What are the best practices for PHP function safety?
Best practices for securing PHP functions: Validate input to prevent injection and XSS attacks. Encode output to prevent XSS attacks. Use secure libraries to handle sensitive data. Restrict function access to ensure data security. Log and monitor function calls to facilitate troubleshooting and incident response.

PHP Function Security Best Practices
Writing secure functions in PHP is critical to protecting your application from attacks. Here are the best practices for securing your PHP functions:
1. Input Validation
- Validate user input to prevent injection attacks and cross-site scripting (XSS) ) attack.
- Use
filter_input(),filter_var()or custom rules to validate input.
<?php $username = filter_input(INPUT_POST, 'username', FILTER_SANITIZE_STRING); ?>
2. Output Encoding
- Encode the output to prevent cross-site scripting (XSS) attacks.
- Encode the output using the
htmlspecialchars()function or the built-ine()syntax.
<?php echo htmlspecialchars($output); ?>
3. Use security libraries
- Use built-in PHP libraries (such as
hash(),crypt()) or a verified third-party library to handle sensitive data. - Avoid using custom encryption algorithms as they are prone to errors.
<?php $passwordHash = password_hash($password, PASSWORD_DEFAULT); ?>
4. Restrict function access
- Use access permission control (such as
public,protected,private) to restrict access to functions. - Grant specific access permissions only to the class or object that requires access to the function.
<?php
class MyClass {
private function sensitiveFunction() { }
}
?>5. Logging and Monitoring
- Log all function calls and parameters for troubleshooting and incident response.
- Use a logging mechanism (such as
error_log()or a third-party package) to record function activity.
<?php
error_log("Function $functionName called with parameters: " . print_r($params, true));
?>Practical Example: Protecting Password Entry
The following example demonstrates how to use best practices to protect password entry:
<?php
// 输入验证
$password = filter_input(INPUT_POST, 'password', FILTER_SANITIZE_STRING);
// 输出编码
$passwordHash = password_hash($password, PASSWORD_DEFAULT);
// 记录函数调用
error_log("password_hash() called with password: " . $password);
?>Passed By following these best practices, you can write secure PHP functions that help prevent security vulnerabilities in your applications.
The above is the detailed content of What are the best practices for PHP function safety?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 PHP 8.4 Installation and Upgrade guide for Ubuntu and Debian
Dec 24, 2024 pm 04:42 PM
PHP 8.4 Installation and Upgrade guide for Ubuntu and Debian
Dec 24, 2024 pm 04:42 PM
PHP 8.4 brings several new features, security improvements, and performance improvements with healthy amounts of feature deprecations and removals. This guide explains how to install PHP 8.4 or upgrade to PHP 8.4 on Ubuntu, Debian, or their derivati
 CakePHP Date and Time
Sep 10, 2024 pm 05:27 PM
CakePHP Date and Time
Sep 10, 2024 pm 05:27 PM
To work with date and time in cakephp4, we are going to make use of the available FrozenTime class.
 CakePHP File upload
Sep 10, 2024 pm 05:27 PM
CakePHP File upload
Sep 10, 2024 pm 05:27 PM
To work on file upload we are going to use the form helper. Here, is an example for file upload.
 Discuss CakePHP
Sep 10, 2024 pm 05:28 PM
Discuss CakePHP
Sep 10, 2024 pm 05:28 PM
CakePHP is an open-source framework for PHP. It is intended to make developing, deploying and maintaining applications much easier. CakePHP is based on a MVC-like architecture that is both powerful and easy to grasp. Models, Views, and Controllers gu
 CakePHP Creating Validators
Sep 10, 2024 pm 05:26 PM
CakePHP Creating Validators
Sep 10, 2024 pm 05:26 PM
Validator can be created by adding the following two lines in the controller.
 How To Set Up Visual Studio Code (VS Code) for PHP Development
Dec 20, 2024 am 11:31 AM
How To Set Up Visual Studio Code (VS Code) for PHP Development
Dec 20, 2024 am 11:31 AM
Visual Studio Code, also known as VS Code, is a free source code editor — or integrated development environment (IDE) — available for all major operating systems. With a large collection of extensions for many programming languages, VS Code can be c
 How do you parse and process HTML/XML in PHP?
Feb 07, 2025 am 11:57 AM
How do you parse and process HTML/XML in PHP?
Feb 07, 2025 am 11:57 AM
This tutorial demonstrates how to efficiently process XML documents using PHP. XML (eXtensible Markup Language) is a versatile text-based markup language designed for both human readability and machine parsing. It's commonly used for data storage an
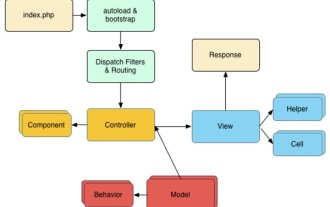 CakePHP Quick Guide
Sep 10, 2024 pm 05:27 PM
CakePHP Quick Guide
Sep 10, 2024 pm 05:27 PM
CakePHP is an open source MVC framework. It makes developing, deploying and maintaining applications much easier. CakePHP has a number of libraries to reduce the overload of most common tasks.






