What kind of vulnerability does the phpmyadmin vulnerability belong to?
phpMyAdmin is vulnerable to multiple vulnerabilities, including: 1. SQL injection vulnerability; 2. Cross-site scripting (XSS) vulnerability; 3. Remote code execution (RCE) vulnerability; 4. Local file inclusion (LFI) Vulnerabilities; 5. Information leakage vulnerabilities; 6. Privilege escalation vulnerabilities.

phpMyAdmin vulnerability type
PHPMyAdmin is an open source database management tool that provides users with The web interface manages the functionality of MySQL and MariaDB databases. Unfortunately, it is also susceptible to various vulnerabilities that can put the database at risk.
Common vulnerability types in phpMyAdmin include:
1. SQL injection vulnerability
SQL injection vulnerability allows an attacker to inject malicious SQL commands into database queries . This may result in database operations being modified or even completely taken over.
2. Cross-Site Scripting (XSS) Vulnerabilities
XSS vulnerabilities allow an attacker to execute scripts in the victim's browser. This can lead to stealing session cookies, injecting malicious content, etc.
3. Remote Code Execution (RCE) Vulnerability
RCE vulnerability allows an attacker to execute arbitrary code on the server. This could lead to the server being taken over completely and used to attack other systems.
4. Local File Inclusion (LFI) Vulnerability
The LFI vulnerability allows an attacker to include arbitrary files on the server. This could lead to the disclosure of sensitive information or even allow an attacker to execute arbitrary code.
5. Information disclosure vulnerability
Information disclosure vulnerability allows an attacker to access information that should not be accessed. This may include a database connection string, username, or password.
6. Privilege Elevation Vulnerability
Elevation of Privilege Vulnerability allows an attacker to increase his or her privilege level in the database. This may result in complete control of the database.
The above is the detailed content of What kind of vulnerability does the phpmyadmin vulnerability belong to?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
 The relationship between mysql user and database
Apr 08, 2025 pm 07:15 PM
The relationship between mysql user and database
Apr 08, 2025 pm 07:15 PM
In MySQL database, the relationship between the user and the database is defined by permissions and tables. The user has a username and password to access the database. Permissions are granted through the GRANT command, while the table is created by the CREATE TABLE command. To establish a relationship between a user and a database, you need to create a database, create a user, and then grant permissions.
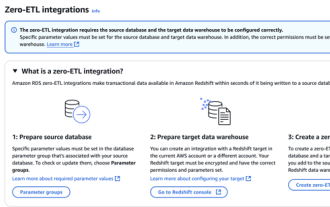 RDS MySQL integration with Redshift zero ETL
Apr 08, 2025 pm 07:06 PM
RDS MySQL integration with Redshift zero ETL
Apr 08, 2025 pm 07:06 PM
Data Integration Simplification: AmazonRDSMySQL and Redshift's zero ETL integration Efficient data integration is at the heart of a data-driven organization. Traditional ETL (extract, convert, load) processes are complex and time-consuming, especially when integrating databases (such as AmazonRDSMySQL) with data warehouses (such as Redshift). However, AWS provides zero ETL integration solutions that have completely changed this situation, providing a simplified, near-real-time solution for data migration from RDSMySQL to Redshift. This article will dive into RDSMySQL zero ETL integration with Redshift, explaining how it works and the advantages it brings to data engineers and developers.
 How to fill in mysql username and password
Apr 08, 2025 pm 07:09 PM
How to fill in mysql username and password
Apr 08, 2025 pm 07:09 PM
To fill in the MySQL username and password: 1. Determine the username and password; 2. Connect to the database; 3. Use the username and password to execute queries and commands.
 Query optimization in MySQL is essential for improving database performance, especially when dealing with large data sets
Apr 08, 2025 pm 07:12 PM
Query optimization in MySQL is essential for improving database performance, especially when dealing with large data sets
Apr 08, 2025 pm 07:12 PM
1. Use the correct index to speed up data retrieval by reducing the amount of data scanned select*frommployeeswherelast_name='smith'; if you look up a column of a table multiple times, create an index for that column. If you or your app needs data from multiple columns according to the criteria, create a composite index 2. Avoid select * only those required columns, if you select all unwanted columns, this will only consume more server memory and cause the server to slow down at high load or frequency times For example, your table contains columns such as created_at and updated_at and timestamps, and then avoid selecting * because they do not require inefficient query se
 MySQL: The Ease of Data Management for Beginners
Apr 09, 2025 am 12:07 AM
MySQL: The Ease of Data Management for Beginners
Apr 09, 2025 am 12:07 AM
MySQL is suitable for beginners because it is simple to install, powerful and easy to manage data. 1. Simple installation and configuration, suitable for a variety of operating systems. 2. Support basic operations such as creating databases and tables, inserting, querying, updating and deleting data. 3. Provide advanced functions such as JOIN operations and subqueries. 4. Performance can be improved through indexing, query optimization and table partitioning. 5. Support backup, recovery and security measures to ensure data security and consistency.
 How to optimize MySQL performance for high-load applications?
Apr 08, 2025 pm 06:03 PM
How to optimize MySQL performance for high-load applications?
Apr 08, 2025 pm 06:03 PM
MySQL database performance optimization guide In resource-intensive applications, MySQL database plays a crucial role and is responsible for managing massive transactions. However, as the scale of application expands, database performance bottlenecks often become a constraint. This article will explore a series of effective MySQL performance optimization strategies to ensure that your application remains efficient and responsive under high loads. We will combine actual cases to explain in-depth key technologies such as indexing, query optimization, database design and caching. 1. Database architecture design and optimized database architecture is the cornerstone of MySQL performance optimization. Here are some core principles: Selecting the right data type and selecting the smallest data type that meets the needs can not only save storage space, but also improve data processing speed.
 How to view mysql
Apr 08, 2025 pm 07:21 PM
How to view mysql
Apr 08, 2025 pm 07:21 PM
View the MySQL database with the following command: Connect to the server: mysql -u Username -p Password Run SHOW DATABASES; Command to get all existing databases Select database: USE database name; View table: SHOW TABLES; View table structure: DESCRIBE table name; View data: SELECT * FROM table name;
 Can I retrieve the database password in Navicat?
Apr 08, 2025 pm 09:51 PM
Can I retrieve the database password in Navicat?
Apr 08, 2025 pm 09:51 PM
Navicat itself does not store the database password, and can only retrieve the encrypted password. Solution: 1. Check the password manager; 2. Check Navicat's "Remember Password" function; 3. Reset the database password; 4. Contact the database administrator.




