MySQL数据库技术(19)_MySQL
3.9 MySQL 不支持的功能
本节介绍其他数据库中有而MySQL 中无的功能。它介绍省略了什么功能,以及在需要这些功能时怎么办。一般情况下, MySQL 之所以忽略某些功能是因为它们有负面性能影响。有的功能正在开发者的计划清单上,一旦找到一种方法可以实现相应的功能而又不致于影响良好性能的目标,就会对它们进行实现。
■ 子选择。子选择是嵌套在另一个SELECT 语句内的SELECT 语句,如下面的查询所示:
SELECT * FROM score
WHERE event_id IN (SELECT event_id FROM event WHERE type = "T")
子选择打算在MySQL 3.24 中给出,到那时它们就不会忽略了。但到那时,许多用子选择撰写的查询也可以用连接来编写。请参阅3 . 8 . 1节“将子选择编写为连接”。
■ 事务处理和提交/回退。事务处理是由其他客户机作为一个整体不中断执行的一组S Q L语句。提交/回退功能允许规定数条语句作为一个整体执行或不执行。即,如果事务处理中的任何一条语句失败,那么直到该语句前执行的所有语句的作用都被撤消。
ySQL 自动进行单一SQL 语句的同步以免客户机互相干扰。(例如,两个客户机不能对相同的表进行同时写入。)此外,可利用LOCK TABLES 和UNLOCK TA B L ES将数条语句组成一个整体,这使您能够完成单条语句的并发控制所不能满足的操作。MySQL 与事务处理有关的问题是,它不能自动对数条语句进行组织,而且如果这些语句中有某一条失败后也不能对它们进行回退。
为了弄清事务处理为什么有用,可举例说明。假如您在服装销售业工作,无论何时,只要您的销售人员进行了一次销售,都要更新库存数目。下面的例子说明了在多个销售人员同时更新数据库时可能出现的问题(假如初始的衬衫库存数目为4 7):
t1 销售人员1卖出3件衬衫
t2 销售人员检索当前衬衫计数( 4 7):
SELECT quantity FROM inventory WHERE item = "shirt"
t3 销售人员2卖出2件衬衫
t4 销售人员2检索当前衬衫计数( 4 7)
SELECT quantity FROM inventory WHERE item = "shirt"
t5 销售人员1计算库存的新数目为47 - 3 = 44 并设置衬衫计数为44:
UPDATE inventory SET quantity = 44 WHERE item = "shirt"
t6 销售人员2计算库存的新数目为47 - 2 = 45 并设置衬衫计数为45:
UPDATE inventory SET quantity = 45 WHERE item = "shirt"
在这个事件序列结束时,您已经卖掉了5 件衬衫,但库存数目却是45 而不是4 2。问题是如果在一条语句中查看库存而在另一条语句中更新其值,这是一个多语句的事务处理。第二条语句中所进行的活动取决于第一条语句中检索出的值。但是如果在重叠的时间范围内出现独立的事务处理,则每个事务处理的语句会纠缠在一起,并且互相干扰。在事务处理型的数据库中,每个销售人员的语句可作为一个事务处理执行,这样,销售人员2 的语句在销售人员1 的语句完成之前不会被执行。在MySQL 中,可用两种方法达到这个目的:
■ 方法1:作为一个整体执行一组语句。可利用LOCK TABLES 和UNLOCK TABLES将语句组织在一起,并将它们作为一个原子单元执行:锁住所需使用的表,发布查询,然后释放这些锁。这样阻止了其他人在您锁住这些表时使用它们。利用表同步,库存情况如下所示:
t1 销售人员1卖出3件衬衫
t2 销售人员1请求一个锁并检索当前衬衫计数(47)
LOCK TABLES inventory WRITE
SELECT quantity FROM inventory WHERE item = "shirt"
t3 销售人员2卖出2件衬衫
t4 销售人员2试图取得一个锁:这被阻塞,因为销售人员1 已经占住了锁:
LOCK TABLES inventory WRITE
t5 销售人员1计算库存的新数目为47 - 3 = 44 并设置衬衫计数为44,然后释放锁:
UPDATE inventory SET quantity = 44 WHERE item = "shirt"
UNLOCK TABLES
t6 现在销售人员2的锁请求成功。销售人员2检索当前衬衫计数( 44)
SELECT quantity FROM inventory WHERE item = "shirt"
t7 销售人员2计算库存的新数目为44 - 2 = 42,设置衬衫计数为4 2,然后释放锁:
UPDATE inventory SET quantity = 42 WHERE item = "shirt"
UNLOCK TABLES

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How effective is receiving phone calls using airplane mode?
Feb 20, 2024 am 10:07 AM
How effective is receiving phone calls using airplane mode?
Feb 20, 2024 am 10:07 AM
What happens when someone calls in airplane mode? Mobile phones have become one of the indispensable tools in people's lives. It is not only a communication tool, but also a collection of entertainment, learning, work and other functions. With the continuous upgrading and improvement of mobile phone functions, people are becoming more and more dependent on mobile phones. With the advent of airplane mode, people can use their phones more conveniently during flights. However, some people are worried about what impact other people's calls in airplane mode will have on the mobile phone or the user? This article will analyze and discuss from several aspects. first
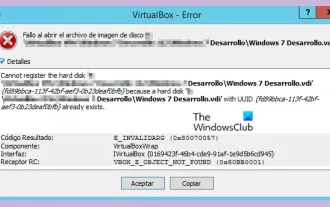 VBOX_E_OBJECT_NOT_FOUND(0x80bb0001)VirtualBox error
Mar 24, 2024 am 09:51 AM
VBOX_E_OBJECT_NOT_FOUND(0x80bb0001)VirtualBox error
Mar 24, 2024 am 09:51 AM
When trying to open a disk image in VirtualBox, you may encounter an error indicating that the hard drive cannot be registered. This usually happens when the VM disk image file you are trying to open has the same UUID as another virtual disk image file. In this case, VirtualBox displays error code VBOX_E_OBJECT_NOT_FOUND(0x80bb0001). If you encounter this error, don’t worry, there are some solutions you can try. First, you can try using VirtualBox's command line tools to change the UUID of the disk image file, which will avoid conflicts. You can run the command `VBoxManageinternal
 File Inclusion Vulnerabilities in Java and Their Impact
Aug 08, 2023 am 10:30 AM
File Inclusion Vulnerabilities in Java and Their Impact
Aug 08, 2023 am 10:30 AM
Java is a commonly used programming language used to develop various applications. However, just like other programming languages, Java has security vulnerabilities and risks. One of the common vulnerabilities is the file inclusion vulnerability (FileInclusionVulnerability). This article will explore the principle, impact and how to prevent this vulnerability. File inclusion vulnerabilities refer to the dynamic introduction or inclusion of other files in the program, but the introduced files are not fully verified and protected, thus
 How to turn off the comment function on TikTok? What happens after turning off the comment function on TikTok?
Mar 23, 2024 pm 06:20 PM
How to turn off the comment function on TikTok? What happens after turning off the comment function on TikTok?
Mar 23, 2024 pm 06:20 PM
On the Douyin platform, users can not only share their life moments, but also interact with other users. Sometimes the comment function may cause some unpleasant experiences, such as online violence, malicious comments, etc. So, how to turn off the comment function of TikTok? 1. How to turn off the comment function of Douyin? 1. Log in to Douyin APP and enter your personal homepage. 2. Click "I" in the lower right corner to enter the settings menu. 3. In the settings menu, find "Privacy Settings". 4. Click "Privacy Settings" to enter the privacy settings interface. 5. In the privacy settings interface, find "Comment Settings". 6. Click "Comment Settings" to enter the comment setting interface. 7. In the comment settings interface, find the "Close Comments" option. 8. Click the "Close Comments" option to confirm closing comments.
 The impact of data scarcity on model training
Oct 08, 2023 pm 06:17 PM
The impact of data scarcity on model training
Oct 08, 2023 pm 06:17 PM
The impact of data scarcity on model training requires specific code examples. In the fields of machine learning and artificial intelligence, data is one of the core elements for training models. However, a problem we often face in reality is data scarcity. Data scarcity refers to the insufficient amount of training data or the lack of annotated data. In this case, it will have a certain impact on model training. The problem of data scarcity is mainly reflected in the following aspects: Overfitting: When the amount of training data is insufficient, the model is prone to overfitting. Overfitting refers to the model over-adapting to the training data.
 What problems will bad sectors on the hard drive cause?
Feb 18, 2024 am 10:07 AM
What problems will bad sectors on the hard drive cause?
Feb 18, 2024 am 10:07 AM
Bad sectors on a hard disk refer to a physical failure of the hard disk, that is, the storage unit on the hard disk cannot read or write data normally. The impact of bad sectors on the hard drive is very significant, and it may lead to data loss, system crash, and reduced hard drive performance. This article will introduce in detail the impact of hard drive bad sectors and related solutions. First, bad sectors on the hard drive may lead to data loss. When a sector in a hard disk has bad sectors, the data on that sector cannot be read, causing the file to become corrupted or inaccessible. This situation is especially serious if important files are stored in the sector where the bad sectors are located.
 What specific impact do mine cards have on the game?
Jan 03, 2024 am 09:05 AM
What specific impact do mine cards have on the game?
Jan 03, 2024 am 09:05 AM
Some users may consider buying mining cards for the sake of cheapness. After all, these cards are top-notch graphics cards. However, some gamers are worried about the impact of mining cards on playing games. Let’s take a look at the detailed introduction below. What are the effects of using a mining card to play games: 1. The stability of playing games with a mining card cannot be guaranteed, because the life of the mining card is very short and it is likely to become useless after just playing. 2. The mining card is basically a castrated version of the original version. Due to long-term wear and tear, the performance in all aspects may be weak. 3. In this way, users may not be able to display all the effects of the game when playing the game. 4. Moreover, the electronic components of the graphics card will age in advance, not to mention that playing games also consumes the graphics card, so it is drained to a greater extent, so the impact on the game is great. 5. In general, use mining cards to play games
 What are the effects of low graphics card configuration?
Feb 15, 2024 pm 03:27 PM
What are the effects of low graphics card configuration?
Feb 15, 2024 pm 03:27 PM
The running quality of a computer basically has a huge impact on its graphics card. Some users don’t know much about graphics cards, and they don’t know exactly what aspects of the computer the graphics card will affect. For your convenience, here is what you need to know: Let’s introduce some effects of low graphics card configuration. What are the effects of low graphics card configuration? Answer: 1. Some large-scale 3D games cannot run. 2. When playing some high-definition videos, the computer will be under great pressure. 3. For some more professional software, there is no way to run it well when drawing and 3D model rendering are required. 4. If the graphics card configuration is low, the game will not be able to open, or it will frequently crash or freeze, and the computer will also have a blurred screen or a blue screen. 5. The most important thing in the game is the graphics card, because many pictures require






