MySQL安全性指南 (1)(转)_MySQL
MySQL安全性指南
作 者: 晏子
作为一个MySQL的系统管理员,你有责任维护你的MySQL数据库系统的数据安全性和完整性。本文主要主要介绍如何建立一个安全的MySQL系统,从系统内部和外部网络两个角度,为你提供一个指南。
本文主要考虑下列安全性有关的问题:
为什么安全性很重要,你应该防范那些攻击?
服务器面临的风险(内部安全性),如何处理?
连接服务器的客户端风险(外部安全性),如何处理?
MySQL管理员有责任保证数据库内容的安全性,使得这些数据记录只能被那些正确授权的用户访问,这涉及到数据库系统的内部安全性和外部安全性。
内部安全性关心的是文件系统级的问题,即,防止MySQL数据目录(DATADIR)被在服务器主机有账号的人(合法或窃取的)进行攻击。如果数据目录内容的权限过分授予,使得每个人均能简单地替代对应于那些数据库表的文件,那么确保控制客户通过网络访问的授权表设置正确,对此毫无意义。
外部安全性关心的是从外部通过网络连接服务器的客户的问题,即,保护MySQL服务器免受来自通过网络对服务器的连接的攻击。你必须设置MySQL授权表(grant table),使得他们不允许访问服务器管理的数据库内容,除非提供有效的用户名和口令。
下面就详细介绍如何设置文件系统和授权表mysql,实现MySQL的两级安全性。
一、内部安全性-保证数据目录访问的安全
MySQL服务器通过在MySQL数据库中的授权表提供了一个灵活的权限系统。你可以设置这些表的内容,允许或拒绝客户对数据库的访问,这提供了你防止未授权的网络访问对你数据库攻击的安全手段,然而如果主机上其他用户能直接访问数据目录内容,建立对通过网络访问数据库的良好安全性对你毫无帮助,除非你知道你是登录MySQL服务器运行主机的唯一用户,否则你需要关心在这台机器上的其他用户获得对数据目录的访问的可能性。
以下是你应该保护的内容:
数据库文件。很明显,你要维护服务器管理的数据库的私用性。数据库拥有者通常并且应该考虑数据库内容的安全性,即使他们不想,也应该考虑时数据库内容公开化,而不是通过糟糕的数据目录的安全性来暴露这些内容。
日志文件。一般和更新日志必须保证安全,因为他们包含查询文本。对日志文件有访问权限的任何人可以监视数据库进行过的操作。
更要重点考虑的日志文件安全性是诸如GRANT和SET PASSWORD等的查询也被记载了,一般和更新日志包含有敏感查询的文本,包括口令(MySQL使用口令加密,但它在已经完成设置后才运用于以后的连接建立。设置一个口令的过程设计象GRANT或SET PASSWORD等查询,并且这些查询以普通文本形式记载在日志文件中)。如果一个攻击者犹如日文件的读权限,只需在日志文件上运行grep寻找诸如GRANT和PASSWORD等词来发现敏感信息。
显然,你不想让服务器主机上的其他用户有数据库目录文件的写权限,因为他们可以重写你的状态文件或数据库表文件,但是读权限也很危险。如果一个数据库表文件能被读取,偷取文件并得到MySQL本身,以普通文本显示表的内容也很麻烦,为什么?因为你要做下列事情:
在服务器主机上安装你自己“特制”的MySQL服务器,但是有一个不同于官方服务器版本的端口、套接字和数据目录。
运行mysql_install_db初始化你的数据目录,这赋予你作为MySQL root用户访问你的服务器的权限,所以你有对服务器访问机制的完全控制,它也建立一个test数据库。
将对应于你想偷取得表文件拷贝到你服务器的数据库目录下的test目录。
启动你的服务器。你可以随意访问数据库表,SHOW TABLES FROM test显示你有一个偷来的表的拷贝,SELECT *显示它们任何一个的全部内容。
如果你确实很恶毒,将权限公开给你服务器的任何匿名用户,这样任何人能从任何地方连接服务器访问你的test数据库。你现在将偷来的数据库表公布于众了。
在考虑一下,从相反的角度,你想让别人对你这样吗?当然不!你可以通过在数据库录下执行ls -l命令确定你的数据库是否包含不安全的文件和目录。查找有“组”和“其他用户”权限设置的文件和目录。下面是一个不安全数据目录的一部分列出:
% ls -l
total 10148
drwxrwxr-x 11 mysqladm wheel 1024 May 8 12:20 .
drwxr-xr-x 22 root wheel 512 May 8 13:31 ..
drwx------ 2 mysqladm mysqlgrp 512 Apr 16 15:57 menagerie
drwxrwxr-x 2 mysqladm wheel 512 Jan 25 20:40 mysql
drwxrwxr-x 7 mysqladm wheel 512 Aug 31 1998 sql-bench
drwxrwxr-x 2 mysqladm wheel 1536 May 6 06:11 test
drwx------ 2 mysqladm mysqlgrp 1024 May 8 18:43 tmp
....
正如你看到的,有些数据库有正确的权限,而其他不是。本例的情形是经过一段时间后的结果。较少限制的权限由在权限设置方面比更新版本更不严格的较早版本服务器设置的(注意更具限制的目录menageria和tmp都有较近日期)。MySQL当前版本确保这些文件只能由运行服务器的用户读取。
让我们来修正这些权限,使得只用服务器用户可访问它们。你的主要保护工具来自于由UNIX文件系统本身提供的设置文件和目录属主和模式的工具。下面是我们要做的:
进入该目录
% cd DATADIR
设置所有在数据目录下的文件属主为由用于运行服务器的账号拥有(你必须以root执行这步)。在本文使用mysqladm和mysqlgrp作为该账号的用户名和组名。你可以使用下列命令之一改变属主:
# chown mysqladm.mysqlgrp .
# find . -follow -type d -print | xargs chown mysqladm.mysqlgrp
设置你的数据目录和数据库目录的模式使得他们只能由mysqladm读取,这阻止其他用户访问你数据库目录的内容。你可以用下列命令之一以root或mysqladm身份运行。
% chmod -R go-rwx .
% find . -follow -type d -print | xargs chmod go-rwx
数据目录内容的属主和模式为mysqladm设置。现在你应该保证你总是以mysqladm用户运行服务器,因为现在这是唯一由访问数据库目录权限的用户(除root)。
在完成这些设置后,你最终应该得到下面的数据目录权限:
% ls -l
total 10148
drwxrwx--- 11 mysqladm mysqlgrp 1024 May 8 12:20 .
drwxr-xr-x 22 root wheel 512 May 8 13:31 ..
drwx------ 2 mysqladm mysqlgrp 512 Apr 16 15:57 menagerie
drwx------ 2 mysqladm mysqlgrp 512 Jan 25 20:40 mysql
drwx------ 7 mysqladm mysqlgrp 512 Aug 31 1998 sql-bench
drwx------ 2 mysqladm mysqlgrp 1536 May 6 06:11 test
drwx------ 2 mysqladm mysqlgrp 1024 May 8 18:43 tmp

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
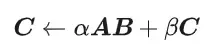 CUDA's universal matrix multiplication: from entry to proficiency!
Mar 25, 2024 pm 12:30 PM
CUDA's universal matrix multiplication: from entry to proficiency!
Mar 25, 2024 pm 12:30 PM
General Matrix Multiplication (GEMM) is a vital part of many applications and algorithms, and is also one of the important indicators for evaluating computer hardware performance. In-depth research and optimization of the implementation of GEMM can help us better understand high-performance computing and the relationship between software and hardware systems. In computer science, effective optimization of GEMM can increase computing speed and save resources, which is crucial to improving the overall performance of a computer system. An in-depth understanding of the working principle and optimization method of GEMM will help us better utilize the potential of modern computing hardware and provide more efficient solutions for various complex computing tasks. By optimizing the performance of GEMM
 Huawei's Qiankun ADS3.0 intelligent driving system will be launched in August and will be launched on Xiangjie S9 for the first time
Jul 30, 2024 pm 02:17 PM
Huawei's Qiankun ADS3.0 intelligent driving system will be launched in August and will be launched on Xiangjie S9 for the first time
Jul 30, 2024 pm 02:17 PM
On July 29, at the roll-off ceremony of AITO Wenjie's 400,000th new car, Yu Chengdong, Huawei's Managing Director, Chairman of Terminal BG, and Chairman of Smart Car Solutions BU, attended and delivered a speech and announced that Wenjie series models will be launched this year In August, Huawei Qiankun ADS 3.0 version was launched, and it is planned to successively push upgrades from August to September. The Xiangjie S9, which will be released on August 6, will debut Huawei’s ADS3.0 intelligent driving system. With the assistance of lidar, Huawei Qiankun ADS3.0 version will greatly improve its intelligent driving capabilities, have end-to-end integrated capabilities, and adopt a new end-to-end architecture of GOD (general obstacle identification)/PDP (predictive decision-making and control) , providing the NCA function of smart driving from parking space to parking space, and upgrading CAS3.0
 Which version of Apple 16 system is the best?
Mar 08, 2024 pm 05:16 PM
Which version of Apple 16 system is the best?
Mar 08, 2024 pm 05:16 PM
The best version of the Apple 16 system is iOS16.1.4. The best version of the iOS16 system may vary from person to person. The additions and improvements in daily use experience have also been praised by many users. Which version of the Apple 16 system is the best? Answer: iOS16.1.4 The best version of the iOS 16 system may vary from person to person. According to public information, iOS16, launched in 2022, is considered a very stable and performant version, and users are quite satisfied with its overall experience. In addition, the addition of new features and improvements in daily use experience in iOS16 have also been well received by many users. Especially in terms of updated battery life, signal performance and heating control, user feedback has been relatively positive. However, considering iPhone14
 Security challenges in Golang development: How to avoid being exploited for virus creation?
Mar 19, 2024 pm 12:39 PM
Security challenges in Golang development: How to avoid being exploited for virus creation?
Mar 19, 2024 pm 12:39 PM
Security challenges in Golang development: How to avoid being exploited for virus creation? With the wide application of Golang in the field of programming, more and more developers choose to use Golang to develop various types of applications. However, like other programming languages, there are security challenges in Golang development. In particular, Golang's power and flexibility also make it a potential virus creation tool. This article will delve into security issues in Golang development and provide some methods to avoid G
 Always new! Huawei Mate60 series upgrades to HarmonyOS 4.2: AI cloud enhancement, Xiaoyi Dialect is so easy to use
Jun 02, 2024 pm 02:58 PM
Always new! Huawei Mate60 series upgrades to HarmonyOS 4.2: AI cloud enhancement, Xiaoyi Dialect is so easy to use
Jun 02, 2024 pm 02:58 PM
On April 11, Huawei officially announced the HarmonyOS 4.2 100-machine upgrade plan for the first time. This time, more than 180 devices will participate in the upgrade, covering mobile phones, tablets, watches, headphones, smart screens and other devices. In the past month, with the steady progress of the HarmonyOS4.2 100-machine upgrade plan, many popular models including Huawei Pocket2, Huawei MateX5 series, nova12 series, Huawei Pura series, etc. have also started to upgrade and adapt, which means that there will be More Huawei model users can enjoy the common and often new experience brought by HarmonyOS. Judging from user feedback, the experience of Huawei Mate60 series models has improved in all aspects after upgrading HarmonyOS4.2. Especially Huawei M
 Differences and similarities of cmd commands in Linux and Windows systems
Mar 15, 2024 am 08:12 AM
Differences and similarities of cmd commands in Linux and Windows systems
Mar 15, 2024 am 08:12 AM
Linux and Windows are two common operating systems, representing the open source Linux system and the commercial Windows system respectively. In both operating systems, there is a command line interface for users to interact with the operating system. In Linux systems, users use the Shell command line, while in Windows systems, users use the cmd command line. The Shell command line in Linux system is a very powerful tool that can complete almost all system management tasks.
 Detailed explanation of how to modify system date in Oracle database
Mar 09, 2024 am 10:21 AM
Detailed explanation of how to modify system date in Oracle database
Mar 09, 2024 am 10:21 AM
Detailed explanation of the method of modifying the system date in the Oracle database. In the Oracle database, the method of modifying the system date mainly involves modifying the NLS_DATE_FORMAT parameter and using the SYSDATE function. This article will introduce these two methods and their specific code examples in detail to help readers better understand and master the operation of modifying the system date in the Oracle database. 1. Modify NLS_DATE_FORMAT parameter method NLS_DATE_FORMAT is Oracle data
 What is the relationship between memory management techniques and security in Java functions?
May 02, 2024 pm 01:06 PM
What is the relationship between memory management techniques and security in Java functions?
May 02, 2024 pm 01:06 PM
Memory management in Java involves automatic memory management, using garbage collection and reference counting to allocate, use and reclaim memory. Effective memory management is crucial for security because it prevents buffer overflows, wild pointers, and memory leaks, thereby improving the safety of your program. For example, by properly releasing objects that are no longer needed, you can avoid memory leaks, thereby improving program performance and preventing crashes.






