Mysql权限系统工作原理_MySQL
MySQL权限系统保证所有的用户可以严格地做他们假定被允许做的事情。当你连接一个MySQL服务器时, 你的身份由你从那连接的主机和你指定的用户名来决定,系统根据你的身份和你想做什么来授予权限。
MySQL在认定身份中考虑你的主机名和用户名字,是因为有很小的原因假定一个给定的用户在因特网上属于同一个人。例如,用户从whitehouse.gov连接的bill不必和从mosoft.com连接bill是同一个人。 MySQL通过允许你区分在不同的主机上碰巧有同样名字用户来处理它:你可以对从whitehouse.gov连接授与bill一个权限集,而为从microsoft.com的连接授予一个不同的权限集。
MySQL存取控制包含2个阶段:
阶段1:服务器检查你是否允许连接。
阶段2:假定你能连接,服务器检查你发出的每个请求。看你是否有足够的权限实施它。例如,如果你从数据库中一个表精选(select)行或从数据库抛弃一个表,服务器确定你对表有select权限或对数据库有drop权限。
服务器在存取控制的两个阶段使用在mysql的数据库中的user、db和host表,在这些授权表中字段如下:
表名称 user db host
范围字段 Host Host Host
User Db Db
Password User
权限字段 Select_priv Select_priv Select_priv
Insert_priv Insert_priv Insert_priv
Update_priv Update_priv Update_priv
Delete_priv Delete_priv Delete_priv
Index_priv Index_priv Index_priv
Alter_priv Alter_priv Alter_priv
Create_priv Create_priv Create_priv
Drop_priv Drop_priv Drop_priv
Grant_priv Grant_priv Grant_priv
Reload_priv
Shutdown_priv
Process_priv
File_priv
对存取控制的第二阶段(请求证实),如果请求涉及表,服务器可以另外参考tables_priv和columns_priv表。这些表的字段如下:
表名称 tables_priv columns_priv
范围字段 Host Host
Db Db
User User
Table_name Table_name
Column_name
权限字段 Table_priv Column_priv
Column_priv
其他字段 Timestamp Timestamp
Grantor
每个授权表包含范围字段和权限字段。
范围字段决定表中每个条目的范围,即,条目适用的上下文。例如, 一个user表条目的Host和User值为''thomas.loc.gov''和''bob''将被用于证实来自主机thomas.loc.gov的bob对服务器的连接。同样,一个db表条目的Host、User和Db字段的值是''thomas.loc.gov''、''bob''和''reports''将用在bob从主机联接thomas.loc.gov存取reports数据库的时候。 tables_priv和columns_priv表包含范围字段,指出每个条目适用的表或表/列的组合。
对于检查存取的用途,比较Host值是忽略大小写的。User、Password、Db和Table_name值是区分大小写的。Column_name值在MySQL3.22.12或以后版本是忽略大小写的。

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 How to solve the problem that Windows 11 prompts you to enter the administrator username and password to continue?
Apr 11, 2024 am 09:10 AM
How to solve the problem that Windows 11 prompts you to enter the administrator username and password to continue?
Apr 11, 2024 am 09:10 AM
When using Win11 system, sometimes you will encounter a prompt that requires you to enter the administrator username and password. This article will discuss how to deal with this situation. Method 1: 1. Click [Windows Logo], then press [Shift+Restart] to enter safe mode; or enter safe mode this way: click the Start menu and select Settings. Select "Update and Security"; select "Restart Now" in "Recovery"; after restarting and entering the options, select - Troubleshoot - Advanced Options - Startup Settings -&mdash
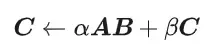 CUDA's universal matrix multiplication: from entry to proficiency!
Mar 25, 2024 pm 12:30 PM
CUDA's universal matrix multiplication: from entry to proficiency!
Mar 25, 2024 pm 12:30 PM
General Matrix Multiplication (GEMM) is a vital part of many applications and algorithms, and is also one of the important indicators for evaluating computer hardware performance. In-depth research and optimization of the implementation of GEMM can help us better understand high-performance computing and the relationship between software and hardware systems. In computer science, effective optimization of GEMM can increase computing speed and save resources, which is crucial to improving the overall performance of a computer system. An in-depth understanding of the working principle and optimization method of GEMM will help us better utilize the potential of modern computing hardware and provide more efficient solutions for various complex computing tasks. By optimizing the performance of GEMM
 Huawei's Qiankun ADS3.0 intelligent driving system will be launched in August and will be launched on Xiangjie S9 for the first time
Jul 30, 2024 pm 02:17 PM
Huawei's Qiankun ADS3.0 intelligent driving system will be launched in August and will be launched on Xiangjie S9 for the first time
Jul 30, 2024 pm 02:17 PM
On July 29, at the roll-off ceremony of AITO Wenjie's 400,000th new car, Yu Chengdong, Huawei's Managing Director, Chairman of Terminal BG, and Chairman of Smart Car Solutions BU, attended and delivered a speech and announced that Wenjie series models will be launched this year In August, Huawei Qiankun ADS 3.0 version was launched, and it is planned to successively push upgrades from August to September. The Xiangjie S9, which will be released on August 6, will debut Huawei’s ADS3.0 intelligent driving system. With the assistance of lidar, Huawei Qiankun ADS3.0 version will greatly improve its intelligent driving capabilities, have end-to-end integrated capabilities, and adopt a new end-to-end architecture of GOD (general obstacle identification)/PDP (predictive decision-making and control) , providing the NCA function of smart driving from parking space to parking space, and upgrading CAS3.0
 What is SOL coin? How does SOL coin work?
Mar 16, 2024 am 10:37 AM
What is SOL coin? How does SOL coin work?
Mar 16, 2024 am 10:37 AM
Solana Blockchain and SOL Token Solana is a blockchain platform focused on providing high performance, security and scalability for decentralized applications (dApps). As the native asset of the Solana blockchain, SOL tokens are mainly used to pay transaction fees, pledge and participate in governance decisions. Solana’s unique features are its fast transaction confirmation times and high throughput, making it a favored choice among developers and users. Through SOL tokens, users can participate in various activities of the Solana ecosystem and jointly promote the development and progress of the platform. How Solana works Solana uses an innovative consensus mechanism called Proof of History (PoH) that is capable of efficiently processing thousands of transactions.
 Always new! Huawei Mate60 series upgrades to HarmonyOS 4.2: AI cloud enhancement, Xiaoyi Dialect is so easy to use
Jun 02, 2024 pm 02:58 PM
Always new! Huawei Mate60 series upgrades to HarmonyOS 4.2: AI cloud enhancement, Xiaoyi Dialect is so easy to use
Jun 02, 2024 pm 02:58 PM
On April 11, Huawei officially announced the HarmonyOS 4.2 100-machine upgrade plan for the first time. This time, more than 180 devices will participate in the upgrade, covering mobile phones, tablets, watches, headphones, smart screens and other devices. In the past month, with the steady progress of the HarmonyOS4.2 100-machine upgrade plan, many popular models including Huawei Pocket2, Huawei MateX5 series, nova12 series, Huawei Pura series, etc. have also started to upgrade and adapt, which means that there will be More Huawei model users can enjoy the common and often new experience brought by HarmonyOS. Judging from user feedback, the experience of Huawei Mate60 series models has improved in all aspects after upgrading HarmonyOS4.2. Especially Huawei M
 What is the architecture and working principle of Spring Data JPA?
Apr 17, 2024 pm 02:48 PM
What is the architecture and working principle of Spring Data JPA?
Apr 17, 2024 pm 02:48 PM
SpringDataJPA is based on the JPA architecture and interacts with the database through mapping, ORM and transaction management. Its repository provides CRUD operations, and derived queries simplify database access. Additionally, it uses lazy loading to only retrieve data when necessary, thus improving performance.
 What is VET coin? How does VET coin work?
Mar 16, 2024 am 11:40 AM
What is VET coin? How does VET coin work?
Mar 16, 2024 am 11:40 AM
VET Coin: Blockchain-based IoT ecosystem VeChainThor (VET) is a platform based on blockchain technology that aims to enhance the Internet of Things (IoT) field by ensuring the credibility of data and enabling safe transfer of value. supply chain management and business processes. VET coin is the native token of the VeChainThor blockchain and has the following functions: Pay transaction fees: VET coins are used to pay transaction fees on the VeChainThor network, including data storage, smart contract execution and identity verification. Governance: VET token holders can participate in the governance of VeChainThor, including voting on platform upgrades and proposals. Incentives: VET coins are used to incentivize validators in the network to ensure the
 What is Polygon coin? How does Polygon coin work?
Mar 16, 2024 am 09:22 AM
What is Polygon coin? How does Polygon coin work?
Mar 16, 2024 am 09:22 AM
Polygon: A multifunctional blockchain that builds the Ethereum ecosystem Polygon is a multifunctional blockchain platform built on Ethereum, formerly known as MaticNetwork. Its goal is to solve the scalability, high fees, and complexity issues in the Ethereum network. Polygon provides developers and users with a faster, cheaper, and simpler blockchain experience by providing scalability solutions. Here’s how Polygon works: Sidechain Network: Polygon creates a network of multiple sidechains. These sidechains run in parallel with the main Ethereum chain and can handle large volumes of transactions, thereby increasing overall network throughput. Plasma framework: Polygon utilizes the Plasma framework, which




