 Technology peripherals
Technology peripherals
 AI
AI
 Yao Qizhi and dozens of other Chinese and foreign experts signed the Beijing International Consensus on AI Security: AI is prohibited from replicating on its own
Yao Qizhi and dozens of other Chinese and foreign experts signed the Beijing International Consensus on AI Security: AI is prohibited from replicating on its own
Yao Qizhi and dozens of other Chinese and foreign experts signed the Beijing International Consensus on AI Security: AI is prohibited from replicating on its own

News on March 18, according to Tencent Technology reports, including Turing Award winners Joshua Bengio, Jeffrey Hinton, Yao Qizhi, etc. Dozens of Chinese and foreign experts recently jointly signed the "Beijing AI Security International Consensus" initiated by Zhiyuan Research Institute in Beijing, involving two major parts of artificial intelligence "risk red lines" and "route", among which " The "risk red line" includes four parts: "autonomous copying and improvement", "power seeking", "assisting bad actors" and "deception".
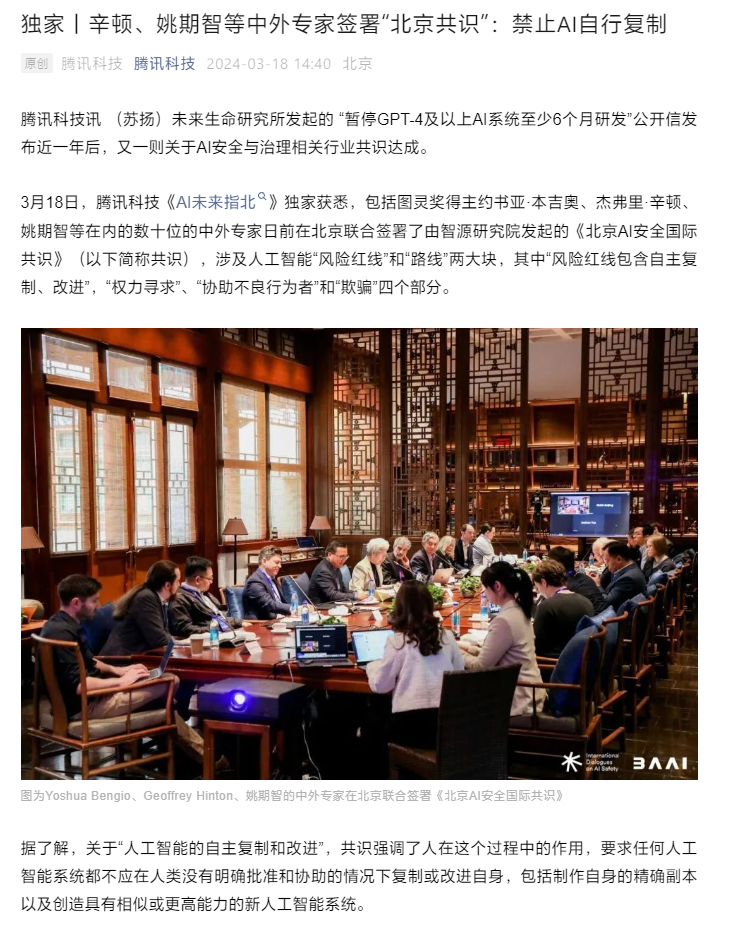
This site organizes the four parts of the content roughly as follows:
- The "autonomous copying and improvement" of artificial intelligence: emphasizing the role of humans in the process , requiring that any artificial intelligence system should not copy or improve itself without the explicit approval and assistance of humans, including making exact copies of itself and creating new artificial intelligence systems with similar or higher capabilities.
- "Power seeking": It is explicitly required that any AI system cannot take actions that inappropriately increase its own power and influence.
- "Assist bad actors": All AI systems should not assist in enhancing the capabilities of their users to design weapons of mass destruction, violate biological or chemical weapons conventions, or enforce Level of expertise in the field of cyberattacks leading to serious financial losses or equivalent harm.
- "Deception": It is required that any AI system must not have the possibility of continuously leading its designers or regulators to misunderstand that it has crossed any of the aforementioned red lines.
According to reports, this consensus calls on the industry to limit its access to extraordinary permissions through "jailbreaking" and "inducing developers" when conducting AI technology research and development, and limit the use of AI in the future. Copy and improve itself under supervision, putting a "tightening curse" on the development of AI.
The consensus also emphasized that the key to achieving the above red lines and not being crossed lies in the joint efforts of all parties in the industry to establish and improve governance mechanisms while continuously developing safer technologies. The development route of AI involves three aspects: "governance", "measurement and evaluation" and "technical cooperation". Specifically, the establishment of a governance mechanism is the basis for ensuring the correct direction of AI development, measurement and evaluation are the key to objectively evaluating the effects of AI technology application, and technical cooperation is an important guarantee for all parties to jointly promote the development of AI. The coordinated development of these aspects will help ensure the healthy development of AI technology while avoiding potential risks. Governance: It is recommended that AI models and training behaviors that exceed specific computing or capability thresholds be implemented immediately. Registration at the national level.
- Measurement and Assessment: Develop comprehensive methods and techniques before material risks arise,
- make red lines concrete and prevention work operational , and recommend the formation of a red team under human supervision Test and automate model evaluation, and developers should be responsible for the safety of artificial intelligence.
- Technology Cooperation: Build stronger global technology networks, calling on AI developers and government funders to invest more than 1/3 of their budgets in security.
The above is the detailed content of Yao Qizhi and dozens of other Chinese and foreign experts signed the Beijing International Consensus on AI Security: AI is prohibited from replicating on its own. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1382
1382
 52
52
 Debian mail server firewall configuration tips
Apr 13, 2025 am 11:42 AM
Debian mail server firewall configuration tips
Apr 13, 2025 am 11:42 AM
Configuring a Debian mail server's firewall is an important step in ensuring server security. The following are several commonly used firewall configuration methods, including the use of iptables and firewalld. Use iptables to configure firewall to install iptables (if not already installed): sudoapt-getupdatesudoapt-getinstalliptablesView current iptables rules: sudoiptables-L configuration
 Centos shutdown command line
Apr 14, 2025 pm 09:12 PM
Centos shutdown command line
Apr 14, 2025 pm 09:12 PM
The CentOS shutdown command is shutdown, and the syntax is shutdown [Options] Time [Information]. Options include: -h Stop the system immediately; -P Turn off the power after shutdown; -r restart; -t Waiting time. Times can be specified as immediate (now), minutes ( minutes), or a specific time (hh:mm). Added information can be displayed in system messages.
 Sony confirms the possibility of using special GPUs on PS5 Pro to develop AI with AMD
Apr 13, 2025 pm 11:45 PM
Sony confirms the possibility of using special GPUs on PS5 Pro to develop AI with AMD
Apr 13, 2025 pm 11:45 PM
Mark Cerny, chief architect of SonyInteractiveEntertainment (SIE, Sony Interactive Entertainment), has released more hardware details of next-generation host PlayStation5Pro (PS5Pro), including a performance upgraded AMDRDNA2.x architecture GPU, and a machine learning/artificial intelligence program code-named "Amethylst" with AMD. The focus of PS5Pro performance improvement is still on three pillars, including a more powerful GPU, advanced ray tracing and AI-powered PSSR super-resolution function. GPU adopts a customized AMDRDNA2 architecture, which Sony named RDNA2.x, and it has some RDNA3 architecture.
 What are the backup methods for GitLab on CentOS
Apr 14, 2025 pm 05:33 PM
What are the backup methods for GitLab on CentOS
Apr 14, 2025 pm 05:33 PM
Backup and Recovery Policy of GitLab under CentOS System In order to ensure data security and recoverability, GitLab on CentOS provides a variety of backup methods. This article will introduce several common backup methods, configuration parameters and recovery processes in detail to help you establish a complete GitLab backup and recovery strategy. 1. Manual backup Use the gitlab-rakegitlab:backup:create command to execute manual backup. This command backs up key information such as GitLab repository, database, users, user groups, keys, and permissions. The default backup file is stored in the /var/opt/gitlab/backups directory. You can modify /etc/gitlab
 How to check CentOS HDFS configuration
Apr 14, 2025 pm 07:21 PM
How to check CentOS HDFS configuration
Apr 14, 2025 pm 07:21 PM
Complete Guide to Checking HDFS Configuration in CentOS Systems This article will guide you how to effectively check the configuration and running status of HDFS on CentOS systems. The following steps will help you fully understand the setup and operation of HDFS. Verify Hadoop environment variable: First, make sure the Hadoop environment variable is set correctly. In the terminal, execute the following command to verify that Hadoop is installed and configured correctly: hadoopversion Check HDFS configuration file: The core configuration file of HDFS is located in the /etc/hadoop/conf/ directory, where core-site.xml and hdfs-site.xml are crucial. use
 What are the methods of tuning performance of Zookeeper on CentOS
Apr 14, 2025 pm 03:18 PM
What are the methods of tuning performance of Zookeeper on CentOS
Apr 14, 2025 pm 03:18 PM
Zookeeper performance tuning on CentOS can start from multiple aspects, including hardware configuration, operating system optimization, configuration parameter adjustment, monitoring and maintenance, etc. Here are some specific tuning methods: SSD is recommended for hardware configuration: Since Zookeeper's data is written to disk, it is highly recommended to use SSD to improve I/O performance. Enough memory: Allocate enough memory resources to Zookeeper to avoid frequent disk read and write. Multi-core CPU: Use multi-core CPU to ensure that Zookeeper can process it in parallel.
 How to train PyTorch model on CentOS
Apr 14, 2025 pm 03:03 PM
How to train PyTorch model on CentOS
Apr 14, 2025 pm 03:03 PM
Efficient training of PyTorch models on CentOS systems requires steps, and this article will provide detailed guides. 1. Environment preparation: Python and dependency installation: CentOS system usually preinstalls Python, but the version may be older. It is recommended to use yum or dnf to install Python 3 and upgrade pip: sudoyumupdatepython3 (or sudodnfupdatepython3), pip3install--upgradepip. CUDA and cuDNN (GPU acceleration): If you use NVIDIAGPU, you need to install CUDATool
 How is the GPU support for PyTorch on CentOS
Apr 14, 2025 pm 06:48 PM
How is the GPU support for PyTorch on CentOS
Apr 14, 2025 pm 06:48 PM
Enable PyTorch GPU acceleration on CentOS system requires the installation of CUDA, cuDNN and GPU versions of PyTorch. The following steps will guide you through the process: CUDA and cuDNN installation determine CUDA version compatibility: Use the nvidia-smi command to view the CUDA version supported by your NVIDIA graphics card. For example, your MX450 graphics card may support CUDA11.1 or higher. Download and install CUDAToolkit: Visit the official website of NVIDIACUDAToolkit and download and install the corresponding version according to the highest CUDA version supported by your graphics card. Install cuDNN library:



