Review: MOBOX Hacked Analysis
Background
On March 14, 2024, according to the early warning of the Slow Mist MistEye security monitoring system, the decentralized lending protocol MOBOX on the Optimism chain was attacked, causing losses of approximately $750,000. The SlowMist security team analyzed the attack incident and shared the results as follows:
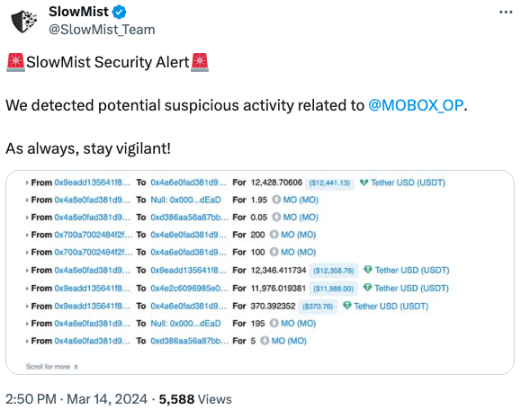
(https://twitter.com/SlowMist_Team /status/1768167772230713410)
##Related information
Attacker address:
0x4e2c6096985e0b2825d06c16f1c8cdc559c1d6f8
0x96f004c81d2c7b907f92c45922d38ab870a53945
Attacked contract address:
0xae7b6514af26bcb2332fea53b8dd57bc13a7838e
Attack transaction:
##0x4ec3061724ca9f0b8d400866dd83b92647ad8c943a1c0ae9ae6c9bd1ef789417There are two main core points of this attack. One is that the attacker exploits the borrow() function vulnerability in the contract, and each time it is called The function will trigger the distribution of rewards to the recommender's address. Since the reward calculation is based on the number of transferred tokens, the attacker can increase the amount of the next borrowing by transferring the reward to the referrer back to the attacked contract again. The second is that each time the borrow() function is called, a part of the MO tokens in the pool will be burned, so the price of MO tokens is continuously raised. In the end, the attacker can make profits by continuously borrowing and superimposing rewards. We can find that the entire attack process mainly involves calling the vulnerable borrow() function in a loop, and then immediately calling redeem() performs a redemption and then transfers the tokens allocated to the referrer back to the attack contract. Following up the analysis of the borrow() function, we can find that every time this function is called, part of the MO tokens in the pool will be burned. However, the amount of USDT loaned out is calculated based on the price of MO tokens in the pool. Since the price of MO tokens is burned due to The continuous increase eventually led to the attacker using a small amount of MO tokens to lend out a large amount of USDT tokens. In addition, each time a loan is borrowed, a referrer address will be given a dividend reward, and this function is based on the number of MO tokens passed in. computational. However, since the recommender address is also controlled by the attacker (0x96f004c81d2c7b907f92c45922d38ab870a53945), the attacker can reward this part after completing the loan operation. Transfer it back to superimpose the next borrowing amount and dividend rewards. After the above cycle operation, the attacker increased the price of MO tokens, and finally could use a very small number of MO tokens to lend out large amounts of money in the contract. amount of USDT, and directly exchange all USDT in the unbalanced pool to make a profit. The core of this attack is that the attacker uses the borrow() function to burn the pool The mechanism of partial tokens in the middle continuously borrows assets to increase the price of tokens in the pool and obtains referrer rewards, and then transfers the tokens back and borrows them again, thereby continuously adding rewards and manipulating prices. The SlowMist security team recommends that project parties add lock-up time limits to similar functions and consider multiple factors when designing the price model of lending to avoid similar incidents from happening again. Attack Core
Transaction Analysis
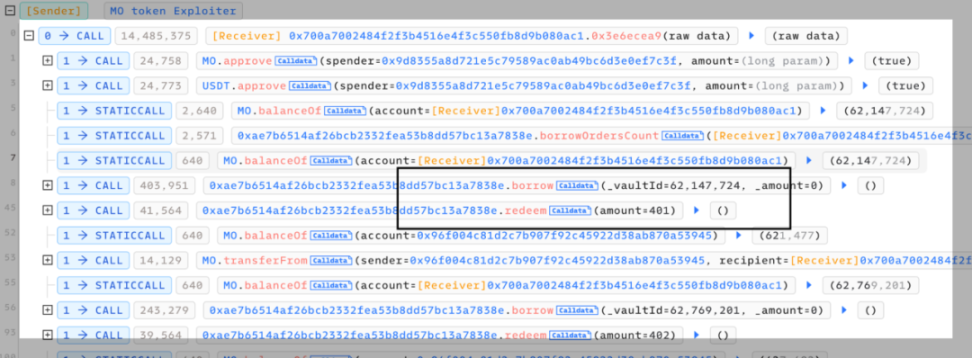
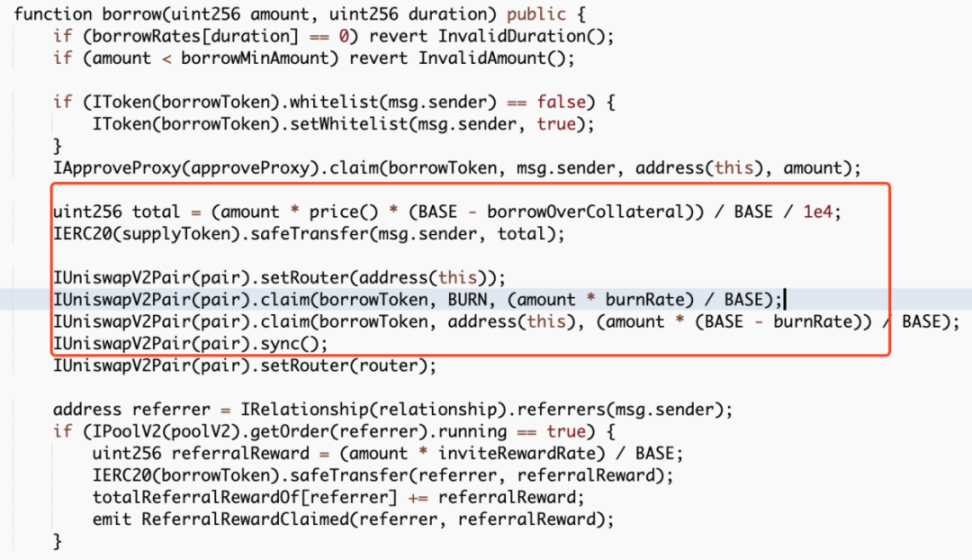
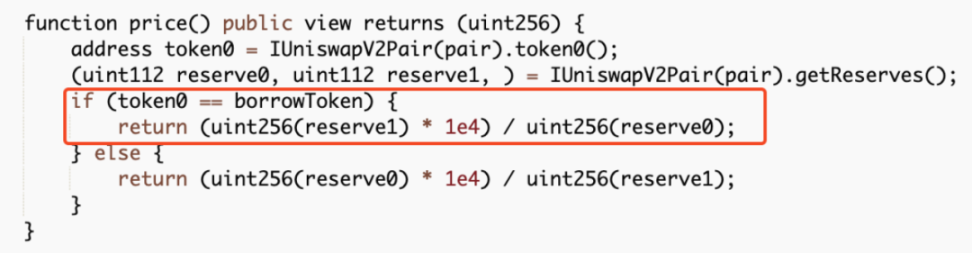
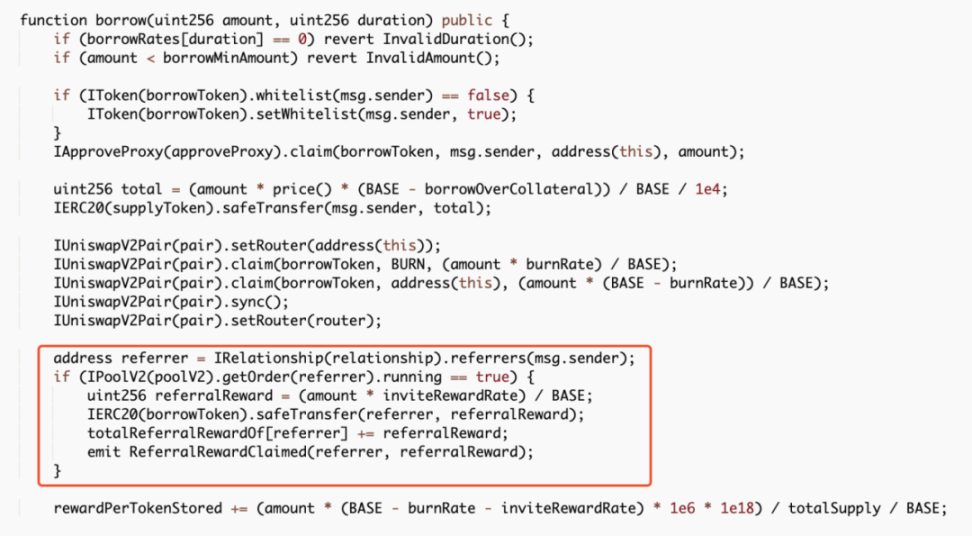
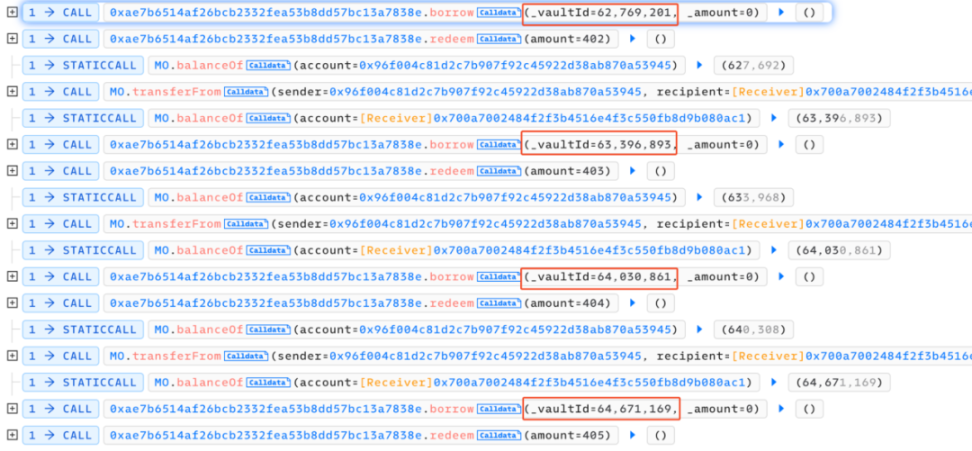
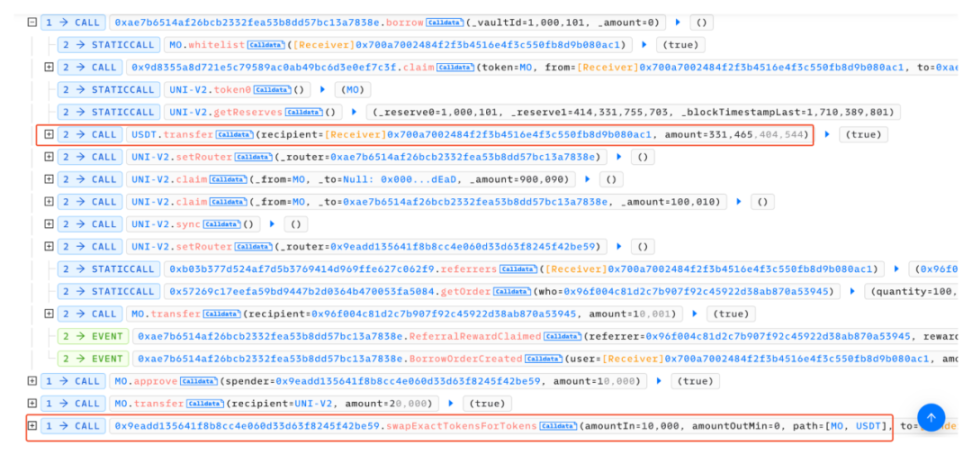
Summary
The above is the detailed content of Review: MOBOX Hacked Analysis. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1382
1382
 52
52
 What is Ouyi for? What is Ouyi
Apr 01, 2025 pm 03:18 PM
What is Ouyi for? What is Ouyi
Apr 01, 2025 pm 03:18 PM
OKX is a global digital asset trading platform. Its main functions include: 1. Buying and selling digital assets (spot trading), 2. Trading between digital assets, 3. Providing market conditions and data, 4. Providing diversified trading products (such as derivatives), 5. Providing asset value-added services, 6. Convenient asset management.
 How to roll positions in digital currency? What are the digital currency rolling platforms?
Mar 31, 2025 pm 07:36 PM
How to roll positions in digital currency? What are the digital currency rolling platforms?
Mar 31, 2025 pm 07:36 PM
Digital currency rolling positions is an investment strategy that uses lending to amplify trading leverage to increase returns. This article explains the digital currency rolling process in detail, including key steps such as selecting trading platforms that support rolling (such as Binance, OKEx, gate.io, Huobi, Bybit, etc.), opening a leverage account, setting a leverage multiple, borrowing funds for trading, and real-time monitoring of the market and adjusting positions or adding margin to avoid liquidation. However, rolling position trading is extremely risky, and investors need to operate with caution and formulate complete risk management strategies. To learn more about digital currency rolling tips, please continue reading.
 How to operate simulated trading on exchanges? Detailed tutorial on simulated trading on Ouyi Exchange
Mar 05, 2025 am 11:12 AM
How to operate simulated trading on exchanges? Detailed tutorial on simulated trading on Ouyi Exchange
Mar 05, 2025 am 11:12 AM
Novice usually needs to have a trading knowledge base before entering the cryptocurrency market, especially when trading contracts, and even more so. In order to make novice novice get started faster, exchanges such as Ouyi and Binance have also implemented simulated trading to help investors enter the market, learn trading knowledge and increase their experience. But there are still many people who don’t even know how to operate simulated trading on exchanges? This operation is relatively simple. Generally speaking, novices can practice the operation on simulated trading, and then make formal transactions after getting familiar with it. The editor will tell you in detail below. How to operate simulated trading on exchanges? The simulation trading operation on the exchange is relatively simple. Currently, exchanges such as Ouyi and Binance support them. The following is a detailed tutorial on conducting simulation trading on the Ouyi Exchange: 1.
 How to register and download the latest app on Bitget official website
Mar 05, 2025 am 07:54 AM
How to register and download the latest app on Bitget official website
Mar 05, 2025 am 07:54 AM
This guide provides detailed download and installation steps for the official Bitget Exchange app, suitable for Android and iOS systems. The guide integrates information from multiple authoritative sources, including the official website, the App Store, and Google Play, and emphasizes considerations during download and account management. Users can download the app from official channels, including app store, official website APK download and official website jump, and complete registration, identity verification and security settings. In addition, the guide covers frequently asked questions and considerations, such as
 gateio Sesame Open Door Exchange official website login the latest entrance
Mar 05, 2025 pm 08:12 PM
gateio Sesame Open Door Exchange official website login the latest entrance
Mar 05, 2025 pm 08:12 PM
Gate.io is a crypto asset exchange that provides a wide range of services including registration, account verification, deposits, transactions and withdrawals. Users can start using Gate.io by creating an account, completing verification, selecting a deposit method, and then sending funds to the generated address. The platform provides a variety of transaction pairs, order types and trading tools to facilitate users to conduct transactions. Users can also withdraw money from Gate.io by selecting a withdrawal method, generating a withdrawal address, entering the withdrawal amount, and completing security verification.
 Will Ethereum be lonely after upgrading
Mar 18, 2025 pm 04:00 PM
Will Ethereum be lonely after upgrading
Mar 18, 2025 pm 04:00 PM
Ethereum has recently completed a series of important upgrades aimed at improving scalability, security and sustainability, which has sparked discussions on its future direction. Upgrading brings opportunities such as scalability improvement, energy efficiency improvement, security enhancement and ecosystem prosperity, but it also faces challenges such as centralized risks, escalation complexity, intensified competition and market fluctuations. Mainstream exchanges are actively responding to escalation and providing support and risk warnings. The future of Ethereum depends on whether it can effectively solve these challenges, continue to innovate and attract developers and users. Although facing competitive pressure, its strong technical foundation and active community make it still hopeful to maintain its leading position. Investors need to analyze rationally and invest cautiously.
 Is USDT price stable? Will it fluctuate? Understand the price fluctuations of Tether
Mar 20, 2025 pm 06:09 PM
Is USDT price stable? Will it fluctuate? Understand the price fluctuations of Tether
Mar 20, 2025 pm 06:09 PM
As one of the most popular stablecoins on the market, USDT (Tether) has always attracted much attention. Although USDT is intended to be 1:1 linked to the US dollar, in actual transactions, its prices will fluctuate due to factors such as market supply and demand, investor sentiment, regulatory policies, etc., resulting in slight premiums or discounts, panic selling, etc. This article will deeply analyze the causes of USDT price fluctuations, including market supply and demand relationships, TEDA reserves, regulatory policies, market sentiment, and trading platform credibility, and discuss how to avoid risks and help investors better understand and use USDT.
 Which exchanges publish pi news
Mar 28, 2025 pm 03:33 PM
Which exchanges publish pi news
Mar 28, 2025 pm 03:33 PM
Pi Network has not yet officially launched trading on mainstream exchanges. As of 2024, Pi is still in the stage of closing the main network, and only some small and medium-sized exchanges provide IOU transactions. The official does not authorize any transactions. It is recommended to mine through official channels and wait for the main network to open and trade on compliant exchanges.



