 web3.0
web3.0
 Buterin shares a research article on fully homomorphic encryption: What is FHE and can it solve Web3 privacy problems?
Buterin shares a research article on fully homomorphic encryption: What is FHE and can it solve Web3 privacy problems?
Buterin shares a research article on fully homomorphic encryption: What is FHE and can it solve Web3 privacy problems?

Vitalik Buterin, the co-founder of Ethereum, has frequently talked about privacy issues recently, first for the privacy protocol Railgun, and after the U.S. Congress approved a controversial issue in the Foreign Intelligence Surveillance Act last month. After extending the terms for two years and authorizing U.S. intelligence agencies to monitor foreign targets without a search warrant, he criticized the value of cryptocurrency for being under attack.
Vitalik Buterin tweeted on the 5th that many people have recently been interested in fully homomorphic encryption (Fully homomophic Encryption, FHE) technology. Therefore, he republished his article published in 2020, which went into depth. The relevant mathematical working principles of FHE are introduced.
FHE Introduction
Vitalik Buterin pointed out in this article that FHE has long been considered one of the holy grails of cryptography. FHE is an encryption technology that allows third parties to perform calculations on encrypted materials. , and obtain the encrypted result, which the third party can return to anyone who has the decryption key of the original material, but the third party itself cannot decrypt the material or the result itself.
Vitalik Buterin pointed out as an example that a user receives a series of emails and wants to use a third-party spam filter to check whether they are spam.
Generally speaking, spam filters will want to protect the privacy of the algorithm. Either the spam filter provider wants its source code to be closed source, or it will rely on a very large database, and the provider does not want to make this public. Database, because this will make attacks easier, but users who are concerned about the privacy of their data and do not want to upload their unencrypted emails to third parties can use FHE to achieve this.
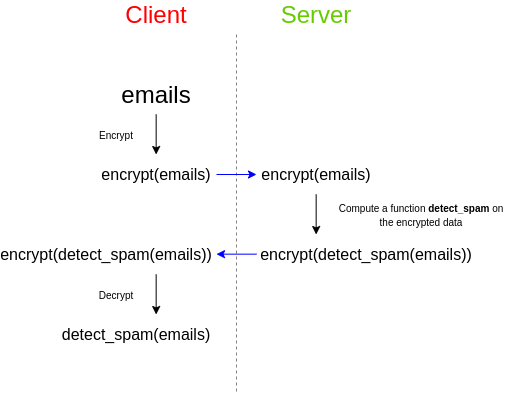
FHE is widely used
The article mentioned that FHE is widely used, covering the blockchain field, such as light clients that can be used to protect privacy end, the following applications can also be implemented:
More efficient covert address protocols, and more general scalability solutions for privacy protection protocols. The current privacy protection protocol requires each user Scan the entire blockchain yourself for incoming transactions.
A privacy-preserving data sharing marketplace that allows users to perform specific calculations on their data while maintaining full control over their data.
As part of stronger cryptographic primitives, such as more efficient multi-party computation protocols, program obfuscation may eventually also be covered.
What are the differences between FHE, ZK and MPC?
Previously, Portal Ventures wrote an article last year to discuss FHE technology, analyzing its differences with zero-knowledge proof (ZK) and multi-party computation (MPC), pointing out that in the field of cryptocurrency, FHE can be used to build a more private For smart contracts and other blockchain applications, ZK is used to build scalable blockchain solutions, while MPC is mainly used for private key management and custody.
The article mentioned that although FHE, ZK and MPC overlap in some aspects, they all have their own unique advantages and application scenarios. In the currency circle, these three technologies are all for enhancing privacy and The security offers huge potential, but their combination and further research remains an active area in the crypto community.
The above is the detailed content of Buterin shares a research article on fully homomorphic encryption: What is FHE and can it solve Web3 privacy problems?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 okx Ouyi Exchange web version enter link click to enter
Mar 31, 2025 pm 06:21 PM
okx Ouyi Exchange web version enter link click to enter
Mar 31, 2025 pm 06:21 PM
1. Enter the web version of okx Euyi Exchange ☜☜☜☜☜☜ Click to save 2. Click the link of okx Euyi Exchange app ☜☜☜☜ Click to save 3. After entering the official website, the clear interface provides a login and registration portal. Users can choose to log in to an existing account or register a new account according to their own situation. Whether it is viewing real-time market conditions, conducting transactions, or managing assets, the OKX web version provides a simple and smooth operating experience, suitable for beginners and veterans. Visit OKX official website now for easy experience
 gate.io registration tutorial
Mar 31, 2025 pm 11:09 PM
gate.io registration tutorial
Mar 31, 2025 pm 11:09 PM
This article provides a detailed Gate.io registration tutorial, covering every step from accessing the official website to completing registration, including filling in registration information, verifying, reading user agreements, etc. The article also emphasizes security measures after successful registration, such as setting up secondary verification and completing real-name authentication, and gives tips from beginners to help users safely start their digital asset trading journey.
 What is Ouyi for? What is Ouyi
Apr 01, 2025 pm 03:18 PM
What is Ouyi for? What is Ouyi
Apr 01, 2025 pm 03:18 PM
OKX is a global digital asset trading platform. Its main functions include: 1. Buying and selling digital assets (spot trading), 2. Trading between digital assets, 3. Providing market conditions and data, 4. Providing diversified trading products (such as derivatives), 5. Providing asset value-added services, 6. Convenient asset management.
 How to roll positions in digital currency? What are the digital currency rolling platforms?
Mar 31, 2025 pm 07:36 PM
How to roll positions in digital currency? What are the digital currency rolling platforms?
Mar 31, 2025 pm 07:36 PM
Digital currency rolling positions is an investment strategy that uses lending to amplify trading leverage to increase returns. This article explains the digital currency rolling process in detail, including key steps such as selecting trading platforms that support rolling (such as Binance, OKEx, gate.io, Huobi, Bybit, etc.), opening a leverage account, setting a leverage multiple, borrowing funds for trading, and real-time monitoring of the market and adjusting positions or adding margin to avoid liquidation. However, rolling position trading is extremely risky, and investors need to operate with caution and formulate complete risk management strategies. To learn more about digital currency rolling tips, please continue reading.
 ok official portal web version ok exchange official web version login portal
Mar 31, 2025 pm 06:24 PM
ok official portal web version ok exchange official web version login portal
Mar 31, 2025 pm 06:24 PM
This article details how to use the official web version of OK exchange to log in. Users only need to search for "OK Exchange Official Web Version" in their browser, click the login button in the upper right corner after entering the official website, and enter the user name and password to log in. Registered users can easily manage assets, conduct transactions, deposit and withdraw funds, etc. The official website interface is simple and easy to use, and provides complete customer service support to ensure that users have a smooth digital asset trading experience. What are you waiting for? Visit the official website of OK Exchange now to start your digital asset journey!
 How to calculate the transaction fee of gate.io trading platform?
Mar 31, 2025 pm 09:15 PM
How to calculate the transaction fee of gate.io trading platform?
Mar 31, 2025 pm 09:15 PM
The handling fees of the Gate.io trading platform vary according to factors such as transaction type, transaction pair, and user VIP level. The default fee rate for spot trading is 0.15% (VIP0 level, Maker and Taker), but the VIP level will be adjusted based on the user's 30-day trading volume and GT position. The higher the level, the lower the fee rate will be. It supports GT platform coin deduction, and you can enjoy a minimum discount of 55% off. The default rate for contract transactions is Maker 0.02%, Taker 0.05% (VIP0 level), which is also affected by VIP level, and different contract types and leverages
 What are the recommended websites for virtual currency app software?
Mar 31, 2025 pm 09:06 PM
What are the recommended websites for virtual currency app software?
Mar 31, 2025 pm 09:06 PM
This article recommends ten well-known virtual currency-related APP recommendation websites, including Binance Academy, OKX Learn, CoinGecko, CryptoSlate, CoinDesk, Investopedia, CoinMarketCap, Huobi University, Coinbase Learn and CryptoCompare. These websites not only provide information such as virtual currency market data, price trend analysis, etc., but also provide rich learning resources, including basic blockchain knowledge, trading strategies, and tutorials and reviews of various trading platform APPs, helping users better understand and make use of them
 On which platform is web3 transaction?
Mar 31, 2025 pm 07:54 PM
On which platform is web3 transaction?
Mar 31, 2025 pm 07:54 PM
This article lists the top ten well-known Web3 trading platforms, including Binance, OKX, Gate.io, Kraken, Bybit, Coinbase, KuCoin, Bitget, Gemini and Bitstamp. The article compares the characteristics of each platform in detail, such as the number of currencies, trading types (spot, futures, options, NFT, etc.), handling fees, security, compliance, user groups, etc., aiming to help investors choose the most suitable trading platform. Whether it is high-frequency traders, contract trading enthusiasts, or investors who focus on compliance and security, they can find reference information from it.


