
Data storage encryption methods
Data storage encryption methods include symmetric encryption, asymmetric encryption and hashing algorithms. For more information on data storage encryption methods, please see this topic. PHP Chinese website welcomes everyone to come and learn.
 196
196
 10
10
Data storage encryption methods

Introduction to PHP simple symmetric encryption algorithm (code example)
This article brings you an introduction to PHP's simple symmetric encryption algorithm (code example). It has certain reference value. Friends in need can refer to it. I hope it will be helpful to you.
Mar 16, 2019 am 11:39 AM
Learn the encryption and decryption functions in Go language and implement symmetric encryption algorithms
Learn the encryption and decryption functions in Go language and implement symmetric encryption algorithms. In the modern Internet era, data security is particularly important. In order to ensure the safe transmission and storage of sensitive data, encryption and decryption are essential core operations. As a modern programming language, Go language provides a variety of encryption and decryption functions. This article will introduce common encryption and decryption functions in Go language and implement symmetric encryption algorithms through sample codes. Symmetric encryption algorithm refers to an encryption algorithm that uses the same key for encryption and decryption. Common symmetric encryption algorithms are D
Jul 30, 2023 pm 01:46 PM
Learn the encryption and decryption functions in Go language and implement asymmetric encryption algorithms
Learn the encryption and decryption functions in Go language and implement asymmetric encryption algorithms. In the modern information age, data security has become particularly important. To protect sensitive data from hackers and illegal visitors, encryption algorithms are widely used. Among them, asymmetric encryption algorithms are popular because of their high security. Go language is a powerful and concise programming language that provides us with a wealth of encryption and decryption functions to ensure data security. This article will introduce the encryption and decryption functions in Go language and demonstrate how to implement asymmetric encryption algorithms through examples. we will
Aug 01, 2023 pm 01:15 PM
Implement your own sha-256 hashing algorithm in PHP!
Hash is also called "hash". It receives any set of input information of any length and transforms it into a fixed-length data fingerprint through the hash algorithm. The fingerprint is the hash value. Overall, a hash can be thought of as a message digest.
May 23, 2022 am 11:39 AM
What are the key steps to learn hashing algorithms in PHP? How to optimize the computing performance of hash functions?
What are the key steps to learn hashing algorithms in PHP? How to optimize the computing performance of hash functions? The hash algorithm is one of the important algorithms widely used in computer science. Its main function is to convert input data of any length into a fixed-length hash value. In PHP programming, we often use hash algorithms, such as password encryption, data verification, etc. This article will introduce the key steps to learn the hash algorithm in PHP and how to optimize the computing performance of the hash function. 1. Learn the key steps of the hash algorithm in PHP and determine the purpose of the hash algorithm.
Sep 19, 2023 pm 02:04 PM
How to implement SHA hashing algorithm using Python?
How to implement SHA hashing algorithm using Python? SHA (Secure Hash Algorithm) is a commonly used cryptographic hash function that generates a fixed-length unique hash value for any length of data. The hashlib module is provided in Python, which contains commonly used hashing algorithms, including the SHA algorithm. This article will introduce in detail how to use Python to implement the SHA hash algorithm and provide relevant code examples. First, you need to import the hashlib module. The following is the code to import the hashlib module:
Sep 19, 2023 pm 12:42 PM
Detailed explanation of PHP's AES encryption algorithm example
This article mainly introduces PHP's AES encryption algorithm, and analyzes PHP's AES encryption algorithm class and its specific usage in the form of a complete example. It has certain reference value. Friends in need can refer to it.
Jun 01, 2018 pm 05:20 PM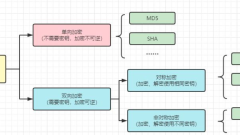
How to perform AES encryption and decryption operations in Java
1. Background knowledge In cryptography, encryption algorithms are divided into one-way encryption and two-way encryption. Symmetric encryption means that the same key is used for encryption and decryption, including AES encryption, DES encryption, etc. Asymmetric encryption refers to the use of different keys for encryption and decryption, including RSA encryption, etc. One-way encryption includes digest algorithms such as MD5 and SHA, which are irreversible. Two-way encryption includes symmetric encryption and asymmetric encryption. Two-way encryption is reversible, and the key to the ciphertext exists. 2. Introduction to AES AES: Advanced Encryption Standard (Advanced Encryption Standard) is a block encryption standard adopted by the U.S. federal government and is currently the most popular symmetric encryption algorithm. It is a new generation block encryption algorithm used to replace DES.
May 08, 2023 pm 10:34 PM
How to use PHP and GMP to perform RSA encryption and decryption algorithms for large integers
How to use PHP and GMP to perform RSA encryption and decryption algorithm for large integers. The RSA encryption algorithm is an asymmetric encryption algorithm that is widely used in the field of data security. It implements the process of public key encryption and private key decryption based on two particularly large prime numbers and some simple mathematical operations. In the PHP language, the calculation of large integers can be realized through the GMP (GNUMultiplePrecision) library, and the encryption and decryption functions can be realized by combining the RSA algorithm. This article will introduce how to use PHP and GMP libraries to
Jul 28, 2023 pm 05:25 PM
How to solve the memory ecc error reported by the Linux server
Memory ECC errors reported on Linux servers usually indicate hardware memory errors. The processing steps are: 1. Check the system log to check whether there are error messages or warnings related to memory errors; 2. Refer to the server manufacturer's documentation to find and run the server's Use a memory diagnostic tool to determine the specific memory problem. 3. Try testing each module one by one to find out if a specific memory module is causing the problem. 4. Update the BIOS and firmware. 5. Contact the hardware vendor's technical support department.
Jul 11, 2023 pm 02:29 PM
Hot Article

Hot Tools
Kits AI
Transform your voice with AI artist voices. Create and train your own AI voice model.
SOUNDRAW - AI Music Generator
Create music easily for videos, films, and more with SOUNDRAW's AI music generator.
Web ChatGPT.ai
Free Chrome extension with OpenAI chatbot for efficient browsing.

Amurex
Amurex unifies workflows and organizes knowledge across existing tools.

Natoma Hosted MCP Platform
Managed platform for easy AI development with prebuilt servers.





