用php代码限制国内IP访问我们网站
这篇文章主要介绍了用php代码限制国内IP访问我们网站,需要的朋友可以参考下
利用淘宝的IP接口来判断IP,是否是国内的ip,是国内(CN)的就不允许访问。
$ip = $_SERVER['REMOTE_ADDR']; $content = file_get_contents(‘?ip='.$ip); $banned = json_decode(trim($content), true); $lan = strtolower($_SERVER['HTTP_ACCEPT_LANGUAGE']); if((!empty($banned['data']['country_id']) && $banned['data']['country_id'] == ‘CN') || strstr($lan, ‘zh')) { header(“HTTP/1.0 404 Not Found”); echo ‘HTTP/1.0 404 Not Found'; exit; }
同时发现一篇好文章: 《Redis 来限制高并发 php代码实例》
Redis本质上也是一种键值数据库的,但它在保持键值数据库简单快捷特点的同时,又吸收了部分关系数据库的优点。从而使它的位置处于关系数据库和键值数据库之间。Redis不仅能保存Strings类型的数据,还能保存Lists类型(有序)和Sets类型(无序)的数据,而且还能完成排序(SORT) 等高级功能,在实现INCR,,SETNX等功能的时候,保证了其操作的原子性,除此以外,还支持主从复制等功能。
Redis 来限制高并发
php代码实例
$redis->setnx(‘lock:hot_items', true)尝试创建一个key作为”锁”.若key已存在,setnx不会做任何动作且返回值为false,所以只有一个客户端会返回true值进入if语句更新缓存. $redis = new redis(); $redis_key = ‘lock:hot_items'; $clock_expire_time = $redis->get($redis_key); if(!empty($clock_expire_time) && time() > intval($clock_expire_time)) { //解除当前Redis锁 $redis->delete($redis_key); } if($redis->setnx($redis_key, time() + 3) !== true) { echo ‘高并发有冲突'; } //操作你的代码, 同一时刻就一个人访问该代码了 //解除当前Redis锁 $redis->delete($redis_key);

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1389
1389
 52
52
 How to remove comment restrictions on video accounts? What is the word limit for comments on a video account?
Mar 22, 2024 pm 02:11 PM
How to remove comment restrictions on video accounts? What is the word limit for comments on a video account?
Mar 22, 2024 pm 02:11 PM
With the popularity of video accounts on social media, more and more people are beginning to use video accounts to share their daily lives, insights and stories. However, some users may experience comments being restricted, which can leave them confused and dissatisfied. 1. How to remove comment restrictions on video accounts? To lift the restriction on commenting on a video account, you must first ensure that the account has been properly registered and real-name authentication has been completed. Video accounts have requirements for comments. Only accounts that have completed real-name authentication can lift comment restrictions. If there are any abnormalities in the account, these issues need to be resolved before comment restrictions can be lifted. 2. Comply with the community standards of the video account. Video accounts have certain standards for comment content. If the comment involves illegal content, you will be restricted from speaking. To lift comment restrictions, you need to abide by the community of the video account
 How to use JavaScript to drag and zoom images while limiting them to the container?
Oct 20, 2023 pm 04:19 PM
How to use JavaScript to drag and zoom images while limiting them to the container?
Oct 20, 2023 pm 04:19 PM
How does JavaScript implement dragging and zooming of images while limiting them to the container? In web development, we often encounter the need to drag and zoom images. This article will introduce how to use JavaScript to implement dragging and zooming of images and limit operations within the container. 1. Drag the picture To drag the picture, we can use mouse events to track the mouse position and move the picture position accordingly. The following is a sample code: //Get the picture element varimage
 How to set up a CentOS system to restrict user modifications to system logs
Jul 05, 2023 pm 03:43 PM
How to set up a CentOS system to restrict user modifications to system logs
Jul 05, 2023 pm 03:43 PM
How to set up the CentOS system to restrict users from modifying the system log. In the CentOS system, the system log is a very important source of information. It records the system's operating status, error messages, warnings, etc. In order to protect the stability and security of the system, we should restrict users from modifying system logs. This article will introduce how to set up the CentOS system to restrict the modification permissions of the system log. 1. Create user groups and users. First, we need to create a user group specifically responsible for managing system logs, and a user group for managing system logs.
 What are the limitations and considerations for C++ function overloading?
Apr 13, 2024 pm 01:09 PM
What are the limitations and considerations for C++ function overloading?
Apr 13, 2024 pm 01:09 PM
Restrictions on function overloading include: parameter types and orders must be different (when the number of parameters is the same), and default parameters cannot be used to distinguish overloading. In addition, template functions and non-template functions cannot be overloaded, and template functions with different template specifications can be overloaded. It's worth noting that excessive use of function overloading can affect readability and debugging, the compiler searches from the most specific to the least specific function to resolve conflicts.
 What are the limitations of reflection mechanism in Go language?
Jun 09, 2023 pm 11:31 PM
What are the limitations of reflection mechanism in Go language?
Jun 09, 2023 pm 11:31 PM
As a statically typed language, Go language needs to clarify the type of each variable when writing code. However, in some cases, we need to dynamically analyze and operate types in the program, and in this case, we need to use the reflection mechanism. The reflection mechanism can dynamically obtain the type information of the program object when the program is running, and can analyze and operate it, which is very useful. However, the reflection mechanism in Go language also has some limitations. Let’s take a closer look below. The impact of reflection mechanism on performance Using reflection mechanism can greatly enhance generation
 Nginx restricts access frequency configuration to prevent malicious attacks
Jul 04, 2023 pm 05:01 PM
Nginx restricts access frequency configuration to prevent malicious attacks
Jul 04, 2023 pm 05:01 PM
Nginx restricts access frequency configuration to prevent malicious attacks. With the development of the Internet, website security has become an important issue. In order to prevent malicious attacks, we need to limit access frequency. As a high-performance web server, Nginx can achieve this goal through configuration. Nginx provides a module called limit_req_module, which can limit access frequency. Before configuring, we need to make sure the module is enabled. at nginx.con
 Applications and limitations of inline template functions
Apr 28, 2024 pm 02:33 PM
Applications and limitations of inline template functions
Apr 28, 2024 pm 02:33 PM
Inline template functions insert code directly into the call point without generating a separate function object. Applications include code optimization, performance improvement, constant evaluation, and code simplification. But be aware of its limitations, such as longer compilation times, increased code size, reduced debuggability, and limitations across compilation units.
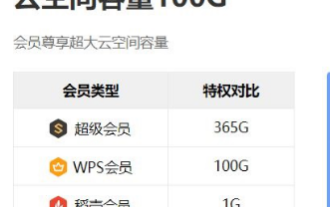 What should I do if the maximum size of documents that WPS members can upload exceeds the limit?
Mar 20, 2024 pm 06:40 PM
What should I do if the maximum size of documents that WPS members can upload exceeds the limit?
Mar 20, 2024 pm 06:40 PM
WPS is an office software that integrates comprehensive operations. You can now download WPS for use, but if you want to have more functions, you need to register as a member. Some people may wonder what is the maximum file size that a WPS member can upload? If you are a WPS member user, you can upload files up to 1G each time, and all files can add up to 365G. There may be some differences in different terminals, but the overall display is basically similar. What should I do if I cannot upload beyond the limit? We will explain it next. 1. When uploading files, such as cloud documents, there is a certain amount of space. If it exceeds the size, it cannot be uploaded. 2. Click on the membership logo, purchase membership according to your needs, and expand the space. 3. Coupons may appear occasionally, so don’t forget to use them.




