm is considered no longer secure in the field of cryptography, it is still widely used in data integrity verification and file verification.
 How to set up a CentOS system to restrict user modifications to system logs
Jul 05, 2023 pm 03:43 PM
How to set up a CentOS system to restrict user modifications to system logs
Jul 05, 2023 pm 03:43 PM
How to set up the CentOS system to restrict users from modifying the system log. In the CentOS system, the system log is a very important source of information. It records the system's operating status, error messages, warnings, etc. In order to protect the stability and security of the system, we should restrict users from modifying system logs. This article will introduce how to set up the CentOS system to restrict the modification permissions of the system log. 1. Create user groups and users. First, we need to create a user group specifically responsible for managing system logs, and a user group for managing system logs.
 How to use JavaScript to drag and zoom images while limiting them to the container?
Oct 20, 2023 pm 04:19 PM
How to use JavaScript to drag and zoom images while limiting them to the container?
Oct 20, 2023 pm 04:19 PM
How does JavaScript implement dragging and zooming of images while limiting them to the container? In web development, we often encounter the need to drag and zoom images. This article will introduce how to use JavaScript to implement dragging and zooming of images and limit operations within the container. 1. Drag the picture To drag the picture, we can use mouse events to track the mouse position and move the picture position accordingly. The following is a sample code: //Get the picture element varimage
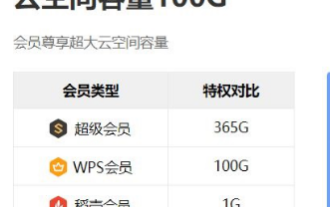 What should I do if the maximum size of documents that WPS members can upload exceeds the limit?
Mar 20, 2024 pm 06:40 PM
What should I do if the maximum size of documents that WPS members can upload exceeds the limit?
Mar 20, 2024 pm 06:40 PM
WPS is an office software that integrates comprehensive operations. You can now download WPS for use, but if you want to have more functions, you need to register as a member. Some people may wonder what is the maximum file size that a WPS member can upload? If you are a WPS member user, you can upload files up to 1G each time, and all files can add up to 365G. There may be some differences in different terminals, but the overall display is basically similar. What should I do if I cannot upload beyond the limit? We will explain it next. 1. When uploading files, such as cloud documents, there is a certain amount of space. If it exceeds the size, it cannot be uploaded. 2. Click on the membership logo, purchase membership according to your needs, and expand the space. 3. Coupons may appear occasionally, so don’t forget to use them.
 Applications and limitations of inline template functions
Apr 28, 2024 pm 02:33 PM
Applications and limitations of inline template functions
Apr 28, 2024 pm 02:33 PM
Inline template functions insert code directly into the call point without generating a separate function object. Applications include code optimization, performance improvement, constant evaluation, and code simplification. But be aware of its limitations, such as longer compilation times, increased code size, reduced debuggability, and limitations across compilation units.
 What are the limitations and considerations for C++ function overloading?
Apr 13, 2024 pm 01:09 PM
What are the limitations and considerations for C++ function overloading?
Apr 13, 2024 pm 01:09 PM
Restrictions on function overloading include: parameter types and orders must be different (when the number of parameters is the same), and default parameters cannot be used to distinguish overloading. In addition, template functions and non-template functions cannot be overloaded, and template functions with different template specifications can be overloaded. It's worth noting that excessive use of function overloading can affect readability and debugging, the compiler searches from the most specific to the least specific function to resolve conflicts.
 Advantages and limitations of MyBatis reverse engineering
Feb 22, 2024 pm 07:27 PM
Advantages and limitations of MyBatis reverse engineering
Feb 22, 2024 pm 07:27 PM
MyBatis is a popular persistence framework that provides reverse engineering functions, which allows developers to automatically generate entity classes, Mapper interfaces, and XML mapping files based on the table structure in the database. Reverse engineering is an important feature of MyBatis, which can greatly reduce the developer's workload and improve the maintainability of the code. However, reverse engineering also has some limitations. This article will introduce the advantages and limitations of MyBatis reverse engineering and illustrate it with specific code examples. First, let's






