 Technology peripherals
Technology peripherals
 AI
AI
 Sora comes to Adobe video editing software! The new version of Premiere Pro opens the era of AI editing
Sora comes to Adobe video editing software! The new version of Premiere Pro opens the era of AI editing
Sora comes to Adobe video editing software! The new version of Premiere Pro opens the era of AI editing
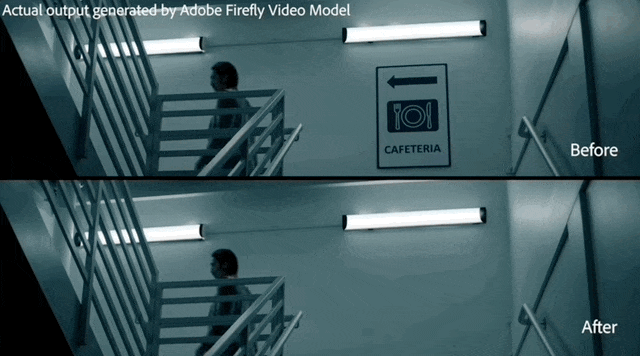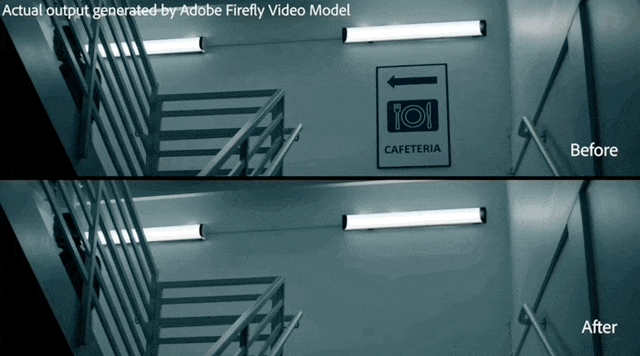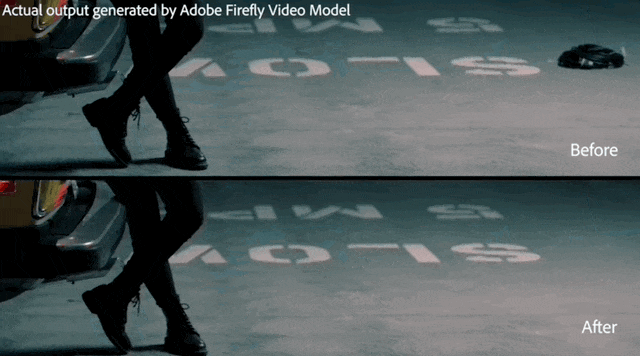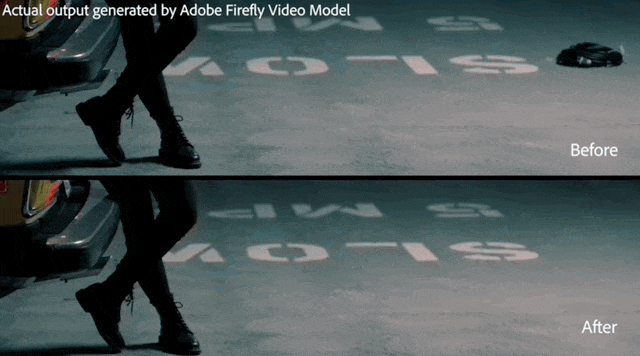
Sora will be integrated into Adobe video editing software.
In the latest Premier Pro concept demonstration, Adobe showed the results of its collaboration with OpenAI:
Outside of the main lens, Sora Generate a B-roll auxiliary shot.

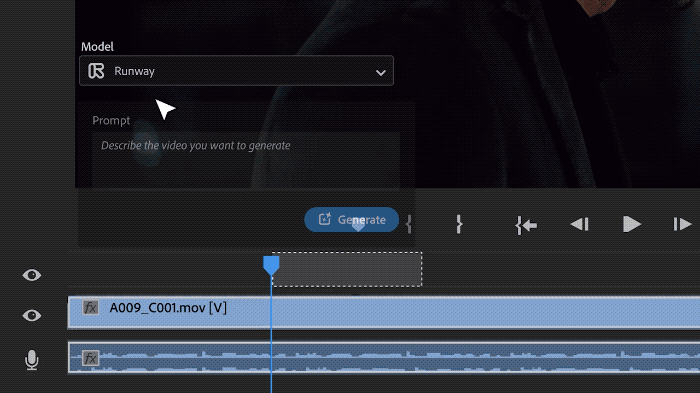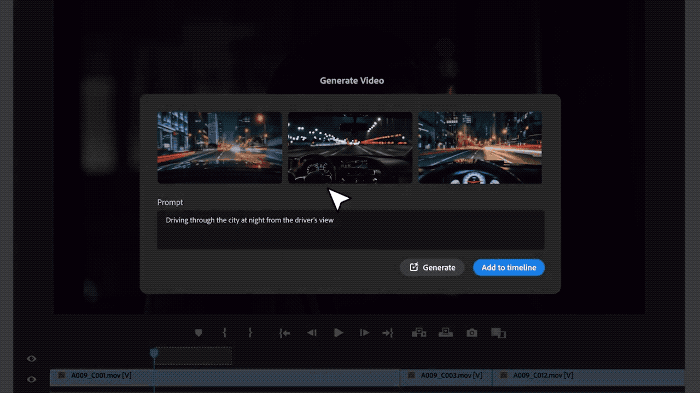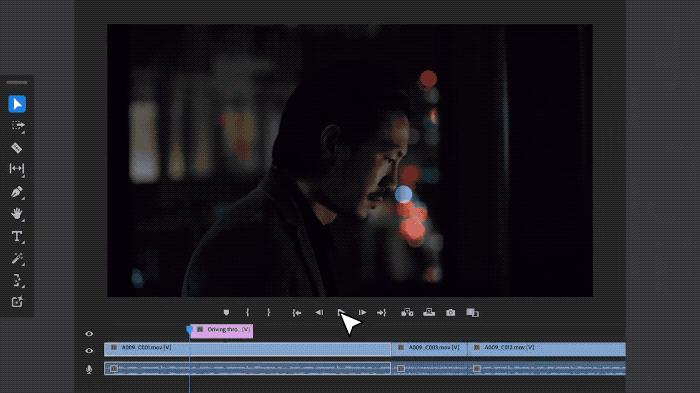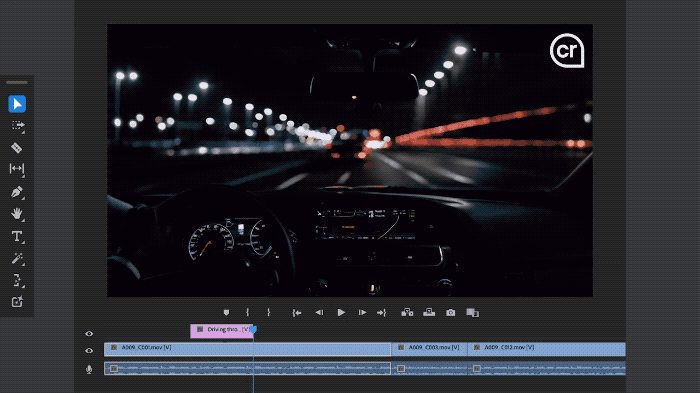
In addition to Sora, other popular AI video tools Runway and Pika will also be optional.
Runway is used similarly to Sora in the demonstration and can generate a brand new auxiliary shot.
#Pika can naturally extend the existing lens for several seconds.
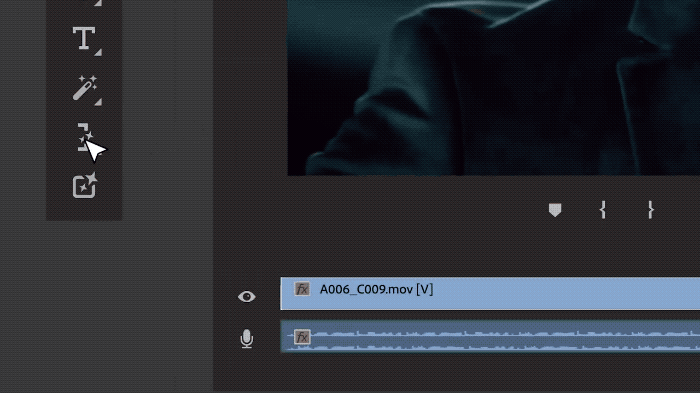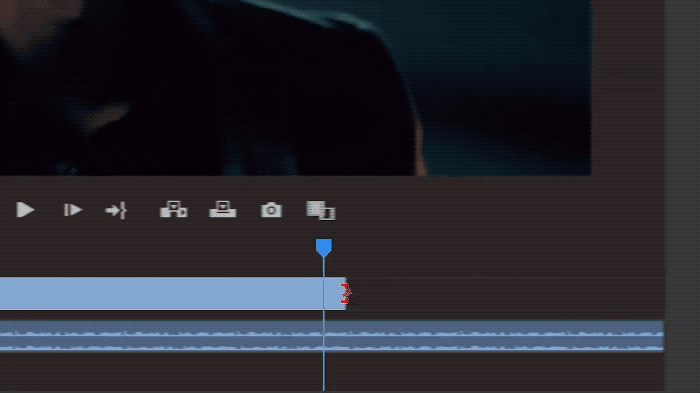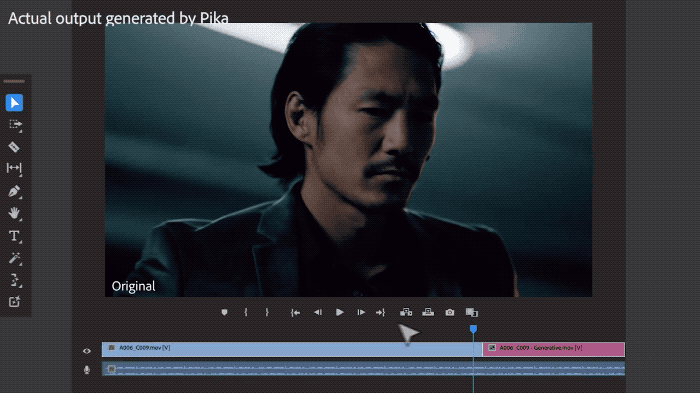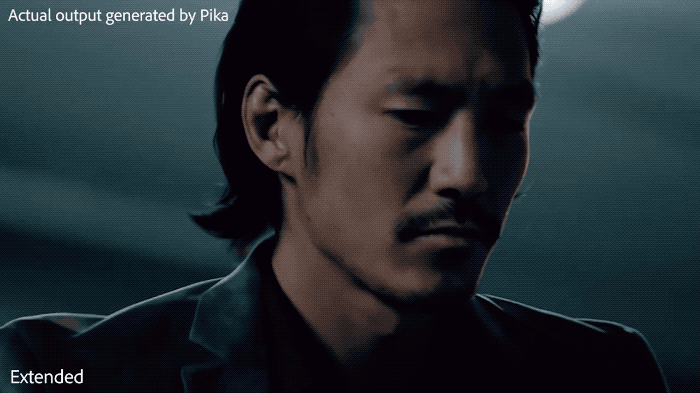
It should be emphasized that these features are still in the early preview and research stage, and it has not yet been revealed when they will be released.
In contrast, the functions supported by Adobe’s own AI product Firefly are more certain.
Professional editors can easily add and remove objects from their videos and expand footage on the timeline without ever leaving Premiere Pro.
Within this year, the video editing workflow will officially enter the AI era.
 Adobe’s promotional video this time mainly shows three major “functions”.
Adobe’s promotional video this time mainly shows three major “functions”.
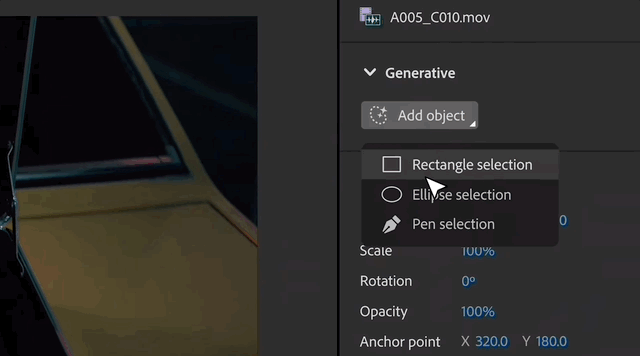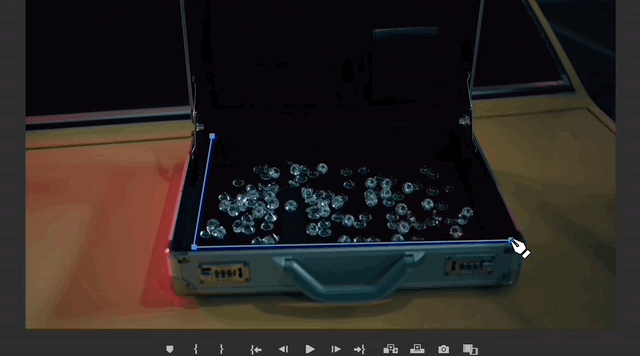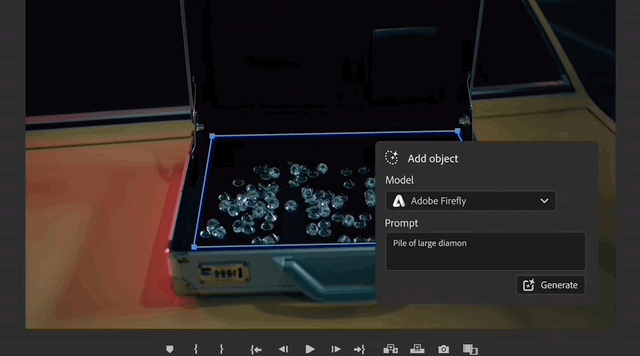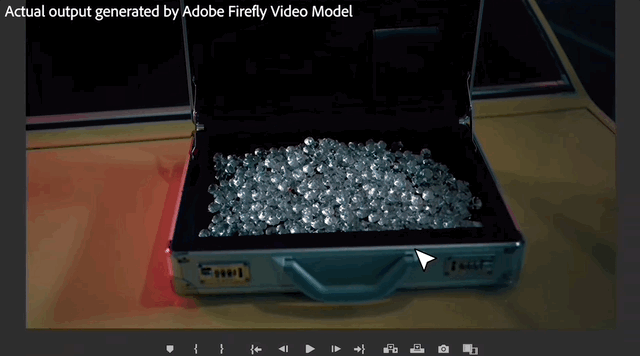
The first step is to add objects
to parts of the videoand add new objects.
In the video, the man slowly walked towards the woman, and then the woman turned around and opened a suitcase placed on the trunk of the car.
#Looking carefully, the box contains some scattered diamonds.

 In addition to such "addition", "subtraction" operation -
In addition to such "addition", "subtraction" operation -
- Premier will also do it.
With the blessing of the smart magic wand, it only takes one click to automatically identify the entire object, unlike the ordinary magic wand which can only select areas with similar colors. After the recognition is completed, objects can be eliminated with just one click, and the background of the corresponding area will be automatically completed.
#Exhibition boards on the wall and objects on the ground can all be removed with one click, leaving no trace of what once existed.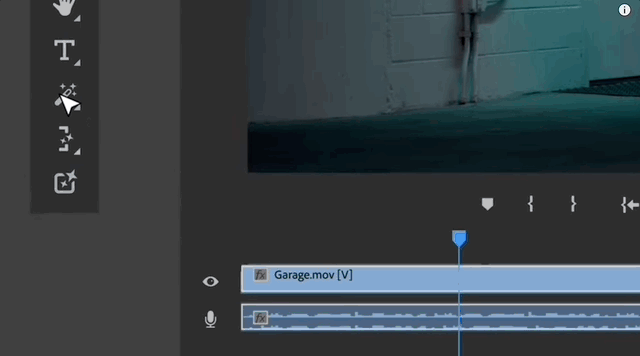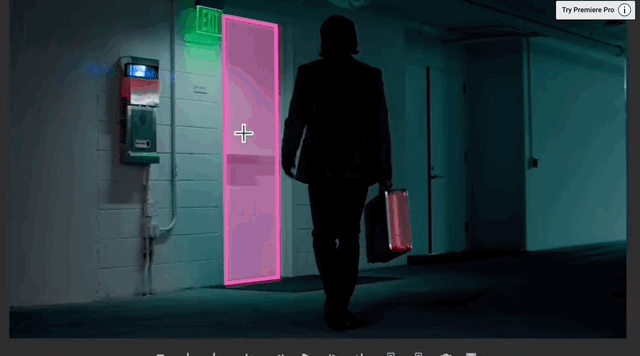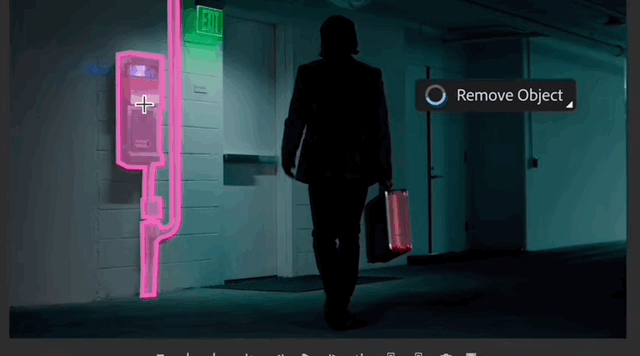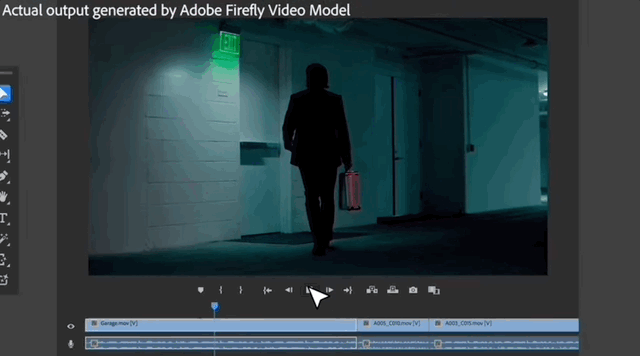
 The man in the video put on a new watch that can follow the movement of his wrist, and other parts of the video are not affected.
The man in the video put on a new watch that can follow the movement of his wrist, and other parts of the video are not affected.
Video extension .
.
When you find that there is a gap in the timeline and you don’t know what materials to put in it, Premiere can directly generate content to fill the gap, and it can be completed with just one click and drag.
The effect can be said to be seamless.
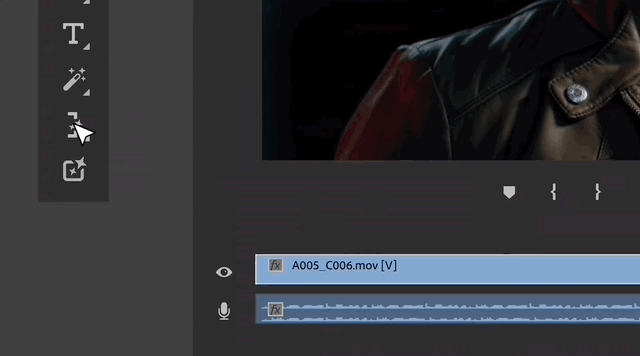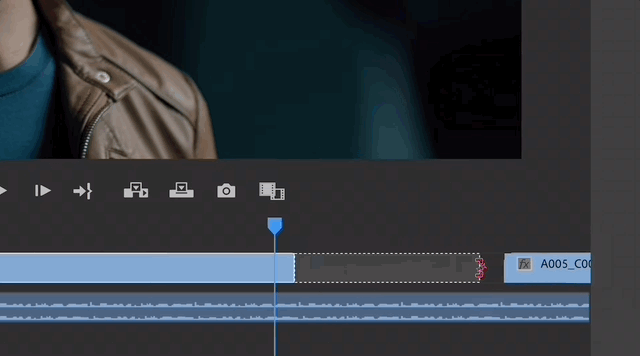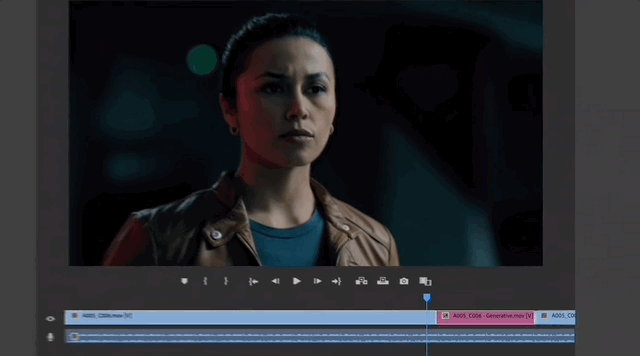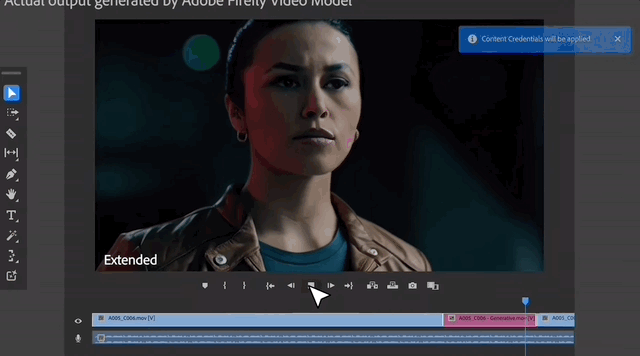
The most critical thing is that all AI generated results are not destructive to the original material.
You can roll back to the initial version at any time, or switch directly between different AI model results.
In addition, Adobe also provides a "content certificate" function. All videos produced by Premiere Pro will clearly indicate whether and which AI technology was used.
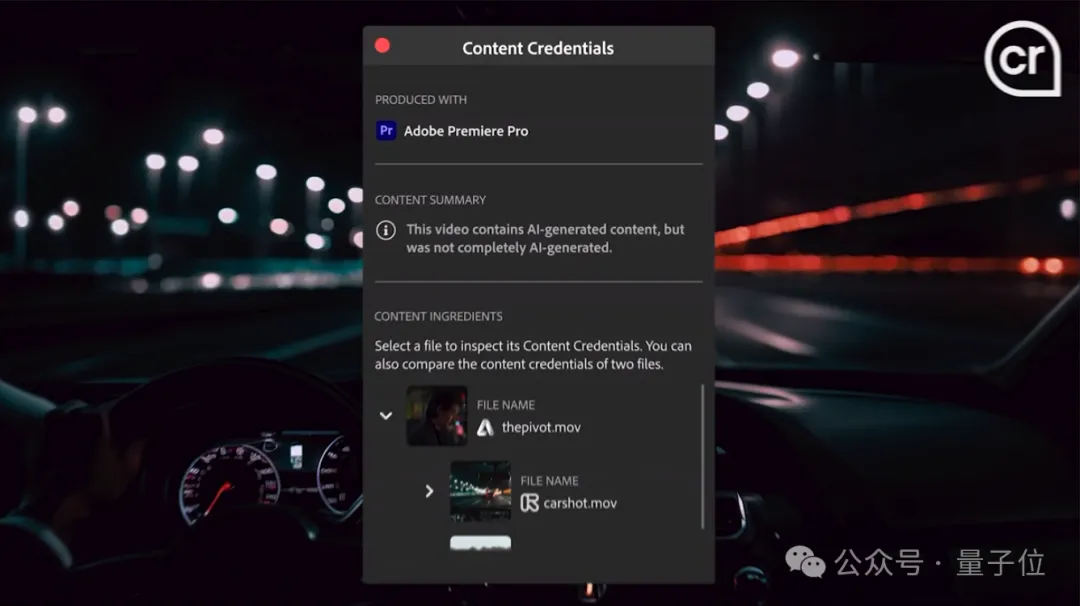
The release date of the above functions has not yet been determined, and no more information has been disclosed except that it will be released within this year.
In addition, Deepa Subramaniam, Adobe’s vice president of product marketing for creative professional applications, said that Adobe has not yet resolved the issue of how revenue generated from the use of third-party AI tools will be distributed between Adobe and partners.
To train its own AI video models, Adobe is buying video clips from photographers and artists.
Including short films showing people's daily activities and expressing various emotions, the payment is 2.62-7.25 US dollars per minute.
In this way, Adobe Firefly will ensure that AI-generated content is safe for commercial use.
The above is the detailed content of Sora comes to Adobe video editing software! The new version of Premiere Pro opens the era of AI editing. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 How to configure Debian Apache log format
Apr 12, 2025 pm 11:30 PM
How to configure Debian Apache log format
Apr 12, 2025 pm 11:30 PM
This article describes how to customize Apache's log format on Debian systems. The following steps will guide you through the configuration process: Step 1: Access the Apache configuration file The main Apache configuration file of the Debian system is usually located in /etc/apache2/apache2.conf or /etc/apache2/httpd.conf. Open the configuration file with root permissions using the following command: sudonano/etc/apache2/apache2.conf or sudonano/etc/apache2/httpd.conf Step 2: Define custom log formats to find or
 How Tomcat logs help troubleshoot memory leaks
Apr 12, 2025 pm 11:42 PM
How Tomcat logs help troubleshoot memory leaks
Apr 12, 2025 pm 11:42 PM
Tomcat logs are the key to diagnosing memory leak problems. By analyzing Tomcat logs, you can gain insight into memory usage and garbage collection (GC) behavior, effectively locate and resolve memory leaks. Here is how to troubleshoot memory leaks using Tomcat logs: 1. GC log analysis First, enable detailed GC logging. Add the following JVM options to the Tomcat startup parameters: -XX: PrintGCDetails-XX: PrintGCDateStamps-Xloggc:gc.log These parameters will generate a detailed GC log (gc.log), including information such as GC type, recycling object size and time. Analysis gc.log
 How to implement file sorting by debian readdir
Apr 13, 2025 am 09:06 AM
How to implement file sorting by debian readdir
Apr 13, 2025 am 09:06 AM
In Debian systems, the readdir function is used to read directory contents, but the order in which it returns is not predefined. To sort files in a directory, you need to read all files first, and then sort them using the qsort function. The following code demonstrates how to sort directory files using readdir and qsort in Debian system: #include#include#include#include#include//Custom comparison function, used for qsortintcompare(constvoid*a,constvoid*b){returnstrcmp(*(
 How to configure firewall rules for Debian syslog
Apr 13, 2025 am 06:51 AM
How to configure firewall rules for Debian syslog
Apr 13, 2025 am 06:51 AM
This article describes how to configure firewall rules using iptables or ufw in Debian systems and use Syslog to record firewall activities. Method 1: Use iptablesiptables is a powerful command line firewall tool in Debian system. View existing rules: Use the following command to view the current iptables rules: sudoiptables-L-n-v allows specific IP access: For example, allow IP address 192.168.1.100 to access port 80: sudoiptables-AINPUT-ptcp--dport80-s192.16
 How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
In Debian systems, readdir system calls are used to read directory contents. If its performance is not good, try the following optimization strategy: Simplify the number of directory files: Split large directories into multiple small directories as much as possible, reducing the number of items processed per readdir call. Enable directory content caching: build a cache mechanism, update the cache regularly or when directory content changes, and reduce frequent calls to readdir. Memory caches (such as Memcached or Redis) or local caches (such as files or databases) can be considered. Adopt efficient data structure: If you implement directory traversal by yourself, select more efficient data structures (such as hash tables instead of linear search) to store and access directory information
 Where is the Debian Nginx log path
Apr 12, 2025 pm 11:33 PM
Where is the Debian Nginx log path
Apr 12, 2025 pm 11:33 PM
In the Debian system, the default storage locations of Nginx's access log and error log are as follows: Access log (accesslog):/var/log/nginx/access.log Error log (errorlog):/var/log/nginx/error.log The above path is the default configuration of standard DebianNginx installation. If you have modified the log file storage location during the installation process, please check your Nginx configuration file (usually located in /etc/nginx/nginx.conf or /etc/nginx/sites-available/ directory). In the configuration file
 Debian mail server SSL certificate installation method
Apr 13, 2025 am 11:39 AM
Debian mail server SSL certificate installation method
Apr 13, 2025 am 11:39 AM
The steps to install an SSL certificate on the Debian mail server are as follows: 1. Install the OpenSSL toolkit First, make sure that the OpenSSL toolkit is already installed on your system. If not installed, you can use the following command to install: sudoapt-getupdatesudoapt-getinstallopenssl2. Generate private key and certificate request Next, use OpenSSL to generate a 2048-bit RSA private key and a certificate request (CSR): openss
 Debian mail server firewall configuration tips
Apr 13, 2025 am 11:42 AM
Debian mail server firewall configuration tips
Apr 13, 2025 am 11:42 AM
Configuring a Debian mail server's firewall is an important step in ensuring server security. The following are several commonly used firewall configuration methods, including the use of iptables and firewalld. Use iptables to configure firewall to install iptables (if not already installed): sudoapt-getupdatesudoapt-getinstalliptablesView current iptables rules: sudoiptables-L configuration



