Protecting Privacy: A Guide to Encrypting Word Documents
Guarantee Privacy: Word Document Encryption Operation Guide
In today's highly developed information technology, our personal information, business secrets and other important data are often stored in various documents in electronic form. In order to ensure that this information is not peeked by unauthorized persons and protect the security of personal privacy and confidential information, encryption has become one of the important means. This article will introduce how to encrypt documents in the commonly used office software Word to ensure their security and privacy.
1. The Importance of Word Document Encryption
Word document is one of the document formats often used in our daily work and study, which may contain personal privacy, business secrets, personal information, etc. Sensitive information. If this information is leaked or stolen, it will cause immeasurable losses to individuals or organizations. Therefore, it is particularly important to encrypt Word documents.
2. How to encrypt Word documents
- Use password encryption
Open the Word document to be encrypted, click "File" - "Information" - "Protect Document" - "Encrypted Document". Enter the password in the pop-up dialog box, confirm it and enter the password again to ensure it is consistent. After saving the document, you will need to enter a password to view the document content next time you open the document. - Using permission settings
In addition to password protection, Word also provides the function of permission settings. You can set the document's opening, editing, printing and other permissions as needed to restrict unauthorized personnel's operations on the document. Similarly, settings can be made through "File" - "Information" - "Protect Document" - "Restrict Editing". - Use third-party encryption software
In addition to the encryption function that comes with Word, you can also use third-party encryption software to provide a higher level of encryption protection for Word documents. These software typically offer more encryption options and settings to ensure document security.
3. Precautions for encrypting documents
- Password settings
When setting a password, choose a complex enough combination, including uppercase and lowercase letters, numbers, and special characters. characters to avoid using easy-to-guess passwords and enhance document security. - Change the password regularly
In order to increase the security of the document, it is recommended to change the encryption password regularly to avoid the risk of password leakage caused by long-term use of the same password. - Reasonable sharing permissions
If you need to share encrypted documents, you should pay attention to reasonably controlling the sharing permissions to avoid misoperation or unauthorized users viewing the document content.
4. Protect privacy, starting with encrypted documents
With the continuous development of information technology, data leakage and information security issues have become increasingly prominent. Protecting personal privacy and the security of important data has become an issue that everyone should pay attention to. By encrypting Word documents in such a simple and effective way, the security and privacy of documents can be guaranteed to a certain extent. We hope that through the introduction of this article, readers can understand in more detail how to encrypt Word documents, thereby effectively protecting the privacy and security of individuals and organizations.
The above is the detailed content of Protecting Privacy: A Guide to Encrypting Word Documents. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1359
1359
 52
52
 Guide to turning off VBS in Windows 11
Mar 08, 2024 pm 01:03 PM
Guide to turning off VBS in Windows 11
Mar 08, 2024 pm 01:03 PM
With the launch of Windows 11, Microsoft has introduced some new features and updates, including a security feature called VBS (Virtualization-basedSecurity). VBS utilizes virtualization technology to protect the operating system and sensitive data, thereby improving system security. However, for some users, VBS is not a necessary feature and may even affect system performance. Therefore, this article will introduce how to turn off VBS in Windows 11 to help
 Setting up Chinese with VSCode: The Complete Guide
Mar 25, 2024 am 11:18 AM
Setting up Chinese with VSCode: The Complete Guide
Mar 25, 2024 am 11:18 AM
VSCode Setup in Chinese: A Complete Guide In software development, Visual Studio Code (VSCode for short) is a commonly used integrated development environment. For developers who use Chinese, setting VSCode to the Chinese interface can improve work efficiency. This article will provide you with a complete guide, detailing how to set VSCode to a Chinese interface and providing specific code examples. Step 1: Download and install the language pack. After opening VSCode, click on the left
 Detailed explanation of jQuery reference methods: Quick start guide
Feb 27, 2024 pm 06:45 PM
Detailed explanation of jQuery reference methods: Quick start guide
Feb 27, 2024 pm 06:45 PM
Detailed explanation of jQuery reference method: Quick start guide jQuery is a popular JavaScript library that is widely used in website development. It simplifies JavaScript programming and provides developers with rich functions and features. This article will introduce jQuery's reference method in detail and provide specific code examples to help readers get started quickly. Introducing jQuery First, we need to introduce the jQuery library into the HTML file. It can be introduced through a CDN link or downloaded
 How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
In Apple mobile phones, users can encrypt photo albums according to their own needs. Some users don't know how to set it up. You can add the pictures that need to be encrypted to the memo, and then lock the memo. Next, the editor will introduce the method of setting up the encryption of mobile photo albums for users. Interested users, come and take a look! Apple mobile phone tutorial How to set up iPhone photo album encryption A: After adding the pictures that need to be encrypted to the memo, go to lock the memo for detailed introduction: 1. Enter the photo album, select the picture that needs to be encrypted, and then click [Add to] below. 2. Select [Add to Notes]. 3. Enter the memo, find the memo you just created, enter it, and click the [Send] icon in the upper right corner. 4. Click [Lock Device] below
 PHP7 installation directory configuration guide
Mar 11, 2024 pm 12:18 PM
PHP7 installation directory configuration guide
Mar 11, 2024 pm 12:18 PM
PHP7 Installation Directory Configuration Guide PHP is a popular server-side scripting language used to develop dynamic web pages. Currently, the latest version of PHP is PHP7, which introduces many new features and performance optimizations and is the preferred version for many websites and applications. When installing PHP7, it is very important to correctly configure the installation directory. This article will provide you with a detailed guide to configuring the PHP7 installation directory, with specific code examples. To download PHP7 first, you need to download it from the PHP official website (https://www.
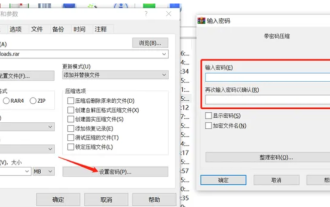 How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
The editor will introduce to you three methods of encryption and compression: Method 1: Encryption The simplest encryption method is to enter the password you want to set when encrypting the file, and the encryption and compression are completed. Method 2: Automatic encryption Ordinary encryption method requires us to enter a password when encrypting each file. If you want to encrypt a large number of compressed packages and the passwords are the same, then we can set automatic encryption in WinRAR, and then just When compressing files normally, WinRAR will add a password to each compressed package. The method is as follows: Open WinRAR, click Options-Settings in the setting interface, switch to [Compression], click Create Default Configuration-Set Password Enter the password we want to set here, click OK to complete the setting, we only need to correct
 Linux ldconfig usage guide
Mar 14, 2024 pm 12:36 PM
Linux ldconfig usage guide
Mar 14, 2024 pm 12:36 PM
Title: Linuxldconfig Usage Guide In Linux systems, the ldconfig command is a very important tool for updating link files connected to shared libraries in executable programs when the dynamic linker is running. Correct use of ldconfig can ensure that the system can correctly find and load the corresponding shared library files, thereby ensuring the normal operation of the program. This article will introduce the basic usage of ldconfig and provide some specific code examples. 1. Introduction to ldconfig ldcon
 How to decrypt the encrypted computer version of EZVIZ Cloud Video? -EZVIZ Cloud Video PC version exits full screen?
Mar 18, 2024 pm 12:25 PM
How to decrypt the encrypted computer version of EZVIZ Cloud Video? -EZVIZ Cloud Video PC version exits full screen?
Mar 18, 2024 pm 12:25 PM
How to de-encrypt videos on EZVIZ Cloud: There are many ways to de-encrypt videos on EZVIZ Cloud, one of which is by using the EZVIZ Cloud Mobile App. Users only need to enter the device list, select the camera to be decrypted and enter the device details page. On the device details page, find the "Settings" option, and then select "Video Encryption" to make relevant settings. In the video encryption settings interface, you can choose the option to turn off video encryption, and save the settings to complete the decryption operation. This simple step allows users to easily decrypt videos and improves the convenience of using the camera. If you use the computer client of EZVIZ Cloud, you can also cancel video encryption through similar steps. Just log in and select the corresponding camera, enter the device details interface, and then look for video addition in the settings.




